Deploying a Static Website on AWS S3 & EC2 Using Terraform" published: true
Deploying a Static Website on AWS S3 & EC2 Using Terraform Infrastructure as Code (IaC) simplifies cloud management. In this guide, we'll automate the deployment of a static website on AWS S3 and create an EC2 instance using Terraform. What We'll Cover S3 Bucket Creation & Hosting – Automating website deployment. Bucket Policy for Public Access – Ensuring public accessibility. EC2 Instance Creation – Managing compute resources. Using Variables & Outputs – Making the configuration reusable. Prerequisites AWS account with CLI configured (aws configure) Terraform installed (terraform -v) Step 1: Configure Terraform & AWS Provider Create a main.tf file and define the Terraform and AWS provider configuration: terraform { required_version = ">= 1.7.4" required_providers { aws = { source = "hashicorp/aws" version = "5.40.0" } } } provider "aws" { profile = "default" region = "us-east-1" } Step 2: Create an S3 Bucket for Static Website Hosting resource "aws_s3_bucket" "website_bucket" { bucket = "my-static-website-43234" } resource "aws_s3_bucket_website_configuration" "website_config" { bucket = aws_s3_bucket.website_bucket.id index_document { suffix = "index.html" } } resource "aws_s3_object" "index_file" { bucket = aws_s3_bucket.website_bucket.id key = "index.html" source = "index.html" content_type = "text/html" etag = filemd5("index.html") } Step 3: Configure Public Access Policy resource "aws_s3_bucket_public_access_block" "public_access" { bucket = aws_s3_bucket.website_bucket.id block_public_acls = false block_public_policy = false } resource "aws_s3_bucket_policy" "allow_public_access" { bucket = aws_s3_bucket.website_bucket.id policy = jsonencode({ Version = "2012-10-17" Statement = [ { Sid = "PublicReadGetObject" Effect = "Allow" Principal = "*" Action = "s3:GetObject" Resource = "${aws_s3_bucket.website_bucket.arn}/*" } ] }) depends_on = [aws_s3_bucket_public_access_block.public_access] } Step 4: Create an EC2 Instance resource "aws_instance" "web_server" { ami = "ami-0c55b159cbfafe1f0" instance_type = "t2.micro" tags = { Name = "WebServerInstance" } } Step 5: Use Variables & Outputs Define variables in variables.tf: variable "instance_type" { description = "Type of EC2 instance" type = string default = "t2.micro" } variable "website_bucket_name" { description = "S3 bucket name for website hosting" type = string default = "my-static-website-43234" } Define outputs in outputs.tf: output "website_url" { value = "http://${aws_s3_bucket.website_bucket.bucket}.s3-website.${provider.aws.region}.amazonaws.com" } output "ec2_instance_id" { value = aws_instance.web_server.id } output "ec2_public_ip" { value = aws_instance.web_server.public_ip } Step 6: Deploy with Terraform terraform init terraform plan terraform apply -auto-approve To destroy the infrastructure: terraform destroy -auto-approve Conclusion By following these steps, you automated the deployment of an S3-hosted static website and an EC2 instance using Terraform. This approach ensures reproducibility, scalability, and efficient cloud management.
Deploying a Static Website on AWS S3 & EC2 Using Terraform
Infrastructure as Code (IaC) simplifies cloud management. In this guide, we'll automate the deployment of a static website on AWS S3 and create an EC2 instance using Terraform.
What We'll Cover
- S3 Bucket Creation & Hosting – Automating website deployment.
- Bucket Policy for Public Access – Ensuring public accessibility.
- EC2 Instance Creation – Managing compute resources.
- Using Variables & Outputs – Making the configuration reusable.
Prerequisites
- AWS account with CLI configured (
aws configure) - Terraform installed (
terraform -v)
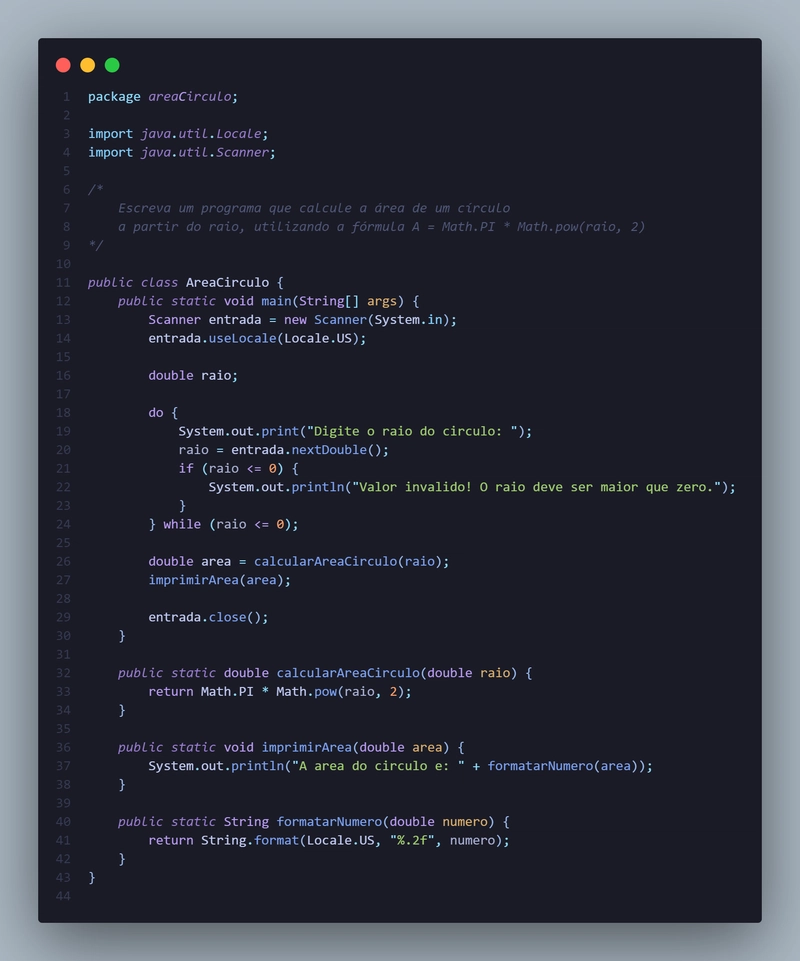
Step 1: Configure Terraform & AWS Provider
Create a main.tf file and define the Terraform and AWS provider configuration:
terraform {
required_version = ">= 1.7.4"
required_providers {
aws = {
source = "hashicorp/aws"
version = "5.40.0"
}
}
}
provider "aws" {
profile = "default"
region = "us-east-1"
}
Step 2: Create an S3 Bucket for Static Website Hosting
resource "aws_s3_bucket" "website_bucket" {
bucket = "my-static-website-43234"
}
resource "aws_s3_bucket_website_configuration" "website_config" {
bucket = aws_s3_bucket.website_bucket.id
index_document {
suffix = "index.html"
}
}
resource "aws_s3_object" "index_file" {
bucket = aws_s3_bucket.website_bucket.id
key = "index.html"
source = "index.html"
content_type = "text/html"
etag = filemd5("index.html")
}
Step 3: Configure Public Access Policy
resource "aws_s3_bucket_public_access_block" "public_access" {
bucket = aws_s3_bucket.website_bucket.id
block_public_acls = false
block_public_policy = false
}
resource "aws_s3_bucket_policy" "allow_public_access" {
bucket = aws_s3_bucket.website_bucket.id
policy = jsonencode({
Version = "2012-10-17"
Statement = [
{
Sid = "PublicReadGetObject"
Effect = "Allow"
Principal = "*"
Action = "s3:GetObject"
Resource = "${aws_s3_bucket.website_bucket.arn}/*"
}
]
})
depends_on = [aws_s3_bucket_public_access_block.public_access]
}
Step 4: Create an EC2 Instance
resource "aws_instance" "web_server" {
ami = "ami-0c55b159cbfafe1f0"
instance_type = "t2.micro"
tags = {
Name = "WebServerInstance"
}
}
Step 5: Use Variables & Outputs
Define variables in variables.tf:
variable "instance_type" {
description = "Type of EC2 instance"
type = string
default = "t2.micro"
}
variable "website_bucket_name" {
description = "S3 bucket name for website hosting"
type = string
default = "my-static-website-43234"
}
Define outputs in outputs.tf:
output "website_url" {
value = "http://${aws_s3_bucket.website_bucket.bucket}.s3-website.${provider.aws.region}.amazonaws.com"
}
output "ec2_instance_id" {
value = aws_instance.web_server.id
}
output "ec2_public_ip" {
value = aws_instance.web_server.public_ip
}
Step 6: Deploy with Terraform
terraform init
terraform plan
terraform apply -auto-approve
To destroy the infrastructure:
terraform destroy -auto-approve
Conclusion
By following these steps, you automated the deployment of an S3-hosted static website and an EC2 instance using Terraform. This approach ensures reproducibility, scalability, and efficient cloud management.









































































































































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)


























































































































![[FREE EBOOKS] The Kubernetes Bible, The Ultimate Linux Shell Scripting Guide & Four More Best Selling Titles](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)



![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)






































































































.png?#)




.jpg?#)































_Christophe_Coat_Alamy.jpg?#)







































































































![Rapidus in Talks With Apple as It Accelerates Toward 2nm Chip Production [Report]](https://www.iclarified.com/images/news/96937/96937/96937-640.jpg)