Zero Trust Architecture
Zero Trust Architecture: Never Trust, Always Verify Introduction: Zero Trust Architecture (ZTA) is a security model based on the principle of "never trust, always verify." Unlike traditional perimeter-based security, which assumes trust within the network, ZTA assumes no implicit trust granted to any user, device, or network segment, regardless of location. Every access request is verified before granting access, minimizing the impact of breaches. Prerequisites: Implementing ZTA requires a robust infrastructure capable of continuous monitoring and verification. Key prerequisites include: Strong Identity and Access Management (IAM): Robust authentication and authorization mechanisms are crucial. Microsegmentation: Network segmentation isolates resources, limiting the blast radius of potential breaches. Comprehensive logging and monitoring: Continuous monitoring and detailed logs are essential for threat detection and response. Data loss prevention (DLP) tools: Prevent sensitive data from leaving the network. Features: ZTA employs several key features: Least privilege access: Users and devices are only granted access to the resources absolutely necessary for their tasks. Multi-factor authentication (MFA): Multiple authentication factors enhance security. Device posture assessment: Verifies the security posture of devices before granting access. This might involve checking for up-to-date antivirus software. Continuous monitoring and analytics: Real-time monitoring and analytics provide insights into user behavior and potential threats. Advantages: Reduced attack surface: Limiting access significantly reduces the potential impact of successful attacks. Improved security posture: Continuous verification and strong authentication enhance overall security. Enhanced compliance: ZTA helps organizations meet various security and compliance regulations. Disadvantages: Increased complexity: Implementing and managing ZTA can be complex and require specialized expertise. Higher costs: The infrastructure and management tools needed for ZTA can be expensive. Performance impact: The continuous verification process may impact application performance. Conclusion: Zero Trust Architecture is a transformative security approach that significantly enhances security posture in today's distributed and cloud-centric environments. While implementing ZTA presents challenges, its advantages outweigh the disadvantages, making it a crucial consideration for organizations seeking robust and adaptable security. A phased approach, focusing on high-value assets initially, is often recommended for successful implementation.
Zero Trust Architecture: Never Trust, Always Verify
Introduction:
Zero Trust Architecture (ZTA) is a security model based on the principle of "never trust, always verify." Unlike traditional perimeter-based security, which assumes trust within the network, ZTA assumes no implicit trust granted to any user, device, or network segment, regardless of location. Every access request is verified before granting access, minimizing the impact of breaches.
Prerequisites:
Implementing ZTA requires a robust infrastructure capable of continuous monitoring and verification. Key prerequisites include:
- Strong Identity and Access Management (IAM): Robust authentication and authorization mechanisms are crucial.
- Microsegmentation: Network segmentation isolates resources, limiting the blast radius of potential breaches.
- Comprehensive logging and monitoring: Continuous monitoring and detailed logs are essential for threat detection and response.
- Data loss prevention (DLP) tools: Prevent sensitive data from leaving the network.
Features:
ZTA employs several key features:
- Least privilege access: Users and devices are only granted access to the resources absolutely necessary for their tasks.
- Multi-factor authentication (MFA): Multiple authentication factors enhance security.
- Device posture assessment: Verifies the security posture of devices before granting access. This might involve checking for up-to-date antivirus software.
- Continuous monitoring and analytics: Real-time monitoring and analytics provide insights into user behavior and potential threats.
Advantages:
- Reduced attack surface: Limiting access significantly reduces the potential impact of successful attacks.
- Improved security posture: Continuous verification and strong authentication enhance overall security.
- Enhanced compliance: ZTA helps organizations meet various security and compliance regulations.
Disadvantages:
- Increased complexity: Implementing and managing ZTA can be complex and require specialized expertise.
- Higher costs: The infrastructure and management tools needed for ZTA can be expensive.
- Performance impact: The continuous verification process may impact application performance.
Conclusion:
Zero Trust Architecture is a transformative security approach that significantly enhances security posture in today's distributed and cloud-centric environments. While implementing ZTA presents challenges, its advantages outweigh the disadvantages, making it a crucial consideration for organizations seeking robust and adaptable security. A phased approach, focusing on high-value assets initially, is often recommended for successful implementation.





































































































































































![[The AI Show Episode 145]: OpenAI Releases o3 and o4-mini, AI Is Causing “Quiet Layoffs,” Executive Order on Youth AI Education & GPT-4o’s Controversial Update](https://www.marketingaiinstitute.com/hubfs/ep%20145%20cover.png)





























































































































![[FREE EBOOKS] Learn Computer Forensics — 2nd edition, AI and Business Rule Engines for Excel Power Users & Four More Best Selling Titles](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)





![From Art School Drop-out to Microsoft Engineer with Shashi Lo [Podcast #170]](https://cdn.hashnode.com/res/hashnode/image/upload/v1746203291209/439bf16b-c820-4fe8-b69e-94d80533b2df.png?#)






































































































(1).jpg?#)



















![Apple to Split iPhone Launches Across Fall and Spring in Major Shakeup [Report]](https://www.iclarified.com/images/news/97211/97211/97211-640.jpg)
![Apple to Move Camera to Top Left, Hide Face ID Under Display in iPhone 18 Pro Redesign [Report]](https://www.iclarified.com/images/news/97212/97212/97212-640.jpg)











_Inge_Johnsson-Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)






















































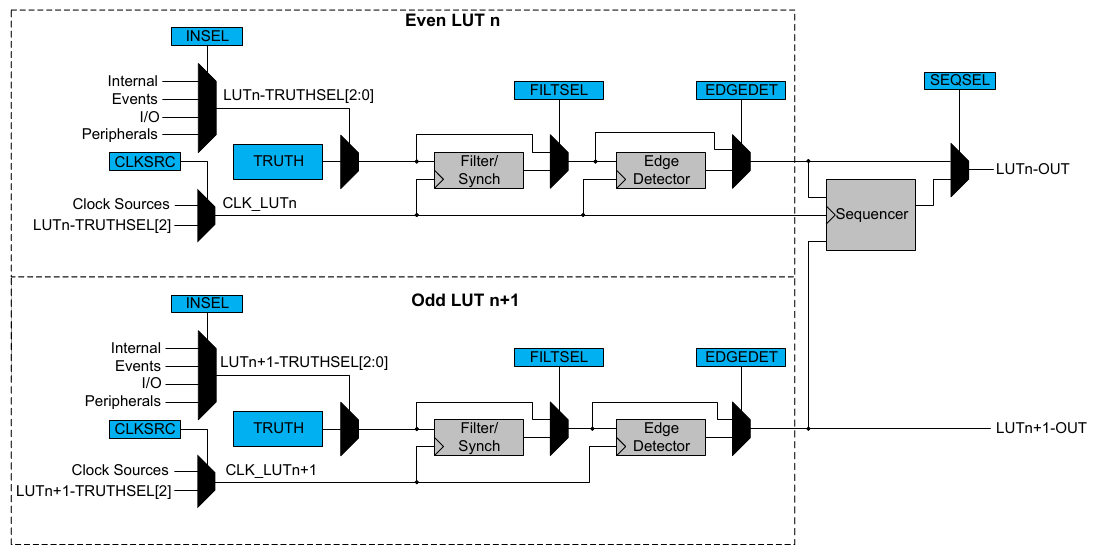
















































![Apple Developing Battery Case for iPhone 17 Air Amid Battery Life Concerns [Report]](https://www.iclarified.com/images/news/97208/97208/97208-640.jpg)
![AirPods 4 On Sale for $99 [Lowest Price Ever]](https://www.iclarified.com/images/news/97206/97206/97206-640.jpg)