Guide for the CompTIA Security+ SY0-701 exam
Exam Domains & Weightage: General Security Concepts (12%) Threats, Vulnerabilities, & Mitigations (22%) Security Architecture (18%) Security Operations (28%) Security Program Management & Oversight (20%) General Security Concepts (12%) Key Topics ✅ CIA Triad (Confidentiality, Integrity, Availability) ✅ Access Control Models (RBAC, DAC, MAC, ABAC) ✅ Authentication & Authorization (MFA, SSO, Federated Identity) ✅ Cybersecurity Frameworks (NIST, ISO 27001, CIS Controls) ✅ Common Cybersecurity Roles & Responsibilities ✅ Basic Cryptographic Concepts (Hashing, Symmetric & Asymmetric Encryption) CIA Triad (Confidentiality, Integrity, Availability) The CIA Triad is the foundation of cybersecurity. Every security control, policy, or mechanism must align with one or more of these principles. 1️⃣ Confidentiality – Protecting data from unauthorized access. Example: Encrypting emails using PGP to prevent eavesdropping. Controls: Encryption (AES, RSA), Access Control (RBAC), MFA, VPNs. 2️⃣ Integrity – Ensuring data remains accurate and unaltered. Example: A hashing algorithm (SHA-256) ensures a file wasn't modified. Controls: Digital Signatures, Hashing, Checksums, Data Validation. 3️⃣ Availability – Ensuring data is accessible when needed. Example: Redundant servers ensure a website stays online even if one server crashes. Controls: Load Balancers, RAID, Cloud Backups, DDoS Mitigation.
Exam Domains & Weightage:
- General Security Concepts (12%)
- Threats, Vulnerabilities, & Mitigations (22%)
- Security Architecture (18%)
- Security Operations (28%)
- Security Program Management & Oversight (20%)
General Security Concepts (12%)
Key Topics
✅ CIA Triad (Confidentiality, Integrity, Availability)
✅ Access Control Models (RBAC, DAC, MAC, ABAC)
✅ Authentication & Authorization (MFA, SSO, Federated Identity)
✅ Cybersecurity Frameworks (NIST, ISO 27001, CIS Controls)
✅ Common Cybersecurity Roles & Responsibilities
✅ Basic Cryptographic Concepts (Hashing, Symmetric & Asymmetric Encryption)
CIA Triad (Confidentiality, Integrity, Availability)
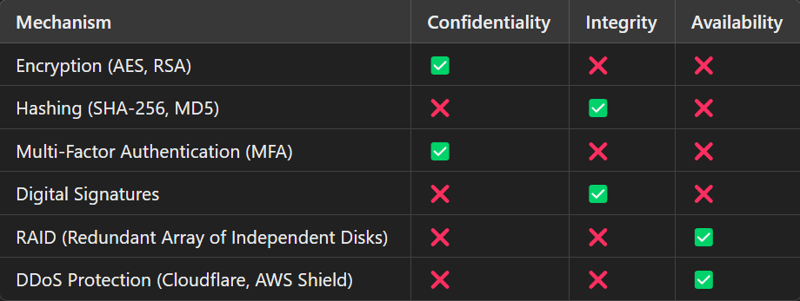
The CIA Triad is the foundation of cybersecurity. Every security control, policy, or mechanism must align with one or more of these principles.
1️⃣ Confidentiality – Protecting data from unauthorized access.
Example: Encrypting emails using PGP to prevent eavesdropping.
Controls: Encryption (AES, RSA), Access Control (RBAC), MFA, VPNs.
2️⃣ Integrity – Ensuring data remains accurate and unaltered.
Example: A hashing algorithm (SHA-256) ensures a file wasn't modified.
Controls: Digital Signatures, Hashing, Checksums, Data Validation.
3️⃣ Availability – Ensuring data is accessible when needed.
Example: Redundant servers ensure a website stays online even if one server crashes.
Controls: Load Balancers, RAID, Cloud Backups, DDoS Mitigation.








































































































































































![[The AI Show Episode 143]: ChatGPT Revenue Surge, New AGI Timelines, Amazon’s AI Agent, Claude for Education, Model Context Protocol & LLMs Pass the Turing Test](https://www.marketingaiinstitute.com/hubfs/ep%20143%20cover.png)



































































































































![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)









































































































.jpg?#)




























_ArtemisDiana_Alamy.jpg?#)












































































-xl.jpg)











![Yes, the Gemini icon is now bigger and brighter on Android [U]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/02/Gemini-on-Galaxy-S25.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)










![Apple Rushes Five Planes of iPhones to US Ahead of New Tariffs [Report]](https://www.iclarified.com/images/news/96967/96967/96967-640.jpg)
![Apple Vision Pro 2 Allegedly in Production Ahead of 2025 Launch [Rumor]](https://www.iclarified.com/images/news/96965/96965/96965-640.jpg)