The 6.5 Tbps Attack!
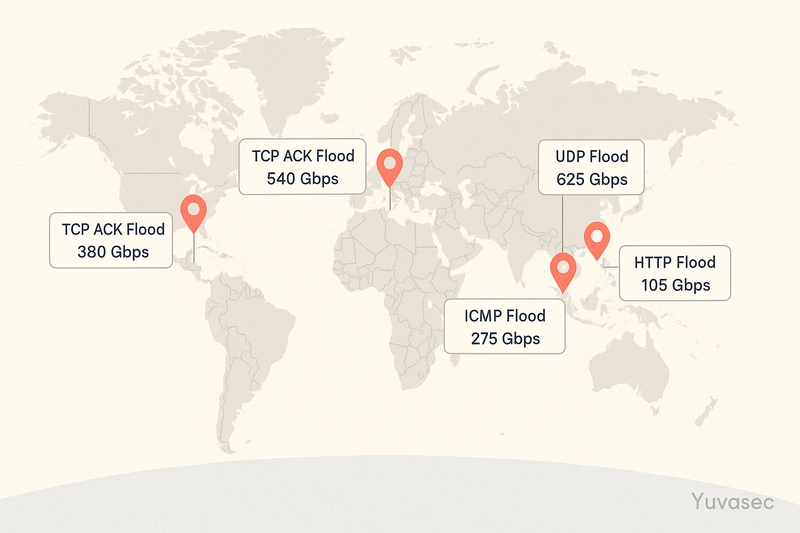
Introduction In April 2025, a major online betting platform went dark for 90 minutes during a peak sports event. The reason? A hyper-volumetric Distributed Denial of Service (DDoS) attack that scaled up to nearly 1 terabit per second in just 20 minutes. Thousands of users were locked out. Millions in revenue? Lost. This isn’t an isolated event - it’s a sign of the times. DDoS attacks have exploded in both scale and sophistication. According to Cloudflare, the first quarter of 2025 alone witnessed 20.5 million attacks, a 358% increase year-over-year. This article dives deep into what DDoS attacks really are, how attackers pull them off, and most importantly, how you can defend your digital assets before they’re knocked offline. What is a DDoS Attack? Short Concept: DDoS stands for Distributed Denial of Service. It’s like flooding a shop with so many fake customers that the real ones can’t get in. Anecdote: Imagine you're selling lemonade. Suddenly, 500 kids show up pretending to buy but never actually do, they just crowd your stand. Real thirsty customers? They leave because they can’t even reach you! How Does a DDoS Attack Happen? Short Concept: Hackers use bots — infected computers and devices — to all send traffic at the same time to one place, like angry robots crashing a party. Anecdote: You throw a birthday party and invite 10 friends. Suddenly, 10,000 robots crash it. They don't eat cake — they just make noise and mess up everything! Why Do People Launch DDoS Attacks? Short Concept: Sometimes it’s to cause chaos, ask for ransom, or attack competition. Anecdote: Imagine two lemonade stands side by side. One stand hires a bunch of clowns to block customers from reaching the other stand. Unfair and sneaky! Types of DDoS Attacks Short Concept: There are different "flavors" of attacks: Volumetric Attacks: Overwhelm the internet connection. Protocol Attacks: Target servers directly. Application Attacks: Break specific apps like websites or games. Anecdote: Think about it like ruining a fair: Volumetric = Flood the entrance with balloons. Protocol = Break the ticket machine. Application = Sabotage the ice cream stand inside. Anatomy of a DDoS Attack 1. Build or Rent a Botnet Malicious actors use malware to compromise IoT devices, servers, and PCs. These devices form a botnet—a digital army under the attacker’s control. 2. Command and Control (C2) The attacker communicates with bots via C2 servers. Instructions: Attack this IP, use this method, flood at this rate. 3. Attack Vectors Bandwidth attacks: Saturate networks (e.g., UDP flood). Application-layer attacks: Exhaust app resources (e.g., HTTP GET floods). Protocol attacks: Exploit weaknesses in transport layers (e.g., SYN floods). 4. Amplification & Obfuscation Using spoofed IPs, attackers mask origins. Reflective attacks can amplify traffic 100x by exploiting misconfigured servers. Recent Case Studies

Introduction
In April 2025, a major online betting platform went dark for 90 minutes during a peak sports event. The reason? A hyper-volumetric Distributed Denial of Service (DDoS) attack that scaled up to nearly 1 terabit per second in just 20 minutes. Thousands of users were locked out. Millions in revenue? Lost.
This isn’t an isolated event - it’s a sign of the times.
DDoS attacks have exploded in both scale and sophistication.
According to Cloudflare, the first quarter of 2025 alone witnessed 20.5 million attacks, a 358% increase year-over-year.
This article dives deep into what DDoS attacks really are, how attackers pull them off, and most importantly, how you can defend your digital assets before they’re knocked offline.
What is a DDoS Attack?
Short Concept:
DDoS stands for Distributed Denial of Service. It’s like flooding a shop with so many fake customers that the real ones can’t get in.
Anecdote:
Imagine you're selling lemonade. Suddenly, 500 kids show up pretending to buy but never actually do, they just crowd your stand. Real thirsty customers? They leave because they can’t even reach you!
How Does a DDoS Attack Happen?
Short Concept:
Hackers use bots — infected computers and devices — to all send traffic at the same time to one place, like angry robots crashing a party.
Anecdote:
You throw a birthday party and invite 10 friends. Suddenly, 10,000 robots crash it. They don't eat cake — they just make noise and mess up everything!
Why Do People Launch DDoS Attacks?
Short Concept:
Sometimes it’s to cause chaos, ask for ransom, or attack competition.
Anecdote:
Imagine two lemonade stands side by side. One stand hires a bunch of clowns to block customers from reaching the other stand. Unfair and sneaky!
Types of DDoS Attacks
Short Concept:
There are different "flavors" of attacks:
- Volumetric Attacks: Overwhelm the internet connection.
- Protocol Attacks: Target servers directly.
- Application Attacks: Break specific apps like websites or games.
Anecdote:
Think about it like ruining a fair:
- Volumetric = Flood the entrance with balloons.
- Protocol = Break the ticket machine.
- Application = Sabotage the ice cream stand inside.
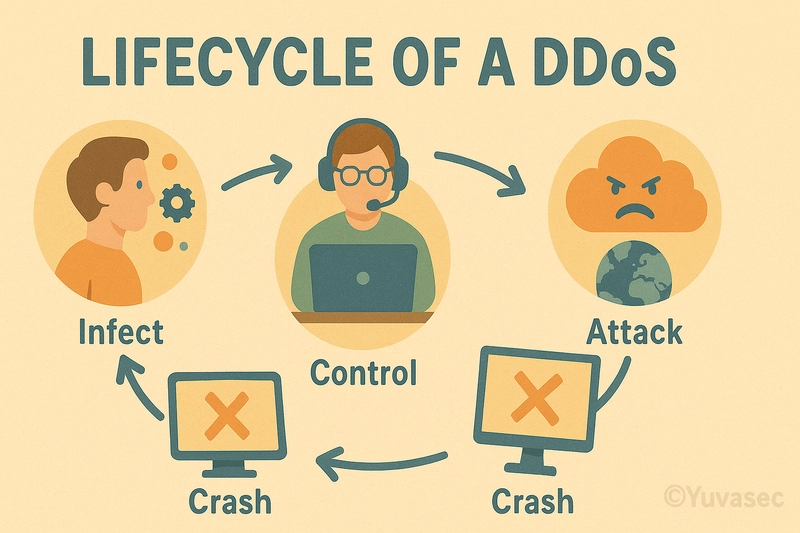
Anatomy of a DDoS Attack
1. Build or Rent a Botnet
- Malicious actors use malware to compromise IoT devices, servers, and PCs.
- These devices form a botnet—a digital army under the attacker’s control.
2. Command and Control (C2)
- The attacker communicates with bots via C2 servers.
- Instructions: Attack this IP, use this method, flood at this rate.
3. Attack Vectors
- Bandwidth attacks: Saturate networks (e.g., UDP flood).
- Application-layer attacks: Exhaust app resources (e.g., HTTP GET floods).
- Protocol attacks: Exploit weaknesses in transport layers (e.g., SYN floods).
4. Amplification & Obfuscation
- Using spoofed IPs, attackers mask origins.
- Reflective attacks can amplify traffic 100x by exploiting misconfigured servers.



































































































































































![[The AI Show Episode 145]: OpenAI Releases o3 and o4-mini, AI Is Causing “Quiet Layoffs,” Executive Order on Youth AI Education & GPT-4o’s Controversial Update](https://www.marketingaiinstitute.com/hubfs/ep%20145%20cover.png)


































































































































































































































































_NicoElNino_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)

























































































![Craft adds Readwise integration for working with book notes and highlights [50% off]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/04/craft3.jpg.png?resize=1200%2C628&quality=82&strip=all&ssl=1)















![Apple Restructures Global Affairs and Apple Music Teams [Report]](https://www.iclarified.com/images/news/97162/97162/97162-640.jpg)
![New iPhone Factory Goes Live in India, Another Just Days Away [Report]](https://www.iclarified.com/images/news/97165/97165/97165-640.jpg)