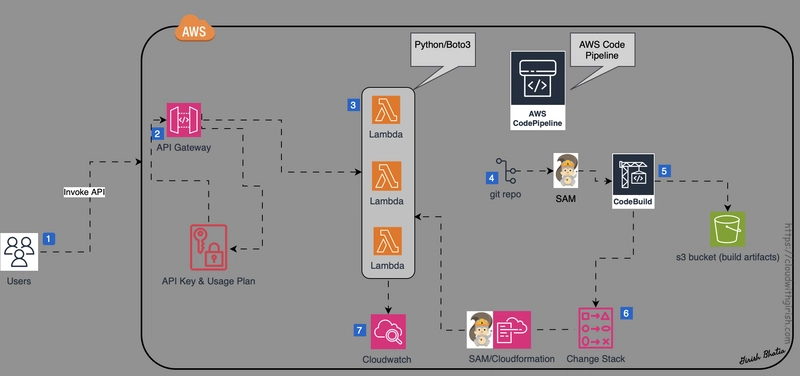
AWS Serverless: Build a CI/CD Pipeline for Lambda and API Gateway Using SAM and GitHub - Part 1
How do you build your software application? Do you still rely on a manual build process? Do you have a dedicated team member who runs the build multiple times a day or handles deployments to development, test, or production environments? If so, this article is for you. In this article, I will implement an AWS Code Pipeline for a serverless function and API built using AWS Lambda and API Gateway. The Lambda function itself is very simple and it returns just a 'Hello World' however, however, I will demonstrate the process of building the function and API using AWS SAM (Serverless Application Model) and validate it locally. Once I have validated the function locally using AWS SAM, I will integrate it with GitHub and AWS Code Pipeline for the CICD. With this CICD Pipeline, each time a commit is pushed to the git repo, AWS Pipeline will be triggered and updated stack will be automatically deployed into AWS cloud. Before diving in, let’s review the architecture diagram to understand how these components interact. Introduction to AWS SAM AWS SAM (Serverless Application Model) is a framework that simplifies the development, testing and deployment of serverless application on AWS. It uses a template file in YAML format that defines the resources like Lambda function, API, permission policies and more. With AWS SAM, developers can build and test the lambda function locally before deploying those to the AWS Cloud. An ability to develop and test locally enables the developers to debug the functions in a speedy reducing the cycle time for the testing and deployment. With commands like SAM Build, SAM Local Invoke and SAM Deploy, developers can use command line to accelerate the build, validate and deploy the resources. Overview of AWS Code Pipeline AWS Code Pipeline is a fully managed, serverless service that enables continuous integration and continuous delivery (CI/CD) for software application releases. It allows software teams to build CI/CD workflows as a series of stages, such as source, build, test, and deploy. AWS Code Pipeline integrates seamlessly with source control tools like GitHub and AWS services such as CodeBuild and CodeDeploy. By creating a CI/CD pipeline, teams can significantly reduce or even eliminate manual efforts and ensure consistency across different environments like development, testing, and production. This automation empowers teams to release software more frequently and reliably. Review AWS SAM Template The AWS Serverless Application Model (SAM) template defines the infrastructure required for the lambda function and API. Here’s what the SAM template for this solution looks like: Review AWS Lambda function (Python/Boto3 Library) Lambda function is developed using Python and uses the Boto3 library to interact with Amazon Lambda and API. Review Buildspec.yml A buildspec.yml file is a configuration file that tells AWS CodeBuild how to build your project. It's written in a simple YAML format and does these main things: Sets up your build environment Lists the commands to run during different phases of building: install phase: where you install dependencies pre_build phase: for setup steps before the main build build phase: where the actual building happens post_build phase: for cleanup and final steps after building Defines what files to save after building as Artifacts like packaged SAM template or compressed lambda code. Reports or test results This file stays in the root of your source code repository and helps automate the build process as part of CI/CD pipeline with AWS CodePipeline and AWS SAM. Commit code to Git Repo For this example, the GitHub repository is named helloworldcicd. Once your project files are ready, follow these steps to commit and push the code to your repository: git add . git commit -m "Initial commit" git push origin main Validate Code in GitHub After pushing the code, navigate to your GitHub repository (helloworldcicd) in the browser and verify that all files have been successfully uploaded. This ensures that the pipeline will be able to fetch the source code correctly from the main branch. Configure Code Build Now that we have the SAM template, Lambda code and a git repo ready, let's configure AWS Code Build to build the code and store the artifacts in a s3 bucket. To build a code build project using AWS Code Build, follow the steps as below: Go to AWS Console → CodeBuild → Create project Select Source: GitHub Select Environment: Managed image and Compute option Select Buildspec: Use the buildspec.yml in your repo Service role: Create new or use existing with necessary permissions (S3, CloudFormation, Lambda, API) Create AWS Code Pipeline Now that the CodeBuild project is set up, let's configure AWS CodePipeline to automate the CI/CD process. Navigate to AWS Console Go to CodePipeline → click Create pipeline. Pipeline Settings Enter a name for your pipeline (e.g., HelloWorldCICDPipeline). Optionally, select
How do you build your software application?
Do you still rely on a manual build process?
Do you have a dedicated team member who runs the build multiple times a day or handles deployments to development, test, or production environments?
If so, this article is for you.
In this article, I will implement an AWS Code Pipeline for a serverless function and API built using AWS Lambda and API Gateway.
The Lambda function itself is very simple and it returns just a 'Hello World' however, however, I will demonstrate the process of building the function and API using AWS SAM (Serverless Application Model) and validate it locally. Once I have validated the function locally using AWS SAM, I will integrate it with GitHub and AWS Code Pipeline for the CICD.
With this CICD Pipeline, each time a commit is pushed to the git repo, AWS Pipeline will be triggered and updated stack will be automatically deployed into AWS cloud.
Before diving in, let’s review the architecture diagram to understand how these components interact.
Introduction to AWS SAM
AWS SAM (Serverless Application Model) is a framework that simplifies the development, testing and deployment of serverless application on AWS. It uses a template file in YAML format that defines the resources like Lambda function, API, permission policies and more.
With AWS SAM, developers can build and test the lambda function locally before deploying those to the AWS Cloud. An ability to develop and test locally enables the developers to debug the functions in a speedy reducing the cycle time for the testing and deployment.
With commands like SAM Build, SAM Local Invoke and SAM Deploy, developers can use command line to accelerate the build, validate and deploy the resources.
Overview of AWS Code Pipeline
AWS Code Pipeline is a fully managed, serverless service that enables continuous integration and continuous delivery (CI/CD) for software application releases. It allows software teams to build CI/CD workflows as a series of stages, such as source, build, test, and deploy.
AWS Code Pipeline integrates seamlessly with source control tools like GitHub and AWS services such as CodeBuild and CodeDeploy. By creating a CI/CD pipeline, teams can significantly reduce or even eliminate manual efforts and ensure consistency across different environments like development, testing, and production. This automation empowers teams to release software more frequently and reliably.
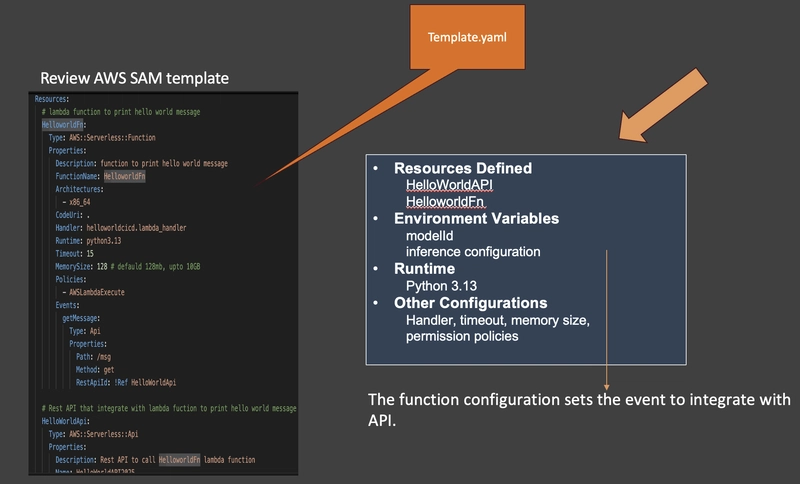
Review AWS SAM Template
The AWS Serverless Application Model (SAM) template defines the infrastructure required for the lambda function and API.
Here’s what the SAM template for this solution looks like:
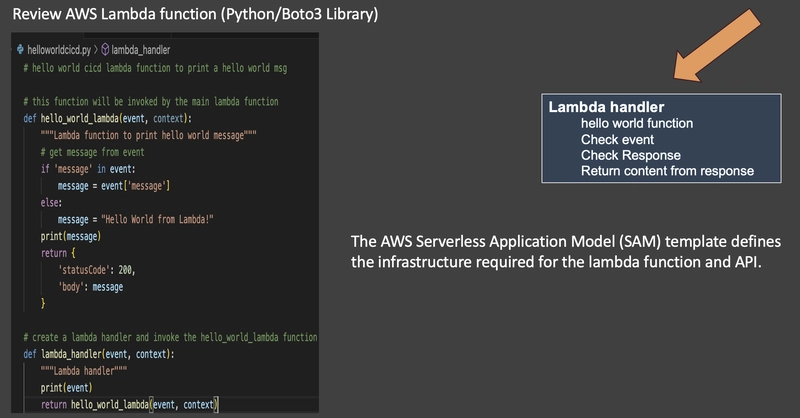
Review AWS Lambda function (Python/Boto3 Library)
Lambda function is developed using Python and uses the Boto3 library to interact with Amazon Lambda and API.
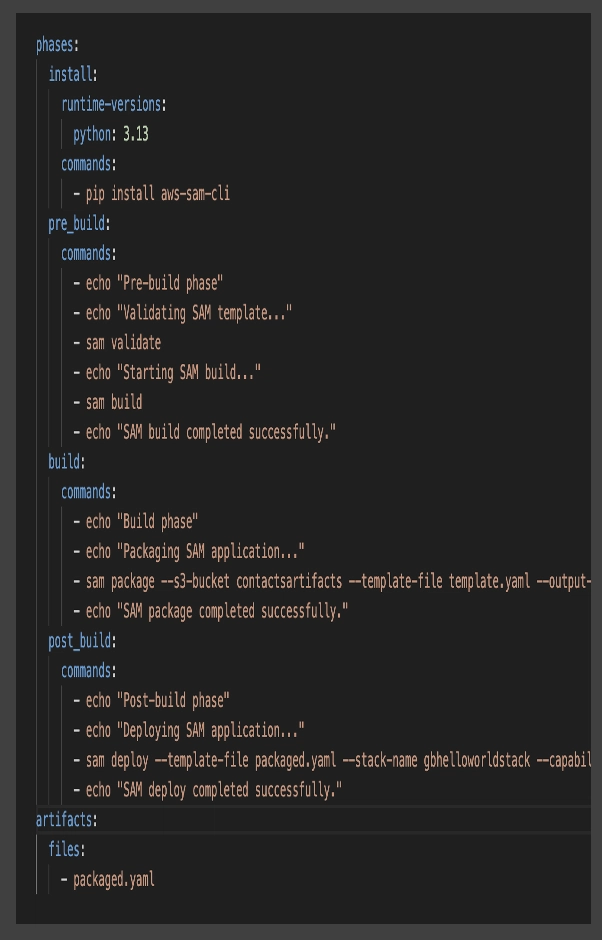
Review Buildspec.yml
A buildspec.yml file is a configuration file that tells AWS CodeBuild how to build your project. It's written in a simple YAML format and does these main things:
- Sets up your build environment
- Lists the commands to run during different phases of building:
install phase: where you install dependencies
pre_build phase: for setup steps before the main build
build phase: where the actual building happens
post_build phase: for cleanup and final steps after building
- Defines what files to save after building as Artifacts like packaged SAM template or compressed lambda code.
- Reports or test results
This file stays in the root of your source code repository and helps automate the build process as part of CI/CD pipeline with AWS CodePipeline and AWS SAM.
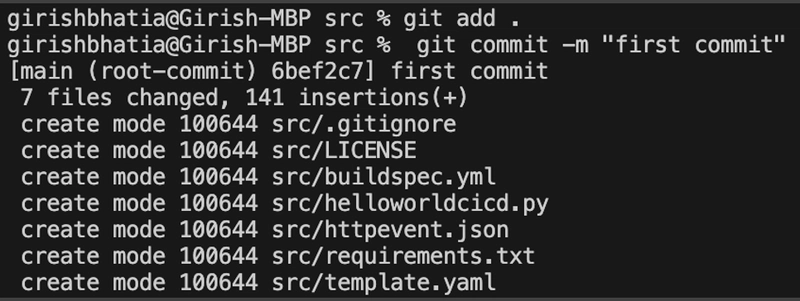
Commit code to Git Repo
For this example, the GitHub repository is named helloworldcicd. Once your project files are ready, follow these steps to commit and push the code to your repository:
git add .
git commit -m "Initial commit"
git push origin main
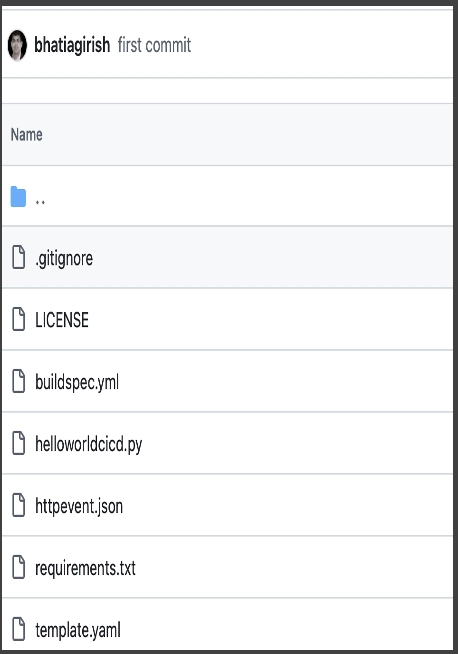
Validate Code in GitHub
After pushing the code, navigate to your GitHub repository (helloworldcicd) in the browser and verify that all files have been successfully uploaded. This ensures that the pipeline will be able to fetch the source code correctly from the main branch.
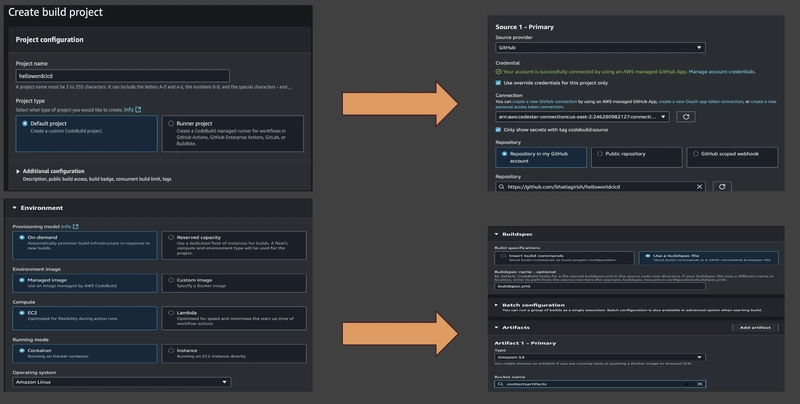
Configure Code Build
Now that we have the SAM template, Lambda code and a git repo ready, let's configure AWS Code Build to build the code and store the artifacts in a s3 bucket.
To build a code build project using AWS Code Build, follow the steps as below:
- Go to AWS Console → CodeBuild → Create project
- Select Source: GitHub
- Select Environment: Managed image and Compute option
- Select Buildspec: Use the buildspec.yml in your repo
- Service role: Create new or use existing with necessary permissions (S3, CloudFormation, Lambda, API)
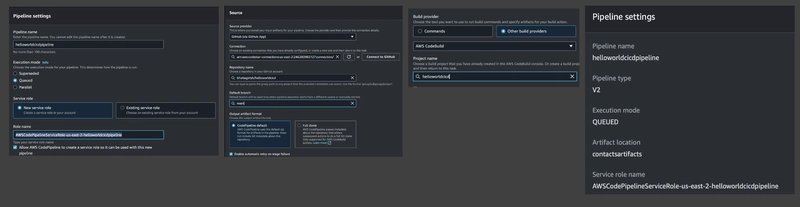
Create AWS Code Pipeline
Now that the CodeBuild project is set up, let's configure AWS CodePipeline to automate the CI/CD process.
Navigate to AWS Console Go to CodePipeline → click Create pipeline.
Pipeline Settings
- Enter a name for your pipeline (e.g., HelloWorldCICDPipeline).
- Optionally, select an S3 bucket to store pipeline artifacts under Advanced settings.
Add Source Stage
- Source provider: GitHub (connect to your GitHub account if not already connected)
- Repository: Select your repo (e.g., helloworldcicd)
- Branch: main
- Change detection: Enable GitHub webhooks for automatic triggers (recommended)
Add Build Stage
- Build provider: AWS CodeBuild
- Project: Select the build project you previously configured
Deploy Stage
- Skip deployment stage Since deployment is handled inside the buildspec.yml using sam deploy, choose to skip the deploy stage here.
Review and Create
- Review all your settings
- Click Create pipeline
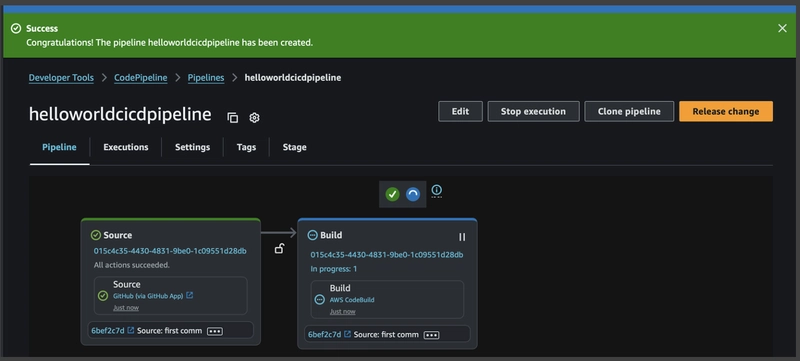
Review AWS Code Pipeline
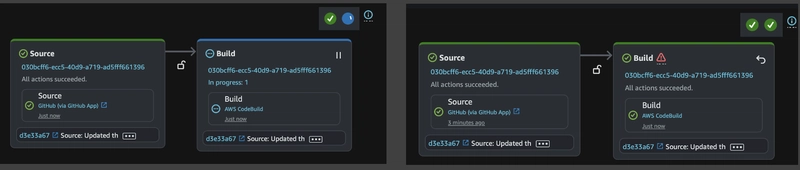
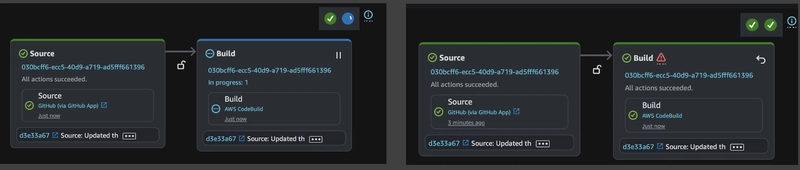
The AWS Code Pipeline has been successfully created with the configured Source and Build stages. Since the pipeline is integrated with GitHub, it automatically triggers whenever a new commit is pushed to the connected branch.
In the example below, the Source stage has completed successfully, while the Build stage is still in progress.
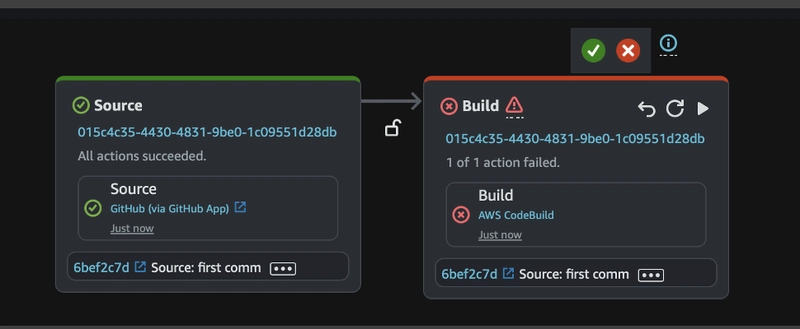
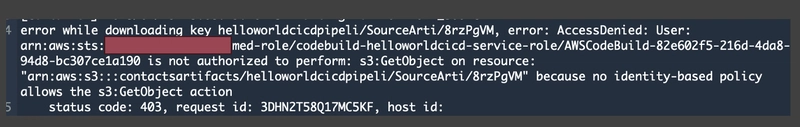
Build Stage Failed
If the Build stage does not complete and instead fails, review the error message in the CloudWatch Logs for your CodeBuild project. In this case, the failure is due to insufficient IAM policy permissions.
Review the error:
Fixing the Permission Issue
To resolve this, you’ll need to add the necessary permissions to the CodeBuild service role, allowing it to interact with required AWS services such as S3, CloudFormation, Lambda, and API Gateway.
For demonstration purposes, we're assigning full access permissions, but in a production environment, you should always follow the principle of least privilege and grant only the specific permissions required.
- Attach the following policies to the CodeBuild role:
- AmazonS3FullAccess
- AWSCloudFormationFullAccess
- AWSLambda_FullAccess
- AmazonAPIGatewayAdministrator
After updating the IAM permissions, go back to your pipeline and retry the failed build action. You should see the status progress from Failed → In Progress → Succeeded for both stages.
Validate by Invoking the deployed function and API
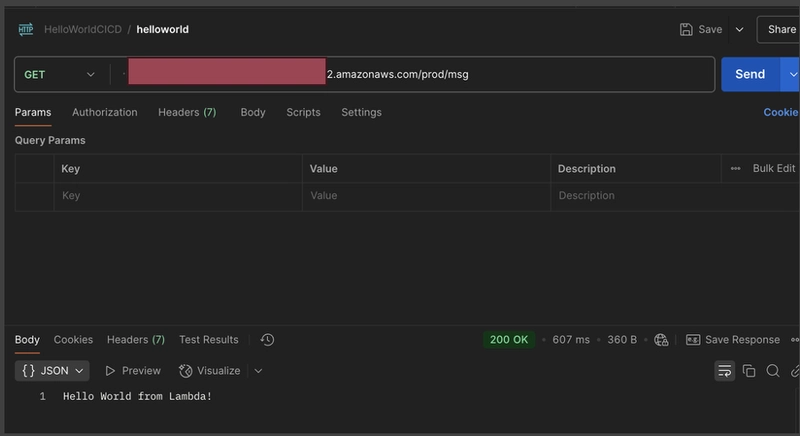
AWS CodePipeline has successfully built the code, resulting in the deployment of the Lambda function and its integration with an API Gateway endpoint. Now, let’s validate the deployment by invoking the API.
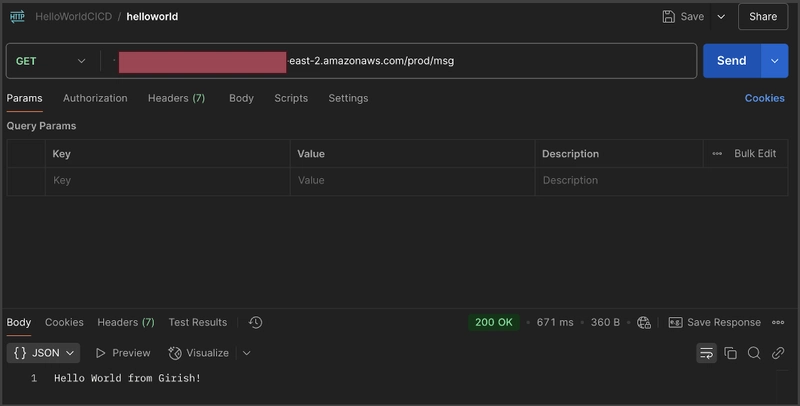
I’ll use Postman to send a request to the deployed API endpoint and review the response.
The API successfully returned the response defined in the Lambda function, confirming that the deployment and integration were successful.
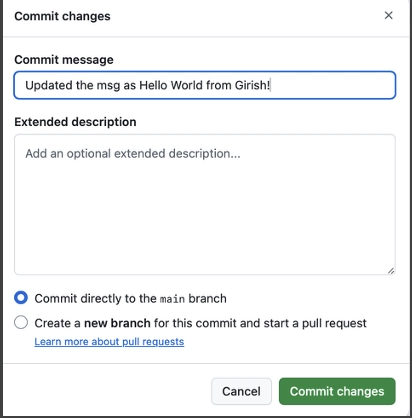
Push a code change to Git Repo
Let’s make a change to the Lambda function and commit the updated code to the Git repository.
Once the changes are pushed, this will automatically trigger the AWS Code Pipeline.
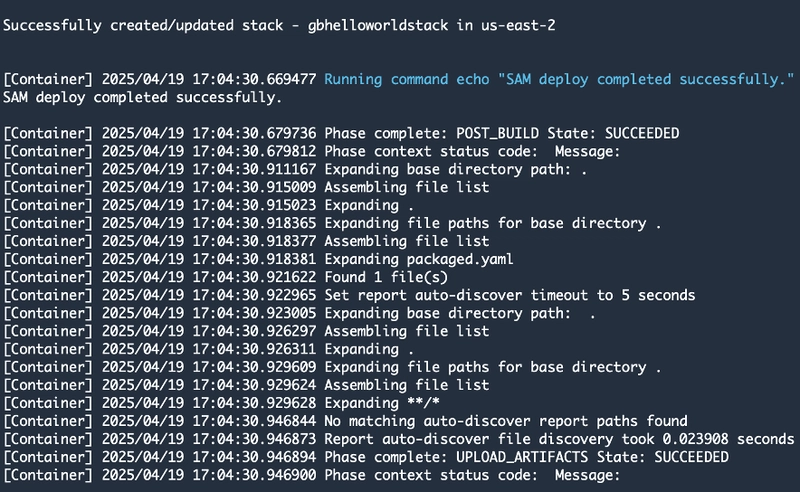
After the pipeline starts, we’ll review the build and deployment stages to confirm the updated function is successfully redeployed.
You can see that the pipeline automatically triggered the Source and Build stages, both of which completed successfully!
Validate by Invoking the deployed function and API
Since the pipeline has successfully completed, the updated Lambda function and API have been deployed. Let's validate again using Postman.
You should now see the updated message returned by the Lambda function through the API endpoint, confirming that the changes were successfully deployed.
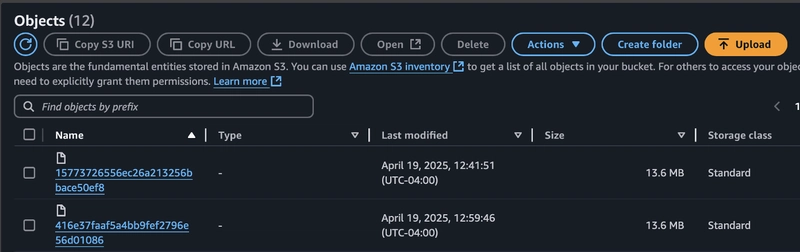
Review S3 bucket for Code artifact
You can also review the S3 bucket where AWS Code Pipeline stores the build artifacts generated during the pipeline execution.
Review Cloud Watch log
The Lambda function is integrated with CloudWatch, and a dedicated log group is automatically created.
You can view the logs by navigating to the function’s log group in the CloudWatch Logs section of the AWS Console.
Cleanup - Delete resources
Once you’ve completed this exercise, make sure to delete all the resources created to avoid unnecessary charges that could impact your overall cloud cost and budget.
In particular, remember to delete the following:
- The AWS Code Pipeline
- The CodeBuild project
- Any S3 buckets used for artifacts (if not reused elsewhere)
- The Lambda function, API Gateway, and associated CloudWatch log groups
- IAM roles created for the pipeline and build process (if they’re not reused)
Conclusion
In this article, I demonstrated I demonstrated how to create a CI/CD pipeline for a Lambda function using AWS SAM.
For this solution, I used Python/Boto3 to create an API integrated with Bedrock via a Lambda function.
I hope you found this article both helpful and informative!
Thank you for reading!
Watch the video here:



































































































































































![[The AI Show Episode 143]: ChatGPT Revenue Surge, New AGI Timelines, Amazon’s AI Agent, Claude for Education, Model Context Protocol & LLMs Pass the Turing Test](https://www.marketingaiinstitute.com/hubfs/ep%20143%20cover.png)








































































































































































































































































_Muhammad_R._Fakhrurrozi_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)
_NicoElNino_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)



































































































![AirPods Pro 2 With USB-C Back On Sale for Just $169! [Deal]](https://www.iclarified.com/images/news/96315/96315/96315-640.jpg)
![Apple Releases iOS 18.5 Beta 4 and iPadOS 18.5 Beta 4 [Download]](https://www.iclarified.com/images/news/97145/97145/97145-640.jpg)
![Apple Seeds watchOS 11.5 Beta 4 to Developers [Download]](https://www.iclarified.com/images/news/97147/97147/97147-640.jpg)
![Apple Seeds visionOS 2.5 Beta 4 to Developers [Download]](https://www.iclarified.com/images/news/97150/97150/97150-640.jpg)