LetsDefend: SOC335 - CVE-2024-49138 Exploitation Detected
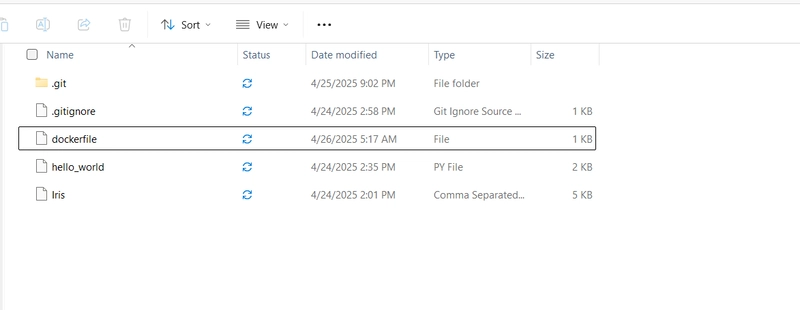
Incident Case Report Case Title: CVE-2024-49138 Exploitation via svohost.exe and Remote RDP Access Case ID: SOC-IR-2025-0122-313 Date/Time of Detection: January 22, 2025, 02:37 AM (UTC) Analyst Assigned: Security Analyst, SOC Team Severity Level: High Executive Summary On January 22, 2025, the SOC detected suspicious behavior on host Victor (IP: 172.16.17.207) at 02:37 AM via detection rule SOC335. A non-standard process, svohost.exe, was executed from an unusual path (C:\temp\service_installer), showing signs of exploiting CVE-2024-49138, a privilege escalation vulnerability. A successful RDP login from a malicious IP (185[.]107[.]56[.]141) confirmed the attacker had gained remote access. Detection Details Field Value Event ID 313 Rule Name SOC335 - CVE-2024-49138 Exploitation Detected Detection Time January 22, 2025, 02:37 AM Affected Hostname Victor File/Process Name svohost.exe File Path C:\temp\service_installer\svohost.exe Malicious IP 185.107.56.141 Command Line \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 Incident Narrative At 02:37 AM, an alert flagged svohost.exe for exhibiting behaviors consistent with CVE-2024-49138. The executable was spawned by powershell.exe, suggesting a fileless attack. The file’s unusual location and behavior indicated malicious intent. A successful RDP login from a known malicious IP shortly followed, confirming system compromise. Indicators of Compromise (IOCs) File Hash: b432dcf4a0f0b601b1d79848467137a5e25cab5a0b7b1224be9d3b6540122db9 Malicious IP: 185.107.56.141 CVE Exploited: CVE-2024-49138 Impact Assessment System Compromise: Confirmed via RDP access. Privilege Escalation: Likely, based on PowerShell and conhost.exe behavior. Persistence: Not confirmed. Scope: Single host (Victor). Recommendations Isolate Host: Prevent lateral movement. Revoke Credentials: Rotate LetsDefend user credentials. Block Malicious IP: At firewall level. Search for IOCs: Across environment. Collect Forensics: Memory and disk images of Victor. Long-Term Actions: Patch systems vulnerable to CVE-2024-49138. Implement MFA for RDP access and segment the network. Conclusion The attacker exploited CVE-2024-49138 for privilege escalation and gained remote access via RDP. Immediate containment and further investigation are essential for full remediation.
Incident Case Report
Case Title: CVE-2024-49138 Exploitation via svohost.exe and Remote RDP Access
Case ID: SOC-IR-2025-0122-313
Date/Time of Detection: January 22, 2025, 02:37 AM (UTC)
Analyst Assigned: Security Analyst, SOC Team
Severity Level: High
Executive Summary
On January 22, 2025, the SOC detected suspicious behavior on host Victor (IP: 172.16.17.207) at 02:37 AM via detection rule SOC335. A non-standard process, svohost.exe, was executed from an unusual path (C:\temp\service_installer), showing signs of exploiting CVE-2024-49138, a privilege escalation vulnerability. A successful RDP login from a malicious IP (185[.]107[.]56[.]141) confirmed the attacker had gained remote access.
Detection Details
| Field | Value |
|---|---|
| Event ID | 313 |
| Rule Name | SOC335 - CVE-2024-49138 Exploitation Detected |
| Detection Time | January 22, 2025, 02:37 AM |
| Affected Hostname | Victor |
| File/Process Name | svohost.exe |
| File Path | C:\temp\service_installer\svohost.exe |
| Malicious IP | 185.107.56.141 |
| Command Line | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 |
Incident Narrative
At 02:37 AM, an alert flagged svohost.exe for exhibiting behaviors consistent with CVE-2024-49138. The executable was spawned by powershell.exe, suggesting a fileless attack. The file’s unusual location and behavior indicated malicious intent. A successful RDP login from a known malicious IP shortly followed, confirming system compromise.
Indicators of Compromise (IOCs)
-
File Hash:
b432dcf4a0f0b601b1d79848467137a5e25cab5a0b7b1224be9d3b6540122db9 -
Malicious IP:
185.107.56.141 - CVE Exploited: CVE-2024-49138
Impact Assessment
- System Compromise: Confirmed via RDP access.
- Privilege Escalation: Likely, based on PowerShell and conhost.exe behavior.
- Persistence: Not confirmed.
-
Scope: Single host (
Victor).
Recommendations
- Isolate Host: Prevent lateral movement.
-
Revoke Credentials: Rotate
LetsDefenduser credentials. - Block Malicious IP: At firewall level.
- Search for IOCs: Across environment.
-
Collect Forensics: Memory and disk images of
Victor.
Long-Term Actions:
- Patch systems vulnerable to CVE-2024-49138.
- Implement MFA for RDP access and segment the network.
Conclusion
The attacker exploited CVE-2024-49138 for privilege escalation and gained remote access via RDP. Immediate containment and further investigation are essential for full remediation.








































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)

















































































































































































.jpg?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)





















































































_Olekcii_Mach_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)










































































































![Apple Drops New Immersive Adventure Episode for Vision Pro: 'Hill Climb' [Video]](https://www.iclarified.com/images/news/97133/97133/97133-640.jpg)

![Most iPhones Sold in the U.S. Will Be Made in India by 2026 [Report]](https://www.iclarified.com/images/news/97130/97130/97130-640.jpg)
![Apple to Shift Robotics Unit From AI Division to Hardware Engineering [Report]](https://www.iclarified.com/images/news/97128/97128/97128-640.jpg)