Securing User Authentication: A Practical Guide to SMS OTP
One-Time Passwords (OTPs) sent via SMS are a widely recognized method for adding an extra layer of security to user authentication. While end-users find them familiar, implementing SMS OTP effectively requires a solid grasp of the technical workflow and crucial security considerations. This guide will walk you through: What SMS OTP is and its common uses. The technical flow of an SMS OTP system. The advantages and disadvantages of using SMS OTP. Detailed security risks and how to mitigate them. Best practices for secure implementation. Stronger alternatives to consider. What is SMS OTP? An SMS OTP is typically a short numeric or alphanumeric code sent via a text message (SMS) to a user's registered mobile phone number. These codes are time-sensitive, usually expiring within a few minutes (e.g., 1 to 5 minutes), and are intended for single use. Common scenarios where SMS OTP is used include: Two-Factor Authentication (2FA): Adding a second layer of security during login. Transaction Verification: Confirming high-value actions or payments. Password Resets: Verifying identity before allowing a password change. Phone Number Verification: Confirming ownership of a phone number during sign-up or profile updates (very common in Nigeria for service registration). How the SMS OTP Process Works Here’s a step-by-step breakdown of the typical SMS OTP flow: User Initiates Action: The user performs an action requiring verification (e.g., login, password reset) and often provides their phone number. Backend Generates OTP: Your application's backend generates a cryptographically secure random code (e.g., 6-8 digits). Store OTP Securely:** The generated OTP is stored temporarily (e.g., in Redis or a database) along with the user identifier (like phone number or user ID), an expiration timestamp, and potentially a usage status flag. Send OTP via SMS Gateway: The backend sends the plain text OTP and the user's phone number to an SMS gateway provider (e.g., Twilio, Vonage, or regional/local providers like Yournotify, Africa’s Talking, Infobip relevant in Nigeria) via their API. Gateway Delivers SMS: The SMS gateway attempts to deliver the text message containing the OTP to the user's mobile device via the telecommunication network (e.g., MTN, Glo, Airtel, 9mobile in Nigeria). User Enters OTP: The user receives the SMS, reads the OTP, and enters it into your application's interface. Backend Validates OTP: Your application retrieves the stored (hashed) OTP record associated with the user. It compares the user-provided OTP (after hashing it using the same method) against the stored hash. It also checks: Has the OTP expired? Has this specific OTP already been used successfully? Has the user exceeded the maximum allowed validation attempts? Grant or Deny Access: If the OTP is valid, hasn't expired, hasn't been used, and retry limits aren't exceeded, the user is authenticated, or the action is authorized. Otherwise, access is denied, and an appropriate error message is shown. The used OTP record should be marked as invalid or deleted immediately after successful validation. Pros and Cons of Using SMS OTP Pros Cons High User Familiarity: Most users understand how to receive and use SMS codes. Security Vulnerabilities: Susceptible to SIM swapping, SS7 attacks, phishing, and malware. Wide Accessibility: Relies on basic mobile phone functionality (SMS), not requiring smartphones or internet access on the receiving device itself. Delivery Issues: Dependent on mobile carrier networks (like MTN, Glo, Airtel, 9mobile in Nigeria), which can experience delays or failures. Relatively Easy Initial Setup: Integrating with SMS gateway APIs is often straightforward. Cost: SMS messages incur costs per message sent, which can add up significantly, especially for international numbers or across networks. Good for Phone Verification: Directly confirms access to the specific phone number. User Friction: Users may need to wait for the SMS, switch apps, and manually type the code. Not Truly "Something You Have": The phone network intercepts and forwards the code, it's not generated solely on the user's physical device like TOTP. Security Risks and How to Mitigate Them While convenient, SMS OTP has known vulnerabilities: SIM Swap Fraud: Attackers trick or bribe mobile carrier employees (or exploit processes) to transfer the victim's phone number to a SIM card they control. They then receive the OTPs. This is a significant concern in Nigeria. Mitigation: Monitor for recent SIM changes (some telco APIs might offer this, check feasibility). Implement velocity checks (unusual login patterns/locations). Consider delays or additional verification after a known SIM swap indicator. Educate users about SIM security. Use SMS OTP as one factor, not the sole recovery method for high-value accounts. SS7 Exploits: Attackers exploit vulnerabilities in the Signalin
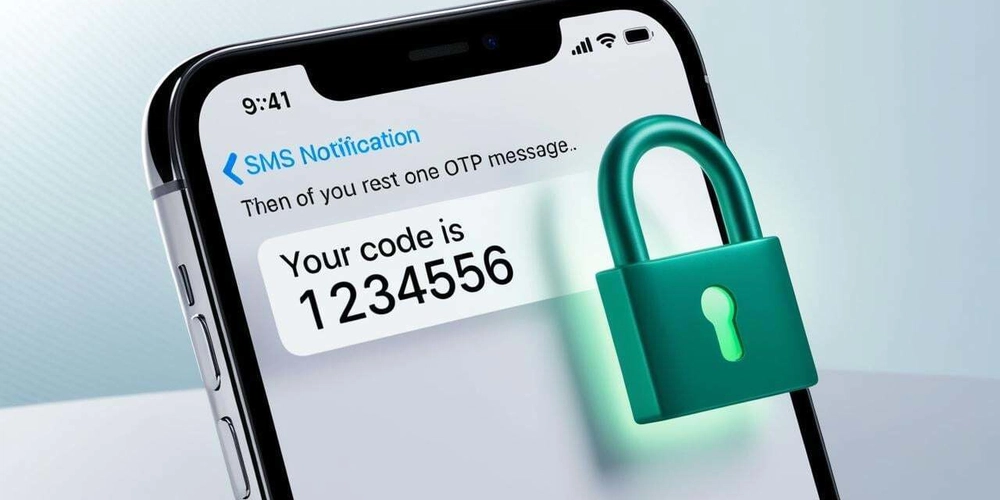
One-Time Passwords (OTPs) sent via SMS are a widely recognized method for adding an extra layer of security to user authentication. While end-users find them familiar, implementing SMS OTP effectively requires a solid grasp of the technical workflow and crucial security considerations.
This guide will walk you through:
- What SMS OTP is and its common uses.
- The technical flow of an SMS OTP system.
- The advantages and disadvantages of using SMS OTP.
- Detailed security risks and how to mitigate them.
- Best practices for secure implementation.
- Stronger alternatives to consider.
What is SMS OTP?
An SMS OTP is typically a short numeric or alphanumeric code sent via a text message (SMS) to a user's registered mobile phone number. These codes are time-sensitive, usually expiring within a few minutes (e.g., 1 to 5 minutes), and are intended for single use.
Common scenarios where SMS OTP is used include:
- Two-Factor Authentication (2FA): Adding a second layer of security during login.
- Transaction Verification: Confirming high-value actions or payments.
- Password Resets: Verifying identity before allowing a password change.
- Phone Number Verification: Confirming ownership of a phone number during sign-up or profile updates (very common in Nigeria for service registration).
How the SMS OTP Process Works
Here’s a step-by-step breakdown of the typical SMS OTP flow:
- User Initiates Action: The user performs an action requiring verification (e.g., login, password reset) and often provides their phone number.
- Backend Generates OTP: Your application's backend generates a cryptographically secure random code (e.g., 6-8 digits).
- Store OTP Securely:** The generated OTP is stored temporarily (e.g., in Redis or a database) along with the user identifier (like phone number or user ID), an expiration timestamp, and potentially a usage status flag.
- Send OTP via SMS Gateway: The backend sends the plain text OTP and the user's phone number to an SMS gateway provider (e.g., Twilio, Vonage, or regional/local providers like Yournotify, Africa’s Talking, Infobip relevant in Nigeria) via their API.
- Gateway Delivers SMS: The SMS gateway attempts to deliver the text message containing the OTP to the user's mobile device via the telecommunication network (e.g., MTN, Glo, Airtel, 9mobile in Nigeria).
- User Enters OTP: The user receives the SMS, reads the OTP, and enters it into your application's interface.
- Backend Validates OTP: Your application retrieves the stored (hashed) OTP record associated with the user. It compares the user-provided OTP (after hashing it using the same method) against the stored hash. It also checks:
- Has the OTP expired?
- Has this specific OTP already been used successfully?
- Has the user exceeded the maximum allowed validation attempts?
- Grant or Deny Access: If the OTP is valid, hasn't expired, hasn't been used, and retry limits aren't exceeded, the user is authenticated, or the action is authorized. Otherwise, access is denied, and an appropriate error message is shown. The used OTP record should be marked as invalid or deleted immediately after successful validation.
Pros and Cons of Using SMS OTP
| Pros | Cons |
|---|---|
| High User Familiarity: Most users understand how to receive and use SMS codes. | Security Vulnerabilities: Susceptible to SIM swapping, SS7 attacks, phishing, and malware. |
| Wide Accessibility: Relies on basic mobile phone functionality (SMS), not requiring smartphones or internet access on the receiving device itself. | Delivery Issues: Dependent on mobile carrier networks (like MTN, Glo, Airtel, 9mobile in Nigeria), which can experience delays or failures. |
| Relatively Easy Initial Setup: Integrating with SMS gateway APIs is often straightforward. | Cost: SMS messages incur costs per message sent, which can add up significantly, especially for international numbers or across networks. |
| Good for Phone Verification: Directly confirms access to the specific phone number. | User Friction: Users may need to wait for the SMS, switch apps, and manually type the code. |
| Not Truly "Something You Have": The phone network intercepts and forwards the code, it's not generated solely on the user's physical device like TOTP. |
Security Risks and How to Mitigate Them
While convenient, SMS OTP has known vulnerabilities:
- SIM Swap Fraud: Attackers trick or bribe mobile carrier employees (or exploit processes) to transfer the victim's phone number to a SIM card they control. They then receive the OTPs. This is a significant concern in Nigeria.
- Mitigation: Monitor for recent SIM changes (some telco APIs might offer this, check feasibility). Implement velocity checks (unusual login patterns/locations). Consider delays or additional verification after a known SIM swap indicator. Educate users about SIM security. Use SMS OTP as one factor, not the sole recovery method for high-value accounts.
- SS7 Exploits: Attackers exploit vulnerabilities in the Signaling System No. 7 (SS7) network protocol (used by telcos globally) to intercept SMS messages, including OTPs, without needing the victim's phone.
- Mitigation: Little direct mitigation for end-applications. This highlights why SMS OTP shouldn't be used for the highest security needs. Rely on secure alternatives where possible.
- Phishing / Social Engineering: Users are tricked via fake websites, calls, or messages (e.g., fake bank alerts) into revealing the OTP they received.
-
Mitigation: Educate users never to share OTPs. Clearly state in the SMS message what the OTP is for (e.g., "
Your login code for MyBankApp is 123456. Do NOT share it."). Never ask for OTPs via email or phone support. Implement clear branding in messages if possible.
-
Mitigation: Educate users never to share OTPs. Clearly state in the SMS message what the OTP is for (e.g., "
- Malware: Malicious apps on the user's phone can potentially read incoming SMS messages.
- Mitigation: Primarily relies on user device security. Encourage users to keep OS/apps updated and install apps only from trusted sources (Google Play Store, Apple App Store).
- Lack of Guaranteed Delivery: You often don't know for sure if the user actually received the SMS, only that the gateway accepted it. Network congestion or routing issues can cause delays/failures.
- Mitigation: Use gateways providing reliable delivery reports (DLRs). Implement resend options with strict rate limiting. Provide clear user feedback and potentially offer alternative verification methods after failures.
Best Practices for Secure Implementation
-
Secure OTP Generation: Use a cryptographically secure pseudo-random number generator (CSPRNG). Node.js's
crypto.randomInt()is suitable. Avoid predictable methods likeMath.random(). Aim for 6-8 digits. - Short Validity Period: Set a strict expiration time (e.g., 2-5 minutes) to limit the window for attack.
-
Rate Limiting: Essential to prevent abuse and control costs.
- Limit OTP generation requests per phone number/user ID (e.g., max 3 requests in 15 minutes).
- Limit validation attempts per specific OTP (e.g., max 3-5 attempts).
- Implement global and/or IP-based rate limiting on the API endpoint to prevent brute-force attacks and SMS Pumping fraud (where attackers trigger mass SMS sends to premium numbers).
- Single Use Only: Ensure an OTP becomes invalid immediately after successful use. Delete it or flag it as used in your temporary store (e.g., Redis, database).
-
Secure Storage: Never store plain text OTPs. Store a salted hash of the OTP (e.g., using
bcrypt). When validating, hash the user input using the same method/salt and compare it with the stored hash. Since OTPs are short-lived, a reasonably fast hashing algorithm is acceptable. - Use Reputable SMS Gateways: Choose providers known for reliability, security practices, good DLRs, and strong deliverability in Nigeria (e.g., Yournotify, Africa’s Talking, Twilio with Nigerian routes, local aggregators). Evaluate their API security, support, and pricing models (per-SMS cost, network differences).
-
Informative but Vague Error Messages: Don't reveal why validation failed specifically on the user interface (e.g., use "
Invalid or expired code." instead of "Code expired" or "Code incorrect"). Do not confirm if a phone number is registered or not during the OTP request step, as this leaks information. -
User Experience (UX): Provide clear instructions (
Enter the code sent to 080xxxxxxx). Show an obvious input field. Consider displaying the remaining validity time. Offer an easy-to-find "Resend code" option (subject to rate limits). - Monitoring and Alerting: Monitor OTP generation rates (per user, globally), delivery success/failure rates (check DLRs), validation attempt failures, and costs. Set alerts for unusual spikes that might indicate abuse.
Code Example: Improved Basic SMS OTP in Node.js
const crypto = require('crypto'); // Use Node.js crypto module for secure random generation
const bcrypt = require('bcrypt'); // Use bcrypt for hashing OTPs before storage
const sendSMS = require('./sendSMS'); // Your SMS gateway integration (e.g., using Termii, Africa's Talking SDK/API)
const otpStore = {}; // !! WARNING: In-memory store suitable only for demos. Use Redis or a DB in production!
const OTP_EXPIRY_MINUTES = 3;
const SALT_ROUNDS = 10; // Cost factor for bcrypt hashing
async function generateAndSendOTP(phoneNumber) {
// 1. Generate Secure OTP
const otp = crypto.randomInt(100000, 999999).toString(); // Generate a 6-digit OTP
const expiresAt = Date.now() + OTP_EXPIRY_MINUTES * 60 * 1000;
try {
// 2. Hash the OTP before storing
const hashedOtp = await bcrypt.hash(otp, SALT_ROUNDS);
// 3. Store hashed OTP, expiry, and attempt count (using phone number as key here)
// !! PRODUCTION: Use Redis with TTL or a database table (e.g., otp_codes(phone_number, otp_hash, expires_at, attempts, status)) !!
otpStore[phoneNumber] = {
hash: hashedOtp,
expiresAt: expiresAt,
attempts: 0
};
// 4. Send the PLAIN TEXT OTP via SMS
// Customize the message clearly! Include your App/Brand Name.
const message = `Your YourAppName verification code is ${otp}. It expires in ${OTP_EXPIRY_MINUTES} mins. Do not share this code.`;
// Ensure phone number is in international format if required by gateway
await sendSMS(phoneNumber, message); // Assuming sendSMS handles async and errors
console.log(`OTP generated for ${phoneNumber} (expires: ${new Date(expiresAt).toLocaleTimeString()})`);
return { success: true };
} catch (error) {
console.error(`Error generating/sending OTP for ${phoneNumber}:`, error);
// Handle specific errors from hashing or SMS sending (e.g., gateway API error, invalid number format)
return { success: false, error: "Failed to send OTP. Please try again later." };
}
}
async function validateOTP(phoneNumber, userInputOtp) {
const record = otpStore[phoneNumber]; // !! Retrieve from Redis/DB in production !!
const MAX_ATTEMPTS = 3;
// Basic checks
if (!record) {
console.warn(`Validation attempt for non-existent/invalidated OTP record: ${phoneNumber}`);
// Return generic error to user
return { valid: false, message: "Invalid or expired code." };
}
// Check expiry FIRST
if (Date.now() > record.expiresAt) {
console.warn(`Validation attempt for expired OTP: ${phoneNumber}`);
// Clean up expired record (optional, depends on storage mechanism)
delete otpStore[phoneNumber]; // Or let Redis TTL handle it / mark as expired in DB
return { valid: false, message: "Invalid or expired code." };
}
// Check attempts
if (record.attempts >= MAX_ATTEMPTS) {
console.warn(`Validation attempt exceeding max tries: ${phoneNumber}`);
// Optionally lock out OTP requests for this number for a short period
return { valid: false, message: "Too many attempts. Please request a new code." };
}
// Increment attempt count BEFORE comparison
// !! In production: Update this atomically in your store !!
record.attempts++;
// otpStore[phoneNumber] = record; // Update the local demo store
try {
// Compare user input (hashed) with stored hash
const isValid = await bcrypt.compare(userInputOtp, record.hash);
if (isValid) {
console.log(`OTP validation successful for ${phoneNumber}`);
// IMPORTANT: Invalidate the OTP immediately after successful validation to prevent reuse
delete otpStore[phoneNumber]; // !! Delete from Redis/DB or mark as used in production !!
return { valid: true, message: "Verification successful." };
} else {
console.warn(`Invalid OTP entered for ${phoneNumber}. Attempt ${record.attempts}/${MAX_ATTEMPTS}`);
// Update the attempt count in the store here in production
// e.g., await redisClient.hIncrBy(phoneNumber, 'attempts', 1);
return { valid: false, message: "Invalid or expired code." };
}
} catch (error) {
console.error(`Error during OTP validation hash comparison for ${phoneNumber}:`, error);
// Avoid leaking internal errors
return { valid: false, message: "An error occurred during validation." };
}
}
// --- Example Usage (Conceptual - NOT for direct execution here) ---
/*
// User requests OTP:
generateAndSendOTP('+23480xxxxxxxx')
.then(result => console.log('OTP Send Result:', result))
.catch(err => console.error('OTP Send Failed:', err));
// User submits OTP '123456':
validateOTP('+23480xxxxxxxx', '123456')
.then(result => console.log('OTP Validation Result:', result))
.catch(err => console.error('OTP Validation Failed:', err));
*/
When Should You Use SMS OTP?
SMS OTP is a reasonable choice when:
You primarily need to verify phone number ownership.
Your target audience has wide access to basic mobile phones but may lack consistent internet access or smartphones needed for authenticator apps (still relevant in some parts of Nigeria, though smartphone penetration is high). It's used as one factor in a multi-factor strategy, not the only high-security factor. Cost and user familiarity outweigh the need for the highest level of security for a specific low-risk action.
Avoid relying solely on SMS OTP for:
Protecting extremely high-value accounts or transactions (e.g., core banking actions, large fund transfers).
Applications where users are known targets for sophisticated attacks like SIM swapping. Situations requiring the highest level of authentication assurance (compliance standards might dictate stronger methods).
Stronger Alternatives to SMS OTP
Consider these more secure methods, especially for sensitive applications:
TOTP (Time-based One-Time Passwords): Generated by authenticator apps (Google Authenticator, Authy, Microsoft Authenticator, etc.) on the user's device. Not vulnerable to SMS interception or SIM swap. Requires users to install an app. Generally very secure.
Push-based Authentication: The service sends a push notification to a registered mobile app (e.g., your banking app). The user taps "Approve" or "Deny" directly in the app, often with contextual information (like location, action type). More user-friendly and uses a more secure channel than SMS.
Email OTPs: Similar mechanism to SMS OTP but uses email. Can be useful if users don't have or want to share phone numbers, but email accounts can also be compromised. Often considered slightly less secure than TOTP or Push for authentication, but better than just a password.
Conclusion
SMS OTP remains a relevant and practical tool for specific use cases in Nigeria and globally, particularly for phone number verification and providing a familiar 2FA option where app-based methods aren't feasible for the entire user base. However, its inherent security weaknesses (SIM swap, SS7 vulnerabilities, phishing risks, delivery uncertainties) mean it should not be treated as a high-security guarantee.
When implementing SMS OTP, prioritize security best practices: use secure generation, hash stored codes, enforce strict time limits and rate limiting, choose reliable local/international gateways, monitor activity, and educate your users. Always evaluate whether more robust alternatives like TOTP, Push Authentication, or Passkeys are a better fit for your application's security requirements and risk profile. Balance convenience with a realistic assessment of the risks involved.




























![[Free Webinar] Guide to Securing Your Entire Identity Lifecycle Against AI-Powered Threats](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjqbZf4bsDp6ei3fmQ8swm7GB5XoRrhZSFE7ZNhRLFO49KlmdgpIDCZWMSv7rydpEShIrNb9crnH5p6mFZbURzO5HC9I4RlzJazBBw5aHOTmI38sqiZIWPldRqut4bTgegipjOk5VgktVOwCKF_ncLeBX-pMTO_GMVMfbzZbf8eAj21V04y_NiOaSApGkM/s1600/webinar-play.jpg?#)








































































































































![[The AI Show Episode 145]: OpenAI Releases o3 and o4-mini, AI Is Causing “Quiet Layoffs,” Executive Order on Youth AI Education & GPT-4o’s Controversial Update](https://www.marketingaiinstitute.com/hubfs/ep%20145%20cover.png)












































































































































































































































_XFkvNLu.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)

























_Tanapong_Sungkaew_via_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)











































































































![Apple Restructures Global Affairs and Apple Music Teams [Report]](https://www.iclarified.com/images/news/97162/97162/97162-640.jpg)
![New iPhone Factory Goes Live in India, Another Just Days Away [Report]](https://www.iclarified.com/images/news/97165/97165/97165-640.jpg)