Samsung MagicINFO Vulnerability Allows Remote Code Execution Without Valid User
A critical security vulnerability has been discovered in Samsung’s MagicINFO digital signage management platform that could allow attackers to execute arbitrary code with system-level privileges without requiring authentication. The vulnerability, tracked as CVE-2024-7399, affects Samsung MagicINFO 9 Server versions prior to 21.1050 and has received a CVSS score of 9.8, indicating maximum severity. Security researchers […] The post Samsung MagicINFO Vulnerability Allows Remote Code Execution Without Valid User appeared first on Cyber Security News.

A critical security vulnerability has been discovered in Samsung’s MagicINFO digital signage management platform that could allow attackers to execute arbitrary code with system-level privileges without requiring authentication.
The vulnerability, tracked as CVE-2024-7399, affects Samsung MagicINFO 9 Server versions prior to 21.1050 and has received a CVSS score of 9.8, indicating maximum severity.
Security researchers have identified a path traversal vulnerability that enables attackers to write arbitrary files to the system.
The flaw specifically exists in an endpoint that fails to properly validate user-supplied paths before using them in file operations.
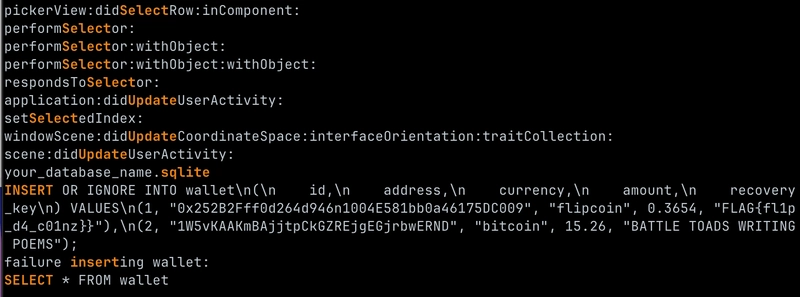
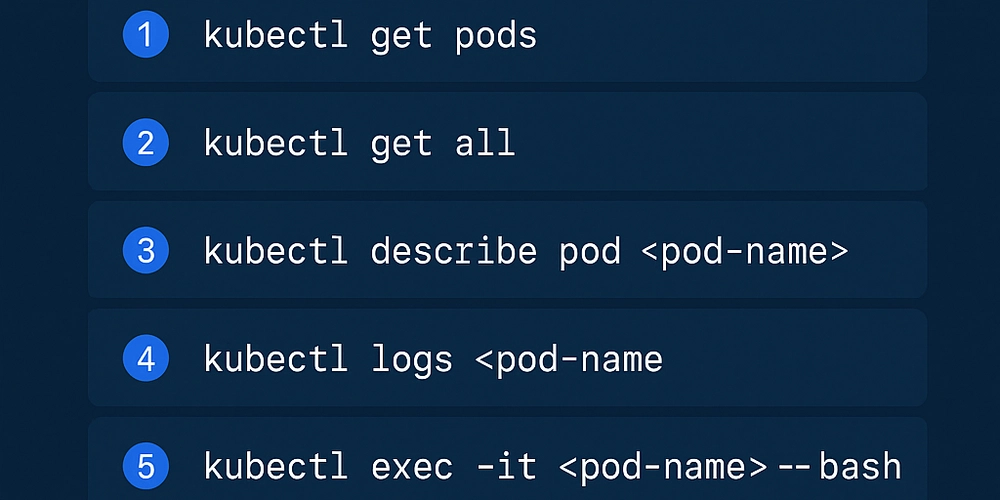
According to the technical analysis, the /MagicInfo/servlet/SWUpdateFileUploader endpoint implemented by the SWUpdateFileUploadServlet class contains multiple security issues.
The endpoint does not verify user authentication, accepts filenames without proper validation, and fails to check file extensions in requests.
When combined, these vulnerabilities allow attackers to upload malicious JSP files and execute arbitrary server-side code with system privileges. The vulnerability’s root cause lies in how the application handles file paths.
The servlet reads the fileName parameter from HTTP requests and concatenates it with a constant directory path without properly neutralizing special path elements.
This allows attackers to use path traversal sequences to place files in unauthorized locations on the server.
The affected code creates paths using:
textString savedFileName = System.currentTimeMillis() + fileName;
swUpdateFilePath = swUpdateFileFolderPath + File.separator + savedFileName;
This implementation enables attackers to upload web shells or other malicious code that can be executed with server privileges, potentially leading to complete system compromise.
Samsung has acknowledged the vulnerability and released a patch in version 21.1050 of the MagicINFO 9 Server. According to Samsung’s security update notice, “The patch modifies verification logic of the input”.
The vulnerability was discovered by an independent security researcher working with SSD Secure Disclosure.
The vendor was notified on January 12, 2025, and after the standard 90-day disclosure window plus grace period, the information has been released to the public due to a duplicate notice received by the vendor.
Organizations using affected versions of Samsung MagicINFO are strongly urged to update to version 21.1050 or later immediately. The vulnerability requires no user interaction to exploit and can be triggered remotely by unauthenticated attackers.
Samsung MagicINFO is widely used for digital signage management across various industries, making this vulnerability particularly concerning for organizations that rely on this platform for their display systems.
The post Samsung MagicINFO Vulnerability Allows Remote Code Execution Without Valid User appeared first on Cyber Security News.




























![[Free Webinar] Guide to Securing Your Entire Identity Lifecycle Against AI-Powered Threats](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjqbZf4bsDp6ei3fmQ8swm7GB5XoRrhZSFE7ZNhRLFO49KlmdgpIDCZWMSv7rydpEShIrNb9crnH5p6mFZbURzO5HC9I4RlzJazBBw5aHOTmI38sqiZIWPldRqut4bTgegipjOk5VgktVOwCKF_ncLeBX-pMTO_GMVMfbzZbf8eAj21V04y_NiOaSApGkM/s1600/webinar-play.jpg?#)








































































































































![[The AI Show Episode 145]: OpenAI Releases o3 and o4-mini, AI Is Causing “Quiet Layoffs,” Executive Order on Youth AI Education & GPT-4o’s Controversial Update](https://www.marketingaiinstitute.com/hubfs/ep%20145%20cover.png)












































































































































































































































_XFkvNLu.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)

























_Tanapong_Sungkaew_via_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)










































































































![Apple Restructures Global Affairs and Apple Music Teams [Report]](https://www.iclarified.com/images/news/97162/97162/97162-640.jpg)
![New iPhone Factory Goes Live in India, Another Just Days Away [Report]](https://www.iclarified.com/images/news/97165/97165/97165-640.jpg)