Strategic Cybersecurity Budgeting – CISO Best Practices
In today’s rapidly evolving threat landscape, Chief Information Security Officers (CISOs) face the challenge of securing their organizations with finite resources against virtually unlimited threats. Strategic cybersecurity budgeting has emerged as a critical leadership function beyond simple cost allocation. Effective budget management requires balancing competing priorities, justifying investments to executive leadership, and demonstrating tangible security […] The post Strategic Cybersecurity Budgeting – CISO Best Practices appeared first on Cyber Security News.

In today’s rapidly evolving threat landscape, Chief Information Security Officers (CISOs) face the challenge of securing their organizations with finite resources against virtually unlimited threats.
Strategic cybersecurity budgeting has emerged as a critical leadership function beyond simple cost allocation.
Effective budget management requires balancing competing priorities, justifying investments to executive leadership, and demonstrating tangible security improvements.
This balancing act becomes even more complex as organizations accelerate digital transformation initiatives while security teams struggle with talent shortages and expanding attack surfaces.
The following best practices offer CISOs a framework for approaching cybersecurity budget planning with strategic vision rather than merely responding to immediate pressures.
Aligning Cybersecurity Budget with Business Objectives
The most successful CISOs approach budgeting through the lens of business enablement rather than as a standalone technical function. This perspective shift transforms the budget conversation from one about costs to one about business value and risk management.
Security leaders must thoroughly understand their organization’s strategic objectives, growth initiatives, and risk appetite.
By mapping security investments directly to business outcomes, CISOs can make more compelling budget requests that resonate with executive leadership.
For example, rather than requesting funds for “enhanced endpoint protection,” frame the investment in terms of “securing our remote workforce strategy” or “reducing business disruption risks by 40%.”
This alignment transforms security from a cost center to a business enabler, making gaining executive support for critical initiatives easier.
The most effective security budgets balance addressing known vulnerabilities, preparing for emerging threats, and supporting the organization’s innovation agenda.
Strategic Resource Allocation Approaches
Deciding where and how to invest limited security resources requires a methodical approach that balances multiple factors. Consider these key strategies:
- Risk-based prioritization: Implement a formal, documented process for evaluating security initiatives based on risk reduction potential. This approach ensures investments target the most significant organizational threats rather than the most visible or recently publicized vulnerabilities.
- Operational vs. capital expenditure balance: Cloud-based security services offer flexibility and reduced capital requirements but may increase operational expenses. Evaluate your organization’s financial preferences and constraints when determining the right balance between CapEx and OpEx security investments.
- Technology consolidation: Many organizations accumulate security tools over time, creating management complexity and integration challenges. Regularly assess your security technology portfolio for opportunities to consolidate vendors and platforms, potentially reducing licensing costs while improving operational efficiency.
- Automation investments: Identify labor-intensive security processes that could benefit from automation. These investments often deliver substantial ROI by reducing analyst workload while accelerating detection and response capabilities.
- Talent development: Even with optimal technology investments, security effectiveness depends on skilled professionals. Allocate resources for training, certification, and retention initiatives to maximize the value of your human capital.
The most successful security programs maintain funding flexibility, with approximately 70% allocated to foundational capabilities and 30% reserved for responding to emerging threats or organizational changes.
Demonstrating and Communicating Budget Effectiveness
Securing appropriate cybersecurity funding requires more than technical justification it demands effective communication tailored to the organization’s various stakeholders.
CISOs must develop a robust measurement framework that demonstrates the effectiveness of security investments in terms that resonate with business leaders.
Begin by establishing a baseline of your current security posture, using a combination of technical metrics and risk indicators. This baseline lets you quantify improvements over time and connect them directly to specific investments.
When communicating with executive stakeholders, focus on business outcomes rather than technical details.
Translate security improvements into business value through metrics like reduced incident response time, decreased business disruption, improved regulatory compliance posture, or enhanced customer trust.
Regular security briefings should include operational metrics and strategic indicators demonstrating progress toward long-term security objectives.
Remember that different stakeholders have varying concerns board members typically focus on risk governance and reputational impact, while operations leaders prioritize service availability and user experience.
Tailor your budget effectiveness communications accordingly.
- Leading indicators to track: Focus on metrics that provide early warning of security effectiveness, such as vulnerability management cycle time, security control coverage, and security awareness program effectiveness scores.
- Security budget benchmark comparisons: Contextualize your security spending against industry peers and best practices, but emphasize that your organization’s unique risk profile should ultimately determine appropriate investment levels rather than arbitrary industry benchmarks.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!
The post Strategic Cybersecurity Budgeting – CISO Best Practices appeared first on Cyber Security News.
.jpg)








































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)















































































































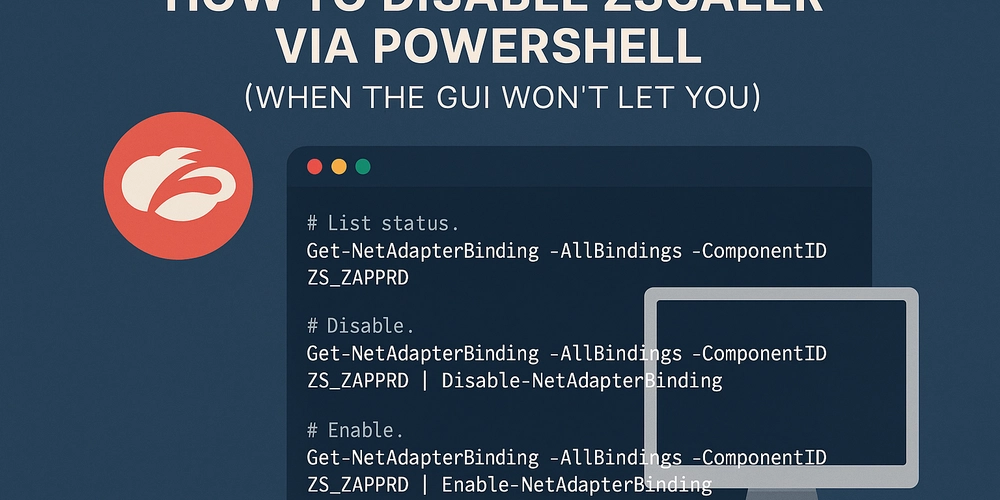

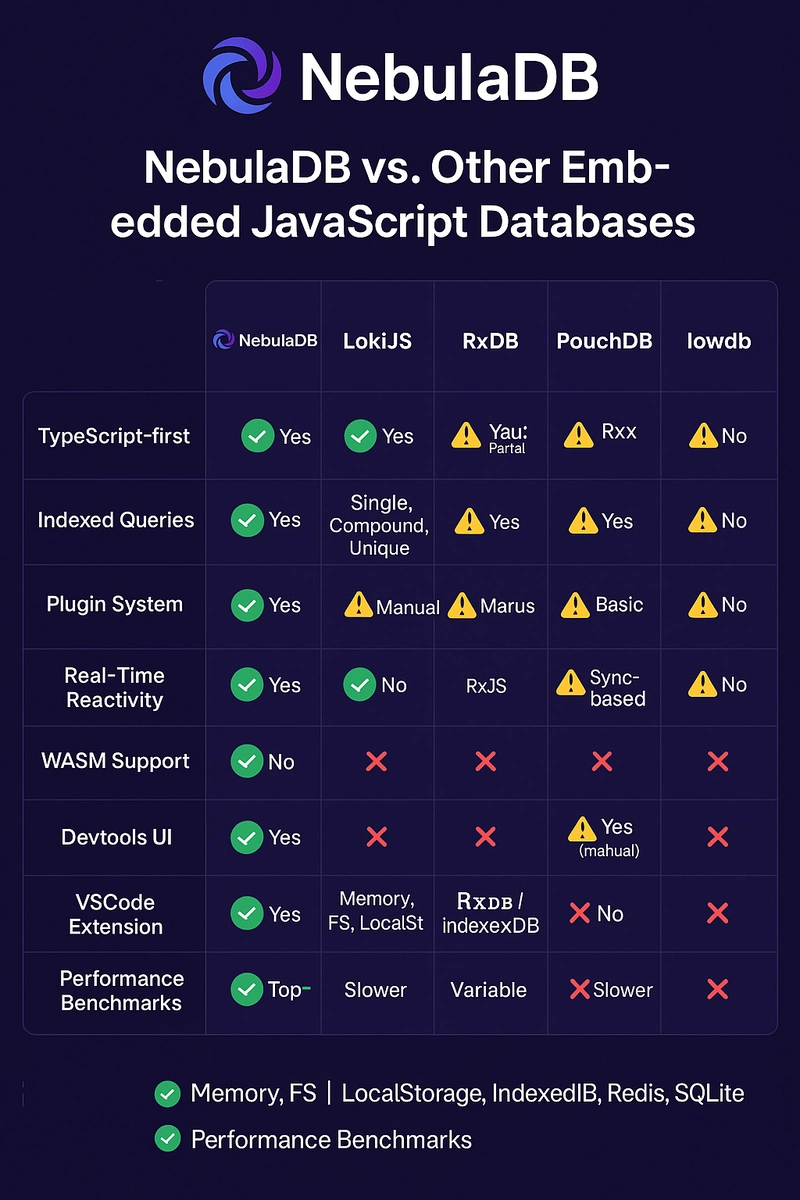





































![BPMN-procesmodellering [closed]](https://i.sstatic.net/l7l8q49F.png)

























































































-All-will-be-revealed-00-35-05.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)
-All-will-be-revealed-00-17-36.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)
-Jack-Black---Steve's-Lava-Chicken-(Official-Music-Video)-A-Minecraft-Movie-Soundtrack-WaterTower-00-00-32_lMoQ1fI.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)












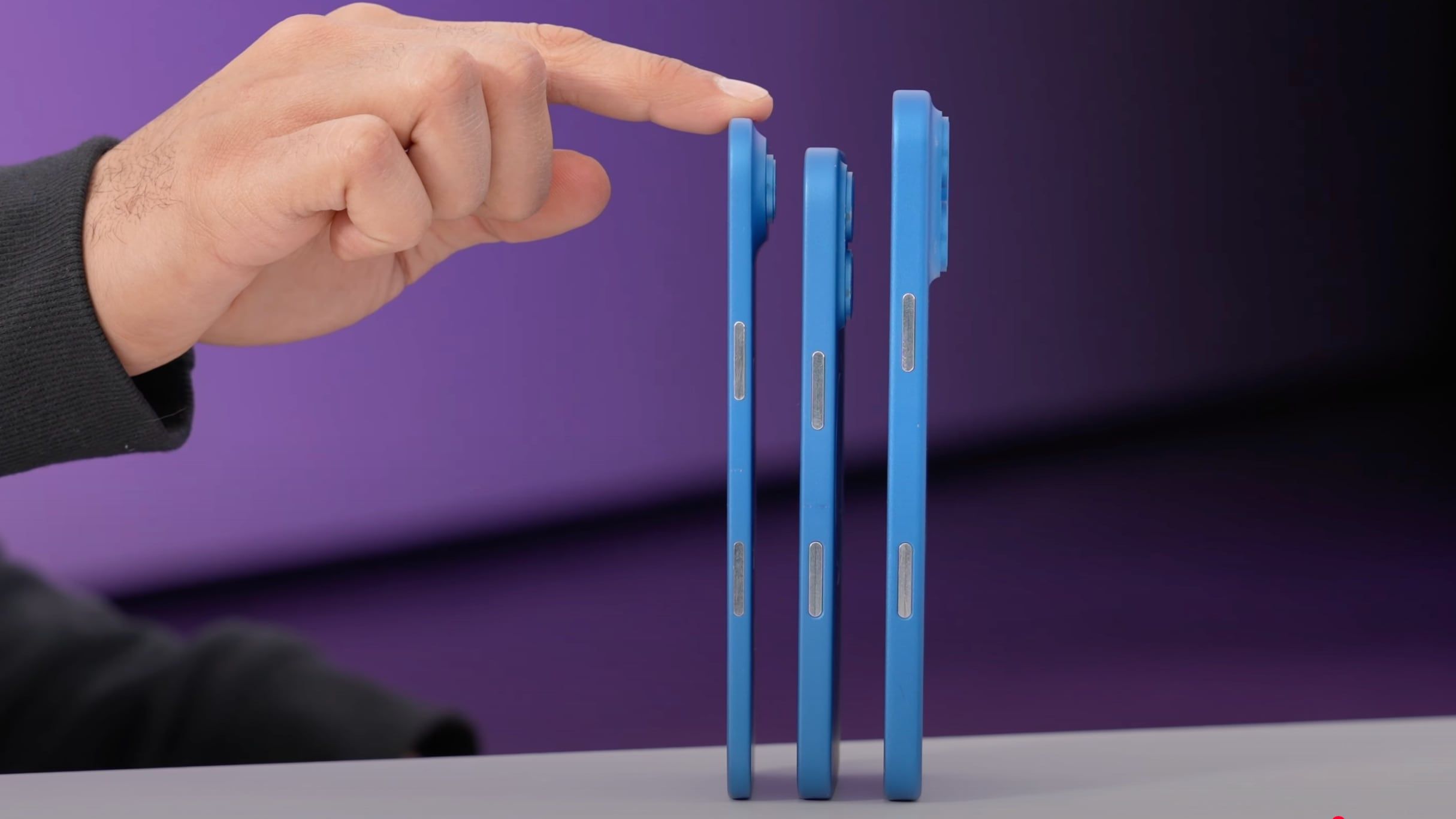











_Weyo_alamy.png?width=1280&auto=webp&quality=80&disable=upscale#)
_Brain_light_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)










































































































![Apple Releases Public Beta 2 of iOS 18.5, iPadOS 18.5, macOS Sequoia 15.5 [Download]](https://www.iclarified.com/images/news/97094/97094/97094-640.jpg)

![New M4 MacBook Air On Sale for $929 [Lowest Price Ever]](https://www.iclarified.com/images/news/97090/97090/97090-1280.jpg)
![Apple iPhone 17 Pro May Come in 'Sky Blue' Color [Rumor]](https://www.iclarified.com/images/news/97088/97088/97088-640.jpg)

























































































































.webp?#)
