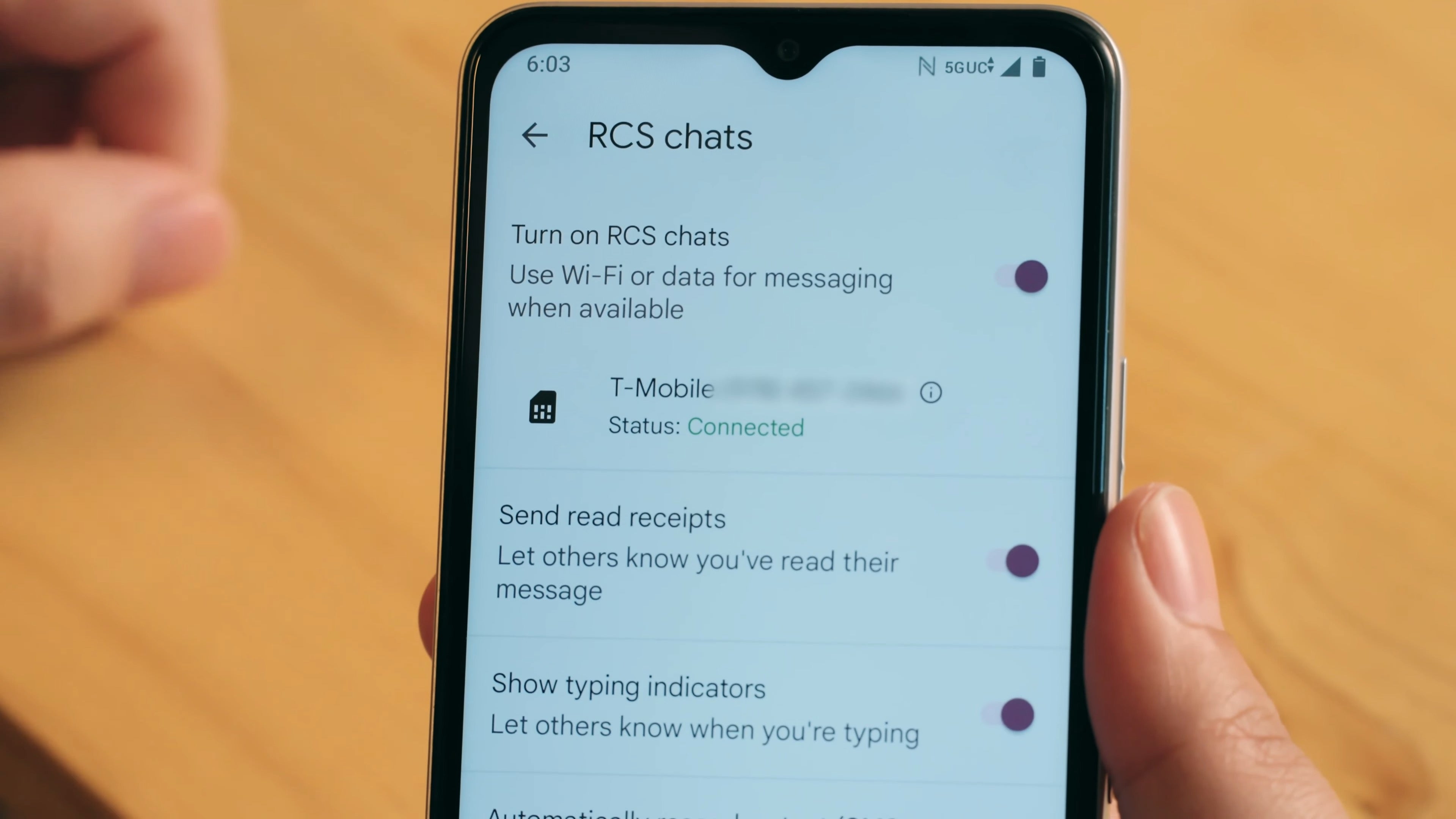
She Shared Her Screen… and Her AWS Secret (Yes, she's a FANG)
Yesterday, on a Zoom meeting, I watched a senior engineer from a company you'd definitely recognize (FANG) accidentally leaked her AWS credentials while sharing her screen. No one on the call said anything. She needed help with debugging a tiny bug. The screen flicked over to her browser, and specifically - AWS console — and right there, in plain text, was a long, juicy AWS secret (❗️). The kind of secrets you hope never leaves your local machine. It lasted maybe 3 seconds, but the meeting was recorded. We’ve normalized zoom/google/whatever meetings and screen sharing, but we haven’t adapted our tools — or habits — to protect sensitive data in real-time. This Happens Way More Than We Think As developers, we move fast. Our tools are always open: Dashboards full of internal data .env files Devtools showing API responses PIIs all over our browser Debug consoles Secrets don’t live in just your code — they’re in your browser, your extensions, your tabs, your terminal. When you screen share, you're not just sharing your work — you're potentially leaking everything under the hood. The Cost of a 3-Second Mistake Screens are recorded. Calls are uploaded. Interns and clients and strangers see your screen. That one token? Maybe it had admin permissions. Maybe it let someone spin up $50k in EC2s. Maybe it wasn’t rotated fast enough. I’ve seen this happen multiple times in the last year. I’ve also… done it myself. So I Built a Fix (Entropy Demo screenshot) This problem kept nagging at me, so I built something to solve it. It’s called Entropy — a Chrome extension that detects and redacts secrets and PII in real time, right inside your browser. ✅ Detects API keys, AWS secrets, emails, tokens, etc. ✅ Redacts data before it shows up on screen ✅ Customizable rules ✅ Fast, private, local Whether you're on a sales call, a Twitch stream, or a demo for your CTO — you shouldn't have to worry about what's lurking in your devtools. Let's Fix This for Everyone If you’ve ever leaked a secret — or almost did — you’re not alone. I’d love to hear your stories, feedback, or ideas. Would this be useful in your team? Try Entropy and let me know what you think. Entropysec.io

Yesterday, on a Zoom meeting, I watched a senior engineer from a company you'd definitely recognize (FANG) accidentally leaked her AWS credentials while sharing her screen.
No one on the call said anything.
She needed help with debugging a tiny bug.
The screen flicked over to her browser, and specifically - AWS console — and right there, in plain text, was a long, juicy AWS secret (❗️).
The kind of secrets you hope never leaves your local machine. It lasted maybe 3 seconds, but the meeting was recorded.
We’ve normalized zoom/google/whatever meetings and screen sharing, but we haven’t adapted our tools — or habits — to protect sensitive data in real-time.
This Happens Way More Than We Think
As developers, we move fast. Our tools are always open:
- Dashboards full of internal data
-
.envfiles - Devtools showing API responses
- PIIs all over our browser
- Debug consoles
Secrets don’t live in just your code — they’re in your browser, your extensions, your tabs, your terminal. When you screen share, you're not just sharing your work — you're potentially leaking everything under the hood.
The Cost of a 3-Second Mistake
Screens are recorded. Calls are uploaded. Interns and clients and strangers see your screen.
That one token? Maybe it had admin permissions. Maybe it let someone spin up $50k in EC2s. Maybe it wasn’t rotated fast enough.
I’ve seen this happen multiple times in the last year. I’ve also… done it myself.
So I Built a Fix
This problem kept nagging at me, so I built something to solve it.
It’s called Entropy — a Chrome extension that detects and redacts secrets and PII in real time, right inside your browser.
- ✅ Detects API keys, AWS secrets, emails, tokens, etc.
- ✅ Redacts data before it shows up on screen
- ✅ Customizable rules
- ✅ Fast, private, local
Whether you're on a sales call, a Twitch stream, or a demo for your CTO — you shouldn't have to worry about what's lurking in your devtools.
Let's Fix This for Everyone
If you’ve ever leaked a secret — or almost did — you’re not alone.
I’d love to hear your stories, feedback, or ideas.
Would this be useful in your team?
Try Entropy and let me know what you think.
Entropysec.io












































































































































































![[The AI Show Episode 146]: Rise of “AI-First” Companies, AI Job Disruption, GPT-4o Update Gets Rolled Back, How Big Consulting Firms Use AI, and Meta AI App](https://www.marketingaiinstitute.com/hubfs/ep%20146%20cover.png)


























































































































![[FREE EBOOKS] Modern Generative AI with ChatGPT and OpenAI Models, Offensive Security Using Python & Four More Best Selling Titles](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)




![How to make Developer Friends When You Don't Live in Silicon Valley, with Iraqi Engineer Code;Life [Podcast #172]](https://cdn.hashnode.com/res/hashnode/image/upload/v1747360508340/f07040cd-3eeb-443c-b4fb-370f6a4a14da.png?#)









































































































































![[Virtual Event] Strategic Security for the Modern Enterprise](https://eu-images.contentstack.com/v3/assets/blt6d90778a997de1cd/blt55e4e7e277520090/653a745a0e92cc040a3e9d7e/Dark_Reading_Logo_VirtualEvent_4C.png?width=1280&auto=webp&quality=80&disable=upscale#)














































































-xl-(1)-xl-xl.jpg)









![Upgrade your CarPlay experience in 2025 with Ottocast NanoAI and Mini Wireless [20% off]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/05/nano-ai-banner-pc.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)














![iPhone 17 Air Could Get a Boost From TDK's New Silicon Battery Tech [Report]](https://www.iclarified.com/images/news/97344/97344/97344-640.jpg)
![Vision Pro Owners Say They Regret $3,500 Purchase [WSJ]](https://www.iclarified.com/images/news/97347/97347/97347-640.jpg)
![Apple Showcases 'Magnifier on Mac' and 'Music Haptics' Accessibility Features [Video]](https://www.iclarified.com/images/news/97343/97343/97343-640.jpg)
![Sony WH-1000XM6 Unveiled With Smarter Noise Canceling and Studio-Tuned Sound [Video]](https://www.iclarified.com/images/news/97341/97341/97341-640.jpg)