TryHackMe: Zeek Exercises
1. Anomalous DNS An alert triggered: "Anomalous DNS Activity". The case was assigned to you. Inspect the PCAP and retrieve the artefacts to confirm this alert is a true positive. Flag 1 Investigate the dns-tunneling.pcap file. Investigate the dns.log file. What is the number of DNS records linked to the IPv6 address? After running zeek -Cr dns-tunneling.pcap, we run head -n 20 dns.log to investigate the file. We see AAAA is marked for some records. As we know, AAAA stands for IPv6. With this in mind, we run cat dns.log | grep AAAA | wc -l to get the number of DNS records linked to IPv6 addresses. Flag 2 Investigate the conn.log file. What is the longest connection duration? Upon reading the file conn.log, we got to see the parameter duration that represent the connection duration. We can try and zeek-cut it to get the output we want. With that in mind, we can do cat conn.log | zeek-cut duration | sort -n | tail -n 1 to get the flag. Flag 3 Investigate the dns.log file. Filter all unique DNS queries. What is the number of unique domain queries? We run cat dns.log | zeek-cut query | rev | cut -d '.' -f 1-2 | rev | sort | uniq | wc -l to get the flag. -rev is used to reverse the output cut -d '.' -f 1-2 is used to separate the string by ., then keep the first 2 parameters, hence -f 1-2 | sort | uniq | wc -l just to get the number of unique outputs Flag 4 There are a massive amount of DNS queries sent to the same domain. This is abnormal. Let's find out which hosts are involved in this activity. Investigate the conn.log file. What is the IP address of the source host? We list out the source IPs and figure out how many times have they been logged. We can do that by running cat conn.log | zeek-cut id.orig_h | grep | wc -l. The higher number is the flag. 2. Phishing An alert triggered: "Phishing Attempt". The case was assigned to you. Inspect the PCAP and retrieve the artefacts to confirm this alert is a true positive. Flag 1 Investigate the logs. What is the suspicious source address? Enter your answer in defanged format. We first run zeek -Cr phishing.pcap. Then we run cat conn.log | zeek-cut id.orig_h | sort | uniq. There is only 1 source IP, so we take that Ip to CyberChef to defang it thus getting the flag. Flag 2 Investigate the http.log file. Which domain address were the malicious files downloaded from? Enter your answer in defanged format. After reading http.log, we see that 3 files are downloaded, 1 .txt, 1 .doc, 1 .exe. We run cat http.log | zeek-cut host uri | column -t to get the file names and the source domain. .exe files from an unknown source tend to be bad news, so we can associate them with malicious files, which leads to the flag. We then defang it using CyberChef. Flag 3 Investigate the malicious document in VirusTotal. What kind of file is associated with the malicious document? As we try and retrieve the MD5 hash of the files, we see that they are not available. This indicates that we need to run some scripts. In this case, we can use the script file-extract-demo.zeek like so. As we cd into the extarct_files directory and ls, we see that the files were named using the pattern extract-156 We can check the names by reading files.log like so. We got to know that the .doc file is named extract-1561667889.703239-HTTP-FB5o2Hcauv7vpQ8y3. We then get the MD5 hash and search it on VirusTotal. Navigateb to Relations. Flag 4 Investigate the extracted malicious .exe file. What is the given file name in Virustotal? We got to know that the .exe file is named extract-1561667899.060086-HTTP-FOghls3WpIjKpvXaEl. We then get the MD5 hash and search it on VirusTotal. Flag 5 Investigate the malicious .exe file in VirusTotal. What is the contacted domain name? Enter your answer in defanged format. Navigate to Behaviour under VirusTotal and scroll down to the DNS section. Flag 6 Investigate the http.log file. What is the request name of the downloaded malicious .exe file? Run cat http.log | zeek-cut uri to get the flag. 3. Log4J An alert triggered: "Log4J Exploitation Attempt". The case was assigned to you. Inspect the PCAP and retrieve the artefacts to confirm this alert is a true positive. Flag 1 Investigate the log4shell.pcapng file with detection-log4j.zeek script. Investigate the signature.log file. What is the number of signature hits? Run zeek -Cr log4shell.pcapng detection-log4j.zeek. Run cat signatures.log | zeek-cut uid | wc -l and get the flag. Flag 2 Investigate the http.log file. Which tool is used for scanning? As we read some lines of http.log, we see nmap is mentioned. Nmap is a scanning tool, thus get us the flag. Flag 3 Investigate the http.log file. What is the extension of

1. Anomalous DNS
An alert triggered: "Anomalous DNS Activity".
The case was assigned to you. Inspect the PCAP and retrieve the artefacts to confirm this alert is a true positive.
Flag 1
Investigate the dns-tunneling.pcap file. Investigate the dns.log file. What is the number of DNS records linked to the IPv6 address?
After running zeek -Cr dns-tunneling.pcap, we run head -n 20 dns.log to investigate the file.
We see AAAA is marked for some records. As we know, AAAA stands for IPv6.
With this in mind, we run cat dns.log | grep AAAA | wc -l to get the number of DNS records linked to IPv6 addresses.
Flag 2
Investigate the conn.log file. What is the longest connection duration?
Upon reading the file conn.log, we got to see the parameter duration that represent the connection duration. We can try and zeek-cut it to get the output we want.
With that in mind, we can do cat conn.log | zeek-cut duration | sort -n | tail -n 1 to get the flag.
Flag 3
Investigate the dns.log file. Filter all unique DNS queries. What is the number of unique domain queries?
We run cat dns.log | zeek-cut query | rev | cut -d '.' -f 1-2 | rev | sort | uniq | wc -l to get the flag.
-rev is used to reverse the output
-
cut -d '.' -f 1-2is used to separate the string by., then keep the first 2 parameters, hence-f 1-2 -
| sort | uniq | wc -ljust to get the number of unique outputs
Flag 4
There are a massive amount of DNS queries sent to the same domain. This is abnormal. Let's find out which hosts are involved in this activity. Investigate the conn.log file. What is the IP address of the source host?
We list out the source IPs and figure out how many times have they been logged.
We can do that by running cat conn.log | zeek-cut id.orig_h | grep . The higher number is the flag.
2. Phishing
An alert triggered: "Phishing Attempt".
The case was assigned to you. Inspect the PCAP and retrieve the artefacts to confirm this alert is a true positive.
Flag 1
Investigate the logs. What is the suspicious source address? Enter your answer in defanged format.
We first run zeek -Cr phishing.pcap. Then we run cat conn.log | zeek-cut id.orig_h | sort | uniq.
There is only 1 source IP, so we take that Ip to CyberChef to defang it thus getting the flag.
Flag 2
Investigate the http.log file. Which domain address were the malicious files downloaded from? Enter your answer in defanged format.
After reading http.log, we see that 3 files are downloaded, 1 .txt, 1 .doc, 1 .exe.
We run cat http.log | zeek-cut host uri | column -t to get the file names and the source domain. .exe files from an unknown source tend to be bad news, so we can associate them with malicious files, which leads to the flag. We then defang it using CyberChef.
Flag 3
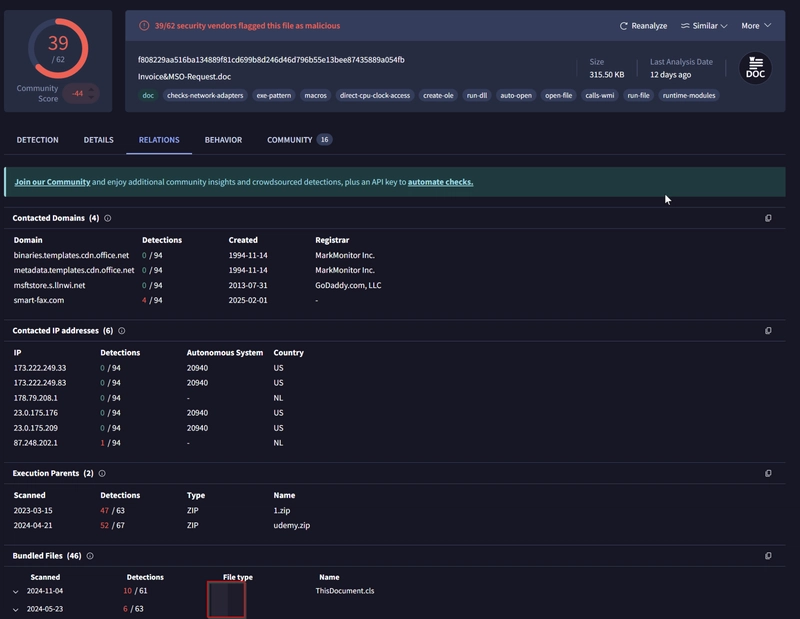
Investigate the malicious document in VirusTotal. What kind of file is associated with the malicious document?
As we try and retrieve the MD5 hash of the files, we see that they are not available. This indicates that we need to run some scripts.
In this case, we can use the script file-extract-demo.zeek like so.
As we cd into the extarct_files directory and ls, we see that the files were named using the pattern extract-156
We can check the names by reading files.log like so.
We got to know that the .doc file is named extract-1561667889.703239-HTTP-FB5o2Hcauv7vpQ8y3.
We then get the MD5 hash and search it on VirusTotal.
Navigateb to Relations.
Flag 4
Investigate the extracted malicious .exe file. What is the given file name in Virustotal?
We got to know that the .exe file is named extract-1561667899.060086-HTTP-FOghls3WpIjKpvXaEl.
We then get the MD5 hash and search it on VirusTotal.
Flag 5
Investigate the malicious .exe file in VirusTotal. What is the contacted domain name? Enter your answer in defanged format.
Navigate to Behaviour under VirusTotal and scroll down to the DNS section.
Flag 6
Investigate the http.log file. What is the request name of the downloaded malicious .exe file?
Run cat http.log | zeek-cut uri to get the flag.
3. Log4J
An alert triggered: "Log4J Exploitation Attempt".
The case was assigned to you. Inspect the PCAP and retrieve the artefacts to confirm this alert is a true positive.
Flag 1
Investigate the log4shell.pcapng file with detection-log4j.zeek script. Investigate the signature.log file. What is the number of signature hits?
Run zeek -Cr log4shell.pcapng detection-log4j.zeek.
Run cat signatures.log | zeek-cut uid | wc -l and get the flag.
Flag 2
Investigate the http.log file. Which tool is used for scanning?
As we read some lines of http.log, we see nmap is mentioned. Nmap is a scanning tool, thus get us the flag.
Flag 3
Investigate the http.log file. What is the extension of the exploit file?
We can run cat http.log | zeek-cut uri | sort | uniq to get all unique entries of the files downloaded. From here we can see the only file that has an extension, and that is the flag.
Flag 4
Investigate the log4j.log file. Decode the base64 commands. What is the name of the created file?
As we read the file log4j.log, we see some encoded strings.
We can bring those to CyberChef to be base64 decoded.




































































































































































![[The AI Show Episode 145]: OpenAI Releases o3 and o4-mini, AI Is Causing “Quiet Layoffs,” Executive Order on Youth AI Education & GPT-4o’s Controversial Update](https://www.marketingaiinstitute.com/hubfs/ep%20145%20cover.png)



























































































































![[DEALS] Microsoft 365: 1-Year Subscription (Family/Up to 6 Users) (23% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)




![From Art School Drop-out to Microsoft Engineer with Shashi Lo [Podcast #170]](https://cdn.hashnode.com/res/hashnode/image/upload/v1746203291209/439bf16b-c820-4fe8-b69e-94d80533b2df.png?#)








































































































(1).jpg?#)































_Inge_Johnsson-Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)

















































































































![New Apple iPad mini 7 On Sale for $399! [Lowest Price Ever]](https://www.iclarified.com/images/news/96096/96096/96096-640.jpg)
![Apple to Split iPhone Launches Across Fall and Spring in Major Shakeup [Report]](https://www.iclarified.com/images/news/97211/97211/97211-640.jpg)
![Apple to Move Camera to Top Left, Hide Face ID Under Display in iPhone 18 Pro Redesign [Report]](https://www.iclarified.com/images/news/97212/97212/97212-640.jpg)
![Apple Developing Battery Case for iPhone 17 Air Amid Battery Life Concerns [Report]](https://www.iclarified.com/images/news/97208/97208/97208-640.jpg)