Introduction to access control model: ACL, RBAC, ABAC
Access Control Models: ACL, RBAC, ABAC In system design, access control is a critical mechanism to ensure data security and correct authorization of functionalities. Depending on the complexity of the system, the variety of user roles, and the flexibility needed in resource management, there are three common access control models: ACL (Access Control List), RBAC (Role-Based Access Control), and ABAC (Attribute-Based Access Control). Below is a brief comparison of these three models, outlining their design logic, characteristics, and application scenarios to help clarify the selection and implementation considerations. ACL Direct authorization, fine-grained, but difficult to manage Design Logic: User → Resource + Operation If a user has read and update permissions for the development department's file list, they can view all the data under that department and make changes to it. RBAC Simplified management, clear structure, but limited flexibility Design Logic: Role → Resource + Operation; User is assigned to a role If a user’s role is a department manager, they can perform CRUD operations on all resources within that department. ABAC Highest flexibility, dynamic condition evaluation based on the user's, resource's, and environment's attributes to determine authorization. Some variants include ReBAC (Relationship-Based Access Control), LBAC (Label-Based Access Control). Design Logic: Access is determined based on attributes. If a user’s department attribute is "HR Department," the resource's attribute is "personnel data," and the current time is within working hours, access is granted. Comparison Table Item ACL (Access Control List) RBAC (Role-Based Access Control) ABAC (Attribute-Based Access Control)

Access Control Models: ACL, RBAC, ABAC
In system design, access control is a critical mechanism to ensure data security and correct authorization of functionalities. Depending on the complexity of the system, the variety of user roles, and the flexibility needed in resource management, there are three common access control models: ACL (Access Control List), RBAC (Role-Based Access Control), and ABAC (Attribute-Based Access Control). Below is a brief comparison of these three models, outlining their design logic, characteristics, and application scenarios to help clarify the selection and implementation considerations.
ACL
Direct authorization, fine-grained, but difficult to manage
- Design Logic: User → Resource + Operation
If a user has read and update permissions for the development department's file list, they can view all the data under that department and make changes to it.
RBAC
Simplified management, clear structure, but limited flexibility
- Design Logic: Role → Resource + Operation; User is assigned to a role
If a user’s role is a department manager, they can perform CRUD operations on all resources within that department.
ABAC
Highest flexibility, dynamic condition evaluation based on the user's, resource's, and environment's attributes to determine authorization.
Some variants include ReBAC (Relationship-Based Access Control), LBAC (Label-Based Access Control).
- Design Logic: Access is determined based on attributes.
If a user’s department attribute is "HR Department," the resource's attribute is "personnel data," and the current time is within working hours, access is granted.






































































































































































![[The AI Show Episode 146]: Rise of “AI-First” Companies, AI Job Disruption, GPT-4o Update Gets Rolled Back, How Big Consulting Firms Use AI, and Meta AI App](https://www.marketingaiinstitute.com/hubfs/ep%20146%20cover.png)
















































































































































































.jpg?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)



















































































_Brian_Jackson_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)

_Steven_Jones_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)


 Stolen 884,000 Credit Card Details on 13 Million Clicks from Users Worldwide.webp?#)



















































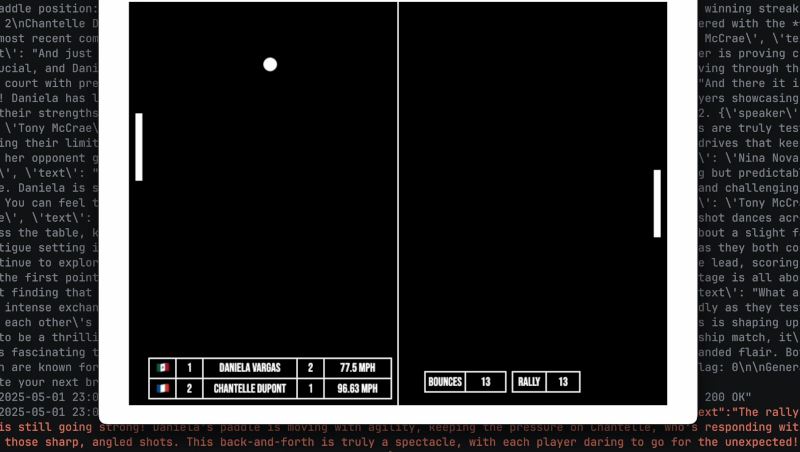








































![Google rolling out Nest Wifi Pro April 2025 update [U]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2022/10/Nest-Wifi-Pro-1.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)












![Apple Seeds visionOS 2.5 RC to Developers [Download]](https://www.iclarified.com/images/news/97240/97240/97240-640.jpg)
![Apple Seeds tvOS 18.5 RC to Developers [Download]](https://www.iclarified.com/images/news/97243/97243/97243-640.jpg)

![Apple Releases macOS Sequoia 15.5 RC to Developers [Download]](https://www.iclarified.com/images/news/97245/97245/97245-640.jpg)