Practical Web Vulnerability Scanning with Burp Suite: Methodology and Precision
Burp Suite is a cornerstone tool in modern web application security testing. But its true power isn’t just in the tools — it’s in how they’re used. In this article, we walk through a precise and efficient workflow for identifying real vulnerabilities using Burp Suite Community/Pro in a black-box environment. 1. Define Scope & Target Start with minimal assumptions. Gather target domains, subdomains, and parameters through: Waybackurls, Amass, or Subfinder Passive DNS + certificate transparency logs Sitemap import or crawling (Burp Spider) Limit the scan to authorized domains and respect robots.txt if required. 2. Intercept & Map Enable the Proxy Intercept to capture HTTP(S) traffic between browser and application. Use Burp’s browser or configure system/browser proxy settings (typically 127.0.0.1:8080). As you interact with the app, Burp will: Record requests/responses Build a sitemap Identify insertion points for testing 3. Passive Analysis (Non-Intrusive) Review what Burp found without sending new requests: SSL/TLS misconfigs Open redirects Sensitive disclosures in headers/cookies Misused HTTP methods (PUT/DELETE) Enable passive scanner to flag issues without triggering alarms. 4. Active Scanning (Pro Edition) Switch to Active Scan to perform real injection tests: XSS, SQLi, SSTI, SSRF, LFI Authentication bypass attempts Parameter pollution, caching issues Recommended settings: Enable insertion point optimization Use time-based detection for blind vulnerabilities Integrate with collaborator for out-of-band testing 5. Manual Testing Use Repeater, Intruder, and Decoder for targeted payload injection. Example: fuzzing a search parameter GET /search?q=admin HTTP/1.1 Host: vulnerable.site Send to Repeater → modify payload → observe response differences. Advanced usage: Use Intruder with payload sets (XSS cheat sheet, SQL payloads) Apply Grep – Match to extract indicators Track behavior across sessions with Burp’s Cookie Jar 6. Reporting & Export Burp generates clean HTML/Markdown/PDF reports. Include: Vulnerability summary HTTP transcripts Risk levels + remediation Pro tip: integrate Burp with CI/CD via REST API or extensions like Burp GraphQL Raider, Logger++, or Logger4Burp. Final Notes Burp Suite is only as powerful as your methodology. Precision over volume. Context over automation. In future posts, we’ll explore: Exploiting authenticated attack surfaces with session hijacking Custom extension scripting via Burp Extender API Using Collaborator for DNS/HTTP exfiltration testing Own the surface. Read the patterns. Trigger only when it matters.

Burp Suite is a cornerstone tool in modern web application security testing.
But its true power isn’t just in the tools — it’s in how they’re used.
In this article, we walk through a precise and efficient workflow for identifying real vulnerabilities using Burp Suite Community/Pro in a black-box environment.
1. Define Scope & Target
Start with minimal assumptions.
Gather target domains, subdomains, and parameters through:
-
Waybackurls,Amass, orSubfinder - Passive DNS + certificate transparency logs
- Sitemap import or crawling (Burp Spider)
Limit the scan to authorized domains and respect robots.txt if required.
2. Intercept & Map
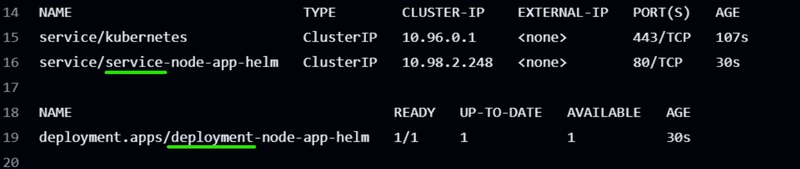
Enable the Proxy Intercept to capture HTTP(S) traffic between browser and application.
Use Burp’s browser or configure system/browser proxy settings (typically 127.0.0.1:8080).
As you interact with the app, Burp will:
- Record requests/responses
- Build a sitemap
- Identify insertion points for testing
3. Passive Analysis (Non-Intrusive)
Review what Burp found without sending new requests:
- SSL/TLS misconfigs
- Open redirects
- Sensitive disclosures in headers/cookies
- Misused HTTP methods (PUT/DELETE)
Enable passive scanner to flag issues without triggering alarms.
4. Active Scanning (Pro Edition)
Switch to Active Scan to perform real injection tests:
- XSS, SQLi, SSTI, SSRF, LFI
- Authentication bypass attempts
- Parameter pollution, caching issues
Recommended settings:
- Enable insertion point optimization
- Use time-based detection for blind vulnerabilities
- Integrate with collaborator for out-of-band testing
5. Manual Testing
Use Repeater, Intruder, and Decoder for targeted payload injection.
Example: fuzzing a search parameter
GET /search?q=admin HTTP/1.1
Host: vulnerable.site
Send to Repeater → modify payload → observe response differences.
Advanced usage:
- Use Intruder with payload sets (XSS cheat sheet, SQL payloads)
- Apply Grep – Match to extract indicators
- Track behavior across sessions with Burp’s Cookie Jar
6. Reporting & Export
Burp generates clean HTML/Markdown/PDF reports.
Include:
- Vulnerability summary
- HTTP transcripts
- Risk levels + remediation
Pro tip: integrate Burp with CI/CD via REST API or extensions like Burp GraphQL Raider, Logger++, or Logger4Burp.
Final Notes
Burp Suite is only as powerful as your methodology.
Precision over volume. Context over automation.
In future posts, we’ll explore:
- Exploiting authenticated attack surfaces with session hijacking
- Custom extension scripting via Burp Extender API
- Using Collaborator for DNS/HTTP exfiltration testing
Own the surface. Read the patterns. Trigger only when it matters.








































































































































































![[The AI Show Episode 143]: ChatGPT Revenue Surge, New AGI Timelines, Amazon’s AI Agent, Claude for Education, Model Context Protocol & LLMs Pass the Turing Test](https://www.marketingaiinstitute.com/hubfs/ep%20143%20cover.png)

































































































































![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)









































































































.jpg?#)































_ArtemisDiana_Alamy.jpg?#)


 (1).webp?#)








































































-xl.jpg)











![Yes, the Gemini icon is now bigger and brighter on Android [U]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/02/Gemini-on-Galaxy-S25.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)










![Apple Rushes Five Planes of iPhones to US Ahead of New Tariffs [Report]](https://www.iclarified.com/images/news/96967/96967/96967-640.jpg)
![Apple Vision Pro 2 Allegedly in Production Ahead of 2025 Launch [Rumor]](https://www.iclarified.com/images/news/96965/96965/96965-640.jpg)