Service Mesh Explained: Building a Proxy Injector in Rust (with code)
Kubernetes service meshes rely on “sidecar” proxies to handle traffic routing transparently, security policies, and observability for your microservices—but manually bolting those proxies onto every Pod spec quickly becomes a maintenance nightmare. What if you could have Kubernetes do the work for you, automatically injecting the proxy whenever a Pod is created? In this tutorial, we’re going to build exactly that: a Mutating Admission Webhook in Rust that hooks into the Kubernetes API server, inspects incoming Pod specs, and—if they meet your criteria—patches them on the fly to include an init‑container (for iptables setup) and your proxy‑sidecar. Along the way, you’ll learn how to: Define the AdmissionReview/AdmissionRequest and AdmissionResponse data structures Wire up an async handler in Axum, complete with #[instrument] tracing for per-request logging Craft a JSONPatch that adds init‑containers and sidecar containers via a base64-encoded payload Stand up a TLS‑secured HTTP server using Rustls so Kubernetes can trust your webhook By the end, you’ll have a drop‑in proxy injector that can be deployed alongside your service mesh control plane—no more manual injection, no more drift, just automatic, consistent proxy injection across your cluster. All the code we walk through here is available on our GitHub repository—feel free to clone and explore it! Let’s dive in!
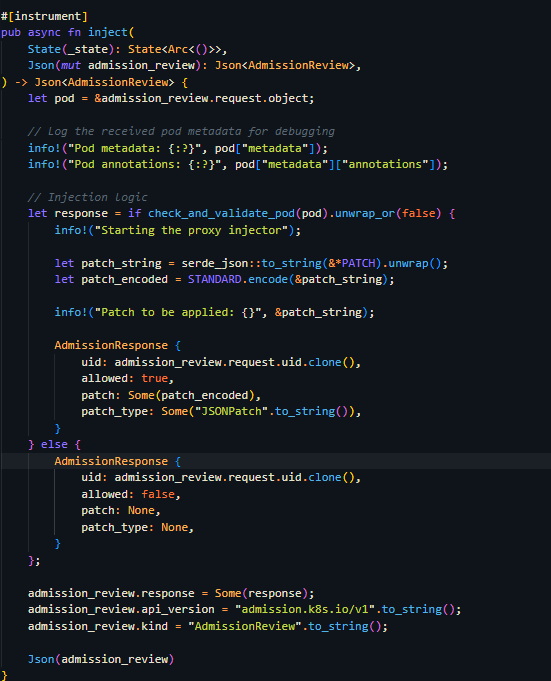
Kubernetes service meshes rely on “sidecar” proxies to handle traffic routing transparently, security
policies, and observability for your microservices—but manually bolting those proxies onto every Pod
spec quickly becomes a maintenance nightmare.
What if you could have Kubernetes do the work for you, automatically injecting the proxy whenever a Pod is created?
In this tutorial, we’re going to build exactly that: a Mutating Admission Webhook in Rust that hooks
into the Kubernetes API server, inspects incoming Pod specs, and—if they meet your criteria—patches
them on the fly to include an init‑container (for iptables setup) and your proxy‑sidecar.
Along the way, you’ll learn how to:
- Define the AdmissionReview/AdmissionRequest and AdmissionResponse data structures
- Wire up an async handler in Axum, complete with #[instrument] tracing for per-request logging
- Craft a JSONPatch that adds init‑containers and sidecar containers via a base64-encoded payload
- Stand up a TLS‑secured HTTP server using Rustls so Kubernetes can trust your webhook
By the end, you’ll have a drop‑in proxy injector that can be deployed alongside your service mesh
control plane—no more manual injection, no more drift, just automatic, consistent proxy injection
across your cluster.
All the code we walk through here is available on our GitHub repository—feel free to clone and explore it!
Let’s dive in!







































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)






















































































































































![Is This Programming Paradigm New? [closed]](https://miro.medium.com/v2/resize:fit:1200/format:webp/1*nKR2930riHA4VC7dLwIuxA.gif)
























































































-Classic-Nintendo-GameCube-games-are-coming-to-Nintendo-Switch-2!-00-00-13.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)







































































































































![M4 MacBook Air Drops to New All-Time Low of $912 [Deal]](https://www.iclarified.com/images/news/97108/97108/97108-640.jpg)
![New iPhone 17 Dummy Models Surface in Black and White [Images]](https://www.iclarified.com/images/news/97106/97106/97106-640.jpg)