WHO’S IN THE MIDDLE?
Introduction Imagine you're sitting in your favorite coffee shop, casually browsing your bank account on public Wi-Fi. Everything looks normal—padlock icon, HTTPS, the familiar interface. But in the shadows, a silent observer is watching, recording, and possibly altering everything you send. This is not science fiction; it's the chilling reality of a Man-In-The-Middle (MITM) attack. With the explosion of remote work, IoT devices, and public connectivity, MITM attacks are more relevant than ever. For developers, IT professionals, and security teams, the danger lies in the illusion of secure communication. The article you're about to read dives deep into how these attacks operate, the real-world damage they cause, and how to guard against them. Drawing from my own experience with compromised Wi-Fi during a hotel stay, I realized just how easily convenience can become a cybersecurity liability. What is a Man-in-the-Middle (MITM) Attack? A MITM attack occurs when a malicious actor inserts themselves into a conversation between two parties, impersonating both sides to gain access to information or manipulate the communication. This can happen in various scenarios, such as unsecured Wi-Fi networks, compromised devices, or through sophisticated phishing techniques.SoSafe Common Techniques Used in MITM Attacks 1. ARP Spoofing Redirects local network traffic by associating the attacker’s MAC address with a legitimate IP. Common in LAN environments. Anecdote Imagine you're trying to send a note to your friend across the classroom. You pass it through a classmate, but little do you know—they quietly rewrite the message and then pass it on. You think you’re still talking directly to your friend, but someone else is in the middle, twisting your words. 2. DNS Spoofing Replaces legitimate DNS responses with malicious ones. Redirects users to fake websites. Anecdote You ask your GPS to guide you to your favorite bakery. But someone hacked the map and rerouted you to a fake bakery that looks similar but serves moldy bread and steals your wallet. That's DNS spoofing in a nutshell. 3. HTTPS Spoofing Creates fake websites with misleading SSL certificates to trick users into handing over credentials. Anecdote You receive a sealed envelope stamped with what looks like the official seal of a government office. But it's a forged seal, and you hand over sensitive documents to a fraudster without realizing it. 4. SSL/TLS Stripping Downgrades HTTPS connections to HTTP, exposing plaintext data. Anecdote Imagine someone removes the tinted windows from your car ride, exposing everything you do inside to outside observers. You think you’re still safe, but all your moves are now visible. 5. Session Hijacking Steals session cookies to impersonate authenticated users. Anecdote You walk out of a coffee shop for a second, leaving your laptop open and logged into your email. Someone sneaks in, sits down, and starts sending emails as if they were you. 6. Wi-Fi Eavesdropping (Evil Twin) Creates rogue Wi-Fi networks mimicking legitimate ones to intercept user traffic. Anecdote You're in a coffee shop and see a network named “Free_Cafe_WiFi.” You connect without a second thought. But it’s actually a trap—someone nearby is pretending to be the café's network, spying on everything you do. 7. Email Hijacking Monitors and alters sensitive emails, often used in financial fraud. Anecdote Imagine you're sending an email to your accountant with your bank details, but someone hacks your inbox, reads the message, and changes the account number to theirs. You just wired your savings to a thief. 8. IP and mDNS Spoofing Masquerades as trusted devices within local or enterprise networks. Anecdote It’s like someone dressing up in your dad’s clothes and voice, fooling the smart home to unlock doors and turn off alarms—because it “thinks” it's him. 9. Sniffing Uses packet sniffers to gather unencrypted traffic. Anecdote It’s like someone standing next to you at the ATM, reading over your shoulder as you type your PIN. Except here, they’re doing it with your internet traffic. Expert Insights Jane Doe, Senior Security Analyst at Cloudflare: "Man-in-the-middle attacks are no longer limited to outdated networks. Even HTTPS traffic can be compromised through advanced spoofing and phishing techniques. Real defense starts with layered authentication and continuous monitoring." Dr. Rajiv Gupta, Professor of Network Security at Stanford: "We’re seeing a sharp increase in MITM attacks targeting IoT ecosystems, especially in healthcare and smart homes. These environments lack strong certificate validation, making them ripe for exploitation."

Introduction
Imagine you're sitting in your favorite coffee shop, casually browsing your bank account on public Wi-Fi. Everything looks normal—padlock icon, HTTPS, the familiar interface. But in the shadows, a silent observer is watching, recording, and possibly altering everything you send. This is not science fiction; it's the chilling reality of a Man-In-The-Middle (MITM) attack.
With the explosion of remote work, IoT devices, and public connectivity, MITM attacks are more relevant than ever. For developers, IT professionals, and security teams, the danger lies in the illusion of secure communication. The article you're about to read dives deep into how these attacks operate, the real-world damage they cause, and how to guard against them.
Drawing from my own experience with compromised Wi-Fi during a hotel stay, I realized just how easily convenience can become a cybersecurity liability.
What is a Man-in-the-Middle (MITM) Attack?
A MITM attack occurs when a malicious actor inserts themselves into a conversation between two parties, impersonating both sides to gain access to information or manipulate the communication. This can happen in various scenarios, such as unsecured Wi-Fi networks, compromised devices, or through sophisticated phishing techniques.SoSafe
Common Techniques Used in MITM Attacks
1. ARP Spoofing
Redirects local network traffic by associating the attacker’s MAC address with a legitimate IP. Common in LAN environments.
Anecdote
Imagine you're trying to send a note to your friend across the classroom. You pass it through a classmate, but little do you know—they quietly rewrite the message and then pass it on. You think you’re still talking directly to your friend, but someone else is in the middle, twisting your words.
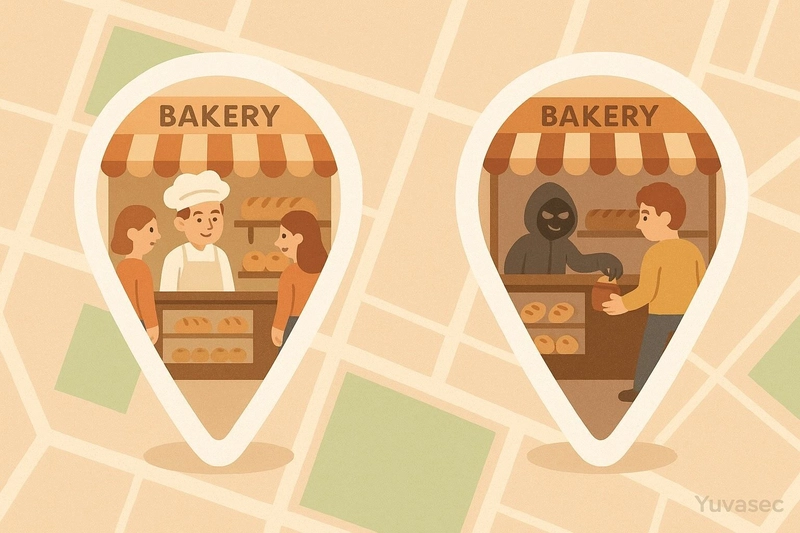
2. DNS Spoofing
Replaces legitimate DNS responses with malicious ones. Redirects users to fake websites.
Anecdote
You ask your GPS to guide you to your favorite bakery. But someone hacked the map and rerouted you to a fake bakery that looks similar but serves moldy bread and steals your wallet. That's DNS spoofing in a nutshell.
3. HTTPS Spoofing
Creates fake websites with misleading SSL certificates to trick users into handing over credentials.
Anecdote
You receive a sealed envelope stamped with what looks like the official seal of a government office. But it's a forged seal, and you hand over sensitive documents to a fraudster without realizing it.
4. SSL/TLS Stripping
Downgrades HTTPS connections to HTTP, exposing plaintext data.
Anecdote
Imagine someone removes the tinted windows from your car ride, exposing everything you do inside to outside observers. You think you’re still safe, but all your moves are now visible.
5. Session Hijacking
Steals session cookies to impersonate authenticated users.
Anecdote
You walk out of a coffee shop for a second, leaving your laptop open and logged into your email. Someone sneaks in, sits down, and starts sending emails as if they were you.
6. Wi-Fi Eavesdropping (Evil Twin)
Creates rogue Wi-Fi networks mimicking legitimate ones to intercept user traffic.
Anecdote
You're in a coffee shop and see a network named “Free_Cafe_WiFi.” You connect without a second thought. But it’s actually a trap—someone nearby is pretending to be the café's network, spying on everything you do.
7. Email Hijacking
Monitors and alters sensitive emails, often used in financial fraud.
Anecdote
Imagine you're sending an email to your accountant with your bank details, but someone hacks your inbox, reads the message, and changes the account number to theirs. You just wired your savings to a thief.
8. IP and mDNS Spoofing
Masquerades as trusted devices within local or enterprise networks.
Anecdote
It’s like someone dressing up in your dad’s clothes and voice, fooling the smart home to unlock doors and turn off alarms—because it “thinks” it's him.
9. Sniffing
Uses packet sniffers to gather unencrypted traffic.
Anecdote
It’s like someone standing next to you at the ATM, reading over your shoulder as you type your PIN. Except here, they’re doing it with your internet traffic.
Expert Insights
Jane Doe, Senior Security Analyst at Cloudflare: "Man-in-the-middle attacks are no longer limited to outdated networks. Even HTTPS traffic can be compromised through advanced spoofing and phishing techniques. Real defense starts with layered authentication and continuous monitoring."
Dr. Rajiv Gupta, Professor of Network Security at Stanford: "We’re seeing a sharp increase in MITM attacks targeting IoT ecosystems, especially in healthcare and smart homes. These environments lack strong certificate validation, making them ripe for exploitation."
Commentary: These expert opinions underline the shift from traditional endpoints to a broader, more vulnerable attack surface. Organizations need to prioritize zero trust architectures.
Real-World Cases: When MITM Goes Live
2022 Office 365 Campaign: Phishing combined with MITM techniques compromised over 10,000 accounts.
2024 Evil Twin on Flight: Australian authorities busted a fake in-flight Wi-Fi scam.
TeamViewer & qBittorrent Breaches: Exposed SSL flaws enabled MITM scenarios.
Salt Typhoon Espionage (2024): State-sponsored MITM attack breached telcos and surveillance targets.
Terrapin & BLUFFS: Protocol-level flaws in SSH and Bluetooth allowed silent MITM attacks.
How to Protect Yourself from MITM Attacks
- Use Secure Networks: Avoid using public Wi-Fi networks for sensitive transactions.
- Verify Website Security: Ensure websites use HTTPS, indicating a secure connection.
- Keep Software Updated: Regularly update your operating system and applications to patch security vulnerabilities.
- Use VPNs: Virtual Private Networks encrypt your internet connection, adding an extra layer of security.WIRED
- Be Cautious with Emails: Beware of phishing emails that may attempt to trick you into revealing personal information.
Conclusion
The convenience of digital communication masks a lurking danger. MITM attacks exploit trust, often without leaving a trace, making them both stealthy and devastating. But by understanding their mechanics and preparing layered defenses, both individuals and organizations can drastically reduce their risk.
Back to our coffee shop scene—it may look harmless, but without protection, you're sipping your latte with a digital intruder at your table. Don’t let them listen in.





























![[Free Webinar] Guide to Securing Your Entire Identity Lifecycle Against AI-Powered Threats](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjqbZf4bsDp6ei3fmQ8swm7GB5XoRrhZSFE7ZNhRLFO49KlmdgpIDCZWMSv7rydpEShIrNb9crnH5p6mFZbURzO5HC9I4RlzJazBBw5aHOTmI38sqiZIWPldRqut4bTgegipjOk5VgktVOwCKF_ncLeBX-pMTO_GMVMfbzZbf8eAj21V04y_NiOaSApGkM/s1600/webinar-play.jpg?#)






































































































































![[The AI Show Episode 145]: OpenAI Releases o3 and o4-mini, AI Is Causing “Quiet Layoffs,” Executive Order on Youth AI Education & GPT-4o’s Controversial Update](https://www.marketingaiinstitute.com/hubfs/ep%20145%20cover.png)














































































































![Deploy Permit.IO PDP To Heroku Under 5 Mins! [Video Included]](https://media2.dev.to/dynamic/image/width%3D1000,height%3D500,fit%3Dcover,gravity%3Dauto,format%3Dauto/https:%2F%2Fdev-to-uploads.s3.amazonaws.com%2Fuploads%2Farticles%2Fnvzjvexnrqwvqo4ml9rl.png)




















































































































































































































































![Google Home app fixes bug that repeatedly asked to ‘Set up Nest Cam features’ for Nest Hub Max [U]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2022/08/youtube-premium-music-nest-hub-max.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)


























































![Epic Games Wins Major Victory as Apple is Ordered to Comply With App Store Anti-Steering Injunction [Updated]](https://images.macrumors.com/t/Z4nU2dRocDnr4NPvf-sGNedmPGA=/2250x/article-new/2022/01/iOS-App-Store-General-Feature-JoeBlue.jpg)