What you need to have in place for AI Agent and MCP Integration for your product
This article is created by Logto, an open-source solution that helps developers implement secure auth in minutes instead of months. How to drive AI transformation and what you need to prepare for your products I’m been really pumped about the upcoming world of AI evolves and let’s see what are the latest news in DeepSeek Chinese startup DeepSeek released DeepSeek-V3-0324, a major upgrade with improved reasoning and coding capabilities—positioning it as a strong OpenAI competitor. OpenAI Operator OpenAI launched Operator, an AI agent that can autonomously perform web tasks using a built-in browser. It rolled out to U.S. ChatGPT Pro users. Manus Chinese AI startup introduced Manus, a government-approved AI assistant positioned as the world’s first general-purpose AI agent with real autonomy. Backed by big names like Alibaba. MCP (Model Context Protocol) Originally launched by Anthropic, MCP became the open standard for connecting AI agents to external tools and APIs. In March 2025, OpenAI adopted MCP in its ecosystem, boosting interoperability. Many AI and agent builders are feeling FOMO and uncertainty about their current products. They’re asking: How should we evolve? What technical foundations do we need from day one? One issue that keeps popping up is surprisingly simple: AI agents often fail at signing up or logging in. In a previous article, we broke down real examples of how today’s agents handle authentication—and uncovered major gaps. These issues raise serious concerns around privacy and user security. In this piece, we’ll go deeper into that topic and what you can do about it. Make sure your product is open standard and enables agent services to access your products. First: Build secure agent authentication, ensure your agent can safely access third-party services and protect user credentials Like the previous article we mentioned, in today’s agent auth landscape, there’s still a lack of clear best practices for how agents should securely access third-party services (like MCP servers). Let’s take a simple example: Say you’re building an agent that replies to emails on your behalf. There are a few common ways to give the agent access: Share your email and password directly
This article is created by Logto, an open-source solution that helps developers implement secure auth in minutes instead of months.
How to drive AI transformation and what you need to prepare for your products
I’m been really pumped about the upcoming world of AI evolves and let’s see what are the latest news in
DeepSeek
Chinese startup DeepSeek released DeepSeek-V3-0324, a major upgrade with improved reasoning and coding capabilities—positioning it as a strong OpenAI competitor.
OpenAI Operator
OpenAI launched Operator, an AI agent that can autonomously perform web tasks using a built-in browser. It rolled out to U.S. ChatGPT Pro users.
Manus
Chinese AI startup introduced Manus, a government-approved AI assistant positioned as the world’s first general-purpose AI agent with real autonomy. Backed by big names like Alibaba.
MCP (Model Context Protocol)
Originally launched by Anthropic, MCP became the open standard for connecting AI agents to external tools and APIs. In March 2025, OpenAI adopted MCP in its ecosystem, boosting interoperability.
Many AI and agent builders are feeling FOMO and uncertainty about their current products. They’re asking:
How should we evolve? What technical foundations do we need from day one?
One issue that keeps popping up is surprisingly simple:
AI agents often fail at signing up or logging in.
In a previous article, we broke down real examples of how today’s agents handle authentication—and uncovered major gaps. These issues raise serious concerns around privacy and user security.
In this piece, we’ll go deeper into that topic and what you can do about it. Make sure your product is open standard and enables agent services to access your products.
First: Build secure agent authentication, ensure your agent can safely access third-party services and protect user credentials
Like the previous article we mentioned, in today’s agent auth landscape, there’s still a lack of clear best practices for how agents should securely access third-party services (like MCP servers).
Let’s take a simple example:
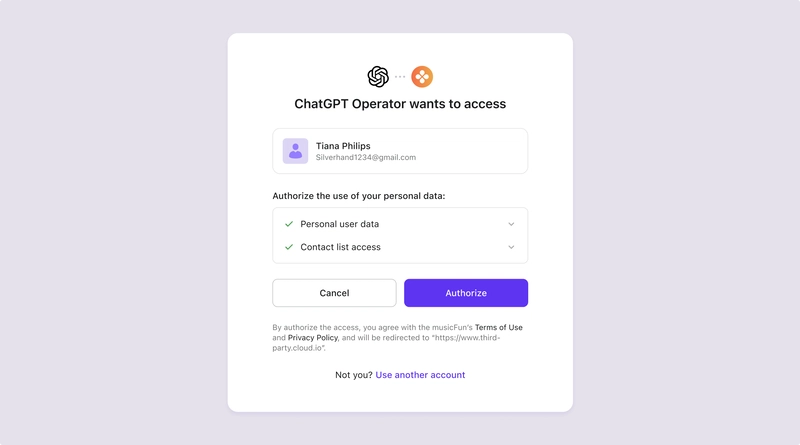
Say you’re building an agent that replies to emails on your behalf. There are a few common ways to give the agent access:
Share your email and password directly




































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)




















































































































































































































































































.jpg?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)

























































.png?#)






































.webp?#)



















































































![Leaker vaguely comments on under-screen camera in iPhone Fold [U]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/04/iPhone-Fold-will-have-Face-ID-embedded-in-the-display-%E2%80%93-leaker.webp?resize=1200%2C628&quality=82&strip=all&ssl=1)


![[Fixed] Gemini app is failing to generate Audio Overviews](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/03/Gemini-Audio-Overview-cover.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)













![Apple Seeds tvOS 18.5 Beta 2 to Developers [Download]](https://www.iclarified.com/images/news/97011/97011/97011-640.jpg)
![Apple Releases macOS Sequoia 15.5 Beta 2 to Developers [Download]](https://www.iclarified.com/images/news/97014/97014/97014-640.jpg)