Cybersecurity Indicators: How IOCs, IOBs, and IOAs Empower Threat Detection & Prevention
In Cybersecurity indicators, three powerful tools Indicators of Compromise (IOCs), Indicators of Behavior (IOBs), and Indicators of Attack (IOAs) are helping organizations detect threats early and respond more effectively. These indicators offer crucial insights into malicious activity, empowering security teams to better protect their systems before damage is done. A recent deep dive by ANY.RUN, […] The post Cybersecurity Indicators: How IOCs, IOBs, and IOAs Empower Threat Detection & Prevention appeared first on Cyber Security News.

In Cybersecurity indicators, three powerful tools Indicators of Compromise (IOCs), Indicators of Behavior (IOBs), and Indicators of Attack (IOAs) are helping organizations detect threats early and respond more effectively.
These indicators offer crucial insights into malicious activity, empowering security teams to better protect their systems before damage is done.
A recent deep dive by ANY.RUN, a leading cybersecurity platform, highlights how these indicators work together to safeguard systems and networks from malicious actors.
Understanding the Trio: IOCs, IOBs, and IOAs
Each indicator plays a distinct role in the fight against cybercrime, offering unique insights into threats at different stages of an attack.
Indicators of Compromise (IOCs):
These are forensic breadcrumbs evidence like malicious file hashes, suspicious IP addresses, or unauthorized system changes—that signal a system has already been breached.
IOCs are reactive, helping security teams confirm incidents and trace attack paths.
For instance, a phishing domain from a prior attack can be blacklisted to prevent future access, as demonstrated by ANY.RUN’s Threat Intelligence Lookup, which flagged the IP “147.185.221.26” as linked to known malware.

“Another way of using IOCs for proactive protection is setting up decoys (honeypots or honeytokens) to monitor access to known indicators or infrastructure that mimics IOC traits”. ANY.RUN said.
Indicators of Behavior (IOBs):
IOBs shift the focus to proactive detection by analyzing patterns of suspicious activity, such as unusual login times or encrypted traffic spikes.
Unlike IOCs, IOBs target attacker tactics, techniques, and procedures (TTPs), making them effective against zero-day or evolving threats.
“This enables them to be used for detecting zero-day attacks, unknown or evolving threats that may not have specific IOCs which makes IOBs useful in proactive threat hunting and monitoring. Suspicious behavior can signal an attack in progress, before significant damage occurs.”
ANY.RUN’s Interactive Sandbox recently uncovered a phishing campaign by Storm-1865, where fake CAPTCHA pages tricked users into executing malicious commands via mshta.exe, showcasing IOBs’ power to spot real-time threats.

Indicators of Attack (IOAs):
IOAs take a strategic approach, focusing on the “how” and “why” of an attack to catch adversaries early in the kill chain.
What typical indicators of attack might look like:
- Word document spawns PowerShell;
- Process injection detected;
- A user logs in from two geographies within minutes;
- Suspicious lateral movement.
“Since IOAs are specific signs of an active or imminent attack, often tied to known TTPs or malicious artifacts, it is possible to research these indicators with the aid of ANY.RUN’s Threat Intelligence Lookup through the Interactive MITRE ATT&CK Matrix.”

From port scanning to credential theft, IOAs map adversary TTPs to frameworks like MITRE ATT&CK, enabling teams to interrupt attacks during reconnaissance or lateral movement. ANY.RUN’s Interactive MITRE ATT&CK Matrix helps analysts visualize these behaviors and link them to real malware samples.
Boost threat detection with ANY.RUN’s TI Feeds Get continuous stream of malicious IOCs from the latest attacks on 15,000+ companies. Try Free Demo.
Turning Indicators into Action
The true strength of these indicators lies in their ability to transform raw data into actionable defenses. IOCs, shared via threat intelligence feeds in formats like STIX and MISP, allow security operations centers (SOCs) to block known threats proactively.
For example, ANY.RUN’s TI Feeds deliver real-time IOCs from 15,000+ organizations, helping teams stay ahead of emerging malware.
IOBs, meanwhile, leverage advanced analytics like machine learning to detect anomalies, though they require robust tools like SIEM or UEBA to minimize false positives.
A recent ANY.RUN analysis revealed how seemingly benign mutexes, like “PackageManager” and “DocumentUpdater,” were tied to Iran’s MuddyWater APT group, underscoring the need for contextual analysis to avoid missteps.
IOAs empower proactive threat hunting by identifying attack patterns, such as process injection or suspicious PowerShell activity, enabling teams to disrupt threats before they escalate.
ANY.RUN’s TI Lookup and Interactive Sandbox provide a sandboxed environment to observe these behaviors safely, offering insights into campaigns like those distributing XWorm and Lumma Stealer.
Despite their strengths, these indicators have limitations. IOCs can become obsolete as attackers swap out domains or hashes, and their effectiveness hinges on fresh, contextual data.
IOBs demand significant resources for behavioral analysis and risk false positives when legitimate actions mimic malicious ones. IOAs, while strategic, require sophisticated tools and expertise to map TTPs accurately.
The ANY.RUN Advantage
ANY.RUN’s suite of tools, including its Interactive Sandbox, TI Lookup, and TI Feeds, equips over 500,000 cybersecurity professionals and 15,000 organizations with the means to harness IOCs, IOBs, and IOAs effectively.
By integrating real-time threat intelligence and behavioral analysis, ANY.RUN helps SOCs prevent financial losses, operational disruptions, and reputational damage.
As cyber threats grow more sophisticated, leveraging IOCs, IOBs, and IOAs is no longer optional it’s essential.
Cybersecurity teams are urged to adopt comprehensive threat intelligence solutions like ANY.RUN to stay one step ahead of adversaries.
For more details or to explore ANY.RUN’s services, try a demo of their Threat Intelligence suite.
The post Cybersecurity Indicators: How IOCs, IOBs, and IOAs Empower Threat Detection & Prevention appeared first on Cyber Security News.
.jpg)








































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)





















































































































































![BPMN-procesmodellering [closed]](https://i.sstatic.net/l7l8q49F.png)

























































































-All-will-be-revealed-00-35-05.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)
-All-will-be-revealed-00-17-36.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)
-Jack-Black---Steve's-Lava-Chicken-(Official-Music-Video)-A-Minecraft-Movie-Soundtrack-WaterTower-00-00-32_lMoQ1fI.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)























_Weyo_alamy.png?width=1280&auto=webp&quality=80&disable=upscale#)
_Brain_light_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)









































































































![Apple Releases Public Beta 2 of iOS 18.5, iPadOS 18.5, macOS Sequoia 15.5 [Download]](https://www.iclarified.com/images/news/97094/97094/97094-640.jpg)

![New M4 MacBook Air On Sale for $929 [Lowest Price Ever]](https://www.iclarified.com/images/news/97090/97090/97090-1280.jpg)
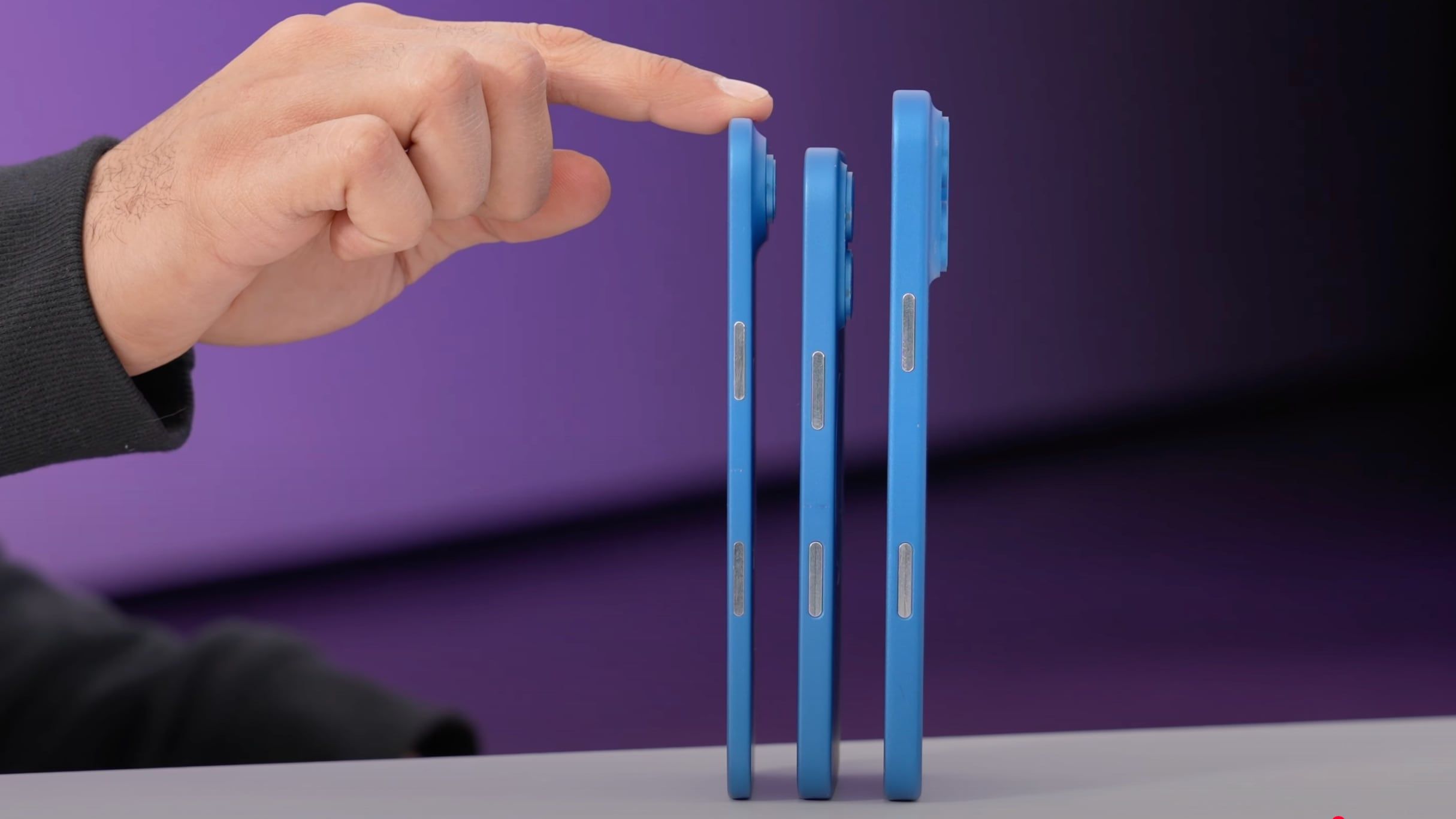
![Apple iPhone 17 Pro May Come in 'Sky Blue' Color [Rumor]](https://www.iclarified.com/images/news/97088/97088/97088-640.jpg)