Agentic Analysis of Open Source Package Code for Malware
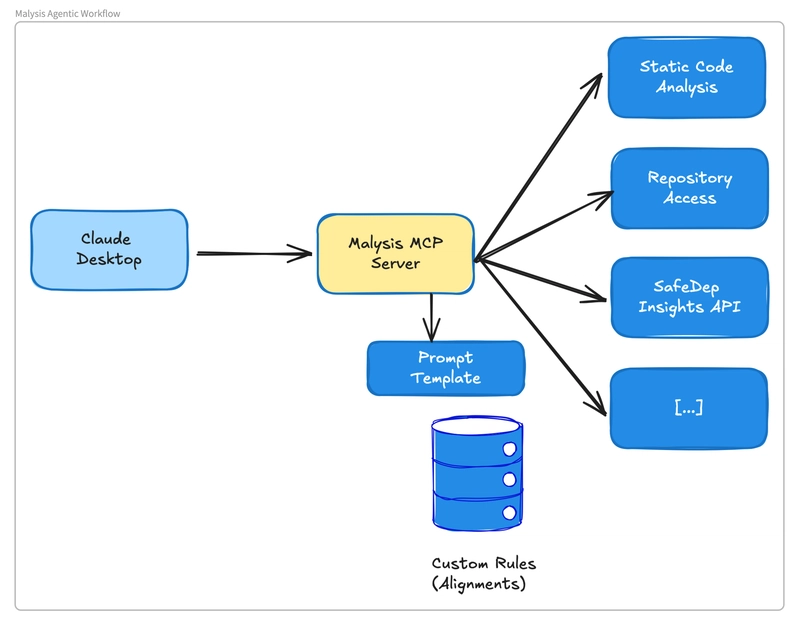
Experiments with agentic workflows for malicious package analysis built using Claude Desktop, Model Context Protocol (MCP) server, static code analysis and SafeDep Cloud API tools. Demo Architecture For the demo, we exposed the following through an MCP Interface to MCP clients like Claude Desk Insights API Malicious Package Scanning API Misc tools for GitHub API access Misc tools for package registry (e.g. npm) access Looking Ahead While the results are promising and exciting for us but there is a long way to go to productionize this. For example, our automated systems that monitor public package registries use statically coded workflows and operate at < 10% time cost of the agentic execution currently. It also minimizes LLM calls by leveraging static code analysis and opinionated rules to scale much better. For proactive protection against malicious open source packages in CI/CD, try vet, its free and open source ➡️ https://github.com/safedep/vet
Experiments with agentic workflows for malicious package analysis built using Claude Desktop, Model Context Protocol (MCP) server, static code analysis and SafeDep Cloud API tools.
Demo
Architecture
For the demo, we exposed the following through an MCP Interface to MCP clients like Claude Desk
- Insights API
- Malicious Package Scanning API
- Misc tools for GitHub API access
- Misc tools for package registry (e.g.
npm) access
Looking Ahead
While the results are promising and exciting for us but there is a long way to go to productionize this. For example, our automated systems that monitor public package registries use statically coded workflows and operate at < 10% time cost of the agentic execution currently. It also minimizes LLM calls by leveraging static code analysis and opinionated rules to scale much better.
For proactive protection against malicious open source packages in CI/CD, try vet, its free and open source








































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)
































































































































































































![Blue Archive tier list [April 2025]](https://media.pocketgamer.com/artwork/na-33404-1636469504/blue-archive-screenshot-2.jpg?#)






























.png?#)









.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)




























.webp?#)















































































![PSA: It’s not just you, Spotify is down [U: Fixed]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2023/06/spotify-logo-2.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)



![[Update: Optional] Google rolling out auto-restart security feature to Android](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/01/google-play-services-2.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)













![Apple Vision 'Air' Headset May Feature Titanium and iPhone 5-Era Black Finish [Rumor]](https://www.iclarified.com/images/news/97040/97040/97040-640.jpg)


![Apple to Split Enterprise and Western Europe Roles as VP Exits [Report]](https://www.iclarified.com/images/news/97032/97032/97032-640.jpg)