Phishing Kit Attacks: How Businesses Can Stop Them Early
Phishing kits have changed the game and not in a good way for businesses. Today, attackers don’t need to be tech experts to launch a convincing phishing attack. Ready-made phishing kits hand them everything they need: fake websites, login pages, email templates, all bundled up and easy to use. This causes more attacks, smarter traps, and […] The post Phishing Kit Attacks: How Businesses Can Stop Them Early appeared first on Cyber Security News.

Phishing kits have changed the game and not in a good way for businesses. Today, attackers don’t need to be tech experts to launch a convincing phishing attack. Ready-made phishing kits hand them everything they need: fake websites, login pages, email templates, all bundled up and easy to use.
This causes more attacks, smarter traps, and a lot more work for security teams. For businesses, the risks go far beyond stolen data.
A successful phishing attack can shatter customer trust, damage a brand’s reputation, and lead to serious financial losses.
Let’s take a closer look at what phishing kits are, why they’ve become such a threat, and how companies can catch them before real damage is done.
What Exactly Is a Phishing Kit?
A phishing kit is a bundle of tools designed to create fake websites or emails that trick people into revealing sensitive information such as login credentials, payment details, or corporate data.
They can be very basic or quite sophisticated, featuring things like encrypted communication, automated deployment, and even customer support for hackers.
Some kits are sold as “Phishing-as-a-Service” (PHaaS) subscriptions, making the attacker’s job almost laughably easy.
Why Phishing Kits Are a Real Problem for Businesses
Phishing kits are a full-on business risk. Here’s why:
- Scale: Attackers can go after hundreds or thousands of employees at once.
- MFA bypass: Kits can steal authentication tokens, making two-factor authentication useless.
- Brand damage: Fake sites impersonate real companies, damaging their reputation and customer trust.
- Supply chain threats: Attackers can target third-party vendors to slip into corporate networks.
Even if just one employee clicks on a fake link, the consequences can ripple across an entire organization.
Real-World Example of Phishing Kit Attack: Tycoon.
Let’s look at a real phishing kit attack captured in ANY.RUN’s Interactive Sandbox.
View analysis session with Tycoon
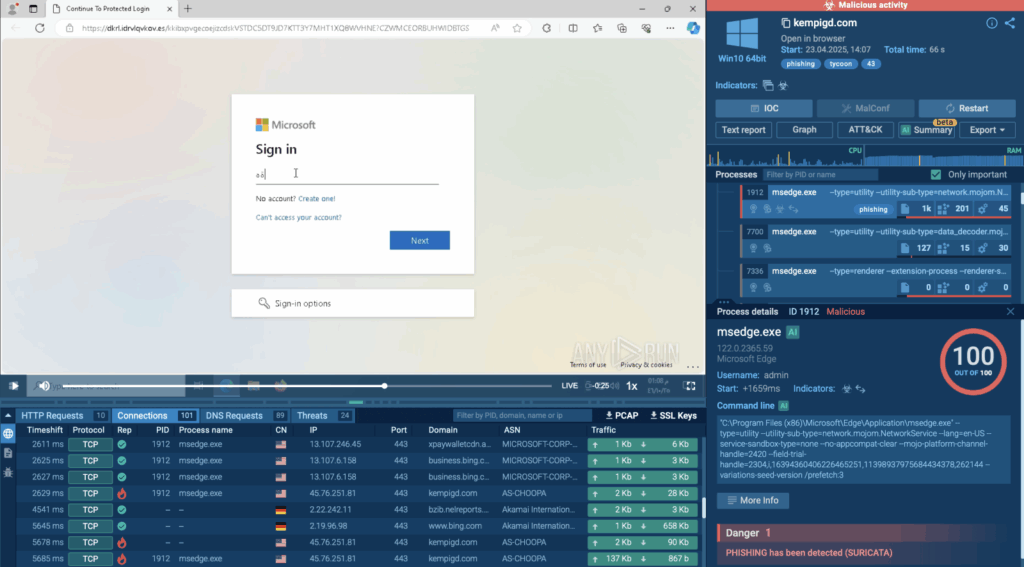
After running the analysis, ANY.RUN’s sandbox immediately flags the process as malicious, identifying phishing activity and labeling it as related to the Tycoon phishing kit.
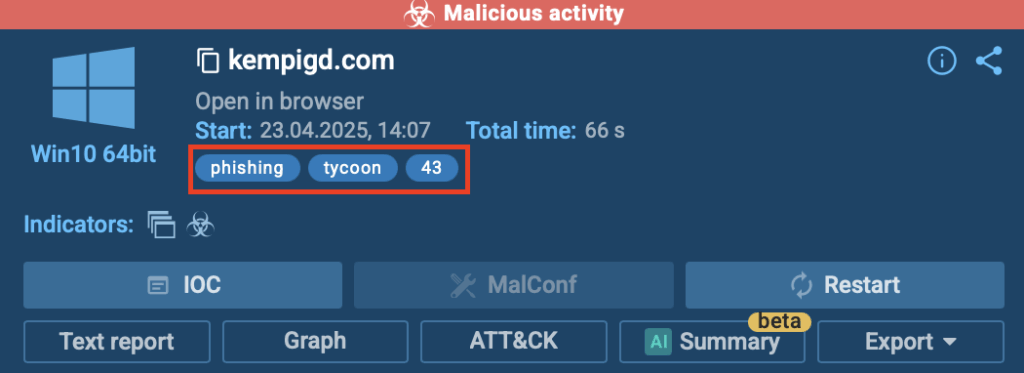
This instant detection is crucial for businesses, it helps security teams spot threats early, investigate faster, and block attacks before they cause real damage.
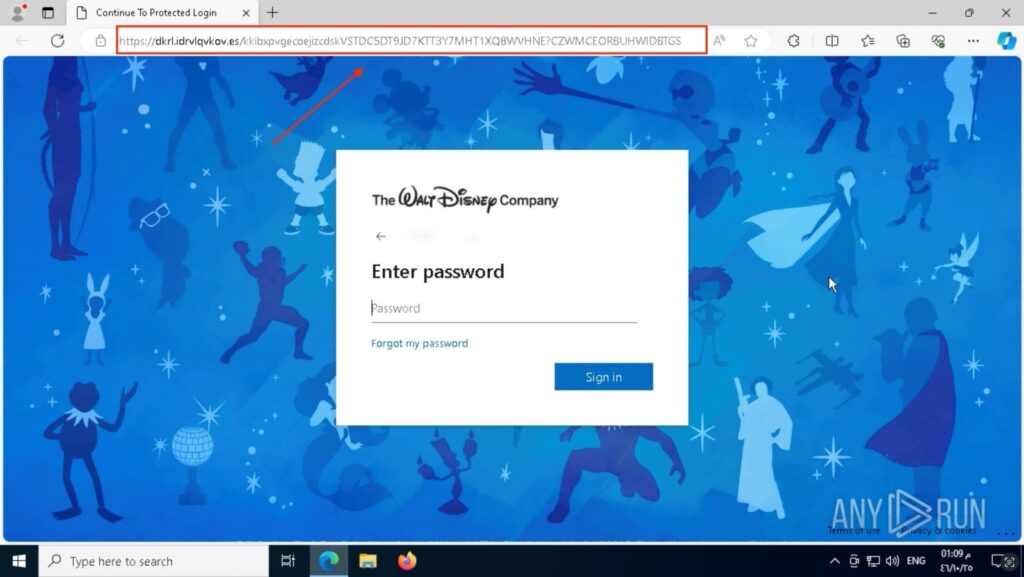
Strengthen your business security with real-time phishing analysis and proactive threat hunting: Get your 14-day ANY.RUN trial today In this case, the Tycoon2FA phishing kit was used to target Microsoft 365 users. Here’s what happened in this analysis session:
When a victim entered a fake login email with the domain @abc.com (belonging to ABC Group owned by Disney), the phishing page didn’t stay generic. It actually changed its background to a Disney-themed image.
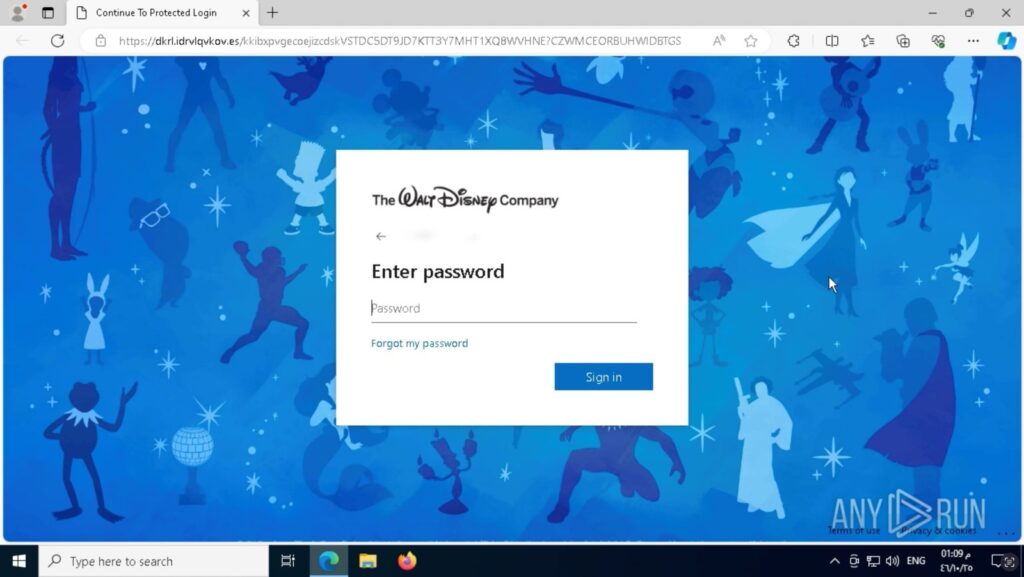
This change makes the page feel more legitimate and trick users into thinking they were logging into a real Disney/Microsoft portal.
However, if you paid close attention, the URL had no real connection to Microsoft, a classic red flag that trained employees could catch.
But that wasn’t the only technique Tycoon used.
The kit also employed system fingerprinting and geolocation filtering to selectively show the phishing page only to users in specific regions, such as Argentina, Brazil, and parts of the Middle East.
Those who didn’t match the target profile were simply redirected to unrelated websites like Tesla or Emirates, helping the phishing campaign stay under the radar.
Detect Phishing Threats Faster and Protect Your Business
Phishing kits are getting smarter, but your business can stay ahead.
ANY.RUN gives you the speed and visibility you need to catch phishing threats before they cause real damage, often detecting malicious activity in under 40 seconds.
Here’s why businesses choose ANY.RUN to fight phishing attacks:
- Real-time detection: Spot phishing pages and malicious processes as they unfold, not after.
- Fast threat identification: Detect phishing attacks and suspicious behavior in less than 40 seconds.
Detailed attack analysis: Understand exactly how phishing kits work, including MFA bypass techniques, fingerprinting, and dynamic page creation. - Proactive defense: Block threats faster, reduce incident response time, and protect your brand and customers.
- Business-focused visibility: Get clear, actionable insights without wasting time on noise.
Phishing kits move fast but with ANY.RUN, you can move even faster.
Get your 14-day ANY.RUN trial today and protect what matters most. The post Phishing Kit Attacks: How Businesses Can Stop Them Early appeared first on Cyber Security News.



































































































































































![[The AI Show Episode 145]: OpenAI Releases o3 and o4-mini, AI Is Causing “Quiet Layoffs,” Executive Order on Youth AI Education & GPT-4o’s Controversial Update](https://www.marketingaiinstitute.com/hubfs/ep%20145%20cover.png)











































































































































































































































































































































































![Google Home app fixes bug that repeatedly asked to ‘Set up Nest Cam features’ for Nest Hub Max [U]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2022/08/youtube-premium-music-nest-hub-max.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)






















































![Epic Games Wins Major Victory as Apple is Ordered to Comply With App Store Anti-Steering Injunction [Updated]](https://images.macrumors.com/t/Z4nU2dRocDnr4NPvf-sGNedmPGA=/2250x/article-new/2022/01/iOS-App-Store-General-Feature-JoeBlue.jpg)