If You Can't Control Access, You Can't Control the Cloud (Part 2)
Have you had any moment when someone says "I can't see this file" or worse, "Who deleted our project folder?" These aren't glitches, they're permission problems that plague cloud environments daily. Access control isn't about playing digital bouncer. It's about protecting your cloud resources like a vault while keeping operations flowing smoothly for everyone who needs access. In cloud environments, visibility without proper control isn't just inefficient, it's a security disaster waiting to happen. Welcome to Part 2 of our series, where we dive into the real powerhouse of permissions management: ACLs (Access Control Lists). Think of them as personalized VIP passes that determine who can do what with your directories and files. You've got the keys to your cloud kingdom, now let's make sure you're distributing them to the right people, for the right reasons, with the right limitations. Index What are ACLs? How to Grant Access Using ACL How to Check Existing ACL Permissions How to Remove Access from a User How to Wipe All ACLs Clean Granting Access to a Whole Group Revoking Group Permissions Summary: Taking Control of Your Cloud 1. What Are ACLs? ACL stands for Access Control List. It's a more flexible permission management system compared to traditional Linux owner/group/others permissions. ACLs allow you to assign specific access rights to multiple users and groups individually. Okay, to understand this better picture this... Your DevOps team needs to manage CI/CD pipelines while your Security team needs to audit them without making changes. Traditional permissions would force you to choose between oversharing or creating complex group structures. With ACLs, you grant write access to DevOps and read-only access to Security for the same directories. Simple and secure!. Let's imagine the finance department in your company stores quarterly reports in a cloud folder. Executives need read access, the Finance team needs full access, and Audit needs temporary access during compliance reviews. ACLs let you maintain one source of truth with precisely tailored permissions, eliminating risky file duplication or overprivileged users. From this image, we should be able to tell when our ACL is active or not. 2. How to Grant Access Using ACL setfacl -m u:: This command adds specific permissions (r for read, w for write, x for execute) for an individual user. Wait until the next point so we can view the ACL permissions we set. In the mean time imagine a database specialist needs temporary access to troubleshoot performance issues on your production servers. Rather than adding them to the privileged sysadmin group, you grant them targeted read and execute permissions to specific diagnostic directories with setfacl -m u:dbspecialist:rx /var/log/performance. They get exactly what they need without excessive privileges. Your company also just brought in a consultant to help optimize your digital marketing strategy. They need to analyze past campaign data but shouldn't access financial details or customer PII. With a simple ACL command, you grant them read-only access to just the marketing analytics folder maintaining security while enabling their work. 3. How to Check Existing ACL Permissions getfacl This command reveals exactly who has access and what permissions they hold for a specific directory. In this example I used two users and since oluwadamilola is the owner, I gave ade ACL permission also. So you can better understand how this ACL permissions work. Okay now, imagine you're troubleshooting a deployment failure at work, where a service can't write to a log directory. Instead of making broad permission changes, you use getfacl to discover that the service account has read but not write permissions. One targeted fix later, and you've solved the problem without creating security gaps. Now before sharing sensitive customer data with your marketing team for a campaign, your Data Protection Officer needs to verify current access permissions. Running getfacl on the directory provides documentation for compliance purposes and confirms that only authorized personnel can access the information. 4. How to Remove Access from a User setfacl -x u: This command cleanly revokes a specific user's direct ACL permissions. Think of this use case, a systems engineer is moving to a different team and no longer needs access to the infrastructure monitoring system. Instead of combing through group memberships, you directly remove their ACL permissions with setfacl -x u:engineer123 /opt/monitoring. Their access is instantly revoked while team workflows continue uninterrupted. Also assuming your contract with an external agency has ended. Their team had access to your brand assets during the project. Using ACL removal, you quickly terminate their access without disrupting permissions for internal teams who still need the

Have you had any moment when someone says "I can't see this file" or worse, "Who deleted our project folder?" These aren't glitches, they're permission problems that plague cloud environments daily.
Access control isn't about playing digital bouncer. It's about protecting your cloud resources like a vault while keeping operations flowing smoothly for everyone who needs access. In cloud environments, visibility without proper control isn't just inefficient, it's a security disaster waiting to happen.
Welcome to Part 2 of our series, where we dive into the real powerhouse of permissions management: ACLs (Access Control Lists). Think of them as personalized VIP passes that determine who can do what with your directories and files. You've got the keys to your cloud kingdom, now let's make sure you're distributing them to the right people, for the right reasons, with the right limitations.
Index
- What are ACLs?
- How to Grant Access Using ACL
- How to Check Existing ACL Permissions
- How to Remove Access from a User
- How to Wipe All ACLs Clean
- Granting Access to a Whole Group
- Revoking Group Permissions
- Summary: Taking Control of Your Cloud
1. What Are ACLs?
ACL stands for Access Control List. It's a more flexible permission management system compared to traditional Linux owner/group/others permissions. ACLs allow you to assign specific access rights to multiple users and groups individually. Okay, to understand this better picture this...
Your DevOps team needs to manage CI/CD pipelines while your Security team needs to audit them without making changes. Traditional permissions would force you to choose between oversharing or creating complex group structures. With ACLs, you grant write access to DevOps and read-only access to Security for the same directories. Simple and secure!.
Let's imagine the finance department in your company stores quarterly reports in a cloud folder. Executives need read access, the Finance team needs full access, and Audit needs temporary access during compliance reviews. ACLs let you maintain one source of truth with precisely tailored permissions, eliminating risky file duplication or overprivileged users.
From this image, we should be able to tell when our ACL is active or not.
2. How to Grant Access Using ACL
setfacl -m u::
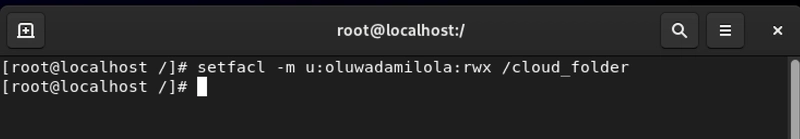
This command adds specific permissions (r for read, w for write, x for execute) for an individual user.
Wait until the next point so we can view the ACL permissions we set.
In the mean time imagine a database specialist needs temporary access to troubleshoot performance issues on your production servers. Rather than adding them to the privileged sysadmin group, you grant them targeted read and execute permissions to specific diagnostic directories with setfacl -m u:dbspecialist:rx /var/log/performance. They get exactly what they need without excessive privileges.
Your company also just brought in a consultant to help optimize your digital marketing strategy. They need to analyze past campaign data but shouldn't access financial details or customer PII. With a simple ACL command, you grant them read-only access to just the marketing analytics folder maintaining security while enabling their work.
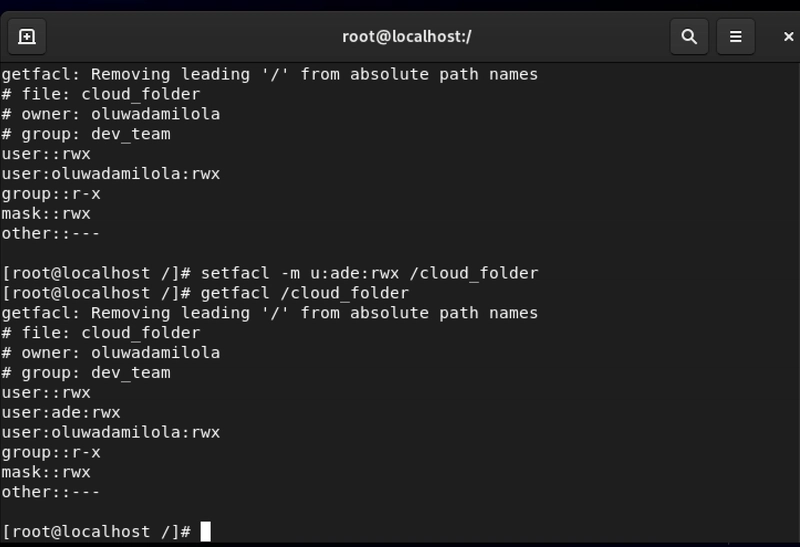
3. How to Check Existing ACL Permissions
getfacl
This command reveals exactly who has access and what permissions they hold for a specific directory.
In this example I used two users and since oluwadamilola is the owner, I gave ade ACL permission also. So you can better understand how this ACL permissions work.
Okay now, imagine you're troubleshooting a deployment failure at work, where a service can't write to a log directory. Instead of making broad permission changes, you use getfacl to discover that the service account has read but not write permissions. One targeted fix later, and you've solved the problem without creating security gaps.
Now before sharing sensitive customer data with your marketing team for a campaign, your Data Protection Officer needs to verify current access permissions. Running getfacl on the directory provides documentation for compliance purposes and confirms that only authorized personnel can access the information.
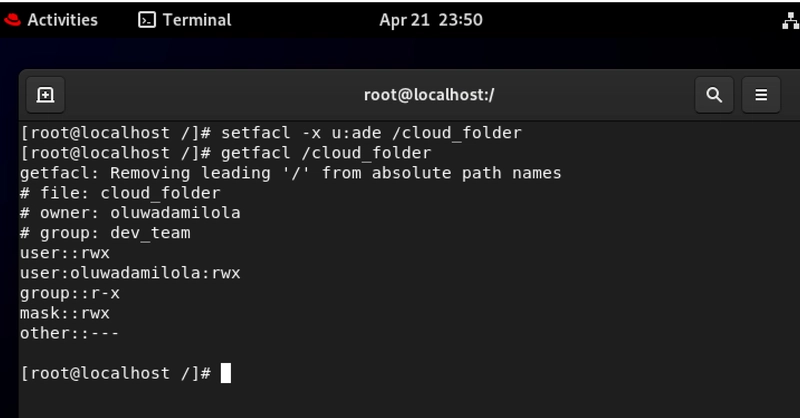
4. How to Remove Access from a User
setfacl -x u:
This command cleanly revokes a specific user's direct ACL permissions.
Think of this use case, a systems engineer is moving to a different team and no longer needs access to the infrastructure monitoring system. Instead of combing through group memberships, you directly remove their ACL permissions with setfacl -x u:engineer123 /opt/monitoring. Their access is instantly revoked while team workflows continue uninterrupted.
Also assuming your contract with an external agency has ended. Their team had access to your brand assets during the project. Using ACL removal, you quickly terminate their access without disrupting permissions for internal teams who still need these resources. Clean offboarding means better security and compliance.
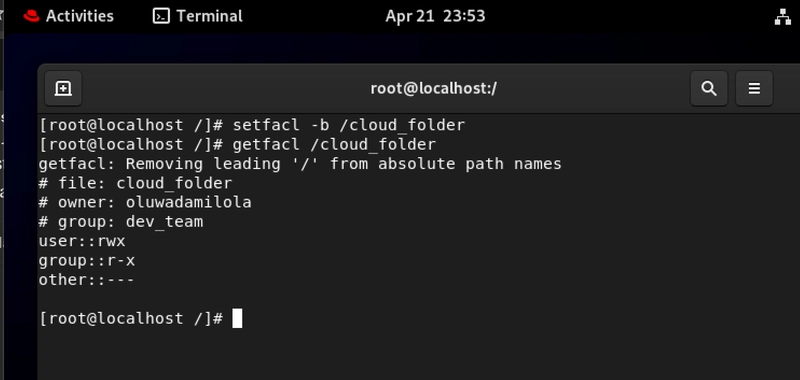
5. How to Wipe All ACLs Clean
setfacl -b
This nuclear option removes all ACL permissions, giving you a clean slate.
Now back to our practical scenarios...
You've inherited a legacy application with years of accumulated, contradicting permission layers. After documenting the current state, you use setfacl -b to clear everything and implement a clean, logical permission structure following least-privilege principles. Your security posture improves dramatically.
Also imagine in your organization, after a corporate merger you discover overlapping teams with inconsistent access to shared resources. Rather than trying to reconcile complex permission structures, you start fresh with setfacl -b on key directories and rebuild permissions based on your new organizational structure and clear data governance policies.
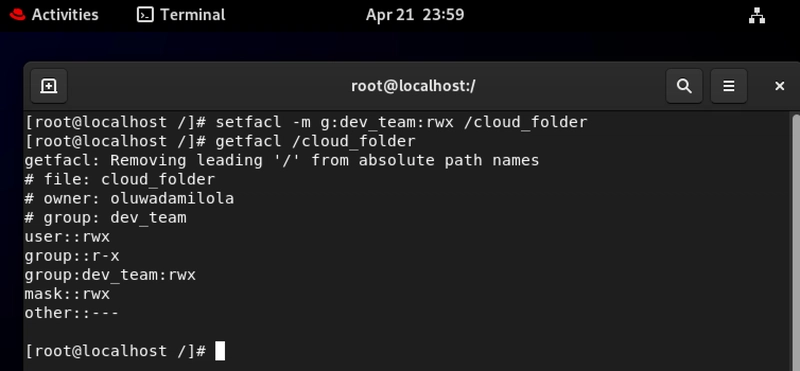
6. Granting Access to a Whole Group
setfacl -m g::
This command grants specified permissions to an entire user group at once.
To better understand this, imagine you're launching a new microservice and need to give your entire development team access to test environments while restricting production access. With setfacl -m g:developers:rwx /srv/test-environments, everyone gets the access they need without individual permission management. When developers come and go, you only need to update group membership.
Or your HR department handles sensitive employee information. Rather than managing permissions for each HR staff member individually, you create an HR group and use setfacl -m g:hr-team:rx /data/employee-records to grant appropriate access. This simplifies onboarding new HR personnel and ensures consistent permissions across the department.
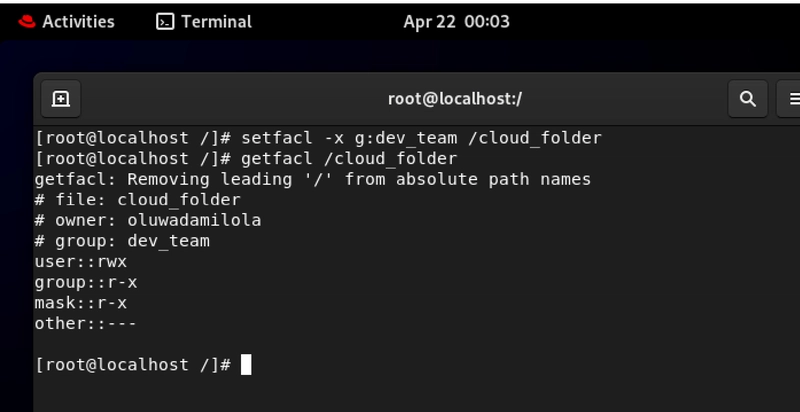
7. Revoking Group Permissions
setfacl -x g:
This command removes access rights from an entire group at once.
For this use case, imagine your company has completed migrating from an old CRM to a new solution. The migration team, which had temporary access to both systems, no longer needs access to the legacy data. With setfacl -x g:migration-team /data/legacy-crm, you instantly revoke access for the entire team, maintaining proper separation of duties.
Also let's imagine, your organization restructures and the Product Innovation team is absorbing the R&D department's responsibilities. Using group-based ACL removal, you revoke the old R&D group's access to innovation pipelines and grant appropriate permissions to the new, combined team. This clean transition prevents orphaned permissions and access confusion.
Summary: Taking Control of Your Cloud
Access control isn't just an IT function, it's a fundamental business capability in the cloud era. With ACLs, you're not just randomly distributing permissions; you're strategically controlling who can see, modify, and execute resources with surgical precision.
The benefits extend beyond security:
- Improved compliance with clear permission trails.
- Reduced risk of accidental data corruption or deletion.
- Better operational efficiency with targeted access.
- Simplified auditing and permission management.
- Enhanced collaboration without compromising security.
Remember in cloud environments, your security is only as strong as your access controls. When you master ACLs, you're not just managing permissions, you're actively controlling your cloud destiny.
The difference between a secure, well-managed cloud and a chaotic one often comes down to this simple truth: If you can't control access, you can't control the cloud.
Stay tuned for Part 3, where we'll explore special permissions.
If you enjoyed reading or learnt from this follow me, comment and connect with me on LinkedIn
#30DaysLinuxChallenge #CloudWhistler #RedHat #Cloudsecurity #DevOps #Linux #OpenSource #CloudComputing #Womenwhobuild #RedHatEnterpriseLinux #ACLpermissions #EnterpriseIT #Ansible #OpenShift #SysAdmin #Automation #CloudEngineer










































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)
































































































































![From fast food worker to cybersecurity engineer with Tae'lur Alexis [Podcast #169]](https://cdn.hashnode.com/res/hashnode/image/upload/v1745242807605/8a6cf71c-144f-4c91-9532-62d7c92c0f65.png?#)























![BPMN-procesmodellering [closed]](https://i.sstatic.net/l7l8q49F.png)
























-Jack-Black---Steve's-Lava-Chicken-(Official-Music-Video)-A-Minecraft-Movie-Soundtrack-WaterTower-00-00-32_lMoQ1fI.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)

























































































_Brain_light_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)
















































































































![Mac Shipments Up 17% in Q1 2025 Fueled by New M4 MacBook Air [Chart]](https://www.iclarified.com/images/news/97086/97086/97086-640.jpg)
![Next Generation iPhone 17e Nears Trial Production [Rumor]](https://www.iclarified.com/images/news/97083/97083/97083-640.jpg)
![Apple Releases iOS 18.5 Beta 3 and iPadOS 18.5 Beta 3 [Download]](https://www.iclarified.com/images/news/97076/97076/97076-640.jpg)
![Apple Seeds visionOS 2.5 Beta 3 to Developers [Download]](https://www.iclarified.com/images/news/97077/97077/97077-640.jpg)