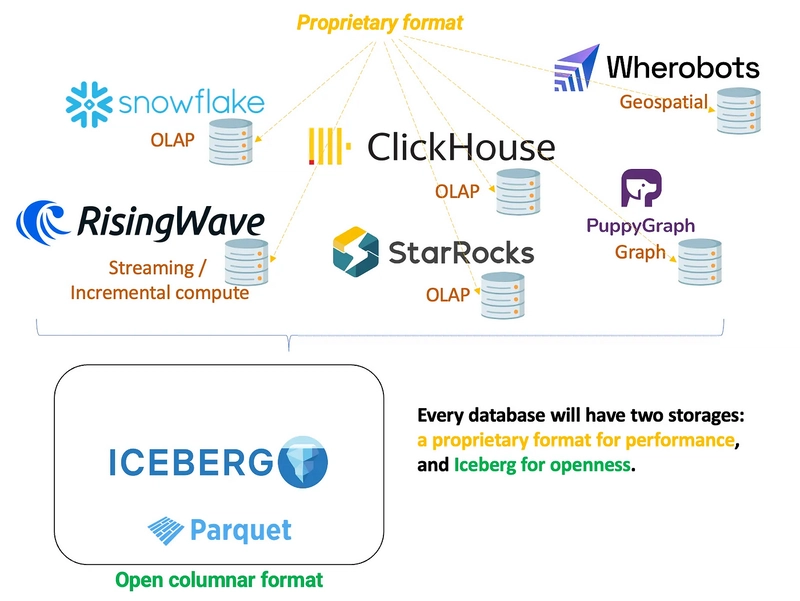
Meet PKI: The Quiet Hero Behind Secure Browsing
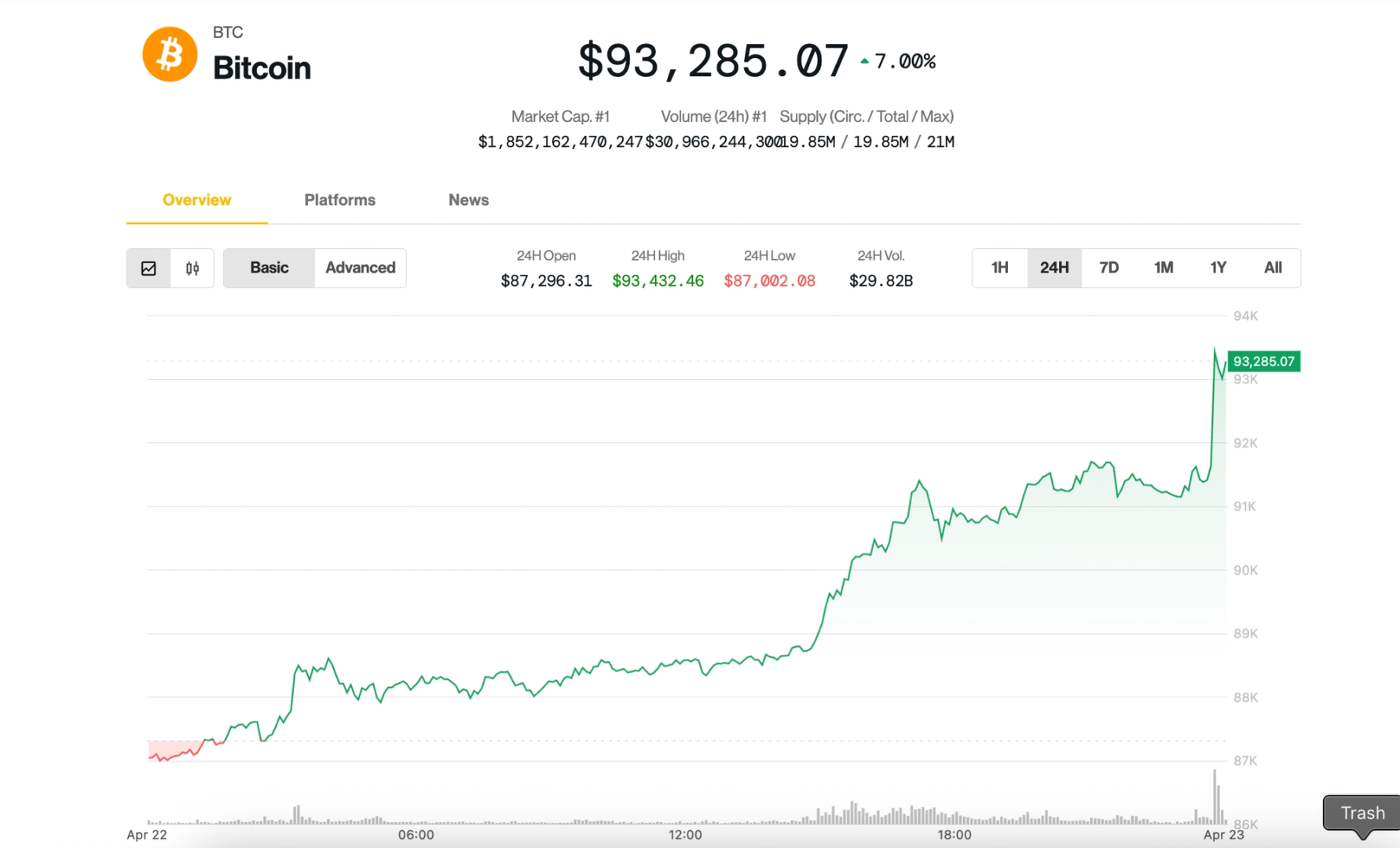
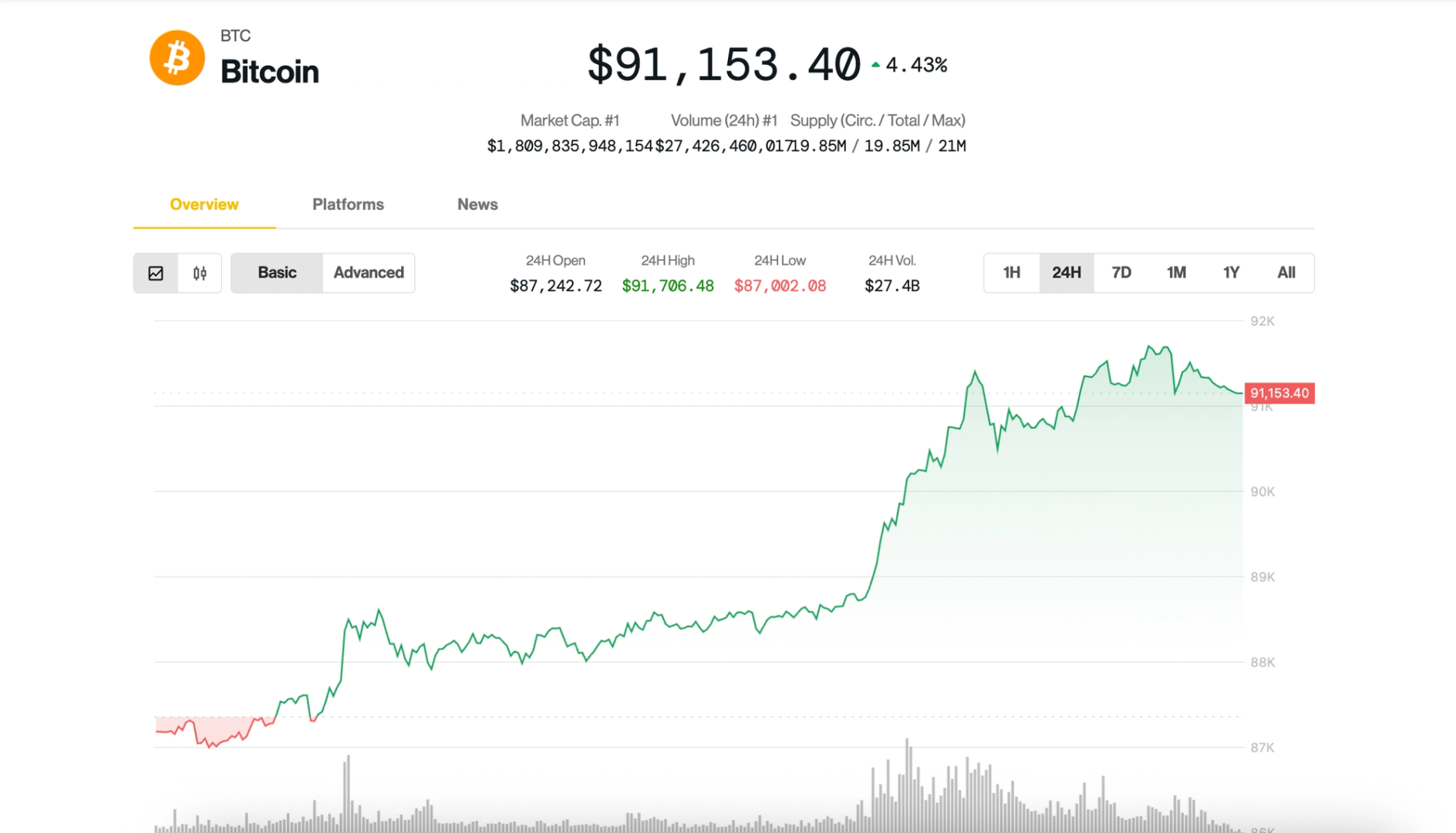
Ever wondered how your data stays secure when you're shopping online, logging into your bank, or even sending an email? Behind the scenes, there’s a superhero framework quietly working to keep everything encrypted, authenticated, and trustworthy. Meet PKI — Public Key Infrastructure. What is PKI? Public Key Infrastructure (PKI) is a system that helps make secure communication possible over the internet. It's like the backstage crew of a rock concert: you don’t always see it, but without it, the whole show would fall apart. At its core, PKI manages two important things: Digital Certificates (like ID cards for websites and apps) Public and Private Keys (for locking and unlocking data) These are used for encryption, authentication, and digital signatures — the trifecta of modern online security. A Quick Peek at Public & Private Keys Imagine you have a mailbox with a mail slot. Anyone can drop letters into it (this is your public key — shareable with the world), but only you have the key to unlock the mailbox and read the letters (that’s your private key — kept secret!). In PKI: Public keys encrypt data Private keys decrypt it OR Private keys sign data Public keys verify that signature This setup ensures data is both confidential and trusted. The Building Blocks of PKI Here’s what makes up a Public Key Infrastructure: 1. Certificate Authority (CA) The trusted VIP that issues digital certificates. When a CA signs your certificate, it’s like a blue checkmark on social media — proof that you’re legit. 2. Registration Authority (RA) The sidekick of the CA. It helps verify that a certificate requester is who they say they are before a certificate is issued. 3. Digital Certificate A file that binds a public key to an entity (like a person, company, or website). It’s your digital passport. It includes: Public key Owner info CA’s digital signature Expiry date 4. Certificate Revocation List (CRL) If a certificate is compromised or no longer trustworthy, it gets revoked. The CRL is the “naughty list” of digital certificates. Where Do We Use PKI? Almost everywhere secure communication is needed. Some common places: SSL/TLS — Secure websites (HTTPS) Email encryption — PGP or S/MIME Secure messaging Code signing — Verifying software integrity Digital ID cards Electronic signatures — Legally binding e-signatures Why Does PKI Matter? Without PKI, we’d be wide open to impersonation, data leaks, and cyber attacks. PKI gives us: Confidentiality – Only the intended recipient can read the data. Integrity – No one can tamper with the data unnoticed. Authentication – Confirm identities in digital spaces. Non-repudiation – Prove that someone really did sign or send something. Final Thoughts PKI might sound intimidating, but it’s really just a clever way of using keys and certificates to build trust in a trustless environment — the internet. So the next time you see that little
Ever wondered how your data stays secure when you're shopping online, logging into your bank, or even sending an email? Behind the scenes, there’s a superhero framework quietly working to keep everything encrypted, authenticated, and trustworthy. Meet PKI — Public Key Infrastructure.
What is PKI?
Public Key Infrastructure (PKI) is a system that helps make secure communication possible over the internet. It's like the backstage crew of a rock concert: you don’t always see it, but without it, the whole show would fall apart.
At its core, PKI manages two important things:
- Digital Certificates (like ID cards for websites and apps)
- Public and Private Keys (for locking and unlocking data)
These are used for encryption, authentication, and digital signatures — the trifecta of modern online security.
A Quick Peek at Public & Private Keys
Imagine you have a mailbox with a mail slot. Anyone can drop letters into it (this is your public key — shareable with the world), but only you have the key to unlock the mailbox and read the letters (that’s your private key — kept secret!).
In PKI:
- Public keys encrypt data
- Private keys decrypt it OR
- Private keys sign data
- Public keys verify that signature
This setup ensures data is both confidential and trusted.
The Building Blocks of PKI
Here’s what makes up a Public Key Infrastructure:
1. Certificate Authority (CA)
The trusted VIP that issues digital certificates. When a CA signs your certificate, it’s like a blue checkmark on social media — proof that you’re legit.
2. Registration Authority (RA)
The sidekick of the CA. It helps verify that a certificate requester is who they say they are before a certificate is issued.
3. Digital Certificate
A file that binds a public key to an entity (like a person, company, or website). It’s your digital passport. It includes:
- Public key
- Owner info
- CA’s digital signature
- Expiry date
4. Certificate Revocation List (CRL)
If a certificate is compromised or no longer trustworthy, it gets revoked. The CRL is the “naughty list” of digital certificates.
Where Do We Use PKI?
Almost everywhere secure communication is needed. Some common places:
- SSL/TLS — Secure websites (HTTPS)
- Email encryption — PGP or S/MIME
- Secure messaging
- Code signing — Verifying software integrity
- Digital ID cards
- Electronic signatures — Legally binding e-signatures
Why Does PKI Matter?
Without PKI, we’d be wide open to impersonation, data leaks, and cyber attacks. PKI gives us:
- Confidentiality – Only the intended recipient can read the data.
- Integrity – No one can tamper with the data unnoticed.
- Authentication – Confirm identities in digital spaces.
- Non-repudiation – Prove that someone really did sign or send something.
Final Thoughts
PKI might sound intimidating, but it’s really just a clever way of using keys and certificates to build trust in a trustless environment — the internet.
So the next time you see that little











































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)

















































































































































































































































-All-will-be-revealed-00-35-05.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)




















































































































![What iPhone 17 model are you most excited to see? [Poll]](https://9to5mac.com/wp-content/uploads/sites/6/2025/04/iphone-17-pro-sky-blue.jpg?quality=82&strip=all&w=290&h=145&crop=1)

















![Hands-On With 'iPhone 17 Air' Dummy Reveals 'Scary Thin' Design [Video]](https://www.iclarified.com/images/news/97100/97100/97100-640.jpg)
![Mike Rockwell is Overhauling Siri's Leadership Team [Report]](https://www.iclarified.com/images/news/97096/97096/97096-640.jpg)
![Instagram Releases 'Edits' Video Creation App [Download]](https://www.iclarified.com/images/news/97097/97097/97097-640.jpg)
![Inside Netflix's Rebuild of the Amsterdam Apple Store for 'iHostage' [Video]](https://www.iclarified.com/images/news/97095/97095/97095-640.jpg)