AWS Config vs Kubernetes Native Policy Engines: Who Governs What?
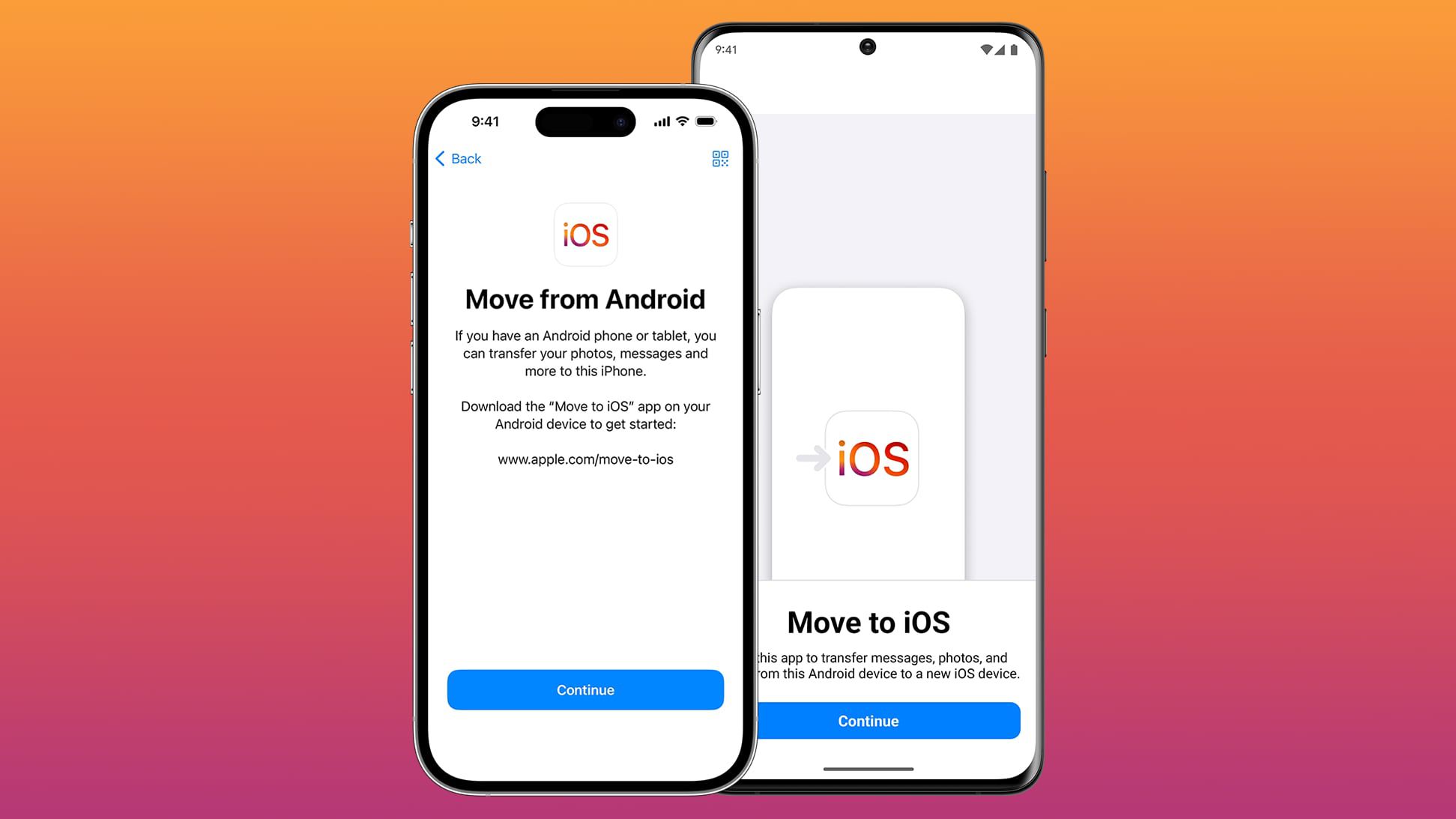
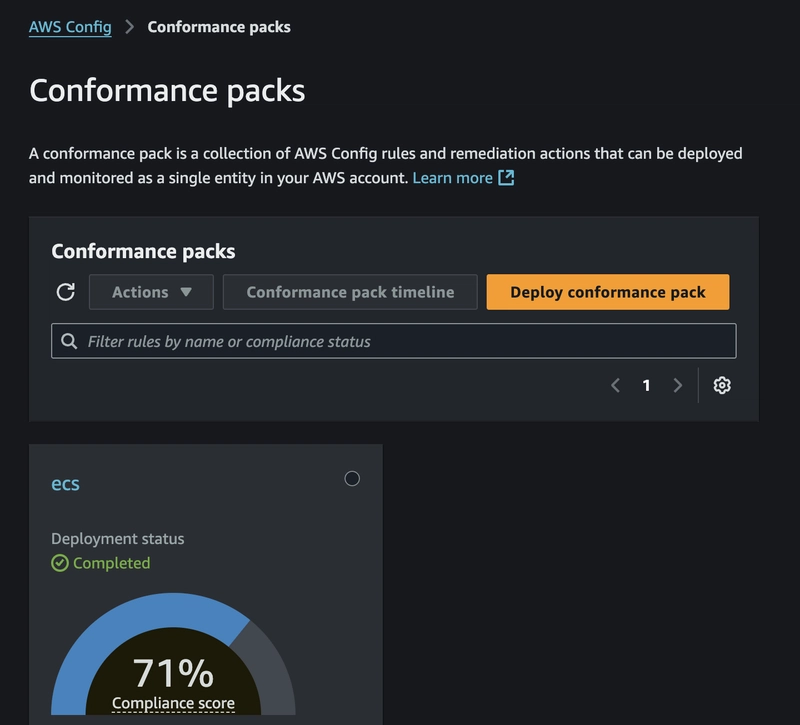
In modern cloud-native environments, compliance, governance, and standardization are critical to ensuring security, operational efficiency, and regulatory adherence. As organizations adopt containerized infrastructure, enforcing consistent policies across platforms like Amazon EKS (Kubernetes-based) and ECS (serverless containers) becomes increasingly complex. At first glance, AWS Config and Kubernetes-native policy engines like OPA Gatekeeper and Kyverno may appear to serve the same function — enforcing rules and ensuring compliance in containerized workloads. But in reality, they operate at different layers, solve distinct problems, and target different scopes of governance. AWS Config is designed for cloud-wide compliance across AWS resources, whereas Kubernetes-native engines are focused on cluster-level policy enforcement within the Kubernetes API lifecycle. In environments where workloads span EKS, ECS, and other AWS services, these tools must often coexist — not compete. This article dives into their differences, where they overlap, and most importantly: who really governs what in a dynamic, multi-platform cloud environment. What is AWS Config? AWS Config is a service that continuously monitors and records AWS resource configurations and evaluates them against desired states. Think of it as a compliance engine: it tracks configuration changes and helps you answer questions like: - Are my EKS clusters configured securely? - Are ECS tasks using only approved IAM roles? - Is anything exposed to the public internet unintentionally? In a cloud environment, AWS Config works by recording and capturing configuration changes in AWS resources using a Config Recorder. By applying AWS Config rules (either managed or custom lambda rules), it can automatically assess whether your resource configurations adhere to best practices and compliance standards. Finally, when noncompliant configurations are detected, AWS Config can initiate automatic remediation actions (if configured) using AWS Systems Manager Automation documents, ensuring resources are promptly corrected to maintain compliance. Using AWS Config with EKS and ECS When operating Kubernetes or container workloads at scale, governance isn’t optional — it’s essential. In Amazon EKS, AWS Config helps you track key components such as: EKS control plane logging, VPC settings and network exposure, encryption status for logs and secrets and IAM roles used by worker node groups. It can detect misconfigurations like:
In modern cloud-native environments, compliance, governance, and standardization are critical to ensuring security, operational efficiency, and regulatory adherence. As organizations adopt containerized infrastructure, enforcing consistent policies across platforms like Amazon EKS (Kubernetes-based) and ECS (serverless containers) becomes increasingly complex.
At first glance, AWS Config and Kubernetes-native policy engines like OPA Gatekeeper and Kyverno may appear to serve the same function — enforcing rules and ensuring compliance in containerized workloads. But in reality, they operate at different layers, solve distinct problems, and target different scopes of governance. AWS Config is designed for cloud-wide compliance across AWS resources, whereas Kubernetes-native engines are focused on cluster-level policy enforcement within the Kubernetes API lifecycle.
In environments where workloads span EKS, ECS, and other AWS services, these tools must often coexist — not compete. This article dives into their differences, where they overlap, and most importantly: who really governs what in a dynamic, multi-platform cloud environment.
What is AWS Config?
AWS Config is a service that continuously monitors and records AWS resource configurations and evaluates them against desired states. Think of it as a compliance engine: it tracks configuration changes and helps you answer questions like:
- Are my EKS clusters configured securely?
- Are ECS tasks using only approved IAM roles?
- Is anything exposed to the public internet unintentionally?
In a cloud environment, AWS Config works by recording and capturing configuration changes in AWS resources using a Config Recorder. By applying AWS Config rules (either managed or custom lambda rules), it can automatically assess whether your resource configurations adhere to best practices and compliance standards. Finally, when noncompliant configurations are detected, AWS Config can initiate automatic remediation actions (if configured) using AWS Systems Manager Automation documents, ensuring resources are promptly corrected to maintain compliance.
Using AWS Config with EKS and ECS
When operating Kubernetes or container workloads at scale, governance isn’t optional — it’s essential.
In Amazon EKS, AWS Config helps you track key components such as: EKS control plane logging, VPC settings and network exposure, encryption status for logs and secrets and IAM roles used by worker node groups. It can detect misconfigurations like:





































































































































































![[The AI Show Episode 145]: OpenAI Releases o3 and o4-mini, AI Is Causing “Quiet Layoffs,” Executive Order on Youth AI Education & GPT-4o’s Controversial Update](https://www.marketingaiinstitute.com/hubfs/ep%20145%20cover.png)








































































































































































































































































_Inge_Johnsson-Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)























































































![Turn any iPad into a gaming display with this one simple trick [Video]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/05/iPad-as-console-FI.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)













![Apple Shares Official Teaser for 'Highest 2 Lowest' Starring Denzel Washington [Video]](https://www.iclarified.com/images/news/97221/97221/97221-640.jpg)

![Under-Display Face ID Coming to iPhone 18 Pro and Pro Max [Rumor]](https://www.iclarified.com/images/news/97215/97215/97215-640.jpg)
![New Powerbeats Pro 2 Wireless Earbuds On Sale for $199.95 [Lowest Price Ever]](https://www.iclarified.com/images/news/97217/97217/97217-640.jpg)