Using Kata Containers as a Container Runtime in OpenStack Zun
As container adoption grows in cloud infrastructure, OpenStack has introduced Zun, a project designed to manage application containers natively within the OpenStack ecosystem. By default, Zun leverages container runtimes like runc, but for users seeking stronger isolation and enhanced security, integrating Kata Containers offers a compelling upgrade. With Kata, containers launched via Zun gain the security advantages of lightweight virtual machines—each with its own kernel—without giving up the flexibility and speed that make containers so attractive. In this post, we'll explore how Kata Containers can be used with Zun to provide a secure and efficient container experience within OpenStack. Topology In this case, we will deploy OpenStack using Kolla-Ansible in all-in-one mode and set Kata Containers as a container runtime for Zun. Here is the topology Here is the topology explaination : eno1 and eno2 wil configured as a bonding interface (802.3ad) named bond0. in bond0 we will create an VLAN interface with ID 100 ( bond0.100 ) for management and access the OpenStack services. This adapter has an IP address. bond0 will configured for external network adapter. We will using VLAN as an external network in ml2.conf. This adapter doesn't have any IP address. OpenStack will deployed using Kolla-ansible with docker for container service Docker and Containerd will need additional coniguration to add kata as a runtime Prerequisites Let's breakdown the prerequisites before start the deployment CPU with virtualization support 64-bit Linux host ( must be using nested virtualization if using VM ) with multiple network adapters. In this case, we will using Ubuntu 24.04 and several network adapters ( explained at topology section ) Internet access Sudo user Pre-installation Disable any swap swapoff -a Don't forget to delete swap partition entry in /etc/fstab to make sure the swap partition will not active when booting. Enable br_netfilter module Load br_netfilter kernel module modprobe br_netfiter Create a new file under /etc/modules-load.d/ and add br_netfilter to make sure the module will automatically loaded when booting echo 'br_netfilter' > /etc/modules-load.d/must-loaded.conf Installation 1. Kata Containers Installation We will start with install Kata Containers. In this case, we will install Kata Containers with Docker. So, we will execute kata-manager.sh file with -D options. ./kata-manager.sh -D Or you can install only Kata Containers and install Docker separately by using -o options. ./kata-manager.sh -o Also, you can change default hypervisor for Kata Containers from qemu to another such as firecracker, cloud-hypervisor, etc with -S options. For example, we will using cloud-hypervisor as a default hypervisor for Kata Containers ./kata-manager.sh -S clh You can follow this post or official document of Kata Containers here for any details. 2. Docker Installation ( Optional ) If you install Kata Containers with Docker by using kata-manager.sh you can skip this step. Follow this guide if you only install Kata Containers without Docker in step 1. 3. Kolla-Ansible Preparation Deploying OpenStack with Kolla-Ansible is quite simple. For this case, We will using OpenStack Dalmatian ( 2024.2 ). Install python build dependencies sudo apt install git python3-dev libffi-dev gcc libssl-dev libdbus-glib-1-dev Create python virtual env Create python virtual env for Kolla python3 -m venv /path/to/venv Activate the virtual env source /path/to/venv/bin/activate Install pip Install pip and make sure we using the latest version of pip pip install -U pip Install Ansible pip install 'ansible-core>=2.17,

As container adoption grows in cloud infrastructure, OpenStack has introduced Zun, a project designed to manage application containers natively within the OpenStack ecosystem. By default, Zun leverages container runtimes like runc, but for users seeking stronger isolation and enhanced security, integrating Kata Containers offers a compelling upgrade. With Kata, containers launched via Zun gain the security advantages of lightweight virtual machines—each with its own kernel—without giving up the flexibility and speed that make containers so attractive. In this post, we'll explore how Kata Containers can be used with Zun to provide a secure and efficient container experience within OpenStack.
Topology
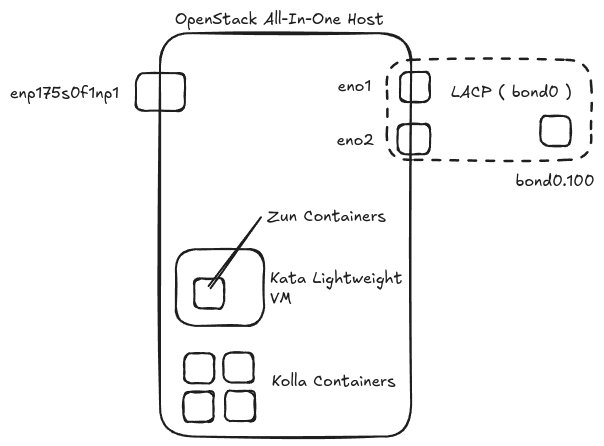
In this case, we will deploy OpenStack using Kolla-Ansible in all-in-one mode and set Kata Containers as a container runtime for Zun. Here is the topology
Here is the topology explaination :
-
eno1andeno2wil configured as a bonding interface (802.3ad) namedbond0. - in
bond0we will create an VLAN interface with ID 100 (bond0.100) for management and access the OpenStack services. This adapter has an IP address. -
bond0will configured for external network adapter. We will using VLAN as an external network inml2.conf. This adapter doesn't have any IP address. - OpenStack will deployed using Kolla-ansible with docker for container service
- Docker and Containerd will need additional coniguration to add
kataas a runtime
Prerequisites
Let's breakdown the prerequisites before start the deployment
- CPU with virtualization support
- 64-bit Linux host ( must be using nested virtualization if using VM ) with multiple network adapters. In this case, we will using Ubuntu 24.04 and several network adapters ( explained at topology section )
- Internet access
- Sudo user
Pre-installation
- Disable any swap
swapoff -a
Don't forget to delete swap partition entry in /etc/fstab to make sure the swap partition will not active when booting.
- Enable
br_netfiltermodule
Load br_netfilter kernel module
modprobe br_netfiter
Create a new file under /etc/modules-load.d/ and add br_netfilter to make sure the module will automatically loaded when booting
echo 'br_netfilter' > /etc/modules-load.d/must-loaded.conf
Installation
1. Kata Containers Installation
We will start with install Kata Containers. In this case, we will install Kata Containers with Docker. So, we will execute kata-manager.sh file with -D options.
./kata-manager.sh -D
Or you can install only Kata Containers and install Docker separately by using -o options.
./kata-manager.sh -o
Also, you can change default hypervisor for Kata Containers from qemu to another such as firecracker, cloud-hypervisor, etc with -S options. For example, we will using cloud-hypervisor as a default hypervisor for Kata Containers
./kata-manager.sh -S clh
You can follow this post or official document of Kata Containers here for any details.
2. Docker Installation ( Optional )
If you install Kata Containers with Docker by using kata-manager.sh you can skip this step. Follow this guide if you only install Kata Containers without Docker in step 1.
3. Kolla-Ansible Preparation
Deploying OpenStack with Kolla-Ansible is quite simple. For this case, We will using OpenStack Dalmatian ( 2024.2 ).
- Install python build dependencies
sudo apt install git python3-dev libffi-dev gcc libssl-dev libdbus-glib-1-dev
- Create python virtual env
Create python virtual env for Kolla
python3 -m venv /path/to/venv
- Activate the virtual env
source /path/to/venv/bin/activate
- Install pip Install pip and make sure we using the latest version of pip
pip install -U pip
- Install Ansible
pip install 'ansible-core>=2.17,<2.17.99'
- Install Kolla-Ansible
Install Kolla-Ansible and its dependencies using pip
pip install git+https://opendev.org/openstack/kolla-ansible@stable/2024.2
- Create Kolla directory
Create directory for kolla config and make sure the permission is accessible with user.
sudo mkdir -p /etc/kolla
sudo chown $USER:$USER /etc/kolla
- Copy preparation file
cp -r /path/to/venv/share/kolla-ansible/etc_examples/kolla/* /etc/kolla
- Copy inventory file
cp /path/to/venv/share/kolla-ansible/ansible/inventory/all-in-one .
- Install Kolla dependencies
kolla-ansible install-deps
- Generate passwords
kolla-genpwd
- Edit globals.yml
Edit globals.yml file and make sure zun are enabled.
enable_zun: "yes"
enable_kuryr: "yes"
enable_etcd: "yes"
docker_configure_for_zun: "yes"
containerd_configure_for_zun: "yes"
You can also include another OpenStack service to install based on your needs.
- Bootstrap server
kolla-ansible bootstrap-servers -i all-in-one
4. Add Kata Runtime
After bootstraping server, we need some configuration in Docker and Containerd side before deploy OpenStack. Change file /etc/docker/daemon.json with this line below
{
"bridge": "none",
"ip-forward": false,
"iptables": false,
"log-opts": {
"max-file": "5",
"max-size": "50m"
},
"runtimes": {
"kata": {
"runtimeType": "io.containerd.kata.v2",
"options": {}
}
}
}
This means we registered kata runtime in Docker configuration. After that, dump all containerd configuration and place it into /etc/containered/config.toml.
containerd config dump | tee /etc/containerd/config.toml
Edit file /etc/containerd/config.toml to do some changes. in [grpc] section, edit gid options
...
[grpc]
gid = 42463
...
Save the configuration. Now, restart containerd and docker service
systemctl restart containerd docker
5. Deploy OpenStack
After all completed, do prechecks before deploy OpenStack
kolla-ansible prechecks -i all-in-one
If no errors shown, we can deploy OpenStack
kolla-ansible deploy -i all-in-one
Wait until OpenStack are successfully deployed.
6. Launch a Container
Access the OpenStack Horizon Dashboard and then create network, subnet, ssh keypair, security group. We need all of these components to create container. Move to menu Container to begin create a container.
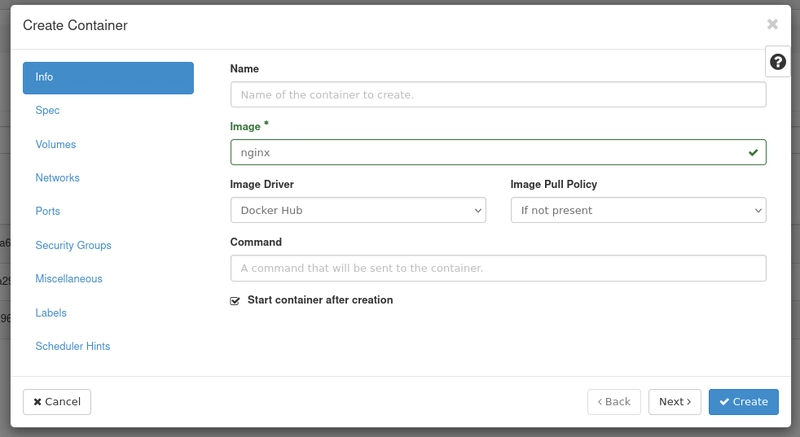
Choose Create Container. Then, input the information about the container. For example, we will create nginx container like this picture below.
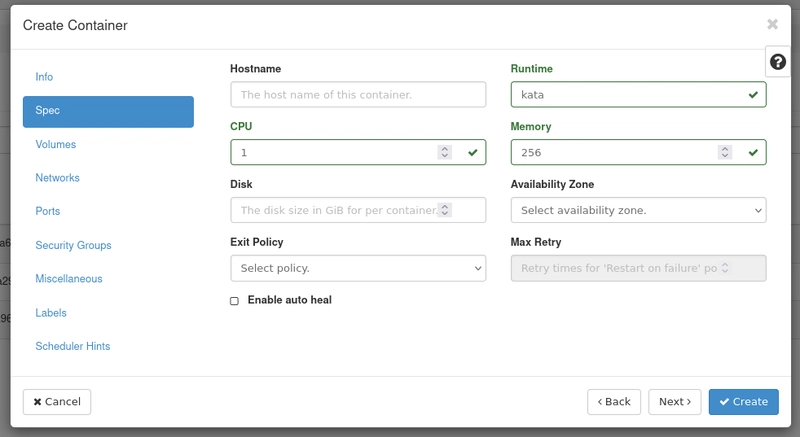
Then, input the container spesification. Don't forget to use kata as a runtime like this picture below.
Fill another requirements like network, volume if you need persistent volume, and other options. Choose create and wait until container created like this picture below.
Conclusions
Integrating Kata Containers as a runtime for OpenStack Zun adds a valuable layer of security and workload isolation to containerized environments. By leveraging lightweight virtual machines, Kata provides strong boundaries between workloads—making it ideal for multi-tenant or untrusted scenarios often found in cloud platforms. This setup allows OpenStack users to benefit from the flexibility of containers without compromising on isolation, all while maintaining compatibility with existing OpenStack services. As container technologies continue to evolve, combining Zun and Kata offers a future-proof, security-conscious approach to running containers at scale within OpenStack.








































































































































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)






























































































































![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)



































































































.png?#)






(1).jpg?width=1920&height=1920&fit=bounds&quality=80&format=jpg&auto=webp#)





























_NicoElNino_Alamy.png?#)
.webp?#)
.webp?#)
































































































![Apple to Source More iPhones From India to Offset China Tariff Costs [Report]](https://www.iclarified.com/images/news/96954/96954/96954-640.jpg)
![Blackmagic Design Unveils DaVinci Resolve 20 With Over 100 New Features and AI Tools [Video]](https://www.iclarified.com/images/news/96951/96951/96951-640.jpg)