One SQL Query That Could Destroy Your Entire Database (And How Hackers Use It)
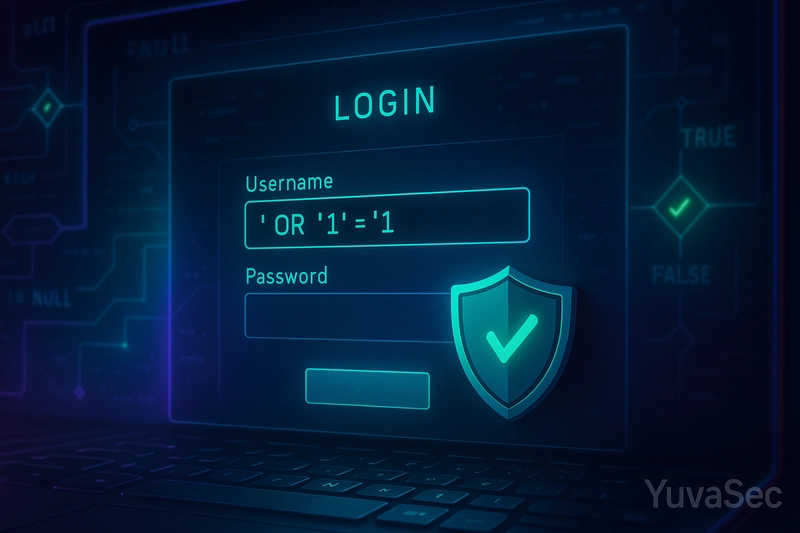
Introduction Imagine logging into your bank account only to discover that someone else got in without your password. Scary, right? That’s not a movie plot—it’s often the result of an SQL Injection attack, one of the most dangerous yet common threats in cybersecurity today. Here, we will embark on an exploration of the construction and use of malicious SQL queries by malicious attackers to bypass logins, retrieve confidential data, delete data or even run system commands. With the rise of AI-driven automation and open-source utilities, the development of such attacks has become faster, easier, and more crippling making it more critical than ever for developers, tech enthusiasts, and security professionals to understand the basic methods at play. ⚠️ Disclaimer: This article is for educational and ethical hacking purposes only. Always have permission before testing any system. Bypassing Login Mechanisms How Attackers Log In Without a Password Many web apps rely on vulnerable login scripts like: SELECT * FROM users WHERE username = '$input' AND password = '$pass'; If an attacker inputs: Username: ' OR '1'='1 Password: anything The query becomes: SELECT * FROM users WHERE username = '' OR '1'='1' AND password = 'anything'; This always returns TRUE, allowing the attacker to bypass authentication. Why it works: SQL interprets '1'='1' as a valid condition Password checks are effectively ignored ⚠️ Why Is This Dangerous? It bypasses login mechanisms. It can be used to extract data, modify databases, or escalate privileges if chained with other exploits. It highlights the need for input sanitization and parameterized queries.
Introduction
Imagine logging into your bank account only to discover that someone else got in without your password. Scary, right? That’s not a movie plot—it’s often the result of an SQL Injection attack, one of the most dangerous yet common threats in cybersecurity today.
Here, we will embark on an exploration of the construction and use of malicious SQL queries by malicious attackers to bypass logins, retrieve confidential data, delete data or even run system commands.
With the rise of AI-driven automation and open-source utilities, the development of such attacks has become faster, easier, and more crippling making it more critical than ever for developers, tech enthusiasts, and security professionals to understand the basic methods at play.
⚠️ Disclaimer: This article is for educational and ethical hacking purposes only. Always have permission before testing any system.
Bypassing Login Mechanisms
How Attackers Log In Without a Password
Many web apps rely on vulnerable login scripts like:
SELECT * FROM users WHERE username = '$input' AND password = '$pass';
If an attacker inputs:
Username: ' OR '1'='1
Password: anything
The query becomes:
SELECT * FROM users WHERE username = '' OR '1'='1' AND password = 'anything';
This always returns TRUE, allowing the attacker to bypass authentication.
Why it works:
SQL interprets '1'='1' as a valid condition
Password checks are effectively ignored
⚠️ Why Is This Dangerous?
It bypasses login mechanisms.
It can be used to extract data, modify databases, or escalate privileges if chained with other exploits.
It highlights the need for input sanitization and parameterized queries.







































































































































































![[The AI Show Episode 143]: ChatGPT Revenue Surge, New AGI Timelines, Amazon’s AI Agent, Claude for Education, Model Context Protocol & LLMs Pass the Turing Test](https://www.marketingaiinstitute.com/hubfs/ep%20143%20cover.png)





























































































































![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)








































































































.jpg?#)
































_ArtemisDiana_Alamy.jpg?#)


 (1).webp?#)




































































-xl.jpg)











![Yes, the Gemini icon is now bigger and brighter on Android [U]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/02/Gemini-on-Galaxy-S25.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)










![Apple Rushes Five Planes of iPhones to US Ahead of New Tariffs [Report]](https://www.iclarified.com/images/news/96967/96967/96967-640.jpg)
![Apple Vision Pro 2 Allegedly in Production Ahead of 2025 Launch [Rumor]](https://www.iclarified.com/images/news/96965/96965/96965-640.jpg)