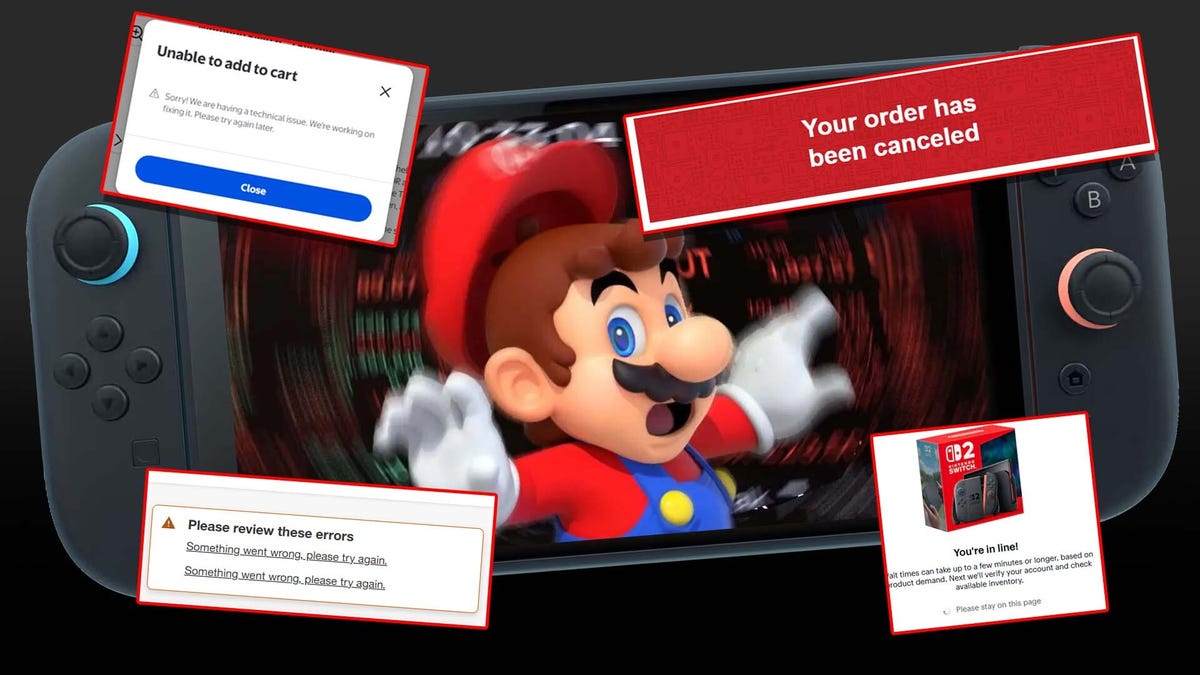
Title: "UID 2556 to Rescue: How Linux Saved Our Group Project"
Intro: The Sysadmin's All-Nighter "3 AM in the computer lab. Our project deadline loomed while error messages mocked us. As the only Cloud Whistler 'student in a team of biologists and artists, I became the accidental sysadmin.Here's how UID 2556 and some Linux magic saved our grades..." Task-1. The Mysterious User Jean Professor's email: "All research accounts must use UID 2556 for security audits." Me (typing furiously): Verification: Task-2. The Group Permission Wars Susan (Biology): "Why can't Harry and I share files?" Harry (Business): "Why is Natasha locked out?" Natasha (Art): "Why does my terminal say 'This account is not available'?" "Susan got her precious /home/susan directory. Harry stopped rm -rf'ing things. Natasha... well, she used the lab Macs instead." Task-3. The "Lost in the Dictionary" Crisis Harry (Business major): "The professor wants every occurrence of 'strato' documented! There are 200,000 words in this file!" Me (sipping energy drinks): "Linux eats dictionary searches for breakfast." Breakdown: grep '^strato': Finds lines starting with "strato" grep -v '^$': Removes blank lines redirects to /root/lines.txt "Bonus: We added ^ to avoid matches like 'substrato' (Spanish for substrate). Harry was impressed." Task-4. Fine-Grained File Access Control Natasha (Art major): 'I need to edit the config!' Susan (Biology): 'But she keeps breaking things!' Me: 'ACLs to the rescue!'" ACL Magic: Breaks down to: Owner (root): read/write Group (root): read-only Others: read-only Task-5. Securing the Shared Directory Harry (Business major): "Why can't I access our project files anymore?" Me:"Because you kept leaking data to competitors. Time for Linux permissions!" - root:sysmgrs = root owns it, sysmgrs group controls access This ensures: Only root and sysmgrs members can access All new files inherit sysmgrs group Proper audit trail maintained Epilogue: "How We Became (Accidental) Linux Sysadmins" "At 7:59 AM, our project submitted, I collapsed onto a keyboard-shaped indent in the lab table. The receipts of our battle? UID 2556 (jean) – The professor’s arbitrary security compliance, conquered. /netdir lockdown – Harry’s ‘creative’ file-sharing habits, neutralized Natasha’s ACLs – Artistic chaos, contained (mostly) Susan’s rescued data – 200 pages of biology research, restored from /tmp/notes_final_final2.txt The professor gave us an A+ and asked, ‘Did you cheat with ChatGPT?’ We grinned. ‘No, just grep, chmod, and 17 energy drinks.’ #30DaysLinuxChallenge #CloudWhisler DevOps #Linux #RHCSA #Opensource #AWS #CloudComputing Catch out by My LinkedIn profile https://www.linkedin.com/in/rajpreet-gill-4569b4161/
Intro: The Sysadmin's All-Nighter
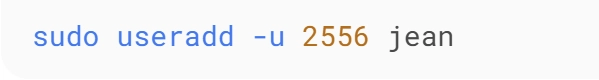
"3 AM in the computer lab. Our project deadline loomed while error messages mocked us. As the only Cloud Whistler 'student in a team of biologists and artists, I became the accidental sysadmin.Here's how UID 2556 and some Linux magic saved our grades..."
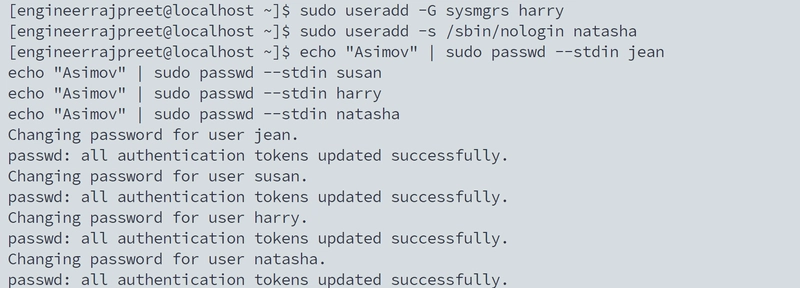
Task-1. The Mysterious User Jean
Professor's email: "All research accounts must use UID 2556 for security audits."
Me (typing furiously):
Verification:
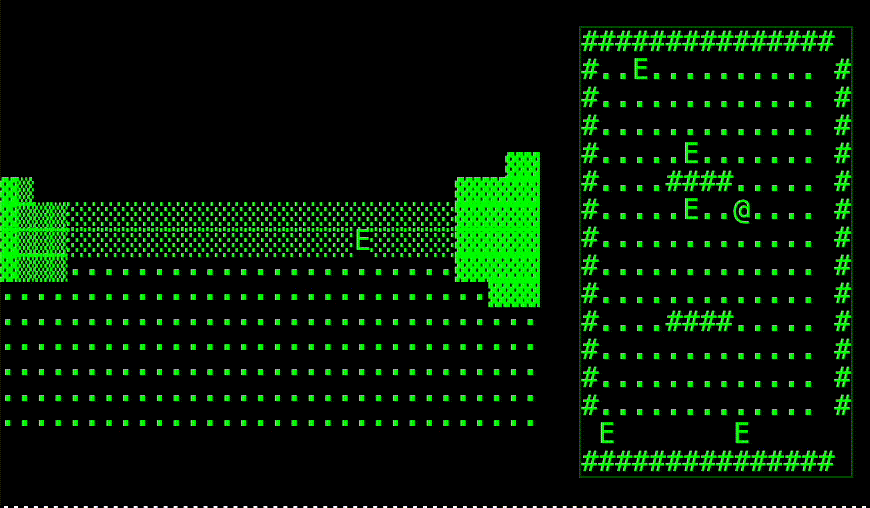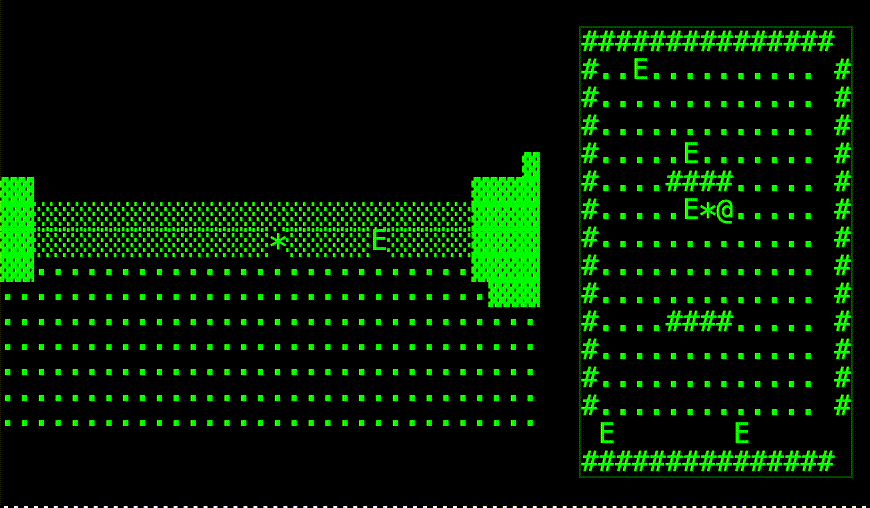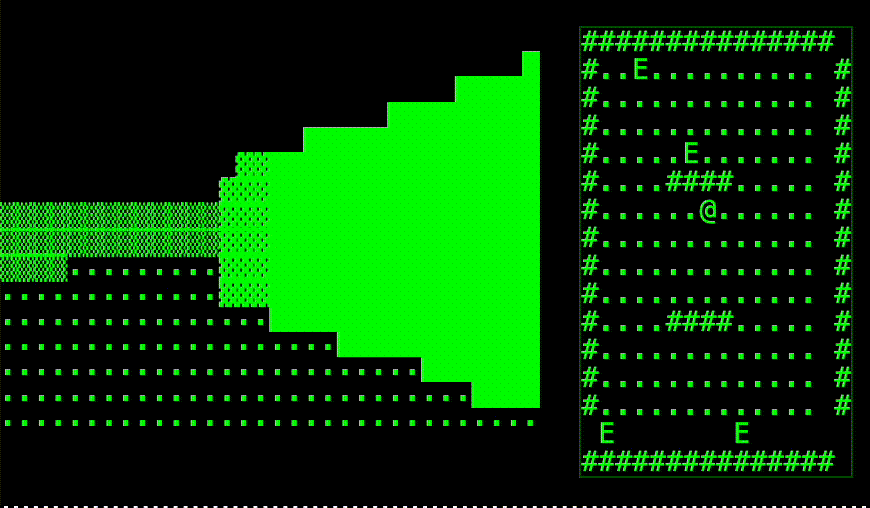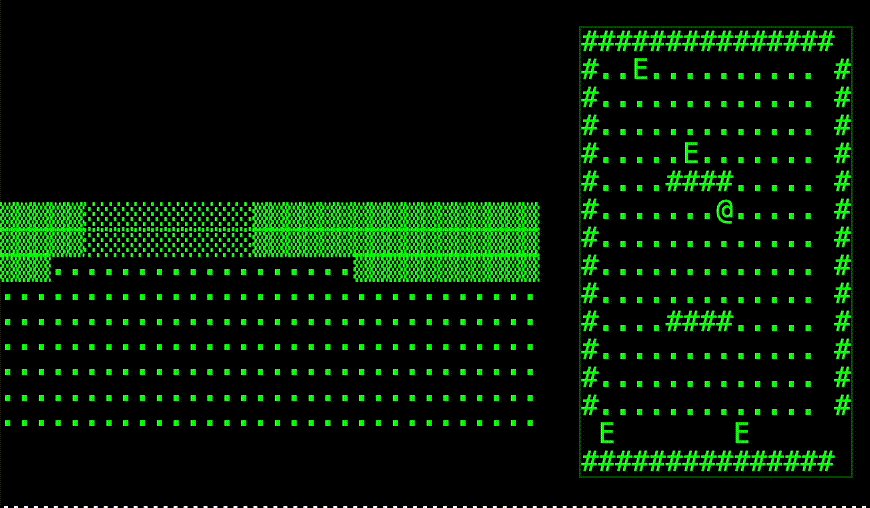
Task-2. The Group Permission Wars
Susan (Biology): "Why can't Harry and I share files?"
Harry (Business): "Why is Natasha locked out?"
Natasha (Art): "Why does my terminal say 'This account is not available'?"
"Susan got her precious /home/susan directory. Harry stopped rm -rf'ing things. Natasha... well, she used the lab Macs instead."
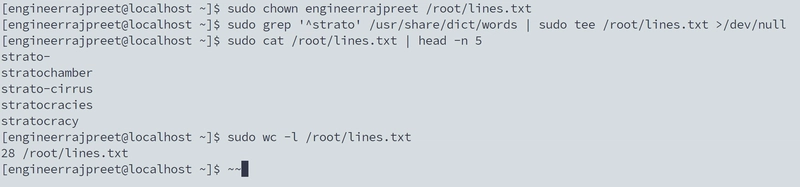
Task-3. The "Lost in the Dictionary" Crisis
Harry (Business major): "The professor wants every occurrence of 'strato' documented! There are 200,000 words in this file!"
Me (sipping energy drinks): "Linux eats dictionary searches for breakfast."
Breakdown:
grep '^strato': Finds lines starting with "strato"
grep -v '^$': Removes blank lines
redirects to /root/lines.txt
"Bonus: We added ^ to avoid matches like 'substrato' (Spanish for substrate). Harry was impressed."
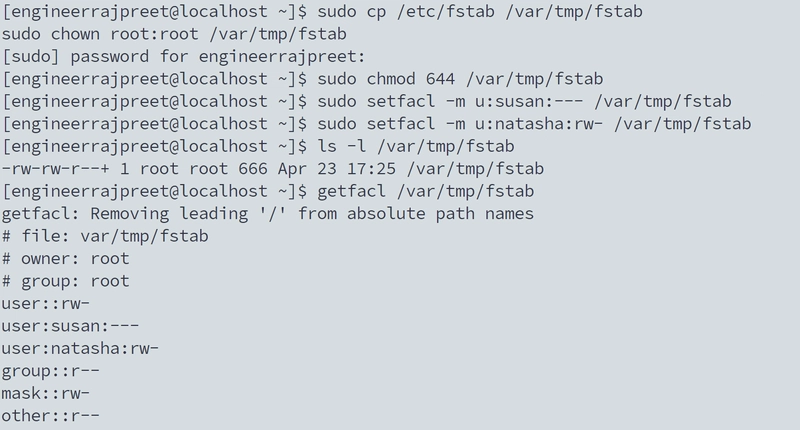
Task-4. Fine-Grained File Access Control
Natasha (Art major): 'I need to edit the config!'
Susan (Biology): 'But she keeps breaking things!'
Me: 'ACLs to the rescue!'"
ACL Magic:
Breaks down to:
Owner (root): read/write
Group (root): read-only
Others: read-only
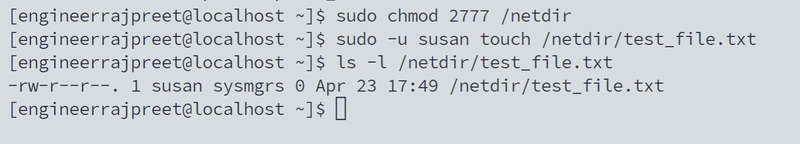
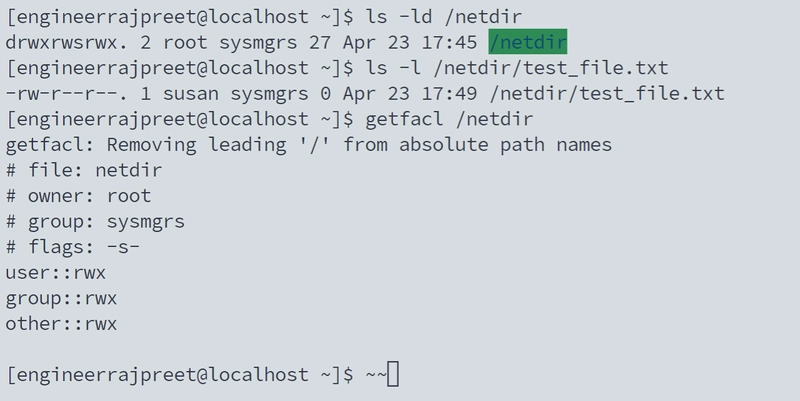
Task-5. Securing the Shared Directory
Harry (Business major): "Why can't I access our project files anymore?"
Me:"Because you kept leaking data to competitors. Time for Linux permissions!"
- root:sysmgrs = root owns it, sysmgrs group controls access
This ensures:
Only root and sysmgrs members can access
All new files inherit sysmgrs group
Proper audit trail maintained
Epilogue: "How We Became (Accidental) Linux Sysadmins"
"At 7:59 AM, our project submitted, I collapsed onto a keyboard-shaped indent in the lab table. The receipts of our battle?
UID 2556 (jean) – The professor’s arbitrary security compliance, conquered.
/netdir lockdown – Harry’s ‘creative’ file-sharing habits, neutralized
Natasha’s ACLs – Artistic chaos, contained (mostly)
Susan’s rescued data – 200 pages of biology research, restored from /tmp/notes_final_final2.txt
The professor gave us an A+ and asked, ‘Did you cheat with ChatGPT?’ We grinned. ‘No, just grep, chmod, and 17 energy drinks.’
#30DaysLinuxChallenge #CloudWhisler
DevOps #Linux #RHCSA #Opensource #AWS #CloudComputing
Catch out by My LinkedIn profile
https://www.linkedin.com/in/rajpreet-gill-4569b4161/






































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)

























































































































































![Is This Programming Paradigm New? [closed]](https://miro.medium.com/v2/resize:fit:1200/format:webp/1*nKR2930riHA4VC7dLwIuxA.gif)
















































































(1).jpg?#)
.jpg?#)




-Classic-Nintendo-GameCube-games-are-coming-to-Nintendo-Switch-2!-00-00-13.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)

























_Olekcii_Mach_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)







































































































![M4 MacBook Air Drops to New All-Time Low of $912 [Deal]](https://www.iclarified.com/images/news/97108/97108/97108-640.jpg)
![New iPhone 17 Dummy Models Surface in Black and White [Images]](https://www.iclarified.com/images/news/97106/97106/97106-640.jpg)