TryHackMe: Snort Challenge - Live Attacks
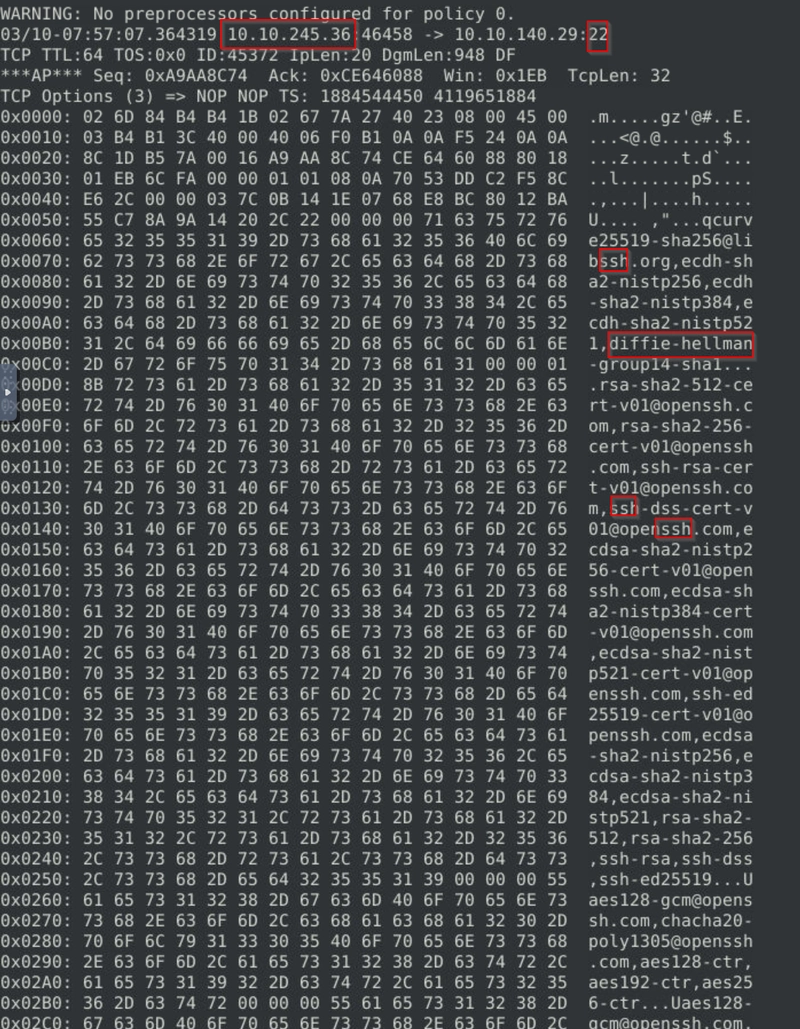
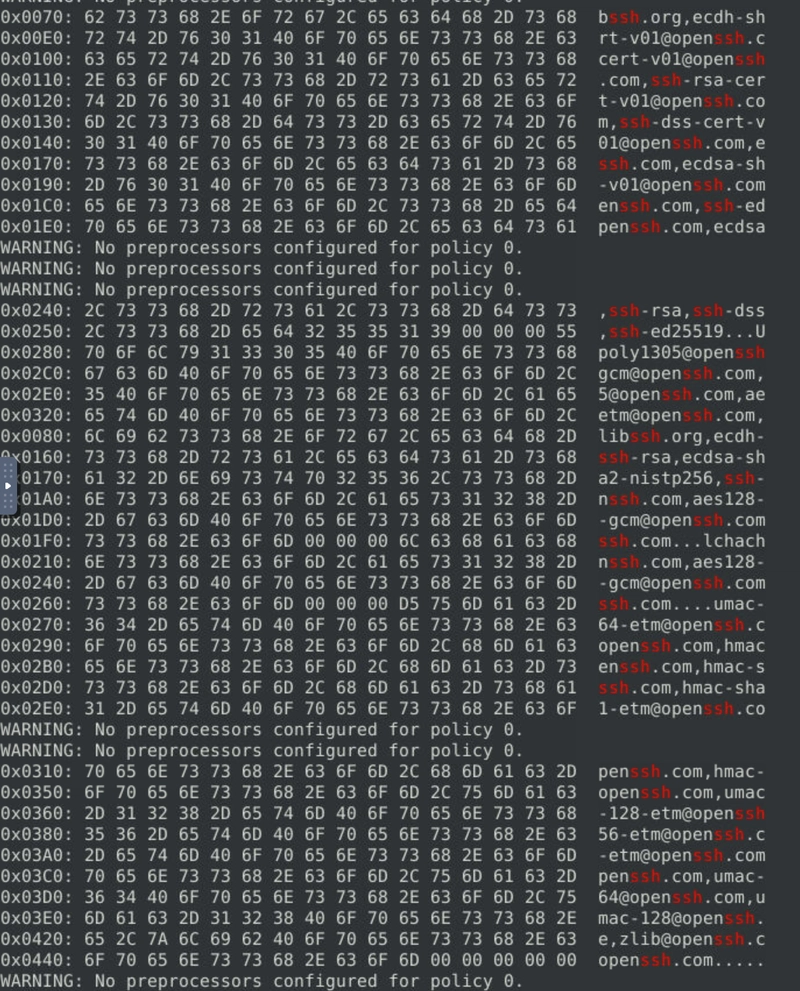
Scenario 1: Brute Force First of all, start Snort in sniffer mode and try to figure out the attack source, service and port. Then, write an IPS rule and run Snort in IPS mode to stop the brute-force attack. Once you stop the attack properly, you will have the flag on the desktop! Here are a few points to remember: Create the rule and test it with "-A console" mode. Use "-A full" mode and the default log path to stop the attack. Write the correct rule and run the Snort in IPS "-A full" mode. Block the traffic at least for a minute and then the flag file will appear on your desktop. Flag 1 Stop the attack and get the flag (which will appear on your Desktop) We first capture the traffic using sudo snort -dev -l .. We then check out the log file generated using sudo snort -r . As we examind the log file, we see an overwhelming amount of port 22 connections from the IP 10.10.245.36, which is a red flag as port 22 is commonly associated with SSH service. We can confirm this by checking on a few packets' header using the command sudo snort -r snort.log.1741593427 -X -n 30. And sure enough we do see an SSH connection attempt. As we run sudo snort -r snort.log.1741593427 -X | grep ssh and sudo snort -r snort.log.1741593427 -X | grep 10.10.245.36, we see that SSH connection attempts are being made by the same IP in between just a few packets, confirming that SSH bruteforce is indeed occuring. With this in mind, we create 2 rules, 1 to alert and 1 to drop the suspicious packet. alert tcp 10.10.245.36 any -> any 22 (msg: "SSH Login Attempt Detected"; sid: 1000001; rev: 1;) drop tcp 10.10.245.36 any -> any 22 (msg: "SSH Login Attempt Dropped"; sid: 1000002; rev: 1;) Run snort using sudo snort -c /etc/snort/rules/local.rules -A full. Let it run for a minute until we see flag.txt on our Desktop. Flag 2 The service under attack is SSH. Flag 3 The protocol is TCP and port is 22, TCP/22. Scenario 2: Reverse Shell First of all, start Snort in sniffer mode and try to figure out the attack source, service and port. Then, write an IPS rule and run Snort in IPS mode to stop the brute-force attack. Once you stop the attack properly, you will have the flag on the desktop! Here are a few points to remember: Create the rule and test it with "-A console" mode. Use "-A full" mode and the default log path to stop the attack. Write the correct rule and run the Snort in IPS "-A full" mode. Block the traffic at least for a minute and then the flag file will appear on your desktop. Flag 1 Stop the attack and get the flag (which will appear on your Desktop) Run sudo snort -c /etc/snort/snort.conf -T to ensure Snort is properly configured. Capture packets using sudo snort -dev -l .. Examine log file using sudo snort -r Right off the bat we see connections from port 4444, which is a huge red flag as it is the default port for Metasploit. We can run sudo snort -r -X -n 30 to axmine the packet content within the fist 30 packets. A few things to note at the content of this packet. Contains Base64-encoded data, which is often used to encode malicious commands. The command uses multiple decoders (base64 -d, openssl enc -d, python, perl) to ensure execution. The payload is writing a script (/tmp/NLSQY.b64 → /tmp/anCTe), marking it as executable (chmod +x), and executing it. The script is then removed (rm -f), which is a common tactic to cover tracks. We can deduce that the attacker from 10.10.144.156 is sending a payload to 10.10.196.55 over port 4444, likely to gain remote access. Once we confirmed that it is indeed malicious traffic, we create 2 rules, 1 to alert us and 1 to drop them entirely. alert tcp 10.10.144.156 any -> any any (msg: "Attempted RCE Detected"; sid: 1000001; rev: 1;) drop tcp 10.10.144.156 any -> any any (msg: "Attempted RCE Traffic Dropped"; sid: 1000002; rev: 1;) Note: We don't block port 4444 specifically as attacker can easily change its port to something else and perform the same attack, therefore we put any to further reduce attack surface. We the run snort using sudo snort -c /etc/snort/rules/local.rules -A full. Run it for some time and we will see flag.txt on our Desktop.
Scenario 1: Brute Force
First of all, start Snort in sniffer mode and try to figure out the attack source, service and port.
Then, write an IPS rule and run Snort in IPS mode to stop the brute-force attack. Once you stop the attack properly, you will have the flag on the desktop!
Here are a few points to remember:
- Create the rule and test it with "-A console" mode.
- Use "-A full" mode and the default log path to stop the attack.
- Write the correct rule and run the Snort in IPS "-A full" mode.
- Block the traffic at least for a minute and then the flag file will appear on your desktop.
Flag 1
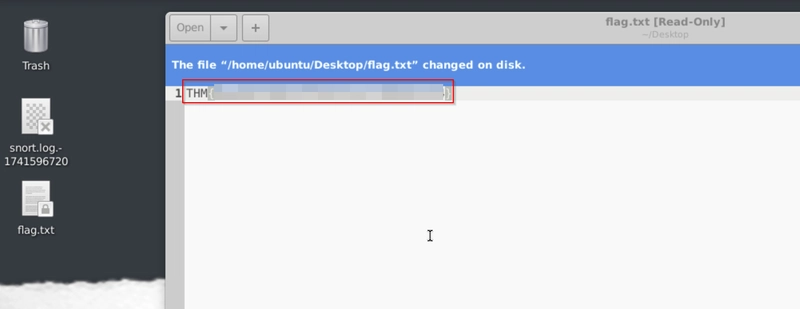
Stop the attack and get the flag (which will appear on your Desktop)
We first capture the traffic using sudo snort -dev -l ..
We then check out the log file generated using sudo snort -r .
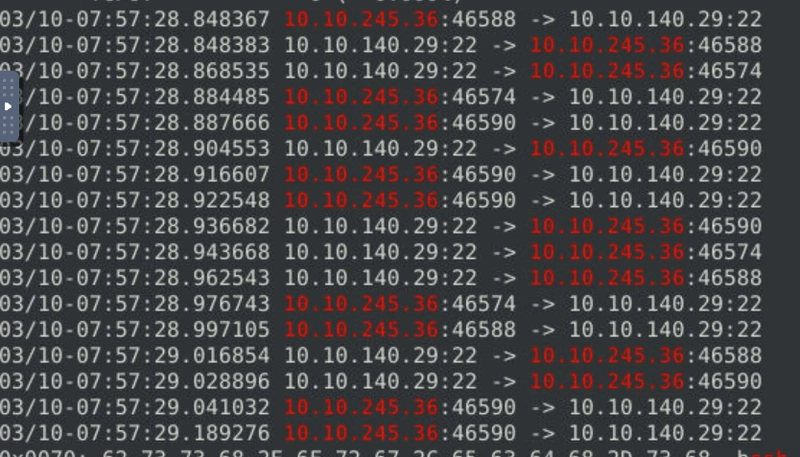
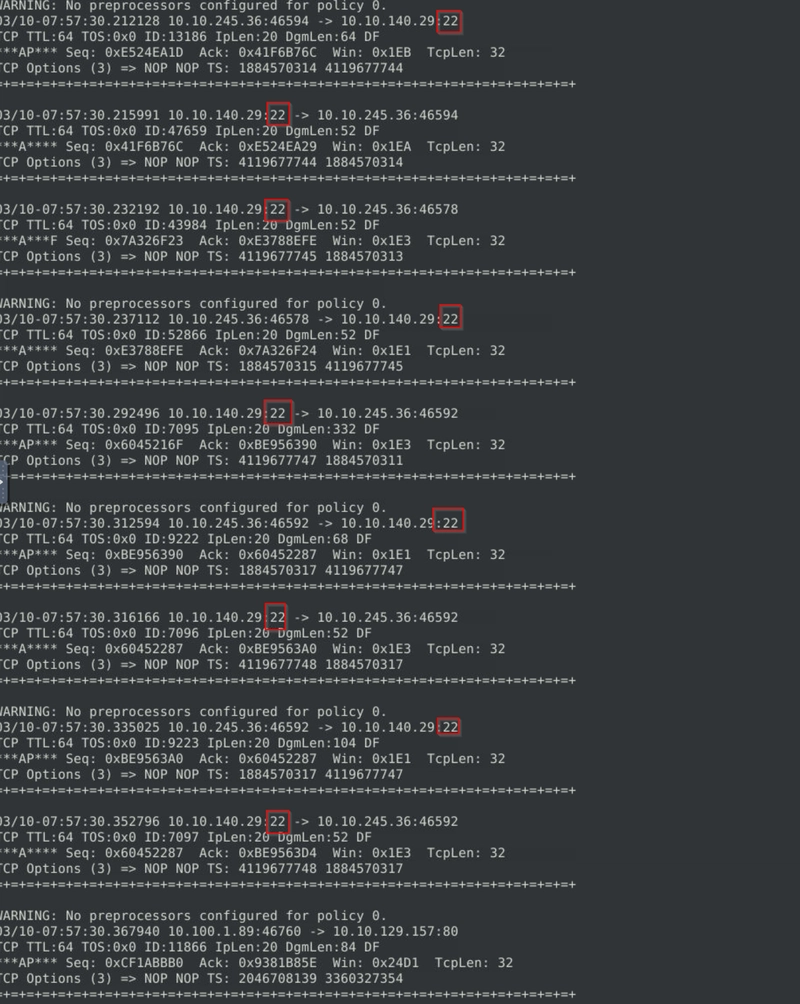
As we examind the log file, we see an overwhelming amount of port 22 connections from the IP 10.10.245.36, which is a red flag as port 22 is commonly associated with SSH service.
We can confirm this by checking on a few packets' header using the command sudo snort -r snort.log.1741593427 -X -n 30.
And sure enough we do see an SSH connection attempt.
As we run sudo snort -r snort.log.1741593427 -X | grep ssh and sudo snort -r snort.log.1741593427 -X | grep 10.10.245.36, we see that SSH connection attempts are being made by the same IP in between just a few packets, confirming that SSH bruteforce is indeed occuring.
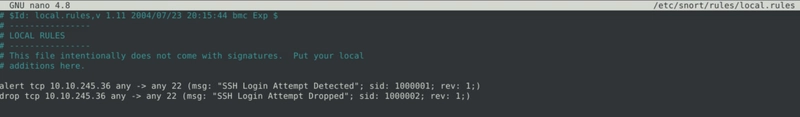
With this in mind, we create 2 rules, 1 to alert and 1 to drop the suspicious packet.
alert tcp 10.10.245.36 any -> any 22 (msg: "SSH Login Attempt Detected"; sid: 1000001; rev: 1;)
drop tcp 10.10.245.36 any -> any 22 (msg: "SSH Login Attempt Dropped"; sid: 1000002; rev: 1;)
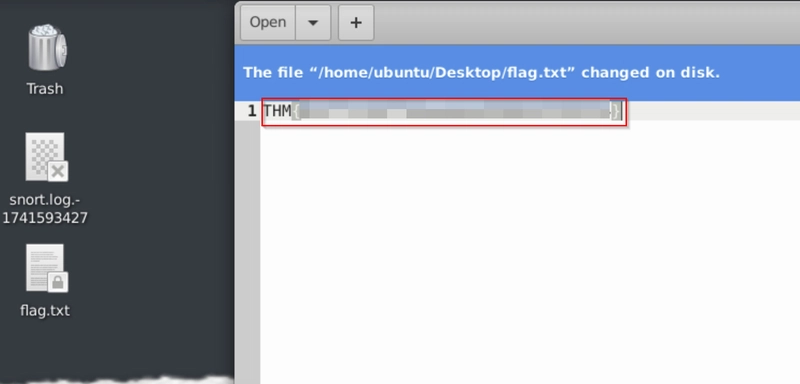
Run snort using sudo snort -c /etc/snort/rules/local.rules -A full.
Let it run for a minute until we see flag.txt on our Desktop.
Flag 2
The service under attack is SSH.
Flag 3
The protocol is TCP and port is 22, TCP/22.
Scenario 2: Reverse Shell
First of all, start Snort in sniffer mode and try to figure out the attack source, service and port.
Then, write an IPS rule and run Snort in IPS mode to stop the brute-force attack. Once you stop the attack properly, you will have the flag on the desktop!
Here are a few points to remember:
- Create the rule and test it with "-A console" mode.
- Use "-A full" mode and the default log path to stop the attack.
- Write the correct rule and run the Snort in IPS "-A full" mode.
- Block the traffic at least for a minute and then the flag file will appear on your desktop.
Flag 1
Stop the attack and get the flag (which will appear on your Desktop)
Run sudo snort -c /etc/snort/snort.conf -T to ensure Snort is properly configured.
Capture packets using sudo snort -dev -l ..
Examine log file using sudo snort -r
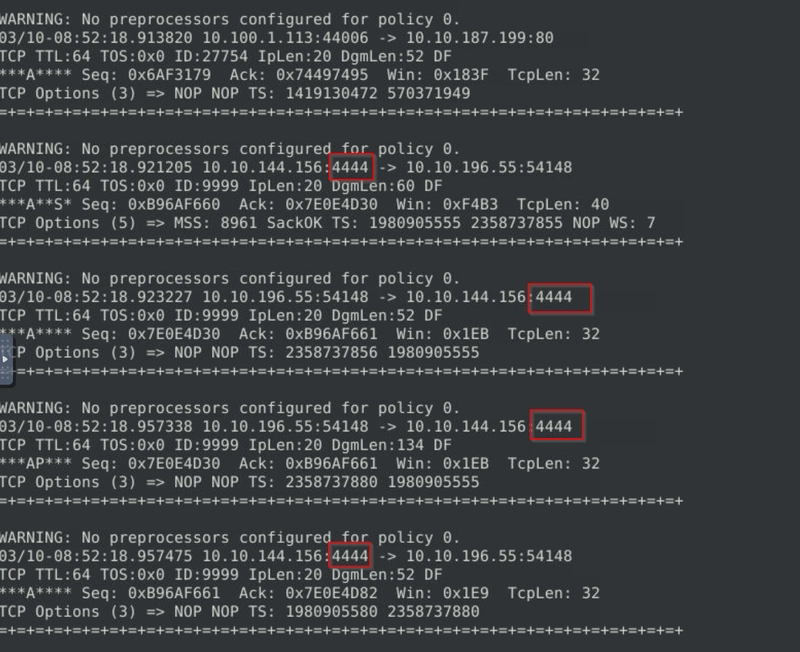
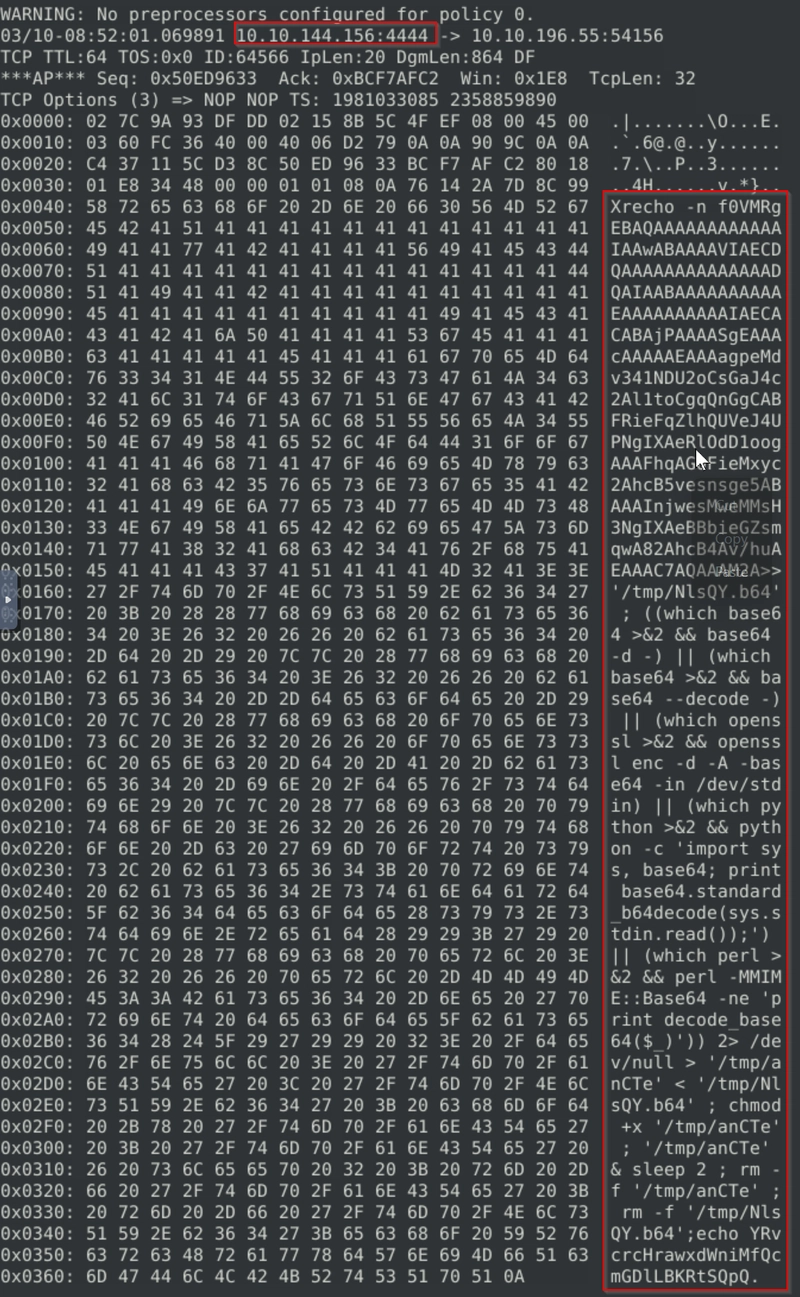
Right off the bat we see connections from port 4444, which is a huge red flag as it is the default port for Metasploit.
We can run sudo snort -r to axmine the packet content within the fist 30 packets.
A few things to note at the content of this packet.
- Contains Base64-encoded data, which is often used to encode malicious commands.
- The command uses multiple decoders (
base64 -d,openssl enc -d,python,perl) to ensure execution. - The payload is writing a script (
/tmp/NLSQY.b64→/tmp/anCTe), marking it as executable (chmod +x), and executing it. - The script is then removed (
rm -f), which is a common tactic to cover tracks.
We can deduce that the attacker from 10.10.144.156 is sending a payload to 10.10.196.55 over port 4444, likely to gain remote access.
Once we confirmed that it is indeed malicious traffic, we create 2 rules, 1 to alert us and 1 to drop them entirely.
alert tcp 10.10.144.156 any -> any any (msg: "Attempted RCE Detected"; sid: 1000001; rev: 1;)
drop tcp 10.10.144.156 any -> any any (msg: "Attempted RCE Traffic Dropped"; sid: 1000002; rev: 1;)
Note: We don't block port 4444 specifically as attacker can easily change its port to something else and perform the same attack, therefore we put any to further reduce attack surface.
We the run snort using sudo snort -c /etc/snort/rules/local.rules -A full.
Run it for some time and we will see flag.txt on our Desktop.

































































































































































![[The AI Show Episode 143]: ChatGPT Revenue Surge, New AGI Timelines, Amazon’s AI Agent, Claude for Education, Model Context Protocol & LLMs Pass the Turing Test](https://www.marketingaiinstitute.com/hubfs/ep%20143%20cover.png)








































































































































































































































































_Muhammad_R._Fakhrurrozi_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)
_NicoElNino_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)




















































































![macOS 15.5 beta 4 now available for download [U]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/04/macOS-Sequoia-15.5-b4.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)















![AirPods Pro 2 With USB-C Back On Sale for Just $169! [Deal]](https://www.iclarified.com/images/news/96315/96315/96315-640.jpg)
![Apple Releases iOS 18.5 Beta 4 and iPadOS 18.5 Beta 4 [Download]](https://www.iclarified.com/images/news/97145/97145/97145-640.jpg)
![Apple Seeds watchOS 11.5 Beta 4 to Developers [Download]](https://www.iclarified.com/images/news/97147/97147/97147-640.jpg)
![Apple Seeds visionOS 2.5 Beta 4 to Developers [Download]](https://www.iclarified.com/images/news/97150/97150/97150-640.jpg)




































![Apple Seeds Fourth Beta of iOS 18.5 to Developers [Update: Public Beta Available]](https://images.macrumors.com/t/uSxxRefnKz3z3MK1y_CnFxSg8Ak=/2500x/article-new/2025/04/iOS-18.5-Feature-Real-Mock.jpg)
![Apple Seeds Fourth Beta of macOS Sequoia 15.5 [Update: Public Beta Available]](https://images.macrumors.com/t/ne62qbjm_V5f4GG9UND3WyOAxE8=/2500x/article-new/2024/08/macOS-Sequoia-Night-Feature.jpg)