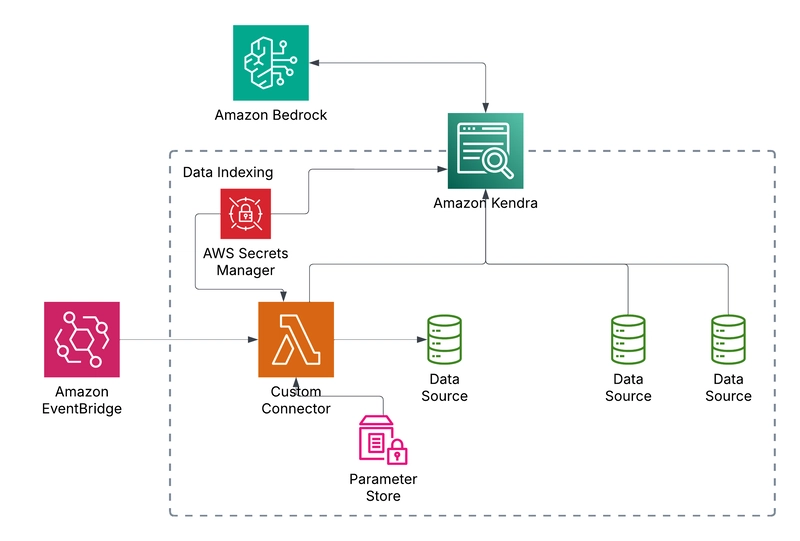
Getting Started with Keycloak: Running Your First Instance
As developers, we often face the challenge of implementing secure authentication and authorization in our applications. Keycloak is an open-source Identity and Access Management solution that can significantly simplify this process. In this first part of our three-part series, we'll set up a Keycloak instance using Docker. Prerequisites Docker installed on your machine Basic understanding of authentication concepts Terminal/Command Prompt access Setting Up Keycloak with Docker First, let's create a docker-compose.yml file: version: '3' services: keycloak: image: quay.io/keycloak/keycloak:22.0.1 environment: - KEYCLOAK_ADMIN=admin - KEYCLOAK_ADMIN_PASSWORD=admin ports: - "8080:8080" command: - start-dev Start the container: docker-compose up -d Your Keycloak instance will be available at http://localhost:8080. Configuring Keycloak Navigate to http://localhost:8080/admin and log in with: Username: admin Password: admin Create a new realm: Click Create Realm Name it demo-realm Click Create Create a client for our applications: Go to Clients → Create client Client ID: demo-app Client Protocol: openid-connect Click Next Enable Client authentication Click Save Configure the client: Valid redirect URIs: http://localhost:8081/* (for Spring Boot) http://localhost:4200/* (for Angular) Web Origins: http://localhost:8081 http://localhost:4200 Click Save Create a test user: Go to Users → Add user Username: testuser Email: testuser@example.com Click Create Go to Credentials tab Set password: password123 Disable Temporary Click Set Password Important Configuration Values Save these values for the next parts: plaintextCopyRealm: demo-realm Client ID: demo-app Client Secret: (find in Clients → demo-app → Credentials tab) Auth URL: http://localhost:8080/realms/demo-realm Testing the Setup Visit http://localhost:8080/realms/demo-realm/.well-known/openid-configuration You should see a JSON document with endpoint configurations In the next part, we'll integrate this Keycloak instance with a Spring Boot application. Stay tuned for Part 2: Integrating Keycloak with Spring Boot!

As developers, we often face the challenge of implementing secure authentication and authorization in our applications. Keycloak is an open-source Identity and Access Management solution that can significantly simplify this process. In this first part of our three-part series, we'll set up a Keycloak instance using Docker.
Prerequisites
Docker installed on your machine
Basic understanding of authentication concepts
Terminal/Command Prompt access
Setting Up Keycloak with Docker
First, let's create a docker-compose.yml file:
version: '3'
services:
keycloak:
image: quay.io/keycloak/keycloak:22.0.1
environment:
- KEYCLOAK_ADMIN=admin
- KEYCLOAK_ADMIN_PASSWORD=admin
ports:
- "8080:8080"
command:
- start-dev
Start the container:
docker-compose up -d
Your Keycloak instance will be available at http://localhost:8080.
Configuring Keycloak
Navigate to http://localhost:8080/admin and log in with:
Username: admin
Password: admin
Create a new realm:
Click
Create Realm
Name itdemo-realm
ClickCreate
Create a client for our applications:
Go to
Clients→Create client
Client ID:demo-app
Client Protocol:openid-connect
ClickNext
EnableClient authentication
ClickSave
Configure the client:
Valid redirect URIs:
http://localhost:8081/* (for Spring Boot)
http://localhost:4200/* (for Angular)
Web Origins:
http://localhost:8081
http://localhost:4200
Click
Save
Create a test user:
Go to
Users→Add user
Username:testuser
Email:testuser@example.com
ClickCreate
Go toCredentialstab
Set password:password123
DisableTemporary
ClickSet Password
Important Configuration Values
Save these values for the next parts:
plaintextCopyRealm: demo-realm
Client ID: demo-app
Client Secret: (find in Clients → demo-app → Credentials tab)
Auth URL: http://localhost:8080/realms/demo-realm
Testing the Setup
Visit http://localhost:8080/realms/demo-realm/.well-known/openid-configuration
You should see a JSON document with endpoint configurations
In the next part, we'll integrate this Keycloak instance with a Spring Boot application.
Stay tuned for Part 2: Integrating Keycloak with Spring Boot!









































































































































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)


























































































































![[FREE EBOOKS] The Kubernetes Bible, The Ultimate Linux Shell Scripting Guide & Four More Best Selling Titles](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)



![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)






































































































.png?#)




.jpg?#)
































_Christophe_Coat_Alamy.jpg?#)







































































































![Rapidus in Talks With Apple as It Accelerates Toward 2nm Chip Production [Report]](https://www.iclarified.com/images/news/96937/96937/96937-640.jpg)