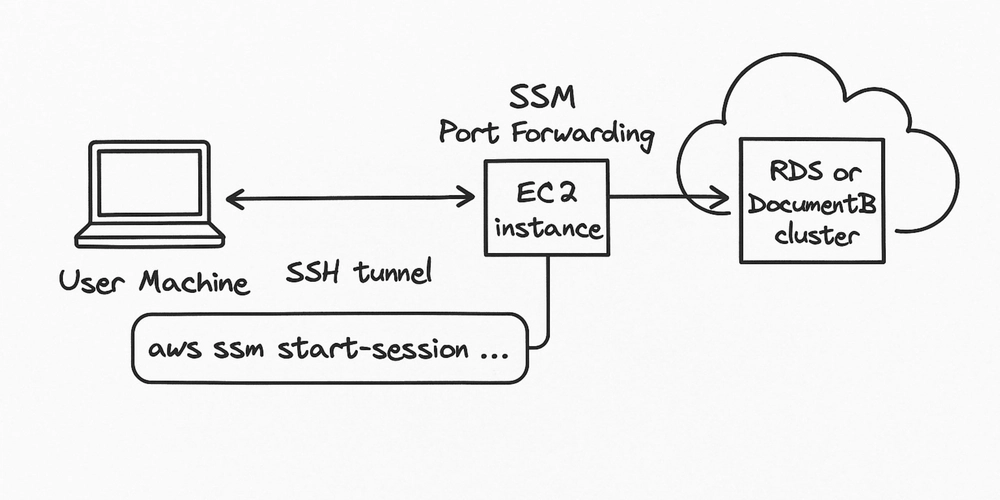
Secure and Seamless Access to Private AWS Databases via SSM Port Forwarding from user machine
Introduction: The SSH Bastion Bottleneck and the GUI Craving For many developers and database administrators working with private AWS database clusters like Aurora PostgreSQL and Document DB, the traditional method of access often involves a familiar, yet somewhat cumbersome, dance. We've all likely navigated the ritual of multiple SSH logins – first to a publicly accessible bastion host and then potentially another hop to the actual database server. While this approach provides a necessary layer of security, it introduces friction into the daily workflow. Consider the scenario: you need to quickly inspect data using your preferred GUI client like DBeaver, pgAdmin or Studio 3T. Instead of a direct connection, you're forced to rely on CLI commands executed through an SSH session. This can be less intuitive, especially for users who prefer the visual interface of a dedicated database tool. Furthermore, the management overhead of the bastion host – the constant need for patching, scaling to handle concurrent connections, and the inherent security considerations of exposing an EC2 instance to the public internet – often feels like an unnecessary tax on productivity. Open Question 1: In your experience, what are the most common pain points Mac/Windows users face when connecting to private AWS databases and how do these issues impact their workflow efficiency? Can you share any specific examples or anecdotes? Enter the desire for a more robust and user-friendly solution – one that empowers users to connect with their familiar GUI database clients directly from their local machines. The goal? To minimize the frustration of multiple logins and the limitations of CLI interaction, all while maintaining a strong security posture. This is where AWS Systems Manager (SSM) Port Forwarding emerges as an elegant and secure alternative. By leveraging the power of the SSM Agent, we can establish secure tunnels to private resources without the need for direct internet exposure. Our goal for this blog post is clear: to provide a comprehensive guide and architectural blueprint for enabling seamless GUI-based database access for users to private Aurora PostgreSQL and DocumentDB clusters using SSM Port Forwarding. I aim to demonstrate how this approach not only enhances user experience but also strengthens the overall security of your AWS environment. Understanding the Power of AWS SSM Port Forwarding At its core, AWS SSM Port Forwarding, facilitated by the AWS-StartPortForwardingSessionToRemoteHost document, provides a secure and auditable way to create network tunnels to private instances without opening inbound ports on those instances. Let's delve into how this mechanism works. It all begins with the SSM Agent, a lightweight piece of software that runs on your EC2 instances within your Virtual Private Cloud (VPC). This agent establishes a secure, outbound connection to the AWS SSM service endpoint. When a user wants to connect to a private database, they initiate a port forwarding session using the AWS CLI or a simple script on their local machine. This command specifies the target EC2 instance (the intermediary), the endpoint adress and port of the destination database cluster (Aurora or DocumentDB), and a local port on their Mac that will act as the entry point for the tunnel. The AWS CLI then communicates with the AWS SSM service, instructing the agent on the specified EC2 instance to establish a secure tunnel. This tunnel effectively maps the local port on the user machine to the private IP address and port of the target database, all through the secure SSM connection. Crucially, the EC2 instance itself only needs outbound connectivity it doesn't require a public IP address or open inbound ports for database access. Diagram Suggestion: A simple, hand-drawn diagram illustrating the basic flow of data from the Mac user's GUI client, through the SSM tunnel, to the private database. This could be a very high-level diagram. Security Benefits: The advantages over a traditional bastion host are significant: No Public Exposure: The EC2 instance acting as the SSM intermediary does not need to be exposed directly to the internet, drastically reducing the attack surface. IAM-Based Control: Access to initiate SSM sessions is granularly controlled through IAM permissions. You define exactly which users or roles can establish these tunnels and to which resources. Security Group Enforcement: The EC2 instance's security group acts as a crucial firewall, controlling the outbound traffic allowed to the private database clusters. Encrypted Sessions: All communication through the SSM session is encrypted, ensuring the confidentiality of data in transit. Reduced Complexity: Eliminating the need to manage public-facing bastion hosts simplifies your infrastructure and reduces potential misconfigurations. User Experience Advantages: The be
Introduction: The SSH Bastion Bottleneck and the GUI Craving
For many developers and database administrators working with private AWS database clusters like Aurora PostgreSQL and Document DB, the traditional method of access often involves a familiar, yet somewhat cumbersome, dance. We've all likely navigated the ritual of multiple SSH logins – first to a publicly accessible bastion host and then potentially another hop to the actual database server. While this approach provides a necessary layer of security, it introduces friction into the daily workflow.
Consider the scenario: you need to quickly inspect data using your preferred GUI client like DBeaver, pgAdmin or Studio 3T. Instead of a direct connection, you're forced to rely on CLI commands executed through an SSH session. This can be less intuitive, especially for users who prefer the visual interface of a dedicated database tool. Furthermore, the management overhead of the bastion host – the constant need for patching, scaling to handle concurrent connections, and the inherent security considerations of exposing an EC2 instance to the public internet – often feels like an unnecessary tax on productivity.
Open Question 1: In your experience, what are the most common pain points Mac/Windows users face when connecting to private AWS databases and how do these issues impact their workflow efficiency? Can you share any specific examples or anecdotes?
Enter the desire for a more robust and user-friendly solution – one that empowers users to connect with their familiar GUI database clients directly from their local machines. The goal? To minimize the frustration of multiple logins and the limitations of CLI interaction, all while maintaining a strong security posture.
This is where AWS Systems Manager (SSM) Port Forwarding emerges as an elegant and secure alternative. By leveraging the power of the SSM Agent, we can establish secure tunnels to private resources without the need for direct internet exposure.
Our goal for this blog post is clear: to provide a comprehensive guide and architectural blueprint for enabling seamless GUI-based database access for users to private Aurora PostgreSQL and DocumentDB clusters using SSM Port Forwarding. I aim to demonstrate how this approach not only enhances user experience but also strengthens the overall security of your AWS environment.
Understanding the Power of AWS SSM Port Forwarding
At its core, AWS SSM Port Forwarding, facilitated by the AWS-StartPortForwardingSessionToRemoteHost document, provides a secure and auditable way to create network tunnels to private instances without opening inbound ports on those instances. Let's delve into how this mechanism works.
It all begins with the SSM Agent, a lightweight piece of software that runs on your EC2 instances within your Virtual Private Cloud (VPC). This agent establishes a secure, outbound connection to the AWS SSM service endpoint.
When a user wants to connect to a private database, they initiate a port forwarding session using the AWS CLI or a simple script on their local machine. This command specifies the target EC2 instance (the intermediary), the endpoint adress and port of the destination database cluster (Aurora or DocumentDB), and a local port on their Mac that will act as the entry point for the tunnel.
The AWS CLI then communicates with the AWS SSM service, instructing the agent on the specified EC2 instance to establish a secure tunnel. This tunnel effectively maps the local port on the user machine to the private IP address and port of the target database, all through the secure SSM connection. Crucially, the EC2 instance itself only needs outbound connectivity it doesn't require a public IP address or open inbound ports for database access.
Diagram Suggestion: A simple, hand-drawn diagram illustrating the basic flow of data from the Mac user's GUI client, through the SSM tunnel, to the private database. This could be a very high-level diagram.
Security Benefits: The advantages over a traditional bastion host are significant:
No Public Exposure: The EC2 instance acting as the SSM intermediary does not need to be exposed directly to the internet, drastically reducing the attack surface.
IAM-Based Control: Access to initiate SSM sessions is granularly controlled through IAM permissions. You define exactly which users or roles can establish these tunnels and to which resources.
Security Group Enforcement: The EC2 instance's security group acts as a crucial firewall, controlling the outbound traffic allowed to the private database clusters.
Encrypted Sessions: All communication through the SSM session is encrypted, ensuring the confidentiality of data in transit.
Reduced Complexity: Eliminating the need to manage public-facing bastion hosts simplifies your infrastructure and reduces potential misconfigurations.
User Experience Advantages: The benefits for Mac users are equally compelling:
Direct GUI Client Connectivity: Users can connect their preferred GUI database clients directly to localhost and the specified local port, as if the database were running locally.
Elimination of SSH Gymnastics: No more juggling multiple SSH sessions or remembering complex SSH tunnel commands.
Consistent Experience: The connection process remains consistent regardless of the underlying database technology (Aurora PostgreSQL or DocumentDB).
Prerequisites (On the User's Machine):
AWS CLI: The AWS Command Line Interface must be installed and configured with valid AWS credentials. These credentials (IAM user or role) need the necessary permissions to initiate SSM sessions (ssm:StartSession, ssm:SendCommand, ssm:TerminateSession) to the designated EC2 instance.
GUI Database Client: The user must have their preferred GUI database client installed (e.g., DBeaver, pgAdmin for PostgreSQL; Studio 3T, DBeaver for DocumentDB).
Architecture Diagram: The Secure Tunnel to Database Bliss
(Handwritten Rough Diagram 1: High-Level Flow)
+--------+ (1. Connect to Local Port) +-----------+
|









































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)




































































































































































































![Blue Archive tier list [April 2025]](https://media.pocketgamer.com/artwork/na-33404-1636469504/blue-archive-screenshot-2.jpg?#)






























.png?#)











-Baldur’s-Gate-3-The-Final-Patch---An-Animated-Short-00-03-43.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)































































































































![Apple's Foldable iPhone May Cost Between $2100 and $2300 [Rumor]](https://www.iclarified.com/images/news/97028/97028/97028-640.jpg)
![Apple Releases Public Betas of iOS 18.5, iPadOS 18.5, macOS Sequoia 15.5 [Download]](https://www.iclarified.com/images/news/97024/97024/97024-640.jpg)
![Apple to Launch In-Store Recycling Promotion Tomorrow, Up to $20 Off Accessories [Gurman]](https://www.iclarified.com/images/news/97023/97023/97023-640.jpg)