What are the common methods to prevent unauthorized access to FPGA designs?
FPGAs are often used in sensitive applications (e.g., defense, finance, IoT), making security critical. Below are key techniques to protect FPGA designs from unauthorized access, reverse engineering, and tampering. 1. Bitstream Encryption What it does: Encrypts the FPGA configuration file (*.bit/.bin) to prevent cloning or tampering. How it works: FPGA vendors (Xilinx, Intel) provide AES-256 encryption support. A secure key (stored in battery-backed RAM, eFUSE, or an external HSM) decrypts the bitstream during loading. Supported FPGAs: Xilinx: UltraScale+, Versal (AES-256, RSA authentication). Intel (Altera): MAX 10, Stratix 10 (AES-256). Limitations: Vulnerable if keys are exposed (e.g., via side-channel attacks). Requires secure key storage. 2. Authentication & Secure Boot What it does: Ensures only trusted bitstreams can be loaded. Methods: RSA or ECDSA signatures: FPGA verifies bitstream authenticity before loading. Chain of trust (e.g., Xilinx’s Secure Boot): Boot ROM verifies the first-stage bootloader. Bootloader verifies the application bitstream. Supported FPGAs: Xilinx Zynq UltraScale+ (PS-side secure boot). Intel Stratix 10 (HPS secure boot). 3. Physical Anti-Tamper Measures What it does: Detects and responds to physical attacks (e.g., probing, decapping). Techniques: Tamper detection circuits: Wipe keys if the enclosure is opened. Active shielding: Mesh layers detect drilling/cutting. Temperature/voltage sensors: Shutdown if under attack. Example FPGAs: Xilinx Spartan-6 (tamper-resistant features). Microsemi (Microchip) SmartFusion2 (anti-tamper IP). 4. Obfuscation & Logic Locking What it does: Makes reverse engineering harder. Methods: Logic encryption: Insert "key-gated" logic blocks that only work with a secret key. Camouflaged cells: Hide true logic functions. Dummy routes: Add fake connections to confuse attackers. Limitations: Not foolproof against advanced attacks (e.g., SAT attacks on logic locking). 5. Secure Key Storage What it does: Protects encryption/authentication keys. Options: Battery-backed RAM (BBRAM): Volatile, but secure if power is cut. eFUSE (one-time programmable): Permanent but irreversible. Hardware Security Modules (HSMs): External secure storage (e.g., TPM, Smartcard). PUF (Physical Unclonable Function): Generates unique keys from silicon variations. 6. JTAG & Debug Port Lockdown What it does: Prevents unauthorized access via debug interfaces. Methods: Disable JTAG after programming: Fuse-based locking (Xilinx, Intel). Password-protect JTAG: Requires auth to access. Use secure debug protocols: Arm’s CoreSight with authentication. 7. Dynamic Partial Reconfiguration (DPR) Security What it does: Secures designs that use runtime reconfiguration. Methods: Encrypt partial bitstreams. Authenticate updates before loading. 8. Secure Update Mechanisms What it does: Prevents malicious firmware updates. Methods: Signed updates: Only accept bitstreams with valid signatures. Rollback protection: Block downgrade attacks. 9. Side-Channel Attack Mitigation What it does: Prevents key extraction via power/EM analysis. Methods: Masking: Hide crypto operations with random noise. Constant-time algorithms: Avoid key-dependent timing leaks. 10. Vendor-Specific Security Features Comparison of Security Methods Best Practices for FPGA Security Always encrypt bitstreams (AES-256 + authentication). Disable unused interfaces (JTAG, USB-UART). Use secure key storage (eFUSE, HSM, or PUF). Regularly update firmware with signed patches. Audit for side-channel leaks in crypto designs. Conclusion FPGA security requires a layered approach—combining encryption, authentication, tamper resistance, and secure key storage. For high-risk applications (e.g., defense), Xilinx Versal or Intel Stratix 10 with secure boot + HSMs are recommended. For cost-sensitive designs, AES-256 + JTAG lockdown is a minimum.
FPGAs are often used in sensitive applications (e.g., defense, finance, IoT), making security critical. Below are key techniques to protect FPGA designs from unauthorized access, reverse engineering, and tampering.
1. Bitstream Encryption
What it does: Encrypts the FPGA configuration file (*.bit/.bin) to prevent cloning or tampering.
How it works:
- FPGA vendors (Xilinx, Intel) provide AES-256 encryption support.
- A secure key (stored in battery-backed RAM, eFUSE, or an external HSM) decrypts the bitstream during loading.
Supported FPGAs:
- Xilinx: UltraScale+, Versal (AES-256, RSA authentication).
- Intel (Altera): MAX 10, Stratix 10 (AES-256).
Limitations:
- Vulnerable if keys are exposed (e.g., via side-channel attacks).
- Requires secure key storage.
2. Authentication & Secure Boot
What it does: Ensures only trusted bitstreams can be loaded.
Methods:
RSA or ECDSA signatures: FPGA verifies bitstream authenticity before loading.
Chain of trust (e.g., Xilinx’s Secure Boot):
Boot ROM verifies the first-stage bootloader.
Bootloader verifies the application bitstream.
Supported FPGAs:
- Xilinx Zynq UltraScale+ (PS-side secure boot).
- Intel Stratix 10 (HPS secure boot).
3. Physical Anti-Tamper Measures
What it does: Detects and responds to physical attacks (e.g., probing, decapping).
Techniques:
- Tamper detection circuits: Wipe keys if the enclosure is opened.
- Active shielding: Mesh layers detect drilling/cutting.
- Temperature/voltage sensors: Shutdown if under attack.
Example FPGAs:
- Xilinx Spartan-6 (tamper-resistant features).
- Microsemi (Microchip) SmartFusion2 (anti-tamper IP).
4. Obfuscation & Logic Locking
What it does: Makes reverse engineering harder.
Methods:
- Logic encryption: Insert "key-gated" logic blocks that only work with a secret key.
- Camouflaged cells: Hide true logic functions.
- Dummy routes: Add fake connections to confuse attackers.
Limitations:
Not foolproof against advanced attacks (e.g., SAT attacks on logic locking).
5. Secure Key Storage
What it does: Protects encryption/authentication keys.
Options:
- Battery-backed RAM (BBRAM): Volatile, but secure if power is cut.
- eFUSE (one-time programmable): Permanent but irreversible.
- Hardware Security Modules (HSMs): External secure storage (e.g., TPM, Smartcard).
- PUF (Physical Unclonable Function): Generates unique keys from silicon variations.
6. JTAG & Debug Port Lockdown
What it does: Prevents unauthorized access via debug interfaces.
Methods:
- Disable JTAG after programming: Fuse-based locking (Xilinx, Intel).
- Password-protect JTAG: Requires auth to access.
- Use secure debug protocols: Arm’s CoreSight with authentication.
7. Dynamic Partial Reconfiguration (DPR) Security
What it does: Secures designs that use runtime reconfiguration.
Methods:
- Encrypt partial bitstreams.
- Authenticate updates before loading.
8. Secure Update Mechanisms
What it does: Prevents malicious firmware updates.
Methods:
- Signed updates: Only accept bitstreams with valid signatures.
- Rollback protection: Block downgrade attacks.
9. Side-Channel Attack Mitigation
What it does: Prevents key extraction via power/EM analysis.
Methods:
- Masking: Hide crypto operations with random noise.
- Constant-time algorithms: Avoid key-dependent timing leaks.
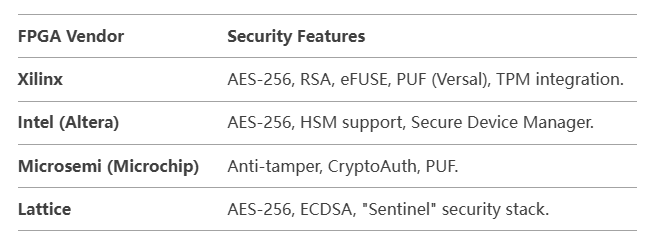
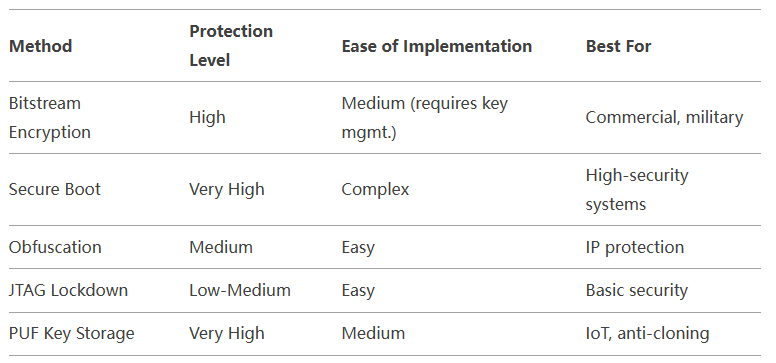
10. Vendor-Specific Security Features
Comparison of Security Methods
Best Practices for FPGA Security
- Always encrypt bitstreams (AES-256 + authentication).
- Disable unused interfaces (JTAG, USB-UART).
- Use secure key storage (eFUSE, HSM, or PUF).
- Regularly update firmware with signed patches.
- Audit for side-channel leaks in crypto designs.
Conclusion
FPGA security requires a layered approach—combining encryption, authentication, tamper resistance, and secure key storage. For high-risk applications (e.g., defense), Xilinx Versal or Intel Stratix 10 with secure boot + HSMs are recommended. For cost-sensitive designs, AES-256 + JTAG lockdown is a minimum.








































































































































































![[The AI Show Episode 143]: ChatGPT Revenue Surge, New AGI Timelines, Amazon’s AI Agent, Claude for Education, Model Context Protocol & LLMs Pass the Turing Test](https://www.marketingaiinstitute.com/hubfs/ep%20143%20cover.png)
































































































































![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)








































































































.jpg?#)































_ArtemisDiana_Alamy.jpg?#)


 (1).webp?#)






































































-xl.jpg)












![Yes, the Gemini icon is now bigger and brighter on Android [U]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/02/Gemini-on-Galaxy-S25.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)









![Apple Rushes Five Planes of iPhones to US Ahead of New Tariffs [Report]](https://www.iclarified.com/images/news/96967/96967/96967-640.jpg)
![Apple Vision Pro 2 Allegedly in Production Ahead of 2025 Launch [Rumor]](https://www.iclarified.com/images/news/96965/96965/96965-640.jpg)