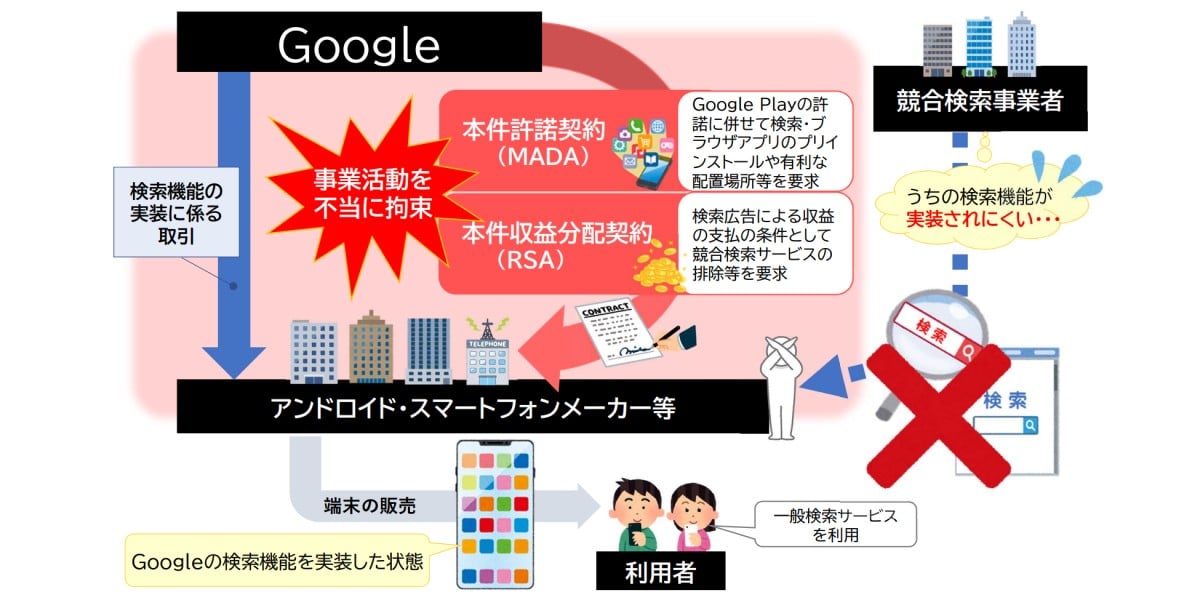
Integrate Modern Strategies for Zero Trust with Identity & Access Management (IAM)
In an era defined by digital transformation, the traditional approach to cybersecurity has proven insufficient. The proliferation of cloud services, mobile devices, and remote work environments has expanded attack surfaces, necessitating a more robust security model. Zero Trust represents a paradigm shift in cybersecurity, grounded in the principle of “never trust, always verify.” Unlike traditional […] The post Integrate Modern Strategies for Zero Trust with Identity & Access Management (IAM) appeared first on Cyber Security News.
.webp?#)
In an era defined by digital transformation, the traditional approach to cybersecurity has proven insufficient. The proliferation of cloud services, mobile devices, and remote work environments has expanded attack surfaces, necessitating a more robust security model.
Zero Trust represents a paradigm shift in cybersecurity, grounded in the principle of “never trust, always verify.” Unlike traditional security models that rely on perimeter-based defenses, Zero Trust assumes no user, device, or application should be trusted by default.
By integrating Zero Trust with Identity and Access Management (IAM), organizations are establishing frameworks that address evolving threat landscapes while maintaining operational efficiency.
Leadership’s strategic involvement is crucial for successful implementation across technical, architectural, and cultural dimensions.
Identity and Access Management
Zero Trust is not merely a technology but a comprehensive security mindset that systematically removes implicit trust in IT infrastructures. It forms a guiding principle for security architectures that improve security posture and increase cyber-resiliency.
The traditional “trust but verify” model has become obsolete as modern infrastructures interconnect with cloud services, IoT devices, and mobile environments, eroding the boundaries of traditional perimeters.
Zero Trust acknowledges that threats can originate from both external and internal sources, necessitating a holistic security approach. This framework addresses the reality that insider threats—whether malicious or accidental—remain among the most challenging security risks.
By focusing on continuous verification and strict access controls, Zero Trust mitigates the risk of unauthorized access, data breaches, and lateral movement within networks.
Strategic leadership alignment is essential, as Zero Trust represents not just a technology choice but a strategic pivot in the organization’s security culture.
Essential Components of Zero Trust IAM
The implementation of Zero Trust in identity and access management requires careful consideration of several critical elements that work together to create a comprehensive security framework.
- Continuous Verification: Every user, device, and application must be verified for every access request, regardless of their location or network connection. This verification ensures that security decisions are made in real-time based on current conditions rather than previous authentication status.
- Least Privilege Access: Users and systems should be granted the minimum permissions required to perform their specific roles, minimizing potential damage from compromised accounts. This principle limits lateral movement and contains potential breaches by restricting access scope.
- Dynamic, Context-Aware Authentication: Access decisions must incorporate real-time context, including device health, user location, time of access, and behavioral patterns. This adaptive approach adds layers of security that adjust to changing risk factors.
- Role-Based Access Control: RBAC provides an elegant approach to access management by assigning permissions based on organizational roles. This reduces the likelihood of errors compared to assigning permissions on an individual basis and simplifies administration.
- Comprehensive Identity Lifecycle Management: Effective user management throughout the entire identity lifecycle—from onboarding to role changes to offboarding—ensures that access privileges remain appropriate and that former users cannot retain system access.
Organizations implementing these components create a stronger security posture that significantly reduces the attack surface while maintaining necessary business functionality.
The technical implementation must be backed by clear policies and procedures that define how these elements are applied across the enterprise.
Strategies for Successful Zero Trust Implementation
Implementing Zero Trust requires technical expertise, but success ultimately depends on strategic leadership. Zero Trust initiatives often face resistance due to perceived impacts on productivity, additional costs, and general organizational resistance to change.
Effective leaders recognize that Zero Trust is not merely a technical implementation but a transformative approach requiring cultural shifts throughout the organization.
Communication becomes paramount—leaders must clearly articulate the benefits of Zero Trust while addressing concerns about workflow disruptions.
The security team cannot drive this change alone; executive sponsorship is essential for aligning security goals with business objectives and ensuring appropriate resource allocation.
Leaders must develop a phased implementation strategy that prioritizes high-value assets and critical access points while minimizing business disruption.
This requires deep understanding of business workflows, data sensitivity, and operational dependencies. Documentation of existing access patterns helps identify where Zero Trust controls will have the most impact while highlighting potential friction points that require special attention.
Successful implementation also demands investing in user education and creating feedback mechanisms to address emerging challenges.
- Critical Success Factors: Executive commitment, clear communication of security and business benefits, adequate resource allocation, and an iterative implementation approach that demonstrates value early in the process.
- Common Implementation Pitfalls: Attempting too much too quickly, failing to gain stakeholder buy-in, inadequate planning for operational impacts, and neglecting the human elements of change management.
Leaders who approach Zero Trust as a strategic business initiative rather than a purely technical project create the foundation for sustainable security transformation.
By fostering collaboration between security, IT, and business units, leaders can ensure that Zero Trust enhances rather than hinders organizational objectives.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!
The post Integrate Modern Strategies for Zero Trust with Identity & Access Management (IAM) appeared first on Cyber Security News.



.jpg)





































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)












































































































































































.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)




















![Blue Archive tier list [April 2025]](https://media.pocketgamer.com/artwork/na-33404-1636469504/blue-archive-screenshot-2.jpg?#)


































.png?#)






































.webp?#)




































































































![Apple to Split Enterprise and Western Europe Roles as VP Exits [Report]](https://www.iclarified.com/images/news/97032/97032/97032-640.jpg)
![Nanoleaf Announces New Pegboard Desk Dock With Dual-Sided Lighting [Video]](https://www.iclarified.com/images/news/97030/97030/97030-640.jpg)

![Apple's Foldable iPhone May Cost Between $2100 and $2300 [Rumor]](https://www.iclarified.com/images/news/97028/97028/97028-640.jpg)


































































































































