The Cloud Security Blind Spots: What Most Cloud Engineers Don’t Know About Linux Security
In today's cloud first world, we're so caught up in configuring IAM policies, setting up security groups, and monitoring CloudTrail logs that we sometimes forget a fundamental tool: Underneath all those abstraction layers sits good old Linux. And there's a critical set of Linux security features that even experienced cloud engineers often overlook. Special Permissions!. These powerful but frequently misunderstood tools can either strengthen your cloud security posture or create dangerous vulnerabilities, if misconfigured. Let's get into the security blind spots that could be putting your cloud infrastructure at risk! Table of Contents The Forgotten Foundation: Linux Under Your Cloud SUID (Set User ID): The Double-Edged Sword SGID (Set Group ID): When Inheritance Goes Wrong Sticky Bit: The Hero of Multi-Tenant Environments Special Permissions By The Numbers Summary: Closing the Linux Security Gap in Your Cloud 1. The Forgotten Foundation: Linux Under Your Cloud While we're busy orchestrating containers, configuring auto-scaling groups, and deploying serverless functions, it's easy to forget that most cloud infrastructure ultimately runs on Linux. AWS EC2 instances, Azure VMs, Google Compute Engine, and even the hosts running your container clusters, they're all powered by Linux variants. Over 65% of cloud security incidents involve Linux misconfigurations that cloud engineers simply didn't account for in their security planning. One particularly overlooked area? Special permissions, a set of powerful Linux capabilities that can either harden your infrastructure or blow security holes right through it. 2. SUID (Set User ID): The Double-Edged Sword SUID allows users to execute programs with the permissions of the file owner (often root) instead of their own permissions. When an executable file has SUID permission, users temporarily gain the owner's privileges when running that specific program. How to Set it? # To set SUID chmod u+s /filename # Numerical method chmod 4755 /filename # To remove SUID chmod u-s /filename # or chmod -4000 /filename If you see s it shows x is still active, while S means x is absent. Real-World Cloud Use Case & Risk Legitimate Use: Your cloud automation scripts might need elevated privileges for specific operations. A common pattern is creating a custom utility that performs a privileged operation (like managing network configurations) that your application needs occasionally. The Blind Spot: Many cloud engineers don't realize that misplaced SUID binaries are one of the most common privilege escalation vectors in cloud environments. A 2023 cloud security study found that over 40% of compromised instances had unauthorized SUID executables, often placed there by attackers who gained initial access through other means. Mitigation Strategy: Conduct regular audits of SUID binaries on your cloud instances. 3. SGID (Set Group ID): When Inheritance Goes Wrong When applied to directories, SGID makes all new files inherit the group ownership of the parent directory rather than the creating user's primary group. How to Set It? # To set SGID on a directory chmod g+s /directory_name # Numerical method chmod 2755 /directory_name # To remove SGID chmod g-s /directory_name # or chmod -2000 /directory_name Real-World Cloud Use Case & Risk Legitimate Use: In multi-service cloud architectures, you might have various microservices writing to shared data directories. SGID ensures consistent group permissions regardless of which service creates the file. The Blind Spot: Cloud engineers often set up SGID directories without understanding the security implications. If the group permissions are too permissive and the group includes untrusted users or compromised services, you've effectively created a path for lateral movement within your infrastructure. Example Scenario: Your data processing pipeline uses SGID on a directory where multiple services dump logs for analysis. If one microservice is compromised and the SGID directory grants group write access, the attacker can now potentially modify files used by other services in your cloud environment. Mitigation Strategy: Use the principle of least privilege when setting group permissions on SGID directories. Regularly audit group memberships and consider isolating critical services with dedicated security groups in your cloud architecture. 4. Sticky Bit: The Hero of Multi-Tenant Environments The sticky bit prevents users from deleting or renaming files in a directory unless they own the file or the directory, regardless of write permissions. How to Set It? # To set sticky bit chmod o+t /directory_name # Numerical method chmod 1755 /directory_name # To remove sticky bit chmod o-t /directory_name # or chmod -1000 /di
In today's cloud first world, we're so caught up in configuring IAM policies, setting up security groups, and monitoring CloudTrail logs that we sometimes forget a fundamental tool: Underneath all those abstraction layers sits good old Linux. And there's a critical set of Linux security features that even experienced cloud engineers often overlook. Special Permissions!.
These powerful but frequently misunderstood tools can either strengthen your cloud security posture or create dangerous vulnerabilities, if misconfigured. Let's get into the security blind spots that could be putting your cloud infrastructure at risk!
Table of Contents
- The Forgotten Foundation: Linux Under Your Cloud
- SUID (Set User ID): The Double-Edged Sword
- SGID (Set Group ID): When Inheritance Goes Wrong
- Sticky Bit: The Hero of Multi-Tenant Environments
- Special Permissions By The Numbers
- Summary: Closing the Linux Security Gap in Your Cloud
1. The Forgotten Foundation: Linux Under Your Cloud
While we're busy orchestrating containers, configuring auto-scaling groups, and deploying serverless functions, it's easy to forget that most cloud infrastructure ultimately runs on Linux. AWS EC2 instances, Azure VMs, Google Compute Engine, and even the hosts running your container clusters, they're all powered by Linux variants.
Over 65% of cloud security incidents involve Linux misconfigurations that cloud engineers simply didn't account for in their security planning. One particularly overlooked area? Special permissions, a set of powerful Linux capabilities that can either harden your infrastructure or blow security holes right through it.
2. SUID (Set User ID): The Double-Edged Sword
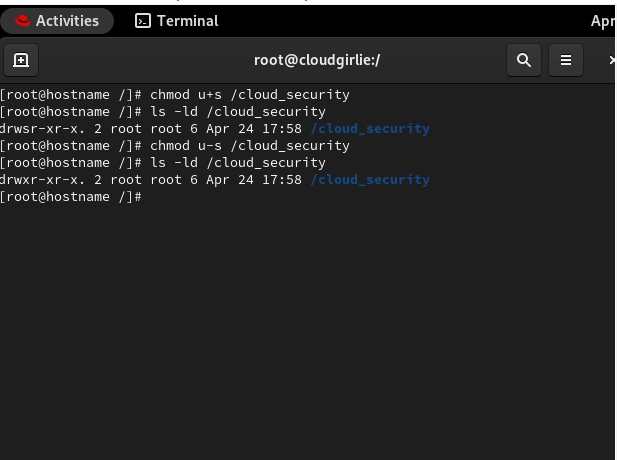
SUID allows users to execute programs with the permissions of the file owner (often root) instead of their own permissions. When an executable file has SUID permission, users temporarily gain the owner's privileges when running that specific program.
How to Set it?
# To set SUID
chmod u+s /filename
# Numerical method
chmod 4755 /filename
# To remove SUID
chmod u-s /filename
# or
chmod -4000 /filename
If you see s it shows x is still active, while S means x is absent.
Real-World Cloud Use Case & Risk
- Legitimate Use: Your cloud automation scripts might need elevated privileges for specific operations. A common pattern is creating a custom utility that performs a privileged operation (like managing network configurations) that your application needs occasionally.
- The Blind Spot: Many cloud engineers don't realize that misplaced SUID binaries are one of the most common privilege escalation vectors in cloud environments. A 2023 cloud security study found that over 40% of compromised instances had unauthorized SUID executables, often placed there by attackers who gained initial access through other means.
- Mitigation Strategy: Conduct regular audits of SUID binaries on your cloud instances.
3. SGID (Set Group ID): When Inheritance Goes Wrong
When applied to directories, SGID makes all new files inherit the group ownership of the parent directory rather than the creating user's primary group.
How to Set It?
# To set SGID on a directory
chmod g+s /directory_name
# Numerical method
chmod 2755 /directory_name
# To remove SGID
chmod g-s /directory_name
# or
chmod -2000 /directory_name
Real-World Cloud Use Case & Risk
- Legitimate Use: In multi-service cloud architectures, you might have various microservices writing to shared data directories. SGID ensures consistent group permissions regardless of which service creates the file.
- The Blind Spot: Cloud engineers often set up SGID directories without understanding the security implications. If the group permissions are too permissive and the group includes untrusted users or compromised services, you've effectively created a path for lateral movement within your infrastructure.
- Example Scenario: Your data processing pipeline uses SGID on a directory where multiple services dump logs for analysis. If one microservice is compromised and the SGID directory grants group write access, the attacker can now potentially modify files used by other services in your cloud environment.
- Mitigation Strategy: Use the principle of least privilege when setting group permissions on SGID directories. Regularly audit group memberships and consider isolating critical services with dedicated security groups in your cloud architecture.
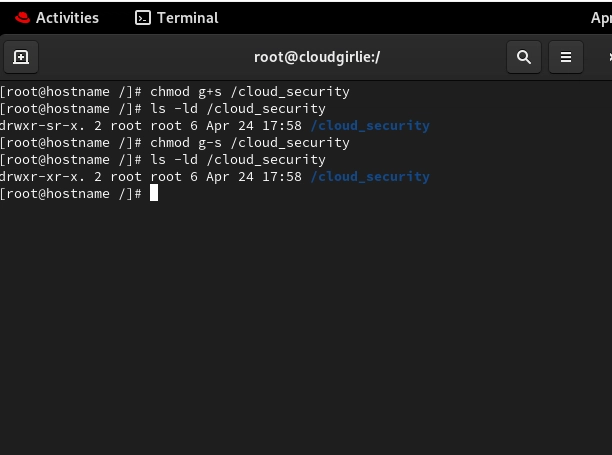
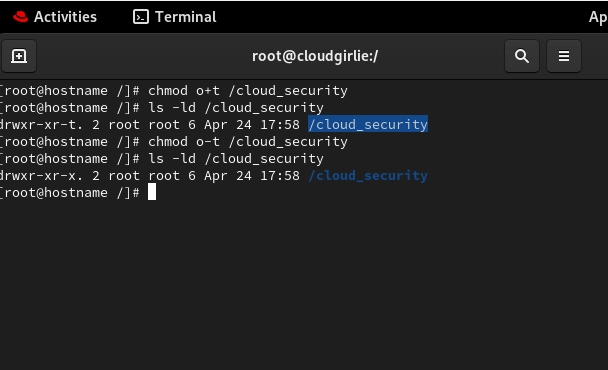
4. Sticky Bit: The Hero of Multi-Tenant Environments
The sticky bit prevents users from deleting or renaming files in a directory unless they own the file or the directory, regardless of write permissions.
How to Set It?
# To set sticky bit
chmod o+t /directory_name
# Numerical method
chmod 1755 /directory_name
# To remove sticky bit
chmod o-t /directory_name
# or
chmod -1000 /directory_name
Real-World Cloud Use Case & Risk
- Legitimate Use: In multi-tenant cloud environments or shared processing directories, the sticky bit ensures that services can't delete each other's files, maintaining data integrity across your ecosystem.
- The Blind Spot: Many cloud engineers don't implement sticky bits for shared directories, creating race conditions and potential denial-of-service vectors where one compromised service can delete files needed by other components.
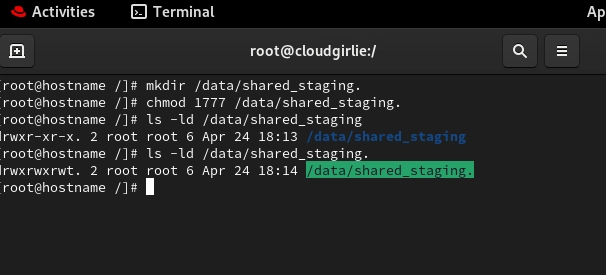
- Example Implementation: For cloud environments running multiple data processing workflows that need to share a staging directory:
Now each process can write to the directory, but can only delete its own files, perfect for multi-tenant cloud architectures.
5. Special Permissions By The Numbers
For those who prefer the numerical approach to permissions, here's how special permissions work with the octal notation by adding a fourth digit at the beginning:
SUID: 4
SGID: 2
Sticky Bit: 1
# Set all special permissions (SUID+SGID+Sticky Bit)
chmod 7755 /file_name # 4+2+1=7
# Set SUID and SGID
chmod 6755 /file_name # 4+2=6
# Set SGID and sticky bit
chmod 3755 /directory_name # 2+1=3
6. Summary: Closing the Linux Security Gap in Your Cloud
As cloud infrastructure grows more complex, we can't afford to overlook the fundamentals. Linux special permissions represent both powerful tools and potential security risks in cloud environments:
- SUID needs careful auditing to prevent privilege escalation vectors.
- SGID requires thoughtful group management to prevent lateral movement.
- Sticky Bit should be standard practice for shared directories in multi-tenant environments.
Even with all the sophisticated cloud security tooling available today, a single misconfigured special permission can create a vulnerability that bypasses your carefully constructed security controls.
The most secure cloud engineers recognize that cloud security isn't just about mastering the latest cloud-native security features, it's about understanding the operating system fundamentals that underpin everything. By closing the Linux special permissions blind spot, you're addressing a critical but often overlooked aspect of your cloud security posture.
What Linux security practices have you incorporated into your cloud security program? Share your experiences in the comments!
Did you find this article helpful? There's more where this came from, connect with me on LinkedIn
#30DaysLinuxChallenge #CloudWhistler #RedHat #Cloudsecurity #DevOps #Linux #OpenSource #CloudComputing #Womenwhobuild #RedHatEnterpriseLinux #LinuxSecurity #EnterpriseIT #Ansible #OpenShift #SysAdmin #Automation #CloudEngineer









































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)































































































































![[DEALS] Sterling Stock Picker: Lifetime Subscription (85% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)











































































































.jpg?#)







































































































































![Apple to Shift Robotics Unit From AI Division to Hardware Engineering [Report]](https://www.iclarified.com/images/news/97128/97128/97128-640.jpg)

![Apple Shares New Ad for iPhone 16: 'Trust Issues' [Video]](https://www.iclarified.com/images/news/97125/97125/97125-640.jpg)