Apple AirPlay SDK devices at risk of takeover—make sure you update
Researchers found a set of vulnerabilities that puts all devices leveraging Apple's AirPlay at risk.

Researchers found a set of vulnerabilities in Apple’s AirPlay SDK that put billions of users at risk of their devices being taking over.
AirPlay is Apple’s proprietary wireless technology that allows you to stream audio, video, photos, and even mirror your device’s screen from an iPhone, iPad, or Mac to other compatible devices like Apple TV, HomePod, smart TVs, or speakers. It works over Wi-Fi, so you don’t need cables.
Apple added the necessary updates on April 28 to the March 31 update. The update—iOS 18.4 and iPadOS 18.4—was initially issued on March 31, but the additional security fixes were delivered through Rapid Security Responses, or minor patches that Apple incorporated after the initial release. Rapid Security Response (RSR) is a type of software patch delivering security fixes between Apple’s regular, scheduled software updates.
The good news is if you installed the March 31 update, you should be fine. Otherwise, check manually if any updates are available.
To check if you’re using the latest software version, go to Settings > General > Software Update. You want to be on iOS 18.4.1 or iPadOS 18.4.1, so update now if you’re not. It’s also worth turning on Automatic Updates if you haven’t already. You can do that on the same screen.
- The latest version of macOS is 15.4.1. Learn how to update the software on your Mac and how to allow important background updates.
- The latest version of tvOS is 18.4.1. Learn how to update the software on your Apple TV.
- The latest version of watchOS is 11.4. Learn how to update the software on your Apple Watch.
- The latest version of visionOS is 2.4.1. Learn how to update the software on your Apple Vision Pro.
The AirPlay SDK (Software Development Kit) is a set of programming tools Apple provides to app developers to integrate AirPlay functionality into their apps. Using the AirPlay SDK, developers can add features that allow their apps to stream audio or video content wirelessly to AirPlay-compatible devices. This makes apps “AirPlay-ready” by handling the streaming and control behind the scenes.
Combining vulnerabilities allows an attacker on the local network to potentially take control of devices that support AirPlay—both Apple devices and third-party devices that leverage the AirPlay SDK.
Apple released updates to fix the vulnerabilities on April 29 for members of the Apple MFi Program, who are developers of Apple-compatible accessories or software.
The researchers who found and reported these flaws warn they can be exploited without any user interaction—or with just a single click—to execute remote code. Attackers could also use them for man-in-the-middle interceptions, denial-of-service disruptions, and to bypass access controls and user prompts. On top of that, these vulnerabilities may allow unauthorized access to sensitive data and local files, making them a serious risk that demands immediate attention.
Technical details
In total, the researchers responsibly disclosed 23 vulnerabilities to Apple, leading to 17 CVEs being issued. A complete list and description of these CVEs, as well as specific attack scenarios they enable, can be found on their blog.
The most important vulnerabilities are:
CVE-2025-24252: Successful exploitation of the use-after-free vulnerability could allow a remote attacker to execute arbitrary code. When exploited together with CVE-2025-24206, the attacker is able to perform zero-click remote code execution on other vulnerable AirPlay-enabled devices in the same network, without any user interaction. The vulnerability has a Common Vulnerability Scoring System (CVSSv3.1) score of 9.8 out of 10.
CVE-2025-24206: Successful exploitation of the vulnerability could allow an attacker to bypass authentication and conduct malicious activities without user interaction when exploited with other vulnerabilities.
CVE-2025-24132: Successful exploitation of the stack-based buffer overflow vulnerability could allow an attacker to perform zero-click remote code execution on vulnerable AirPlay SDK devices and potentially leak sensitive information by eavesdropping.
That the attacker does need to be on the same network, but exploitation require minimal to no interaction of the target.
Possible protective actions
These depend very much on the types of devices you are using, so I will try to give some general guidance and the reasons behind them.
- As we said above, make sure your devices are fully updated
- Use up-to-date and active malware protection
- Disable AirPlay if you’re not using it, or set it to Ask as a minimum
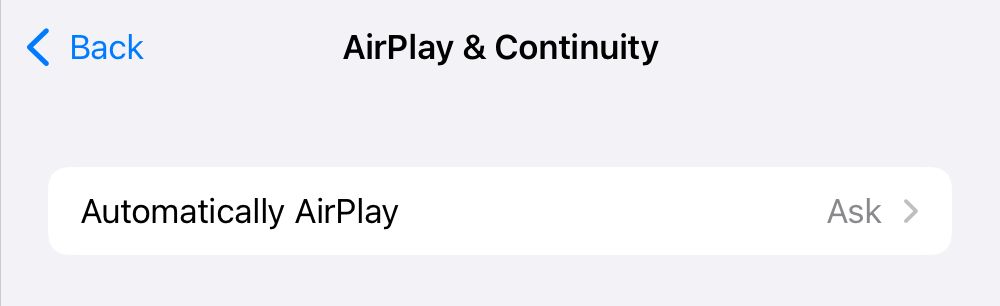
- Disable AirPlay Receiver if it is not in use.
- Be extra careful on public networks. This vulnerability could theoretically spread in airports, offices, hotels, or conferences where many Apple devices are in close proximity. In such cases, avoid using unsecured Wi-Fi.
- Restrict AirPlay settings: Change the Allow AirPlay for to Current User. While this does not prevent all of the issues, it does reduce the protocol’s attack surface.
We don’t just report on phone security—we provide it
Cybersecurity risks should never spread beyond a headline. Keep threats off your mobile devices by downloading Malwarebytes for iOS, and Malwarebytes for Android today.












































































































































































![[The AI Show Episode 152]: ChatGPT Connectors, AI-Human Relationships, New AI Job Data, OpenAI Court-Ordered to Keep ChatGPT Logs & WPP’s Large Marketing Model](https://www.marketingaiinstitute.com/hubfs/ep%20152%20cover.png)





















































































































![[DEALS] Internxt Cloud Storage Lifetime Subscription: 10TB Plan (87% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)


























![Designing a Robust Modular Hardware-Oriented Application in C++ [closed]](https://i.sstatic.net/f2sQd76t.webp)

























.jpg?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)




















































































_Andreas_Prott_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)

_designer491_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)


































































































![What Gemini app features are free versus paid? [June 2025]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/01/gemini-android-5.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)












![Apple M4 Mac Mini Back on Sale for $499 [Deal]](https://www.iclarified.com/images/news/97617/97617/97617-640.jpg)