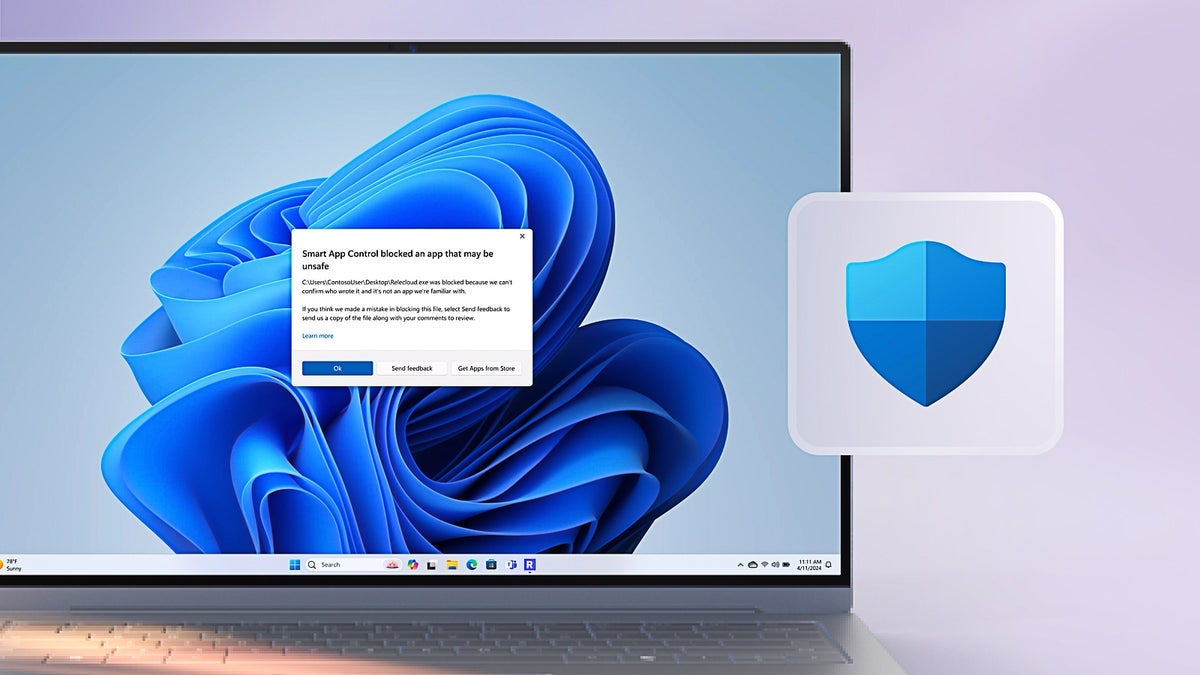
CISA Warns of Microsoft Windows CLFS Vulnerability Exploited in Wild
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical Microsoft Windows vulnerability to its Known Exploited Vulnerabilities (KEV) catalog. The flaw in the Windows Common Log File System (CLFS) driver, tracked as CVE-2025-29824, is being actively exploited in targeted ransomware attacks. Organizations are required to patch this vulnerability by April 29, 2025, […] The post CISA Warns of Microsoft Windows CLFS Vulnerability Exploited in Wild appeared first on Cyber Security News.

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical Microsoft Windows vulnerability to its Known Exploited Vulnerabilities (KEV) catalog.
The flaw in the Windows Common Log File System (CLFS) driver, tracked as CVE-2025-29824, is being actively exploited in targeted ransomware attacks.
Organizations are required to patch this vulnerability by April 29, 2025, to mitigate the risk of compromise.
Microsoft Windows CLFS Vulnerability
The security flaw is classified as a Use-After-Free (UAF) vulnerability, categorized under CWE-416, which occurs when a program attempts to access memory after it has been freed.
With a CVSS score of 7.8, this Elevation of Privilege (EoP) vulnerability allows an attacker with local access to escalate to SYSTEM privileges, effectively taking complete control of the affected system.
Microsoft patched this zero-day vulnerability during its April 2025 Patch Tuesday update after confirming it was being exploited in the wild.
The technical vector for this vulnerability is represented as CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H, indicating local access requirements but high impact on confidentiality, integrity, and availability if successfully exploited.
Microsoft’s security team has identified a malware campaign delivering the exploit through a trojan known as “PipeMagic.” This modular backdoor has been observed in the wild since 2022 and has previously been used to deliver other Windows zero-day exploits.
“The targets include organizations in the information technology (IT) and real estate sectors of the United States, the financial sector in Venezuela, a Spanish software company, and the retail sector in Saudi Arabia,” Microsoft reported.
The attack chain begins with the threat actors using the certutil utility to download malware from previously compromised legitimate third-party sites.
The malware, disguised as an MSBuild file with an encrypted payload, unpacks and launches PipeMagic, which then delivers the CVE-2025-29824 exploit.
According to Microsoft Threat Intelligence: “The exploit targets a vulnerability in the CLFS kernel driver. The exploit then utilizes a memory corruption and the RtlSetAllBits API to overwrite the exploit process’s token with the value 0xFFFFFFFF, enabling all privileges for the process, which allows for process injection into SYSTEM processes”.
After gaining elevated privileges, attackers extract user credentials by dumping the memory of the Local Security Authority Subsystem Service (LSASS) and deploying ransomware that encrypts files with random extensions.
The summary of the vulnerability is given below:
Risk Factors Details Affected Products Windows Server and various Windows versions, including x64 and 32-bit systems. Impact Elevation of Privilege (EoP) Exploit Prerequisites Local access required; attacker must already have a standard user account on the system CVSS Score 7.8 (High severity)
CISA’s Guidance
CISA added CVE-2025-29824 to its KEV catalog on April 8, 2025, flagging it as a significant threat requiring immediate attention.
Federal Civilian Executive Branch (FCEB) agencies must remediate this vulnerability by April 29, 2025, in accordance with Binding Operational Directive (BOD) 22-01.
For non-federal organizations, CISA strongly recommends implementing the same remediation timelines to reduce the risk of compromise.
The agency emphasizes that the KEV catalog should be used as “an input to their vulnerability management prioritization framework.”
Organizations should immediately apply Microsoft’s security patches, limit physical and local access to vulnerable systems, and ensure endpoint detection and response (EDR) tools are properly configured to detect exploitation attempts.
This vulnerability highlights the ongoing threat from kernel-level flaws and reinforces the critical importance of timely patch management in today’s cybersecurity landscape.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try 50 Request for Free
The post CISA Warns of Microsoft Windows CLFS Vulnerability Exploited in Wild appeared first on Cyber Security News.



.jpg)





































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)












































































































































































.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)




















![Blue Archive tier list [April 2025]](https://media.pocketgamer.com/artwork/na-33404-1636469504/blue-archive-screenshot-2.jpg?#)


































.png?#)






































.webp?#)




































































































![Apple to Split Enterprise and Western Europe Roles as VP Exits [Report]](https://www.iclarified.com/images/news/97032/97032/97032-640.jpg)
![Nanoleaf Announces New Pegboard Desk Dock With Dual-Sided Lighting [Video]](https://www.iclarified.com/images/news/97030/97030/97030-640.jpg)

![Apple's Foldable iPhone May Cost Between $2100 and $2300 [Rumor]](https://www.iclarified.com/images/news/97028/97028/97028-640.jpg)


































































































































