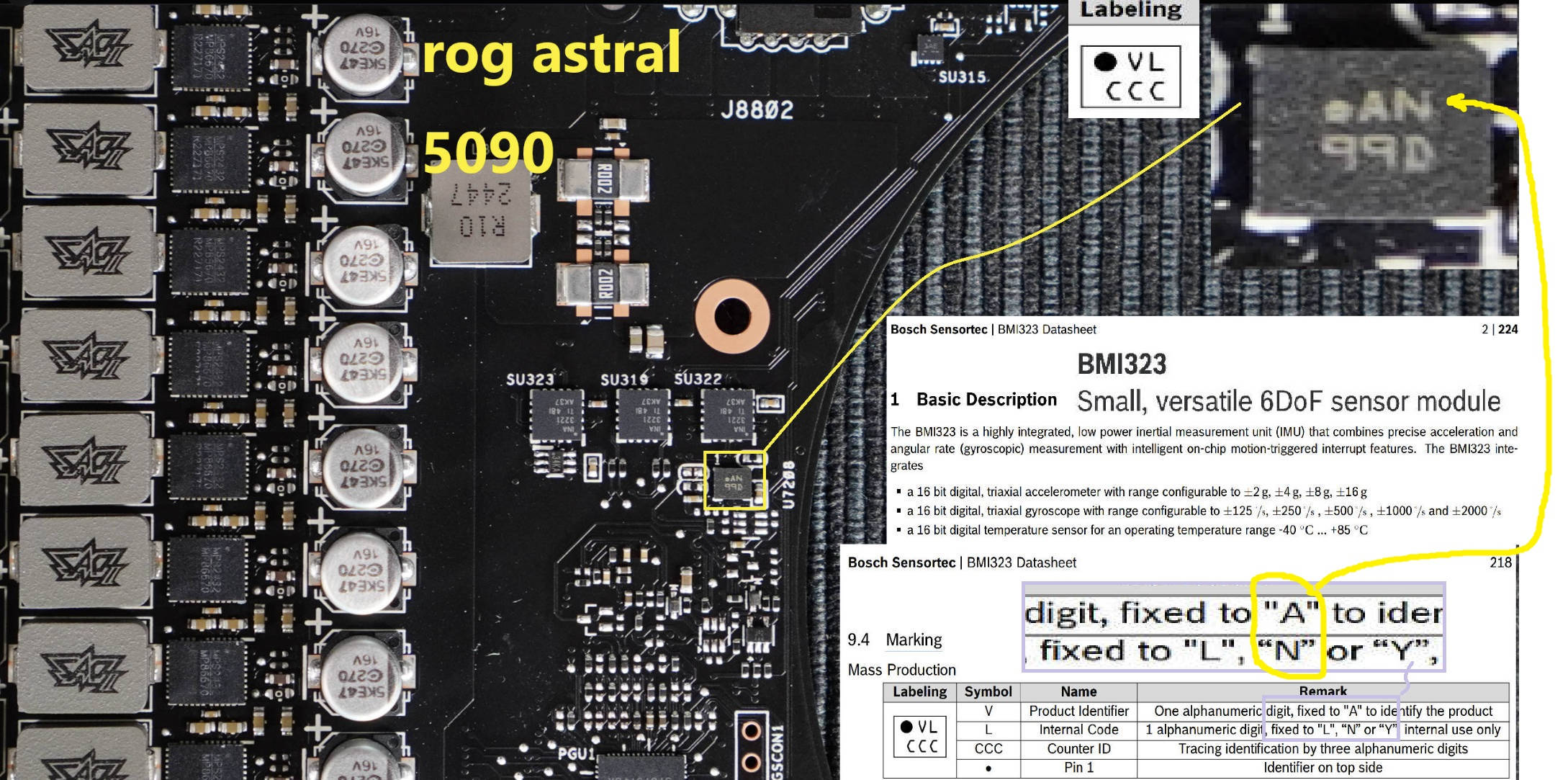
New RedExt Chrome Extension Tool for Red Teamers with Flask-based C2 Server
A sophisticated new red team tool called RedExt has recently been released, combining a Manifest V3 Chrome extension with a Flask-based Command and Control (C2) server to create a powerful framework for authorized security operations. This innovative tool enables comprehensive browser data collection and analysis through a modern dark-themed dashboard interface. RedExt operates as a […] The post New RedExt Chrome Extension Tool for Red Teamers with Flask-based C2 Server appeared first on Cyber Security News.

A sophisticated new red team tool called RedExt has recently been released, combining a Manifest V3 Chrome extension with a Flask-based Command and Control (C2) server to create a powerful framework for authorized security operations.
This innovative tool enables comprehensive browser data collection and analysis through a modern dark-themed dashboard interface.
RedExt operates as a beacon-based system that executes tasks assigned by the C2 server.
The framework includes multiple data collection modules that can extract sensitive browser information, including cookies, browsing history, screenshots, clipboard contents, DOM structures, local storage data, and detailed system information.
RedExt, developed by Security researcher ShadowByte, can operate entirely within the browser context, leveraging Chrome’s extensive API capabilities while maintaining a persistent connection to its command infrastructure.
The framework’s architecture consists of two main components: a Chrome extension built on Manifest V3 and a Python Flask server with SQLite database backend.
This combination allows for efficient task assignment, data collection, and centralized analysis.
RedExt Implementation and Deployment
Security professionals can deploy RedExt by first setting up the C2 server with a few simple commands:
The Chrome extension can then be configured by editing the C2 server address in the background.js file:
Deployment options include GUI-based installation through Chrome’s extension management page or command-line installation:
Operational Functionality
Once deployed, RedExt establishes a connection between the extension (agent) and the C2 server. Security professionals can manage agents, assign tasks, and analyze collected data from the operator dashboard.

The task execution system supports multiple operation types:
- DOM snapshot capture for webpage analysis
- Cookie exfiltration with domain-specific filtering
- Screenshot capture of active browser tabs
- System reconnaissance including browser environment and hardware details
- Browsing history collection with timestamps and visit frequencies
- Bookmark extraction preserving folder structures and metadata
While RedExt demonstrates the potential vulnerabilities of browser extensions, it is explicitly designed for authorized red team operations and security research. The GitHub repository emphasizes: “This tool is designed for authorized operations only.”
Security experts note that tools like RedExt highlight the importance of proper extension vetting and browser security policies.
Organizations should review their browser security controls and consider implementing extension whitelisting to mitigate similar threats..
RedExt is publicly available on GitHub with comprehensive documentation including installation guides, usage instructions, and technical details.
As browser-based attack vectors continue to evolve, tools like RedExt provide valuable insights for both offensive security professionals and defenders seeking to understand and mitigate emerging threats in the browser landscape.
Are you from the SOC and DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.
The post New RedExt Chrome Extension Tool for Red Teamers with Flask-based C2 Server appeared first on Cyber Security News.



































































































































































![[The AI Show Episode 143]: ChatGPT Revenue Surge, New AGI Timelines, Amazon’s AI Agent, Claude for Education, Model Context Protocol & LLMs Pass the Turing Test](https://www.marketingaiinstitute.com/hubfs/ep%20143%20cover.png)





























































































































![[DEALS] Koofr Cloud Storage: Lifetime Subscription (1TB) (80% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)










































































































































_Muhammad_R._Fakhrurrozi_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)
_NicoElNino_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)




























































































![What Google Messages features are rolling out [April 2025]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2023/12/google-messages-name-cover.png?resize=1200%2C628&quality=82&strip=all&ssl=1)












![M4 MacBook Air Drops to Just $849 - Act Fast! [Lowest Price Ever]](https://www.iclarified.com/images/news/97140/97140/97140-640.jpg)
![Apple Smart Glasses Not Close to Being Ready as Meta Targets 2025 [Gurman]](https://www.iclarified.com/images/news/97139/97139/97139-640.jpg)
![iPadOS 19 May Introduce Menu Bar, iOS 19 to Support External Displays [Rumor]](https://www.iclarified.com/images/news/97137/97137/97137-640.jpg)