Security Best Practices for Python Smart Contracts on Xian
Introduction Security is a fundamental aspect of smart contract development. Unlike traditional applications, blockchain-based contracts are immutable once deployed, making it crucial to write secure code from the outset. Xian allows developers to write smart contracts in Python, but this ease of development also comes with potential security risks. In this guide, we’ll cover essential security best practices to help you write robust and attack-resistant Xian smart contracts. 1. Input Validation & Sanitization User input is a major attack vector in smart contracts. Always validate inputs to prevent unexpected behaviors and security vulnerabilities. Example: balances = Hash(default_value=0) @export def transfer(receiver: str, amount: int): assert amount > 0, "Invalid amount" assert balances[ctx.caller] >= amount, 'Not enough coins to send!' Why? Ensures only positive values are processed in financial transactions. Requires the user to have enough balance. 2. Use Access Control & Permissions Unauthorized access to critical contract functions can lead to catastrophic failures. Implement access control mechanisms to restrict who can call sensitive functions. Example: owner = Variable() @construct def initialize(): owner.set(ctx.caller) @export def privileged_function(): assert ctx.caller == owner.get(), "Unauthorized access" # Perform sensitive action Why? Prevents non-owners from calling privileged functions. Uses ctx.caller to verify the identity of the function caller. 3. Prevent Integer Overflows & Underflows In Python, integers are arbitrary-precision, but it’s still good practice to set explicit boundaries to prevent unexpected behaviors. Example: MAX_SUPPLY = 1_000_000 @export def mint(to: str, amount: int): assert amount > 0, "Amount must be positive" assert state['supply'] + amount = amount, "Insufficient balance" # Effects - Deduct the amount first before making any external call state['balances'][ctx.caller] -= amount state['balances'][to] += amount # Interactions - External function call happens *last* to avoid reentrancy risk external_contract.call_some_function() # Reset the lock reentrancy_lock.set(False) Why? Prevents an attacker from re-entering the function before the previous execution completes. Follows the Checks-Effects-Interactions pattern to update state before making external calls. Ensures safe execution even if an external contract attempts to re-enter. 6. Regularly Audit Your Smart Contracts Before deploying a contract, conduct thorough testing and audits to catch vulnerabilities early. Steps to Audit: Static Analysis: Use linting tools to detect code issues. Automated Tests: Write unit tests covering all possible contract behaviors. Peer Reviews: Have other developers review your contract code. Bug Bounties: Encourage security researchers to find vulnerabilities. Conclusion Writing secure smart contracts on Xian requires careful consideration of access controls, input validation, and attack prevention. By following these best practices, you can protect your contracts from common vulnerabilities and ensure a safer blockchain ecosystem.
Introduction
Security is a fundamental aspect of smart contract development. Unlike traditional applications, blockchain-based contracts are immutable once deployed, making it crucial to write secure code from the outset.
Xian allows developers to write smart contracts in Python, but this ease of development also comes with potential security risks. In this guide, we’ll cover essential security best practices to help you write robust and attack-resistant Xian smart contracts.
1. Input Validation & Sanitization
User input is a major attack vector in smart contracts. Always validate inputs to prevent unexpected behaviors and security vulnerabilities.
Example:
balances = Hash(default_value=0)
@export
def transfer(receiver: str, amount: int):
assert amount > 0, "Invalid amount"
assert balances[ctx.caller] >= amount, 'Not enough coins to send!'
Why?
- Ensures only positive values are processed in financial transactions.
- Requires the user to have enough balance.
2. Use Access Control & Permissions
Unauthorized access to critical contract functions can lead to catastrophic failures. Implement access control mechanisms to restrict who can call sensitive functions.
Example:
owner = Variable()
@construct
def initialize():
owner.set(ctx.caller)
@export
def privileged_function():
assert ctx.caller == owner.get(), "Unauthorized access"
# Perform sensitive action
Why?
- Prevents non-owners from calling privileged functions.
- Uses
ctx.callerto verify the identity of the function caller.
3. Prevent Integer Overflows & Underflows
In Python, integers are arbitrary-precision, but it’s still good practice to set explicit boundaries to prevent unexpected behaviors.
Example:
MAX_SUPPLY = 1_000_000
@export
def mint(to: str, amount: int):
assert amount > 0, "Amount must be positive"
assert state['supply'] + amount <= MAX_SUPPLY, "Exceeds maximum supply"
state['supply'] += amount
state['balances'][to] += amount
Why?
- Prevents minting more tokens than allowed.
- Ensures values remain within the intended range.
4. Safe Handling of Decimal Operations in Xian Smart Contracts
In the Contracting language, floating-point numbers are automatically converted to ContractingDecimal. This ensures safe calculations within predefined precision limits, avoiding rounding errors and excessive values. The maximum limit for the decimal type is 1e29, and values exceeding this limit are truncated.
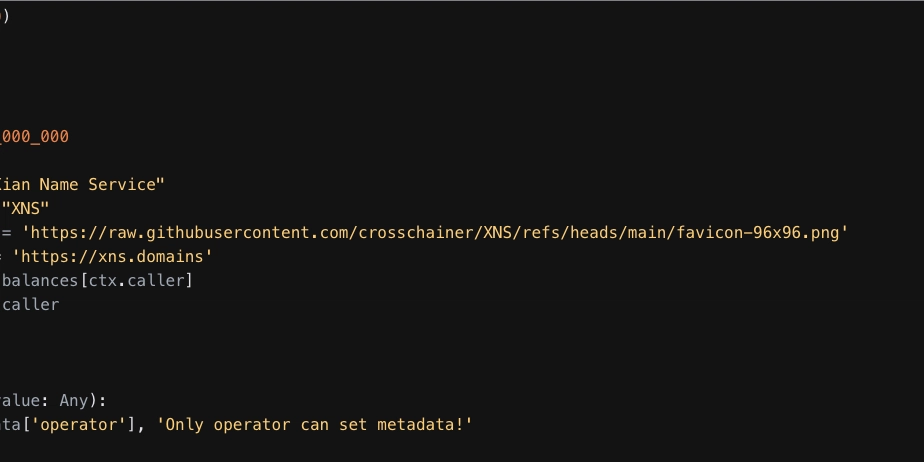
5. Avoid Reentrancy Attacks
Reentrancy occurs when a contract makes an external call before updating its state, allowing an attacker to re-enter and manipulate the contract’s logic. This can lead to unintended execution and fund theft.
Example:
reentrancy_lock = Variable()
@construct
def seed():
reentrancy_lock.set(False)
@export
def withdraw(amount: float, to: str):
assert not reentrancy_lock.get(), "Reentrancy detected"
reentrancy_lock.set(True)
# Checks - Ensure user has enough balance
assert state['balances'][ctx.caller] >= amount, "Insufficient balance"
# Effects - Deduct the amount first before making any external call
state['balances'][ctx.caller] -= amount
state['balances'][to] += amount
# Interactions - External function call happens *last* to avoid reentrancy risk
external_contract.call_some_function()
# Reset the lock
reentrancy_lock.set(False)
Why?
- Prevents an attacker from re-entering the function before the previous execution completes.
- Follows the Checks-Effects-Interactions pattern to update state before making external calls.
- Ensures safe execution even if an external contract attempts to re-enter.
6. Regularly Audit Your Smart Contracts
Before deploying a contract, conduct thorough testing and audits to catch vulnerabilities early.
Steps to Audit:
- Static Analysis: Use linting tools to detect code issues.
- Automated Tests: Write unit tests covering all possible contract behaviors.
- Peer Reviews: Have other developers review your contract code.
- Bug Bounties: Encourage security researchers to find vulnerabilities.
Conclusion
Writing secure smart contracts on Xian requires careful consideration of access controls, input validation, and attack prevention. By following these best practices, you can protect your contracts from common vulnerabilities and ensure a safer blockchain ecosystem.









































































































































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)


























































































































![[FREE EBOOKS] The Kubernetes Bible, The Ultimate Linux Shell Scripting Guide & Four More Best Selling Titles](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)



![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)






































































































.png?#)




.jpg?#)
































_Christophe_Coat_Alamy.jpg?#)







































































































![Rapidus in Talks With Apple as It Accelerates Toward 2nm Chip Production [Report]](https://www.iclarified.com/images/news/96937/96937/96937-640.jpg)