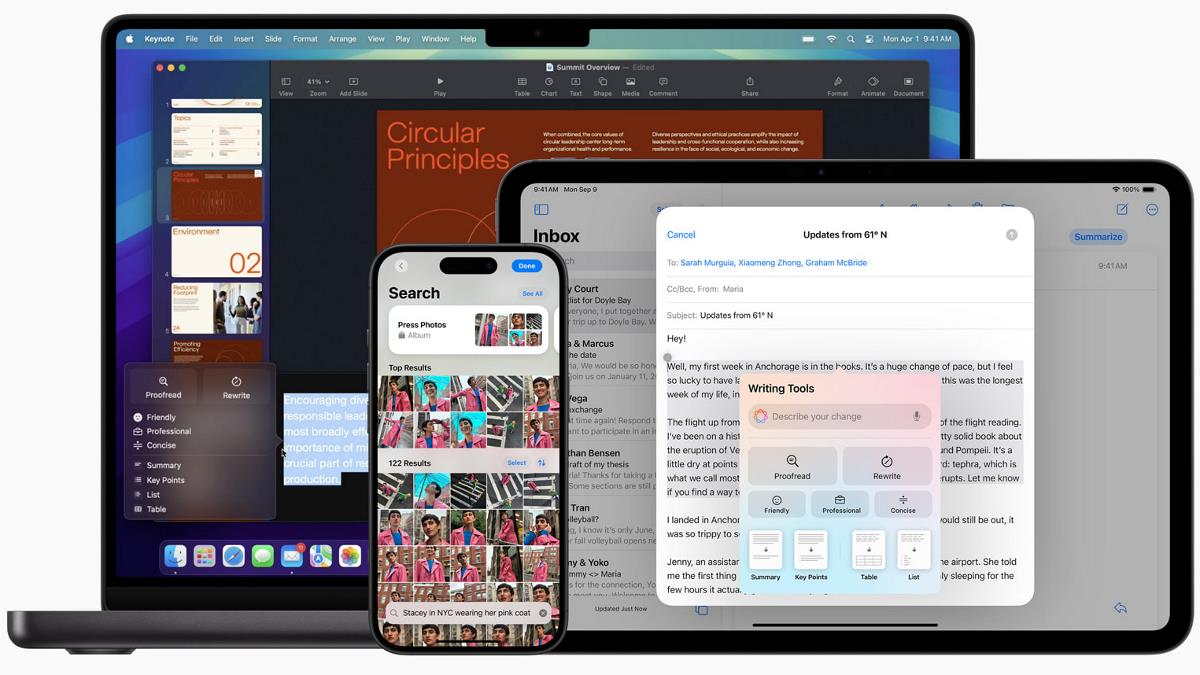
As robotics becomes more accessible and developers take the leap into building their own intelligent machines, the importance of security cannot be overstated. Whether you're tinkering with your first robot at home or developing a prototype for industrial use, it's critical to think beyond just getting ROS2 installed and your nodes communicating. Welcome to the first post in a new series focused on securing your ROS2 environment — starting from the ground up, at the Linux OS level. This guide is crafted to walk you through practical and effective steps to immediately improve the security posture of your robot projects. Our goal is to empower builders and developers to safeguard their work from common attack vectors without getting lost in complexity.
As robotics becomes more accessible and developers take the leap into building their own intelligent machines, the importance of security cannot be overstated. Whether you're tinkering with your first robot at home or developing a prototype for industrial use, it's critical to think beyond just getting ROS2 installed and your nodes communicating.
Welcome to the first post in a new series focused on securing your ROS2 environment — starting from the ground up, at the Linux OS level. This guide is crafted to walk you through practical and effective steps to immediately improve the security posture of your robot projects. Our goal is to empower builders and developers to safeguard their work from common attack vectors without getting lost in complexity.





































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)




































































































































































































![GrandChase tier list of the best characters available [April 2025]](https://media.pocketgamer.com/artwork/na-33057-1637756796/grandchase-ios-android-3rd-anniversary.jpg?#)









































































































































































![Apple M4 13-inch iPad Pro On Sale for $200 Off [Deal]](https://www.iclarified.com/images/news/97056/97056/97056-640.jpg)
![Apple Shares New 'Mac Does That' Ads for MacBook Pro [Video]](https://www.iclarified.com/images/news/97055/97055/97055-640.jpg)