What is Operational Technology (OT) Security?
As cyber threats evolve and industrial systems become increasingly digitized, Operational Technology (OT) security has emerged as a critical pillar of cybersecurity. Once isolated from the digital world, OT environments are now intertwined with IT systems—creating both efficiency and risk. With industries like energy, manufacturing, and utilities relying on OT systems to manage physical processes, even a minor breach can trigger catastrophic consequences. Defining Operational Technology Operational Technology refers to the software and hardware systems that control physical devices, infrastructure, and industrial processes. These systems power essential services, from electricity grids to assembly lines, ensuring that operations run safely and reliably. Unlike IT systems, OT environments prioritize real-time performance and continuous uptime, making traditional security solutions insufficient for their protection. Why OT Security Is No Longer Optional With the rise of the Industrial Internet of Things (IIoT), the line between IT and OT has blurred. While this convergence offers better data insights and automation, it also exposes OT systems—many of which rely on outdated protocols—to modern cyber threats. Attacks targeting OT infrastructures are increasing, and their effects aren’t limited to data loss. They can disrupt public utilities, halt production, or even endanger lives. What Sets OT Security Apart from IT Security? The objectives and design of OT security are fundamentally different from those of IT. OT security focuses on maintaining operational continuity and physical safety, whereas IT security emphasizes data protection. OT systems often run on legacy software with long lifecycles and minimal patching. Their proprietary protocols, limited internet exposure, and high availability requirements make security updates difficult without impacting operations. Key Components and Threat Vectors Core components of OT environments include: ICS (Industrial Control Systems): Oversee physical operations and equipment. SCADA Systems: Provide centralized monitoring and control. IIoT Devices: Collect and transmit real-time operational data. These systems are increasingly targeted by cybercriminals aiming to exploit vulnerabilities for financial gain, espionage, or disruption. Building a Resilient OT Security Framework To effectively secure OT systems, organizations should: Map and monitor all connected assets. Implement network segmentation to isolate critical systems. Deploy real-time threat detection and behavioral monitoring. Apply zero-trust principles and multi-factor authentication. Conduct regular staff training and simulate cyberattack scenarios. Conclusion: Prioritizing Cyber-Physical Protection Operational environments form the backbone of critical infrastructure, and their protection demands a dedicated, adaptive security strategy. As industrial sectors modernize, OT security must evolve in parallel—bridging the gap between legacy technology and the digital age to ensure safe, uninterrupted operations.


As cyber threats evolve and industrial systems become increasingly digitized, Operational Technology (OT) security has emerged as a critical pillar of cybersecurity. Once isolated from the digital world, OT environments are now intertwined with IT systems—creating both efficiency and risk. With industries like energy, manufacturing, and utilities relying on OT systems to manage physical processes, even a minor breach can trigger catastrophic consequences.
Defining Operational Technology
Operational Technology refers to the software and hardware systems that control physical devices, infrastructure, and industrial processes. These systems power essential services, from electricity grids to assembly lines, ensuring that operations run safely and reliably. Unlike IT systems, OT environments prioritize real-time performance and continuous uptime, making traditional security solutions insufficient for their protection.
Why OT Security Is No Longer Optional
With the rise of the Industrial Internet of Things (IIoT), the line between IT and OT has blurred. While this convergence offers better data insights and automation, it also exposes OT systems—many of which rely on outdated protocols—to modern cyber threats. Attacks targeting OT infrastructures are increasing, and their effects aren’t limited to data loss. They can disrupt public utilities, halt production, or even endanger lives.
What Sets OT Security Apart from IT Security?
The objectives and design of OT security are fundamentally different from those of IT. OT security focuses on maintaining operational continuity and physical safety, whereas IT security emphasizes data protection. OT systems often run on legacy software with long lifecycles and minimal patching. Their proprietary protocols, limited internet exposure, and high availability requirements make security updates difficult without impacting operations.
Key Components and Threat Vectors
Core components of OT environments include:
- ICS (Industrial Control Systems): Oversee physical operations and equipment.
- SCADA Systems: Provide centralized monitoring and control.
- IIoT Devices: Collect and transmit real-time operational data.
These systems are increasingly targeted by cybercriminals aiming to exploit vulnerabilities for financial gain, espionage, or disruption.
Building a Resilient OT Security Framework
To effectively secure OT systems, organizations should:
- Map and monitor all connected assets.
- Implement network segmentation to isolate critical systems.
- Deploy real-time threat detection and behavioral monitoring.
- Apply zero-trust principles and multi-factor authentication.
- Conduct regular staff training and simulate cyberattack scenarios.
Conclusion: Prioritizing Cyber-Physical Protection
Operational environments form the backbone of critical infrastructure, and their protection demands a dedicated, adaptive security strategy. As industrial sectors modernize, OT security must evolve in parallel—bridging the gap between legacy technology and the digital age to ensure safe, uninterrupted operations.






































































































































































![[The AI Show Episode 145]: OpenAI Releases o3 and o4-mini, AI Is Causing “Quiet Layoffs,” Executive Order on Youth AI Education & GPT-4o’s Controversial Update](https://www.marketingaiinstitute.com/hubfs/ep%20145%20cover.png)












































































































































































































































































































































































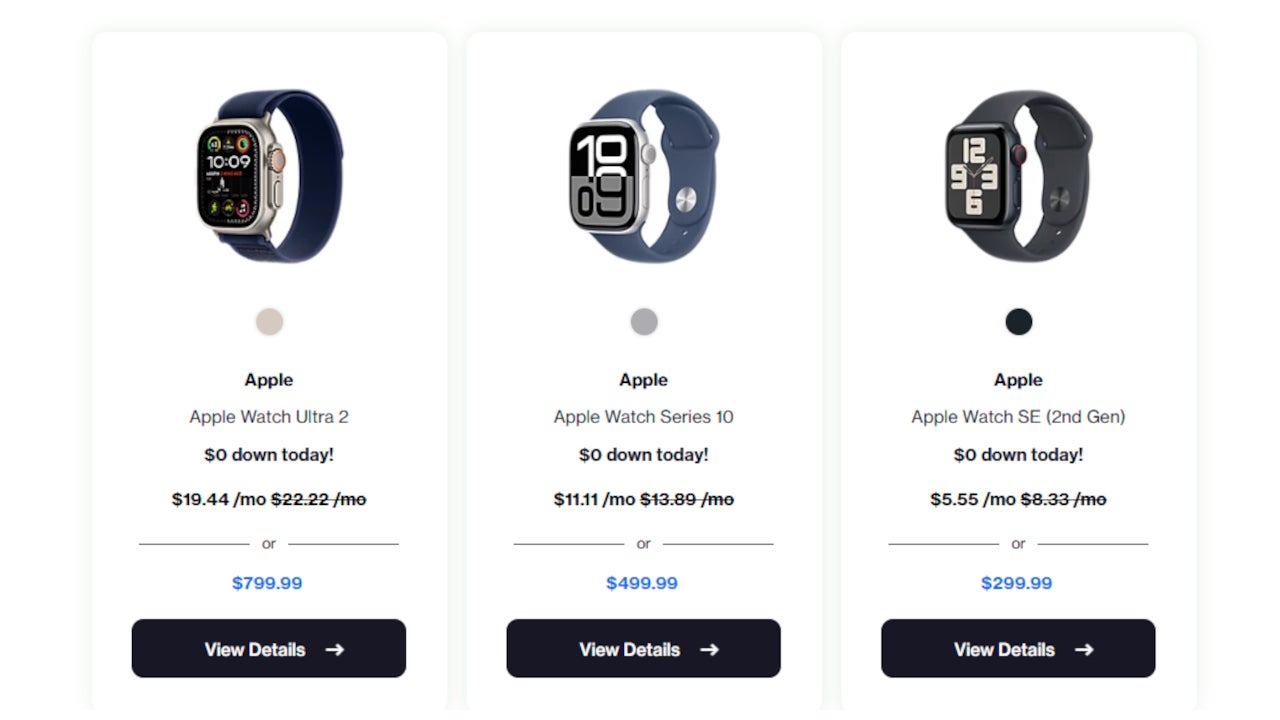
![Apple Shares Official Teaser for 'Highest 2 Lowest' Starring Denzel Washington [Video]](https://www.iclarified.com/images/news/97221/97221/97221-640.jpg)

![Under-Display Face ID Coming to iPhone 18 Pro and Pro Max [Rumor]](https://www.iclarified.com/images/news/97215/97215/97215-640.jpg)
![New Powerbeats Pro 2 Wireless Earbuds On Sale for $199.95 [Lowest Price Ever]](https://www.iclarified.com/images/news/97217/97217/97217-640.jpg)