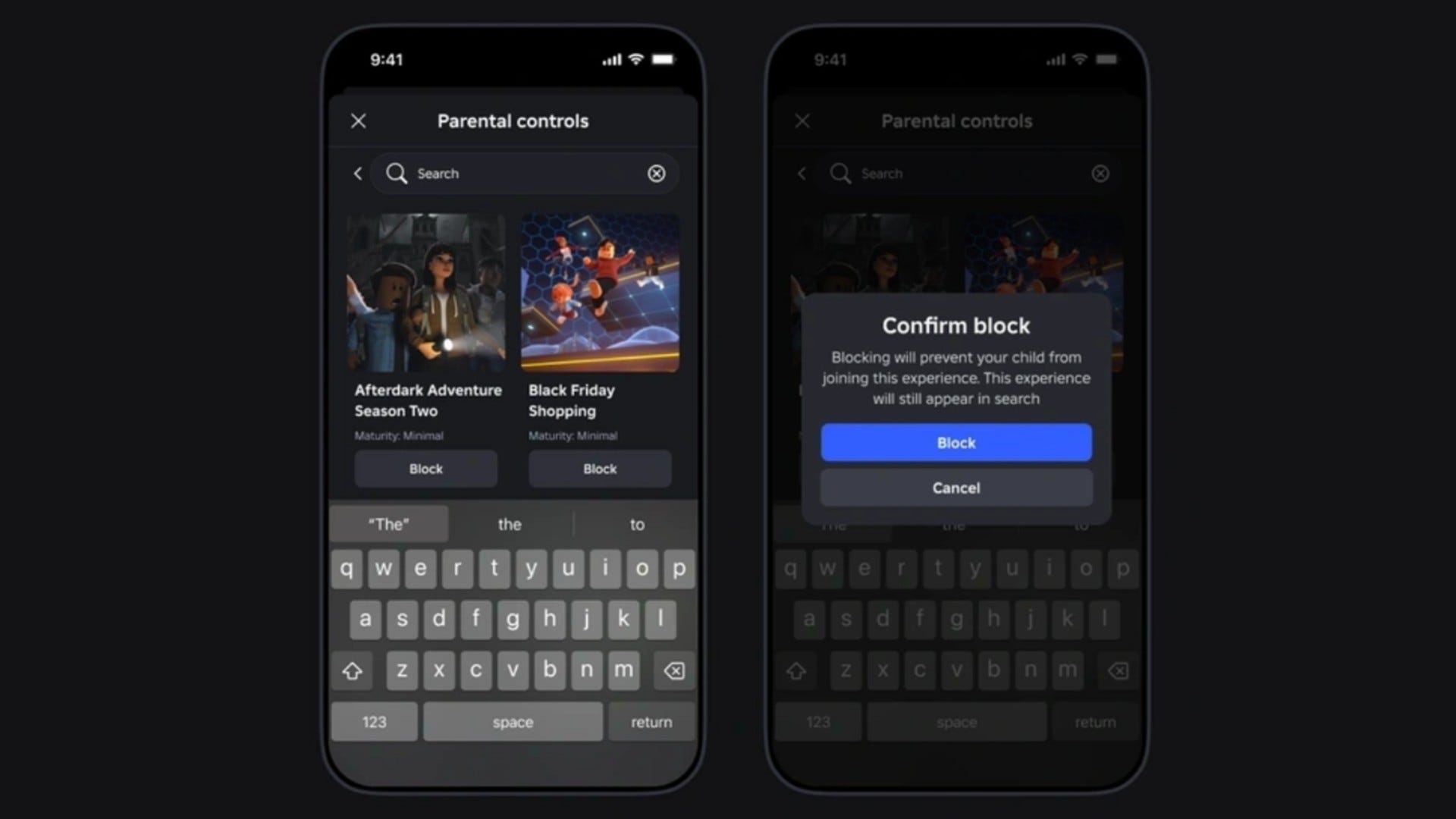
Regex in Action: Tuning Fail2ban with Ansible
Regex has been a constant in nearly every coding project I’ve worked on. And since infrastructure today is also built on code, regex patterns are everywhere—for instance, in the configurations of DevOps tools operating within the context of Infrastructure as Code (IaC). For a demonstration, I’ve pulled a snippet from an Ansible playbook that adjusts the maxretry in Fail2ban to two attempts before blocking SSH access. ... - name: Set the maxretry in fail2ban to 2. lineinfile: path: /etc/fail2ban/jail.d/ssh.conf regexp: '^maxretry =' line: 'maxretry = 2' create: yes notify: Restart fail2ban ... The regex in the lineinfile module tweaks only the maxretry parameter in the ssh.conf configuration file for Fail2ban. If needed, the same approach can apply to adjustments like worker_connections in Nginx or file open limits in limits.conf for Docker, ensuring precise environment configurations.

Regex has been a constant in nearly every coding project I’ve worked on. And since infrastructure today is also built on code, regex patterns are everywhere—for instance, in the configurations of DevOps tools operating within the context of Infrastructure as Code (IaC).
For a demonstration, I’ve pulled a snippet from an Ansible playbook that adjusts the maxretry in Fail2ban to two attempts before blocking SSH access.
...
- name: Set the maxretry in fail2ban to 2.
lineinfile:
path: /etc/fail2ban/jail.d/ssh.conf
regexp: '^maxretry ='
line: 'maxretry = 2'
create: yes
notify: Restart fail2ban
...
The regex in the lineinfile module tweaks only the maxretry parameter in the ssh.conf configuration file for Fail2ban. If needed, the same approach can apply to adjustments like worker_connections in Nginx or file open limits in limits.conf for Docker, ensuring precise environment configurations.












































































































































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)





























































































































![[DEALS] Microsoft Office Professional 2021 for Windows: Lifetime License (75% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)








































































































































_Anthony_Brown_Alamy.jpg?#)
_Hanna_Kuprevich_Alamy.jpg?#)




.png?#)



















































































![Hands-on: We got to play Nintendo Switch 2 for nearly six hours yesterday [Video]](https://i0.wp.com/9to5toys.com/wp-content/uploads/sites/5/2025/04/Switch-FI-.jpg.jpg?resize=1200%2C628&ssl=1)
![Fitbit redesigns Water stats and logging on Android, iOS [U]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2023/03/fitbit-logo-2.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)













![YouTube Announces New Creation Tools for Shorts [Video]](https://www.iclarified.com/images/news/96923/96923/96923-640.jpg)

![Apple Faces New Tariffs but Has Options to Soften the Blow [Kuo]](https://www.iclarified.com/images/news/96921/96921/96921-640.jpg)