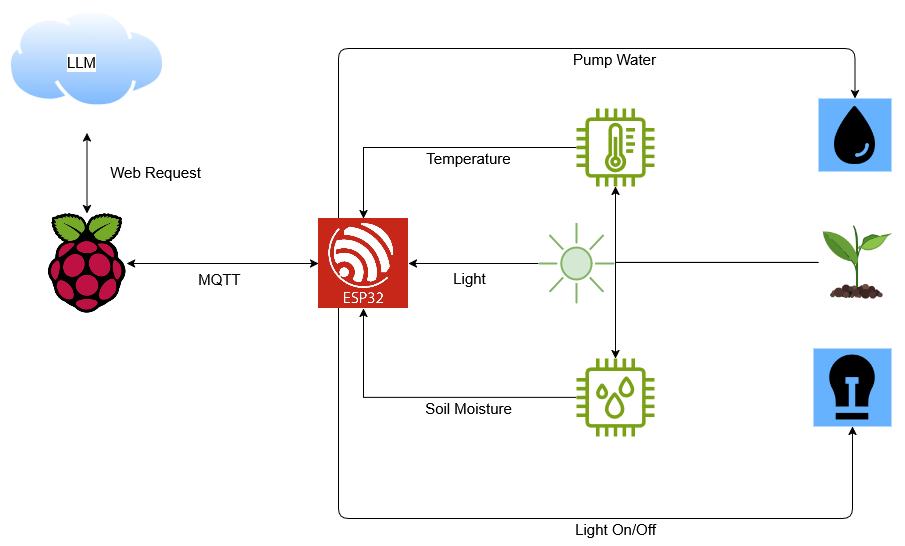
Hackers Leveraging GetShared to Deploy Malware Bypassing Defenses
Cybercriminals have discovered a new attack vector utilizing the legitimate file-sharing service GetShared to distribute malware and conduct phishing campaigns. This emerging threat allows attackers to circumvent traditional email security measures by exploiting the trusted status of notifications from recognized platforms. The technique represents an evolution in threat actors’ methodologies as they continue to adapt […] The post Hackers Leveraging GetShared to Deploy Malware Bypassing Defenses appeared first on Cyber Security News.

Cybercriminals have discovered a new attack vector utilizing the legitimate file-sharing service GetShared to distribute malware and conduct phishing campaigns.
This emerging threat allows attackers to circumvent traditional email security measures by exploiting the trusted status of notifications from recognized platforms.
The technique represents an evolution in threat actors’ methodologies as they continue to adapt to improved security controls at the email gateway level.
The attack begins when victims receive authentic email notifications from GetShared informing them that someone has shared a file, typically with business-related names such as “DESIGN LOGO.rar.”
These notifications contain legitimate formatting and branding from GetShared, making them particularly convincing.
.webp)
The accompanying messages often employ classic phishing tactics, such as inquiries about pricing for items supposedly included in the attachment, along with requests for delivery time and payment details to create a sense of legitimacy.
Kaspersky researchers identified this growing trend after analyzing suspicious notifications forwarded by vigilant users.
Their investigation revealed that GetShared has gained significant popularity among scammers seeking new platforms to exploit after security improvements in previously targeted services like Google Calendar and Dropbox.
What makes this attack vector particularly dangerous is its ability to bypass traditional email security measures.
Most organizations implement robust filtering at the email gateway level, but legitimate notifications from trusted services like GetShared typically pass through these defenses unimpeded.
Infection Mechanism
The actual infection process utilizes GetShared’s file-sharing functionality as a delivery mechanism. When users click the “Download” button in these notifications, they are directed to GetShared’s platform where the malicious payload awaits.
In some instances, rather than delivering malware immediately, attackers distribute text files containing instructions that initiate social engineering tactics to further develop the attack.
This multi-stage approach reduces the likelihood of detection by security solutions that scan for known malicious signatures.
A particularly concerning aspect is the diversification of payloads. While some campaigns distribute obvious malware executables, others employ archive files containing seemingly innocuous documents that execute malicious scripts when opened.
Security experts recommend implementing comprehensive staff training and deploying endpoint protection capable of detecting behavioral anomalies rather than relying solely on signature-based detection.
Malware Trends Report Based on 15000 SOC Teams Incidents, Q1 2025 out!-> Get Your Free Copy
The post Hackers Leveraging GetShared to Deploy Malware Bypassing Defenses appeared first on Cyber Security News.






































































































































































![[The AI Show Episode 145]: OpenAI Releases o3 and o4-mini, AI Is Causing “Quiet Layoffs,” Executive Order on Youth AI Education & GPT-4o’s Controversial Update](https://www.marketingaiinstitute.com/hubfs/ep%20145%20cover.png)









































































































































































_XFkvNLu.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)

























































































_Tanapong_Sungkaew_via_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)





































































































![Apple Restructures Global Affairs and Apple Music Teams [Report]](https://www.iclarified.com/images/news/97162/97162/97162-640.jpg)
![New iPhone Factory Goes Live in India, Another Just Days Away [Report]](https://www.iclarified.com/images/news/97165/97165/97165-640.jpg)