Landing Zone: A Blueprint for Cloud Deployments
After working in the cloud industry for over two years—mostly with Google Cloud Platform—I began to think that I need to start documenting my experiences. Mainly as a personal reference, but hopefully others might find them useful too. This is my first post in a long while (the last one was about two years ago). To kick things off, I want to start with something fundamental: Landing Zone in the cloud. What is A Landing Zone? A Landing Zone is an initial framework or foundation set up in the cloud (such as Google Cloud, AWS, or Azure) to enable organizations to deploy applications and services in a secure, structured, and scalable manner. Landing Zones are dynamic and evolve as your organization adopts more cloud-based workloads over time. When creating a Landing Zone, there is no one-size-fits-all implementation. Each organization is free to design its Landing Zone based on specific business needs. The design is usually influenced by several factors, such as: Industry type Organizational structure and internal processes Security and compliance requirements Types of workloads to be migrated to the cloud Existing infrastructure (either on-premises or in another cloud) Business and customer locations Sample of Landing Zone Architecture. Image credit: Google Cloud The image above shows an example of Landing Zone architecture on Google Cloud. It highlights how different components come together to create a secure, scalable, and well-managed environment for deploying workloads in the cloud. The core elements of Landing Zone that you should include when designing a Landing Zone: Identity provisioning Resource hierarchy Networking Security controls On top of that, you can also add other components based on your business needs, such as: Monitoring and logging Backup and disaster recovery Compliance Cost efficiency and budget control API management Cluster management Automating Landing Zone Creation — Is It Possible? A Landing Zone, as previously explained, is a framework and foundation for our cloud infrastructure. Based on this foundation, we can set up our environment using whichever method we prefer—such as the GCP Console or Cloud Shell. However, if we need to configure many projects, doing so manually can be time-consuming. To simplify this, we can automate the setup of Landing Zone services using Terraform. To give you a better idea of how this works in practice, here's a simple example of how we can use Terraform to create a basic Landing Zone setup on Google Cloud. main.tf provider "google" { project = var.project_id region = var.region zone = var.zone } resource "google_project" "landing_zone_project" { name = var.project_name project_id = var.project_id org_id = var.org_id billing_account = var.billing_account_id } resource "google_project_service" "enabled_apis" { for_each = toset([ "compute.googleapis.com", "iam.googleapis.com", "cloudresourcemanager.googleapis.com" ]) project = google_project.landing_zone_project.project_id service = each.key } resource "google_project_iam_member" "project_owner" { project = google_project.landing_zone_project.project_id role = "roles/owner" member = "user:${var.user_email}" } resource "google_compute_network" "vpc_network" { name = "landing-zone-vpc" auto_create_subnetworks = true project = google_project.landing_zone_project.project_id } resource "google_compute_instance" "vm_instance" { name = "landing-zone-instance" machine_type = "e2-medium" zone = var.zone project = google_project.landing_zone_project.project_id boot_disk { initialize_params { image = "debian-cloud/debian-11" } } network_interface { network = google_compute_network.vpc_network.name access_config { # Ephemeral external IP } } } This main.tf template lays the groundwork for a basic Google Cloud Landing Zone. It starts by configuring the Google provider using project, region, and zone variables. Then, it creates a new GCP project under your organization, connects it to a billing account, and enables a few essential APIs like Compute Engine, IAM, and Cloud Resource Manager. To ensure proper access, it assigns the "Owner" role to a specified user email. After that, it sets up a default VPC network with automatic subnet creation. Finally, it launches a simple VM instance running Debian 11 and connects it to the VPC. This setup gives you a clean starting point to build more infrastructure on GCP. Since dev.to has a content limit, I’m not including the other Terraform files like variables.tf and terraform.tfvars here. That’s a wrap! This setup might be simple, but it’s a solid starting point if you’re looking to build your own Landing Zone on GCP. There’s still a lot you can add and customize depending on your needs, but hopefully this gives you a head start. If you're
After working in the cloud industry for over two years—mostly with Google Cloud Platform—I began to think that I need to start documenting my experiences. Mainly as a personal reference, but hopefully others might find them useful too.
This is my first post in a long while (the last one was about two years ago). To kick things off, I want to start with something fundamental: Landing Zone in the cloud.
What is A Landing Zone?
A Landing Zone is an initial framework or foundation set up in the cloud (such as Google Cloud, AWS, or Azure) to enable organizations to deploy applications and services in a secure, structured, and scalable manner. Landing Zones are dynamic and evolve as your organization adopts more cloud-based workloads over time.
When creating a Landing Zone, there is no one-size-fits-all implementation. Each organization is free to design its Landing Zone based on specific business needs. The design is usually influenced by several factors, such as:
- Industry type
- Organizational structure and internal processes
- Security and compliance requirements
- Types of workloads to be migrated to the cloud
- Existing infrastructure (either on-premises or in another cloud)
- Business and customer locations

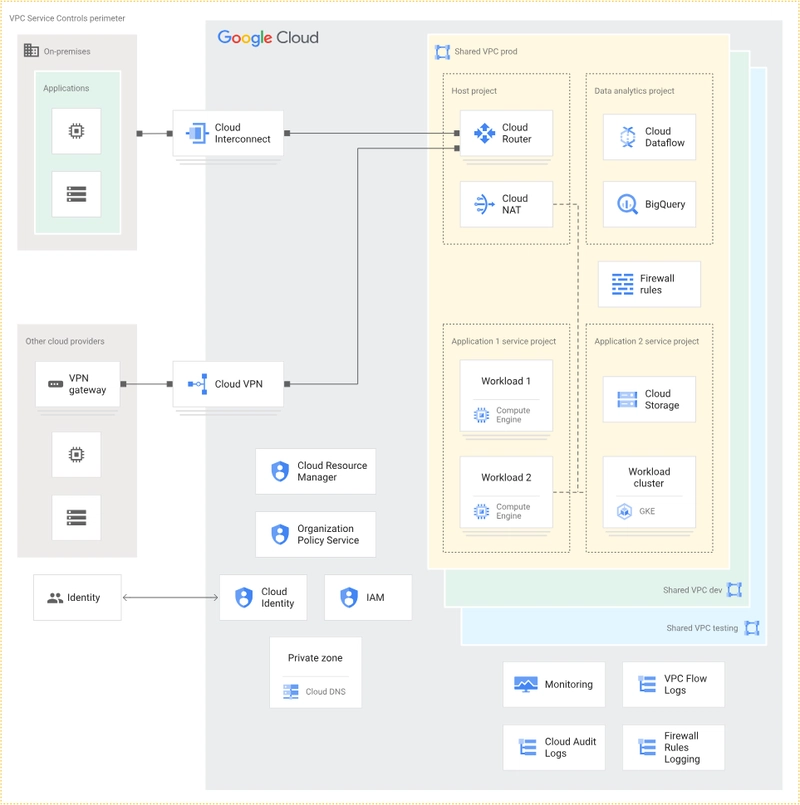
Sample of Landing Zone Architecture. Image credit: Google Cloud
The image above shows an example of Landing Zone architecture on Google Cloud. It highlights how different components come together to create a secure, scalable, and well-managed environment for deploying workloads in the cloud.
The core elements of Landing Zone that you should include when designing a Landing Zone:
- Identity provisioning
- Resource hierarchy
- Networking
- Security controls
On top of that, you can also add other components based on your business needs, such as:
- Monitoring and logging
- Backup and disaster recovery
- Compliance
- Cost efficiency and budget control
- API management
- Cluster management
Automating Landing Zone Creation — Is It Possible?
A Landing Zone, as previously explained, is a framework and foundation for our cloud infrastructure. Based on this foundation, we can set up our environment using whichever method we prefer—such as the GCP Console or Cloud Shell. However, if we need to configure many projects, doing so manually can be time-consuming. To simplify this, we can automate the setup of Landing Zone services using Terraform. To give you a better idea of how this works in practice, here's a simple example of how we can use Terraform to create a basic Landing Zone setup on Google Cloud.
main.tf
provider "google" {
project = var.project_id
region = var.region
zone = var.zone
}
resource "google_project" "landing_zone_project" {
name = var.project_name
project_id = var.project_id
org_id = var.org_id
billing_account = var.billing_account_id
}
resource "google_project_service" "enabled_apis" {
for_each = toset([
"compute.googleapis.com",
"iam.googleapis.com",
"cloudresourcemanager.googleapis.com"
])
project = google_project.landing_zone_project.project_id
service = each.key
}
resource "google_project_iam_member" "project_owner" {
project = google_project.landing_zone_project.project_id
role = "roles/owner"
member = "user:${var.user_email}"
}
resource "google_compute_network" "vpc_network" {
name = "landing-zone-vpc"
auto_create_subnetworks = true
project = google_project.landing_zone_project.project_id
}
resource "google_compute_instance" "vm_instance" {
name = "landing-zone-instance"
machine_type = "e2-medium"
zone = var.zone
project = google_project.landing_zone_project.project_id
boot_disk {
initialize_params {
image = "debian-cloud/debian-11"
}
}
network_interface {
network = google_compute_network.vpc_network.name
access_config {
# Ephemeral external IP
}
}
}
This main.tf template lays the groundwork for a basic Google Cloud Landing Zone. It starts by configuring the Google provider using project, region, and zone variables. Then, it creates a new GCP project under your organization, connects it to a billing account, and enables a few essential APIs like Compute Engine, IAM, and Cloud Resource Manager. To ensure proper access, it assigns the "Owner" role to a specified user email. After that, it sets up a default VPC network with automatic subnet creation. Finally, it launches a simple VM instance running Debian 11 and connects it to the VPC. This setup gives you a clean starting point to build more infrastructure on GCP. Since dev.to has a content limit, I’m not including the other Terraform files like variables.tf and terraform.tfvars here.
That’s a wrap! This setup might be simple, but it’s a solid starting point if you’re looking to build your own Landing Zone on GCP. There’s still a lot you can add and customize depending on your needs, but hopefully this gives you a head start. If you're trying it out or have suggestions, feel free to chat in the comments. Thanks for stopping by!












































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)


































































































































![From fast food worker to cybersecurity engineer with Tae'lur Alexis [Podcast #169]](https://cdn.hashnode.com/res/hashnode/image/upload/v1745242807605/8a6cf71c-144f-4c91-9532-62d7c92c0f65.png?#)























![BPMN-procesmodellering [closed]](https://i.sstatic.net/l7l8q49F.png)





















































































.jpg?#)
.jpg?#)


































.webp?#)


























































































![CarPlay app with web browser for streaming video hits App Store [U]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2024/11/carplay-apple.jpeg?resize=1200%2C628&quality=82&strip=all&ssl=1)



![What’s new in Android’s April 2025 Google System Updates [U: 4/21]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/01/google-play-services-3.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)










![Apple Releases iOS 18.5 Beta 3 and iPadOS 18.5 Beta 3 [Download]](https://www.iclarified.com/images/news/97076/97076/97076-640.jpg)
![Apple Seeds visionOS 2.5 Beta 3 to Developers [Download]](https://www.iclarified.com/images/news/97077/97077/97077-640.jpg)
![Apple Seeds tvOS 18.5 Beta 3 to Developers [Download]](https://www.iclarified.com/images/news/97078/97078/97078-640.jpg)
![Apple Seeds watchOS 11.5 Beta 3 to Developers [Download]](https://www.iclarified.com/images/news/97079/97079/97079-640.jpg)