Firefox 138 Released With Fix for Multiple High-Severity Vulnerabilities
Mozilla has released Firefox 138, addressing several high-severity security vulnerabilities while introducing long-awaited features, including improved profile management. Security researchers identified multiple critical flaws that could allow attackers to escalate privileges or bypass security mechanisms, prompting this significant security update, which was released on April 29, 2025. High-Impact Security Flaws in Firefox and Thunderbird The […] The post Firefox 138 Released With Fix for Multiple High-Severity Vulnerabilities appeared first on Cyber Security News.

Mozilla has released Firefox 138, addressing several high-severity security vulnerabilities while introducing long-awaited features, including improved profile management.
Security researchers identified multiple critical flaws that could allow attackers to escalate privileges or bypass security mechanisms, prompting this significant security update, which was released on April 29, 2025.
High-Impact Security Flaws in Firefox and Thunderbird
The Mozilla Foundation Security Advisory details four high-impact vulnerabilities remediated in this release.
The most concerning issues include a privilege escalation vulnerability, a memory corruption flaw, and a process isolation bypass.
CVE-2025-2817, discovered by security researcher Dong-uk Kim (@justlikebono), revealed a serious privilege escalation vulnerability in Firefox’s update mechanism.
The flaw allowed medium-integrity user processes to interfere with SYSTEM-level updaters by manipulating file-locking behavior.
“By injecting code into the user-privileged process, an attacker could bypass intended access controls, allowing SYSTEM-level file operations on paths controlled by a non-privileged user and enabling privilege escalation,” Mozilla explained in their advisory.
For macOS users, CVE-2025-4082 addressed WebGL shader attribute memory corruption that could trigger an out-of-bounds read.
When chained with other vulnerabilities, this flaw could be weaponized to escalate privileges on affected systems.
Another significant vulnerability, CVE-2025-4083, reported by Nika Layzell, involved a process isolation bypass using URI links in cross-origin frames.
This vulnerability stemmed from improper handling of javascript: URIs, potentially allowing content to execute in the top-level document’s process instead of the intended frame, which could enable a sandbox escape.
Mozilla also fixed memory safety bugs tracked as CVE-2025-4092, which affected both Firefox 137 and Thunderbird 137.
These bugs showed evidence of memory corruption and could potentially be exploited to run arbitrary code.
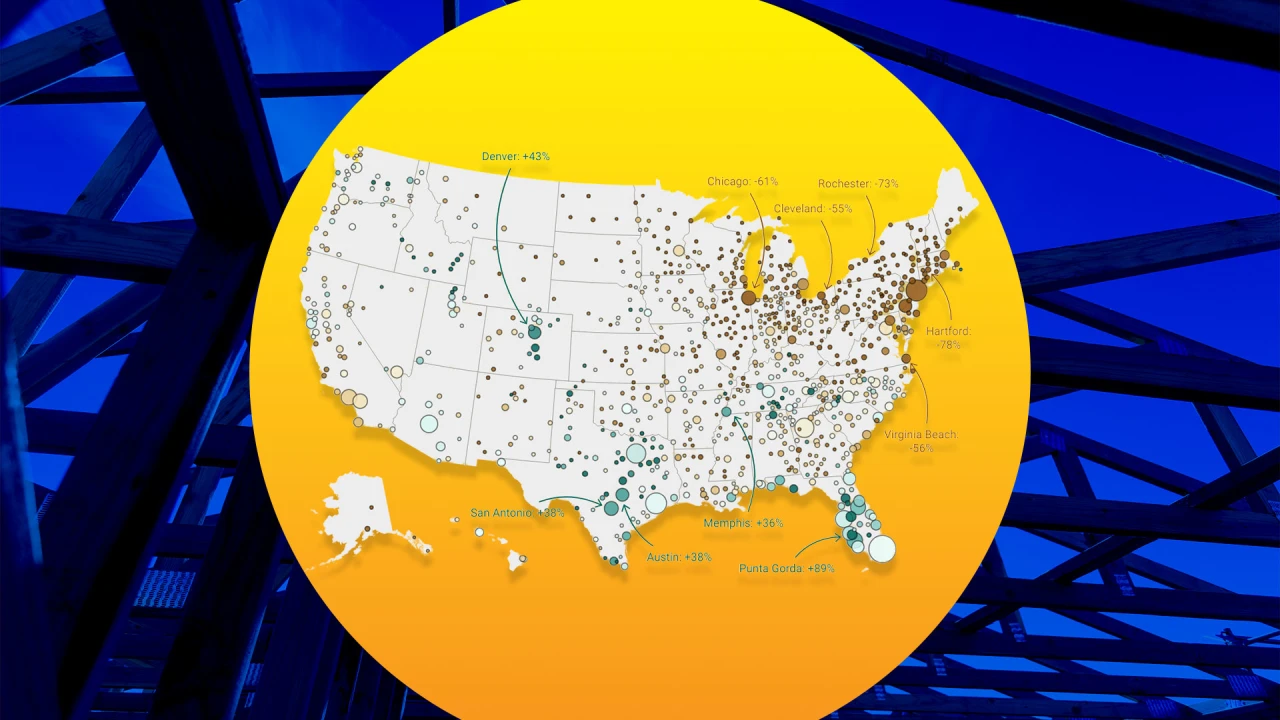
CVEs Affected Products Impact Exploit Prerequisites CVSS 3.1 Score CVE-2025-2817 Firefox Privilege escalation Attacker must have code execution as a medium-integrity user process on the target system; local access required High CVE-2025-4082 Firefox for macOS Memory corruption, privilege escalation Attacker must be able to modify specific WebGL shader attributes; affects only macOS version High CVE-2025-4083 Firefox Process isolation bypass, sandbox escape Attacker must be able to inject or control URI links in cross-origin frames High CVE-2025-4092 Firefox, Thunderbird Memory corruption, arbitrary code execution Attacker must trigger memory safety bugs, likely through crafted web content or email High
New Profile Management Feature
Beyond security improvements, Firefox 138 introduces several user-focused enhancements, most notably a much-anticipated profile management system.
This feature allows users to create separate profiles to compartmentalize their browsing activities, keeping bookmarks, tabs, passwords, and browsing history segregated between different usage contexts.
The feature is rolling out gradually, but can be enabled immediately by toggling the “browser.profiles.enabled” preference in about:config.
The Center for Internet Security (CIS) has rated these vulnerabilities as high-risk for government and business entities.
CISA stated in its advisory that “There are currently no reports of these vulnerabilities being exploited in the wild,” but it recommended that users apply updates immediately after appropriate testing.
Users are strongly encouraged to update to Firefox 138 as soon as possible. In addition to the standard Firefox release, Mozilla has updated Firefox ESR to versions 115.23 and 128.10 with the same security fixes.
Are you from the SOC and DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.
The post Firefox 138 Released With Fix for Multiple High-Severity Vulnerabilities appeared first on Cyber Security News.




























![[Free Webinar] Guide to Securing Your Entire Identity Lifecycle Against AI-Powered Threats](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjqbZf4bsDp6ei3fmQ8swm7GB5XoRrhZSFE7ZNhRLFO49KlmdgpIDCZWMSv7rydpEShIrNb9crnH5p6mFZbURzO5HC9I4RlzJazBBw5aHOTmI38sqiZIWPldRqut4bTgegipjOk5VgktVOwCKF_ncLeBX-pMTO_GMVMfbzZbf8eAj21V04y_NiOaSApGkM/s1600/webinar-play.jpg?#)








































































































































![[The AI Show Episode 145]: OpenAI Releases o3 and o4-mini, AI Is Causing “Quiet Layoffs,” Executive Order on Youth AI Education & GPT-4o’s Controversial Update](https://www.marketingaiinstitute.com/hubfs/ep%20145%20cover.png)












































































































































































































































_XFkvNLu.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)

























_Tanapong_Sungkaew_via_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)










































































































![Apple Restructures Global Affairs and Apple Music Teams [Report]](https://www.iclarified.com/images/news/97162/97162/97162-640.jpg)
![New iPhone Factory Goes Live in India, Another Just Days Away [Report]](https://www.iclarified.com/images/news/97165/97165/97165-640.jpg)