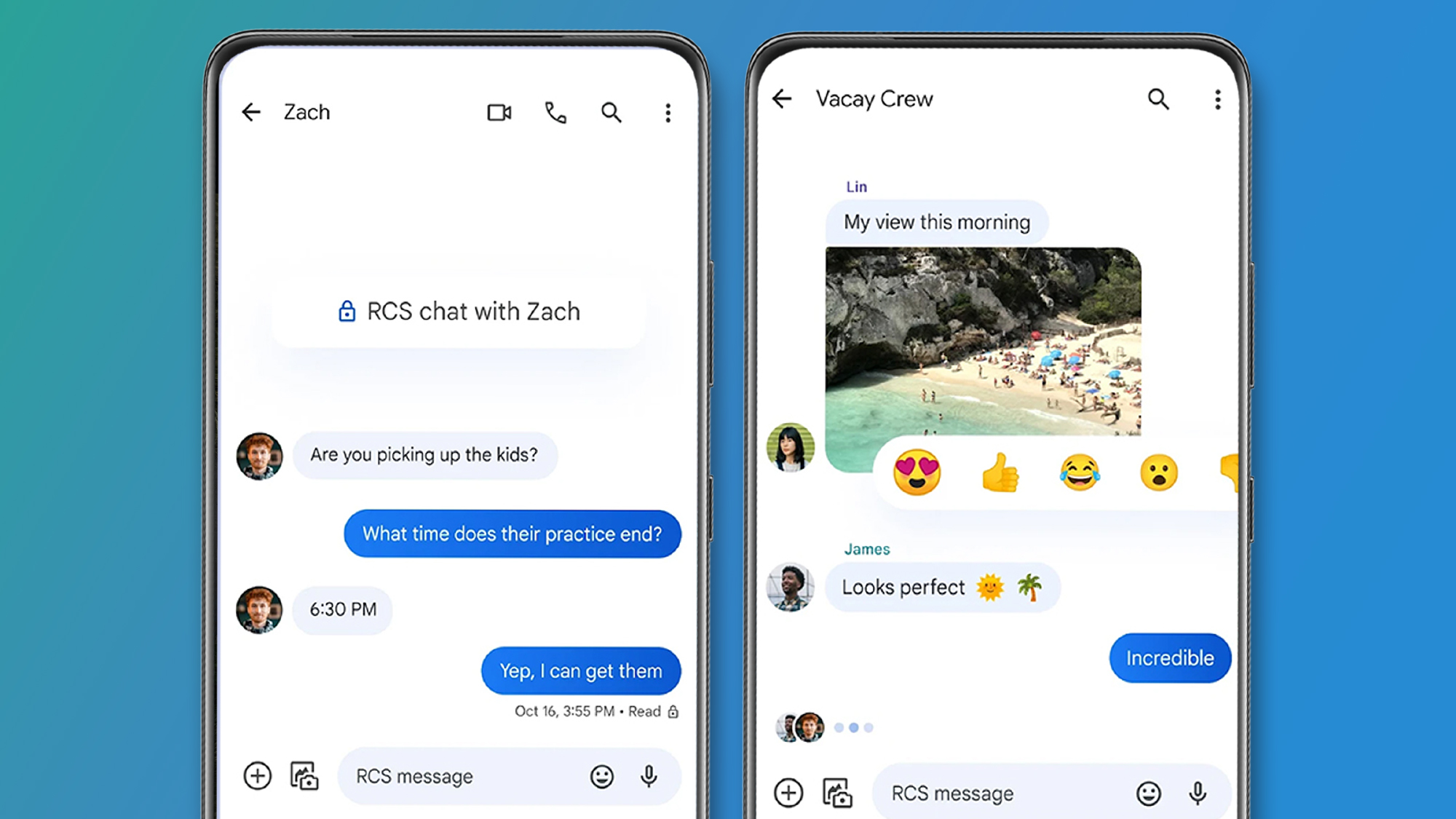
Amazon EKS (Auto Mode) Infrastructure as Code with Terraform
Introduction: Click here: https://dev.to/aws-builders/enable-eks-auto-mode-on-an-existing-cluster-1j5m Terraform Implementation of Amazon EKS Auto Mode locals { cluster_name = "my-vpc-eks-test" } module "vpc_eks" { source = "terraform-aws-modules/vpc/aws" version = "5.18.1" name = "my-vpc-eks-test" cidr = "10.20.0.0/19" azs = ["eu-west-2a", "eu-west-2b", "eu-west-2c"] private_subnets = ["10.20.0.0/21", "10.20.8.0/21", "10.20.16.0/21"] public_subnets = ["10.20.24.0/23", "10.20.26.0/23", "10.20.28.0/23"] enable_nat_gateway = true single_nat_gateway = true one_nat_gateway_per_az = false enable_vpn_gateway = true enable_dns_hostnames = true enable_dns_support = true propagate_private_route_tables_vgw = true propagate_public_route_tables_vgw = true private_subnet_tags = { "kubernetes.io/role/internal-elb" = "1", "mapPublicIpOnLaunch" = "FALSE" "karpenter.sh/discovery" = local.cluster_name "kubernetes.io/role/cni" = "1" } public_subnet_tags = { "kubernetes.io/role/elb" = "1", "mapPublicIpOnLaunch" = "TRUE" } tags = { "kubernetes.io/cluster/${local.cluster_name}" = "shared" } } resource "aws_eks_cluster" "cluster" { name = local.cluster_name role_arn = aws_iam_role.cluster.arn version = "1.32" vpc_config { subnet_ids = module.vpc_eks.private_subnets security_group_ids = [] endpoint_private_access = "true" endpoint_public_access = "true" } access_config { authentication_mode = "API" bootstrap_cluster_creator_admin_permissions = false } bootstrap_self_managed_addons = false zonal_shift_config { enabled = true } compute_config { enabled = true node_pools = ["general-purpose", "system"] node_role_arn = aws_iam_role.node.arn } kubernetes_network_config { elastic_load_balancing { enabled = true } } storage_config { block_storage { enabled = true } } } resource "aws_iam_role" "cluster" { name = "eks-test-cluster-role" assume_role_policy = data.aws_iam_policy_document.cluster_role_assume_role_policy.json } resource "aws_iam_role_policy_attachments_exclusive" "cluster" { role_name = aws_iam_role.cluster.name policy_arns = [ "arn:aws:iam::aws:policy/AmazonEKSClusterPolicy", "arn:aws:iam::aws:policy/AmazonEKSComputePolicy", "arn:aws:iam::aws:policy/AmazonEKSBlockStoragePolicy", "arn:aws:iam::aws:policy/AmazonEKSLoadBalancingPolicy", "arn:aws:iam::aws:policy/AmazonEKSNetworkingPolicy", "arn:aws:iam::aws:policy/AmazonEKSServicePolicy", "arn:aws:iam::aws:policy/AmazonEKSVPCResourceController" ] } data "aws_iam_policy_document" "cluster_role_assume_role_policy" { statement { actions = ["sts:AssumeRole", "sts:TagSession"] principals { type = "Service" identifiers = ["eks.amazonaws.com"] } } } resource "aws_iam_role" "node" { name = "eks-auto-node-example" assume_role_policy = jsonencode({ Version = "2012-10-17" Statement = [ { Action = ["sts:AssumeRole"] Effect = "Allow" Principal = { Service = "ec2.amazonaws.com" } }, ] }) } resource "aws_iam_role_policy_attachment" "node_AmazonEKSWorkerNodeMinimalPolicy" { policy_arn = "arn:aws:iam::aws:policy/AmazonEKSWorkerNodeMinimalPolicy" role = aws_iam_role.node.name } resource "aws_iam_role_policy_attachment" "node_AmazonEC2ContainerRegistryPullOnly" { policy_arn = "arn:aws:iam::aws:policy/AmazonEC2ContainerRegistryPullOnly" role = aws_iam_role.node.name } Ref: https://github.com/terraform-aws-modules/terraform-aws-eks/blob/v20.36.0/examples/eks-auto-mode/main.tf

Introduction:
Click here: https://dev.to/aws-builders/enable-eks-auto-mode-on-an-existing-cluster-1j5m
Terraform Implementation of Amazon EKS Auto Mode
locals {
cluster_name = "my-vpc-eks-test"
}
module "vpc_eks" {
source = "terraform-aws-modules/vpc/aws"
version = "5.18.1"
name = "my-vpc-eks-test"
cidr = "10.20.0.0/19"
azs = ["eu-west-2a", "eu-west-2b", "eu-west-2c"]
private_subnets = ["10.20.0.0/21", "10.20.8.0/21", "10.20.16.0/21"]
public_subnets = ["10.20.24.0/23", "10.20.26.0/23", "10.20.28.0/23"]
enable_nat_gateway = true
single_nat_gateway = true
one_nat_gateway_per_az = false
enable_vpn_gateway = true
enable_dns_hostnames = true
enable_dns_support = true
propagate_private_route_tables_vgw = true
propagate_public_route_tables_vgw = true
private_subnet_tags = {
"kubernetes.io/role/internal-elb" = "1",
"mapPublicIpOnLaunch" = "FALSE"
"karpenter.sh/discovery" = local.cluster_name
"kubernetes.io/role/cni" = "1"
}
public_subnet_tags = {
"kubernetes.io/role/elb" = "1",
"mapPublicIpOnLaunch" = "TRUE"
}
tags = {
"kubernetes.io/cluster/${local.cluster_name}" = "shared"
}
}
resource "aws_eks_cluster" "cluster" {
name = local.cluster_name
role_arn = aws_iam_role.cluster.arn
version = "1.32"
vpc_config {
subnet_ids = module.vpc_eks.private_subnets
security_group_ids = []
endpoint_private_access = "true"
endpoint_public_access = "true"
}
access_config {
authentication_mode = "API"
bootstrap_cluster_creator_admin_permissions = false
}
bootstrap_self_managed_addons = false
zonal_shift_config {
enabled = true
}
compute_config {
enabled = true
node_pools = ["general-purpose", "system"]
node_role_arn = aws_iam_role.node.arn
}
kubernetes_network_config {
elastic_load_balancing {
enabled = true
}
}
storage_config {
block_storage {
enabled = true
}
}
}
resource "aws_iam_role" "cluster" {
name = "eks-test-cluster-role"
assume_role_policy = data.aws_iam_policy_document.cluster_role_assume_role_policy.json
}
resource "aws_iam_role_policy_attachments_exclusive" "cluster" {
role_name = aws_iam_role.cluster.name
policy_arns = [
"arn:aws:iam::aws:policy/AmazonEKSClusterPolicy",
"arn:aws:iam::aws:policy/AmazonEKSComputePolicy",
"arn:aws:iam::aws:policy/AmazonEKSBlockStoragePolicy",
"arn:aws:iam::aws:policy/AmazonEKSLoadBalancingPolicy",
"arn:aws:iam::aws:policy/AmazonEKSNetworkingPolicy",
"arn:aws:iam::aws:policy/AmazonEKSServicePolicy",
"arn:aws:iam::aws:policy/AmazonEKSVPCResourceController"
]
}
data "aws_iam_policy_document" "cluster_role_assume_role_policy" {
statement {
actions = ["sts:AssumeRole", "sts:TagSession"]
principals {
type = "Service"
identifiers = ["eks.amazonaws.com"]
}
}
}
resource "aws_iam_role" "node" {
name = "eks-auto-node-example"
assume_role_policy = jsonencode({
Version = "2012-10-17"
Statement = [
{
Action = ["sts:AssumeRole"]
Effect = "Allow"
Principal = {
Service = "ec2.amazonaws.com"
}
},
]
})
}
resource "aws_iam_role_policy_attachment" "node_AmazonEKSWorkerNodeMinimalPolicy" {
policy_arn = "arn:aws:iam::aws:policy/AmazonEKSWorkerNodeMinimalPolicy"
role = aws_iam_role.node.name
}
resource "aws_iam_role_policy_attachment" "node_AmazonEC2ContainerRegistryPullOnly" {
policy_arn = "arn:aws:iam::aws:policy/AmazonEC2ContainerRegistryPullOnly"
role = aws_iam_role.node.name
}





































































































































































![[The AI Show Episode 145]: OpenAI Releases o3 and o4-mini, AI Is Causing “Quiet Layoffs,” Executive Order on Youth AI Education & GPT-4o’s Controversial Update](https://www.marketingaiinstitute.com/hubfs/ep%20145%20cover.png)
























































































































![Ditching a Microsoft Job to Enter Startup Purgatory with Lonewolf Engineer Sam Crombie [Podcast #171]](https://cdn.hashnode.com/res/hashnode/image/upload/v1746753508177/0cd57f66-fdb0-4972-b285-1443a7db39fc.png?#)
































































































































_Piotr_Adamowicz_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)

_designer491_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)












































































-xl-xl-xl.jpg)

























![Apple Officially Releases macOS Sequoia 15.5 [Download]](https://www.iclarified.com/images/news/97308/97308/97308-640.jpg)