CloudFormation Drift Detection and Notification with AWS Config Remediation Action
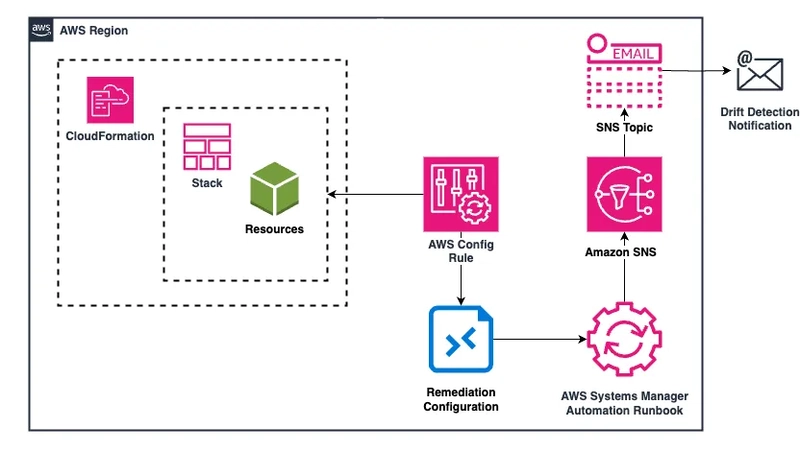
Introduction: CloudFormation stack drift occurs when resources created by a CloudFormation stack are manually changed or deleted. This post explains the process of automatically detecting stack drift using an AWS Config Rule, triggering a Remediation Action with the AWS-PublishSNSNotification Systems Manager automation runbook, and sending notifications via an SNS topic for efficient monitoring and response. About the project: This solution deploys an automated system for monitoring and alerting on CloudFormation stack drift. The core components of the project are: AWS Config Rule: Monitors stacks for drift using the CLOUDFORMATION_STACK_DRIFT_DETECTION_CHECK rule. Remediation Action: Utilizes the AWS-PublishSNSNotification Systems Manager automation runbook to trigger notifications as a remediation step. SNS Notifications: Alerts are sent to a preconfigured endpoint upon drift detection. CloudFormation Templates: Streamline the deployment and configuration of resources. Config Rule and Remediation Action configurations from infrastructure/monitoring_stack.yaml template: Parameters: StackNameToMonitor: Type: String Description: Name of the CloudFormation stack to monitor for drift detection Default: 'base-infrastructure' ConfigRuleName: Type: String Description: Provide the name for the Config rule Default: 'CloudFormationDriftDetection' Resources: IamRoleForConfig: Type: AWS::IAM::Role Properties: RoleName: CloudFormationDriftDetectionRole Description: IAM role for AWS Config to access CloudFormation drift detection AssumeRolePolicyDocument: Version: '2012-10-17' Statement: - Effect: Allow Principal: Service: config.amazonaws.com Action: - sts:AssumeRole ManagedPolicyArns: - arn:aws:iam::aws:policy/ReadOnlyAccess Policies: - PolicyName: CloudFormationDriftDetectionpolicy PolicyDocument: Version: "2012-10-17" Statement: - Effect: Allow Action: - cloudformation:DetectStackResourceDrift - cloudformation:DetectStackDrift - cloudformation:DescribeStacks - cloudformation:DescribeStackResources - cloudformation:BatchDescribeTypeConfigurations - cloudformation:DescribeStackResourceDrifts - cloudformation:DescribeStackDriftDetectionStatus Resource: !Sub "arn:${AWS::Partition}:cloudformation:${AWS::Region}:${AWS::AccountId}:*" ConfigRuleToDetectCfnDrift: Type: AWS::Config::ConfigRule Properties: ConfigRuleName: !Ref ConfigRuleName Description: AWS Config rule to detect drift in CloudFormation stacks Scope: TagKey: stack-name TagValue: !Ref StackNameToMonitor Source: Owner: AWS SourceIdentifier: CLOUDFORMATION_STACK_DRIFT_DETECTION_CHECK MaximumExecutionFrequency: !Ref MaximumExecutionFrequency InputParameters: cloudformationRoleArn: !GetAtt IamRoleForConfig.Arn IamRoleForRemediation: Type: AWS::IAM::Role Properties: RoleName: AwsConfigRemediationAction Description: IAM role for AWS Config remediation action to publish SNS notifications AssumeRolePolicyDocument: Version: '2012-10-17' Statement: - Effect: Allow Principal: Service: - config.amazonaws.com - ssm.amazonaws.com Action: - sts:AssumeRole Policies: - PolicyName: SNSPublishPolicy PolicyDocument: Version: '2012-10-17' Statement: - Effect: Allow Action: - sns:Publish Resource: !Ref SnsTopicToNotifyCfnDriftAlarm RemediationActionForConfigRule: Type: AWS::Config::RemediationConfiguration Properties: ConfigRuleName: !Ref ConfigRuleName TargetType: SSM_DOCUMENT TargetId: AWS-PublishSNSNotification Automatic: true MaximumAutomaticAttempts: 2 RetryAttemptSeconds: 30 Parameters: AutomationAssumeRole: StaticValue: Values: - !GetAtt IamRoleForRemediation.Arn Message: StaticValue: Values: - !Sub | "*** CloudFormation Stack drift detected! ***" "Account: ${AWS::AccountId}" "CloudFormation Stack: ${StackNameToMonitor}" TopicArn: StaticValue: Values: - !Ref SnsTopicToNotifyCfnDriftAlarm Prerequisites: Ensure the following prerequisites are in place: An AWS account with sufficient permissions to create and manage resources. The AWS CLI installed on the local machine. Deployment: 1.Clone the repository. git clone https://gitlab.com
Introduction:
CloudFormation stack drift occurs when resources created by a CloudFormation stack are manually changed or deleted. This post explains the process of automatically detecting stack drift using an AWS Config Rule, triggering a Remediation Action with the AWS-PublishSNSNotification Systems Manager automation runbook, and sending notifications via an SNS topic for efficient monitoring and response.
About the project:
This solution deploys an automated system for monitoring and alerting on CloudFormation stack drift. The core components of the project are:
AWS Config Rule: Monitors stacks for drift using the CLOUDFORMATION_STACK_DRIFT_DETECTION_CHECK rule.
Remediation Action: Utilizes the AWS-PublishSNSNotification Systems Manager automation runbook to trigger notifications as a remediation step.
SNS Notifications: Alerts are sent to a preconfigured endpoint upon drift detection.
CloudFormation Templates: Streamline the deployment and configuration of resources.
Config Rule and Remediation Action configurations from infrastructure/monitoring_stack.yaml template:
Parameters:
StackNameToMonitor:
Type: String
Description: Name of the CloudFormation stack to monitor for drift detection
Default: 'base-infrastructure'
ConfigRuleName:
Type: String
Description: Provide the name for the Config rule
Default: 'CloudFormationDriftDetection'
Resources:
IamRoleForConfig:
Type: AWS::IAM::Role
Properties:
RoleName: CloudFormationDriftDetectionRole
Description: IAM role for AWS Config to access CloudFormation drift detection
AssumeRolePolicyDocument:
Version: '2012-10-17'
Statement:
- Effect: Allow
Principal:
Service: config.amazonaws.com
Action:
- sts:AssumeRole
ManagedPolicyArns:
- arn:aws:iam::aws:policy/ReadOnlyAccess
Policies:
- PolicyName: CloudFormationDriftDetectionpolicy
PolicyDocument:
Version: "2012-10-17"
Statement:
- Effect: Allow
Action:
- cloudformation:DetectStackResourceDrift
- cloudformation:DetectStackDrift
- cloudformation:DescribeStacks
- cloudformation:DescribeStackResources
- cloudformation:BatchDescribeTypeConfigurations
- cloudformation:DescribeStackResourceDrifts
- cloudformation:DescribeStackDriftDetectionStatus
Resource: !Sub "arn:${AWS::Partition}:cloudformation:${AWS::Region}:${AWS::AccountId}:*"
ConfigRuleToDetectCfnDrift:
Type: AWS::Config::ConfigRule
Properties:
ConfigRuleName: !Ref ConfigRuleName
Description: AWS Config rule to detect drift in CloudFormation stacks
Scope:
TagKey: stack-name
TagValue: !Ref StackNameToMonitor
Source:
Owner: AWS
SourceIdentifier: CLOUDFORMATION_STACK_DRIFT_DETECTION_CHECK
MaximumExecutionFrequency: !Ref MaximumExecutionFrequency
InputParameters:
cloudformationRoleArn: !GetAtt IamRoleForConfig.Arn
IamRoleForRemediation:
Type: AWS::IAM::Role
Properties:
RoleName: AwsConfigRemediationAction
Description: IAM role for AWS Config remediation action to publish SNS notifications
AssumeRolePolicyDocument:
Version: '2012-10-17'
Statement:
- Effect: Allow
Principal:
Service:
- config.amazonaws.com
- ssm.amazonaws.com
Action:
- sts:AssumeRole
Policies:
- PolicyName: SNSPublishPolicy
PolicyDocument:
Version: '2012-10-17'
Statement:
- Effect: Allow
Action:
- sns:Publish
Resource: !Ref SnsTopicToNotifyCfnDriftAlarm
RemediationActionForConfigRule:
Type: AWS::Config::RemediationConfiguration
Properties:
ConfigRuleName: !Ref ConfigRuleName
TargetType: SSM_DOCUMENT
TargetId: AWS-PublishSNSNotification
Automatic: true
MaximumAutomaticAttempts: 2
RetryAttemptSeconds: 30
Parameters:
AutomationAssumeRole:
StaticValue:
Values:
- !GetAtt IamRoleForRemediation.Arn
Message:
StaticValue:
Values:
- !Sub |
"*** CloudFormation Stack drift detected! ***"
"Account: ${AWS::AccountId}"
"CloudFormation Stack: ${StackNameToMonitor}"
TopicArn:
StaticValue:
Values:
- !Ref SnsTopicToNotifyCfnDriftAlarm
Prerequisites:
Ensure the following prerequisites are in place:
- An AWS account with sufficient permissions to create and manage resources.
- The AWS CLI installed on the local machine.
Deployment:
1.Clone the repository.
git clone https://gitlab.com/Andr1500/cfn-drift-detection.git
2.Deploy the base infrastructure. Use the infrastructure/infrastructure_stack.yaml template to set up the foundational resources.
aws cloudformation create-stack \
--stack-name base-infrastructure \
--template-body file://infrastructure/infrastructure_stack.yaml \
--capabilities CAPABILITY_NAMED_IAM \
--tags Key=stack-name,Value=base-infrastructure
3.Verify AWS Config setup. Check if AWS Config is enabled, and create necessary resources if missing.
aws configservice describe-configuration-recorders
aws configservice describe-delivery-channels
aws iam get-role --role-name AWSServiceRoleForConfig
aws iam create-service-linked-role --aws-service-name config.amazonaws.com
aws configservice put-configuration-recorder \
--configuration-recorder name=default,roleARN=arn:aws:iam::${AWS::AccountId}:role/aws-service-role/config.amazonaws.com/AWSServiceRoleForConfig
aws configservice put-delivery-channel \
--delivery-channel-name default \
--s3-bucket-name
4.Deploy the monitoring stack using the infrastructure/monitoring_stack.yaml template. It is important to grant necessary access for the Config Rule, otherwise, you will have an error for the monitored stack resources scope:AWS CloudFormation failed to detect drift. The default compliance state has been set to NON_COMPLIANT. Re-evaluate the rule and try again. If the problem persists contact AWS CloudFormation support.
aws cloudformation create-stack \
--stack-name monitoring-infrastructure \
--template-body file://infrastructure/monitoring_stack.yaml \
--capabilities CAPABILITY_NAMED_IAM \
--disable-rollback
5.Test the monitoring stack. Change value of the resource from the base infrastructure stack and evaluate the drift detection rule to verify functionality.
aws ssm put-parameter --name "ConnectionToken" --value "secret_token_value_2" --type "String" --overwrite
aws configservice start-config-rules-evaluation --config-rule-names CloudFormationDriftDetection
6.Clean up resources. After testing, clean up resources by deleting the CloudFormation stacks.
aws cloudformation delete-stack --stack-name infrastructure_stack.yaml
aws cloudformation delete-stack --stack-name monitoring_stack.yaml
Conclusion:
By implementing remediation actions with the AWS-PublishSNSNotification Systems Manager automation runbook, you can automate notifications with minimal setup. While this approach is efficient, it’s essential to consider the 256-character limit for the Message field, which may restrict detailed notifications.
For scenarios requiring advanced workflows or richer notifications, consider augmenting the solution with EventBridge rules or Lambda functions. With this system in place, you can ensure timely responses to drift events and maintain infrastructure compliance effectively.
If you found this post helpful and interesting, please click the reaction button to show your support. Feel free to use and share this post.






















































.jpg)
%20Abstract%20Background%20112024%20SOURCE%20Amazon.jpg)



















































































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)
































































































































![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)





































































































.png?#)





.jpg?#)































_Christophe_Coat_Alamy.jpg?#)








































































































![Rapidus in Talks With Apple as It Accelerates Toward 2nm Chip Production [Report]](https://www.iclarified.com/images/news/96937/96937/96937-640.jpg)