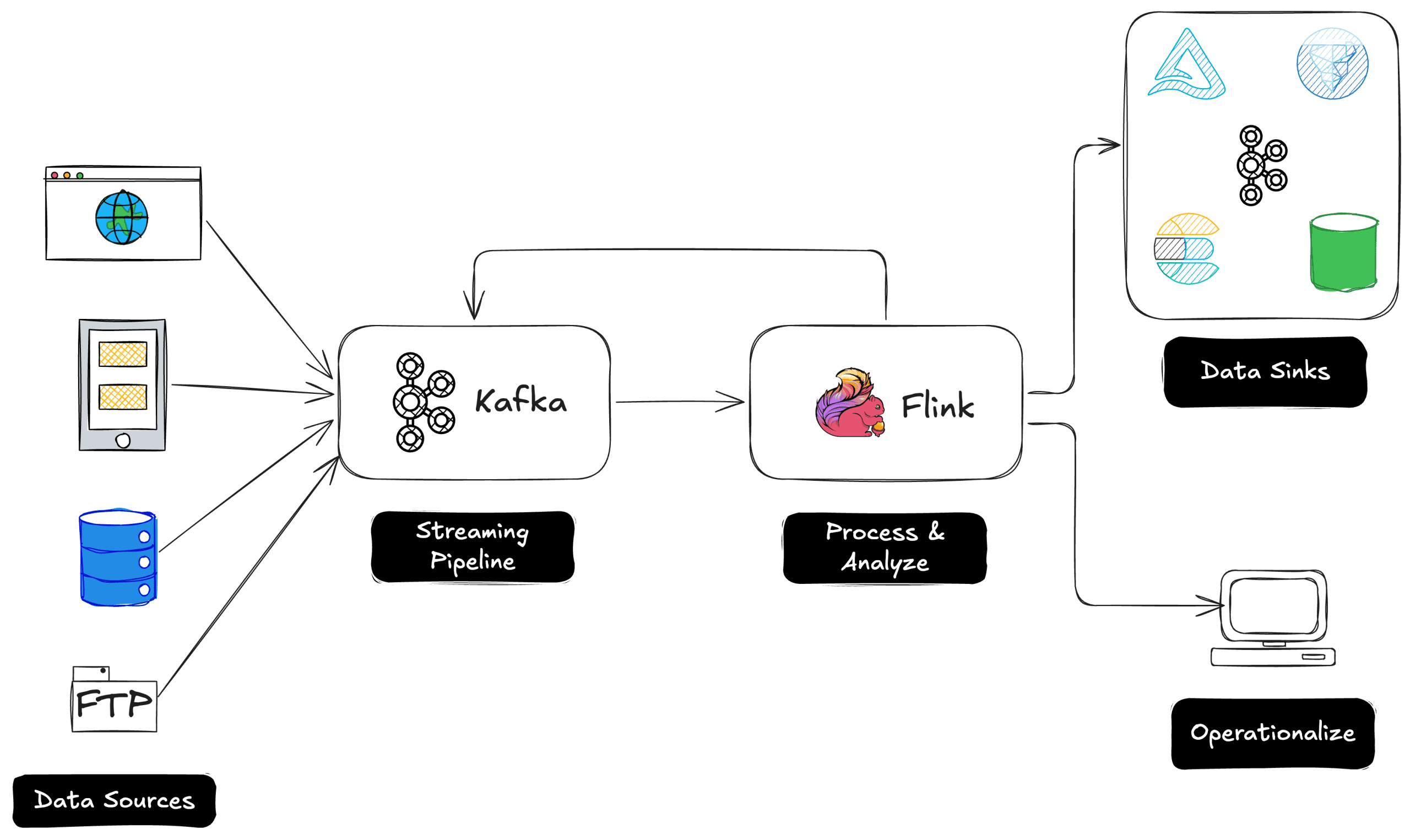
Windows Defender Application Control Bypassed Using Operationalizing Browser Exploits
Researchers have uncovered a sophisticated technique to bypass Windows Defender Application Control (WDAC), a critical Windows security feature designed to prevent unauthorized code execution. The bypass leverages vulnerabilities in trusted Electron applications, effectively circumventing one of Microsoft’s most robust security mechanisms aimed at high-assurance environments. By exploiting the underlying V8 JavaScript engine used in these […] The post Windows Defender Application Control Bypassed Using Operationalizing Browser Exploits appeared first on Cyber Security News.

Researchers have uncovered a sophisticated technique to bypass Windows Defender Application Control (WDAC), a critical Windows security feature designed to prevent unauthorized code execution.
The bypass leverages vulnerabilities in trusted Electron applications, effectively circumventing one of Microsoft’s most robust security mechanisms aimed at high-assurance environments.
By exploiting the underlying V8 JavaScript engine used in these applications, attackers can execute malicious code even under the strictest WDAC policies.
WDAC functions as an application whitelisting mechanism, enforcing policies that only allow explicitly trusted executables, scripts, and drivers to run on a system.
It’s particularly valuable in environments where system integrity is paramount, making this discovery especially concerning for organizations relying on WDAC as a core security control.
The bypass demonstrates how trusted applications can become vehicles for attack when they contain exploitable vulnerabilities.
IBM analysts from the X-Force team identified the novel approach, which they’ve dubbed “bring your own vulnerable application.”
According to lead researcher Valentina Palmiotti, the technique involves targeting signed, trusted Electron applications that contain vulnerabilities in their implementation of the V8 JavaScript engine.
Since these applications are already whitelisted in WDAC policies, they provide an ideal vector for executing arbitrary code.
The research revealed that even when an organization implements the most stringent WDAC configurations, these can be circumvented by exploiting vulnerabilities in trusted applications.
What makes this attack particularly stealthy is that the execution occurs within the context of a browser-like process, where behaviors that might otherwise trigger endpoint detection and response (EDR) systems appear normal, such as having RWX (read-write-execute) memory mapped for Just-In-Time compilation.
Exploit Mechanism: Argument Smuggling and JIT Optimization Challenges
The bypass technique employs what researchers termed “argument smuggling” to execute malicious code.
.webp)
This method involves overwriting specific fields in JavaScript function objects to store crucial information needed by the payload.
By manipulating these objects, attackers can pass arguments to shellcode without traditional parameter passing mechanisms.
// Example of how argument smuggling works within the exploit
// Overwriting unused fields in the JSFunction object to store payload information
function smuggleArguments(jsFunc, payloadAddress, payloadSize) {
// Store crucial information in unused object fields
write64(jsFunc + OFFSET_PAYLOAD_ADDRESS, payloadAddress);
write64(jsFunc + OFFSET_PAYLOAD_SIZE, payloadSize);
}The researchers encountered significant challenges with TurboFan’s JIT optimization, which would deduplicate identical floating-point values in memory.
This imposed limitations on shellcode smuggling, requiring careful crafting of unique values to prevent optimization.
To overcome inconsistent offsets across different Windows versions, they developed a “Just-in-time exploit engine” that would try multiple possible offsets until successful execution was achieved.
While Electron has introduced an experimental integrity verification feature that could prevent such attacks in newer versions, many popular applications have yet to implement this protection.
This leaves numerous environments vulnerable to this sophisticated WDAC bypass technique, highlighting the ongoing cat-and-mouse game between security mechanisms and innovative exploitation methods.
How SOC Teams Save Time and Effort with ANY.RUN - Live webinar for SOC teams and managers
The post Windows Defender Application Control Bypassed Using Operationalizing Browser Exploits appeared first on Cyber Security News.
![[Webinar] From Code to Cloud to SOC: Learn a Smarter Way to Defend Modern Applications](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjLbNLee9VlpBpNmlxQSBF7IHwrQajzAJWYjhcHTIVVqzroGXrpk_x9Sbbua1Xi-QtO9jbcX1canKTWWzfaOshSarJol1Ude7LNQMeV5B2x71gaXxWg_cjEJ3bPuuoyyyMLgWB9hCtZ1PV5j3QOGByinGCAETqul2WWz-mVYiuERYWPVu7ob8lSckM-ocw/s1600/soc.jpg?#)




































































































































































![[The AI Show Episode 147]: OpenAI Abandons For-Profit Plan, AI College Cheating Epidemic, Apple Says AI Will Replace Search Engines & HubSpot’s AI-First Scorecard](https://www.marketingaiinstitute.com/hubfs/ep%20147%20cover.png)

























![How to Enable Remote Access on Windows 10 [Allow RDP]](https://bigdataanalyticsnews.com/wp-content/uploads/2025/05/remote-access-windows.jpg)































































































![[DEALS] The 2025 Ultimate GenAI Masterclass Bundle (87% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)












































![Artist Shocked To Find Her Poster Designs From 2017 In Bungie's Marathon: 'A Major Company Has Deemed It Easier To Pay A Designer To Imitate Or Steal My Work Than To Write Me An Email' [Update]](https://i.kinja-img.com/image/upload/c_fill,h_675,pg_1,q_80,w_1200/4ce7afff77473c3cccca9cc349c42790.jpg)




















































































-Olekcii_Mach_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)

























































































![Apple using sketchy warning for apps bought using third-party payment systems [Updated]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/05/Apple-using-scary-looking-warning-for-apps-bought-using-third-party-payment-systems.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)



















![Sony WH-1000XM6 Unveiled With Smarter Noise Canceling and Studio-Tuned Sound [Video]](https://www.iclarified.com/images/news/97341/97341/97341-640.jpg)


![Watch Aston Martin and Top Gear Show Off Apple CarPlay Ultra [Video]](https://www.iclarified.com/images/news/97336/97336/97336-640.jpg)