How to Prevent Web Cache Deception Attacks in Laravel: A Complete Guide
Introduction to Web Cache Deception Attack Web Cache Deception (WCD) is a vulnerability that occurs when sensitive data is improperly cached by web servers or reverse proxies, which leads to the exposure of private information. This attack typically exploits a misconfigured caching mechanism, causing private user data to be stored in a public cache. Laravel, being a popular PHP framework, is not immune to such attacks. In this blog post, we will explain how Web Cache Deception works, how to identify vulnerabilities in your Laravel app, and how to mitigate the risk with practical code examples. How Does Web Cache Deception Work? Web Cache Deception attacks target caching mechanisms such as Varnish, Nginx, or CDNs that improperly cache private resources. The attacker manipulates URLs or headers to trick the caching mechanism into caching sensitive content like user profiles, account details, or administrative pages. For instance, when a user visits a URL like: https://example.com/user/profile?id=123 A vulnerable caching system may cache the private content based on the id parameter. An attacker can access this cached content by visiting a similar URL, like: https://example.com/user/profile?id=999 If the cache isn’t properly configured, the attacker can view the private user data cached from the earlier request. Detecting Web Cache Deception in Laravel You can use the Website Vulnerability Scanner tool to identify web cache misconfigurations in your Laravel app. The tool helps you detect any caching issues that might lead to vulnerabilities like Web Cache Deception. Here’s how you can use it: Go to Pentest Testing Security Checker. Enter the URL of your Laravel app. Click on "Start Scan" to begin checking for caching vulnerabilities. Screenshot of the free tools webpage where you can access security assessment tools. This scan will generate a detailed report showing whether your application has any misconfigured caching mechanisms. Preventing Web Cache Deception in Laravel Now that we understand how Web Cache Deception works and how to detect it, let’s explore how to mitigate this risk in Laravel. 1. Avoid Caching Dynamic Content The most effective way to prevent WCD attacks is by avoiding caching sensitive dynamic content. In Laravel, you can prevent caching by modifying the Cache-Control headers in your HTTP response. Example Code: use Illuminate\Support\Facades\Response; public function showProfile($id) { $user = User::findOrFail($id); return Response::make(view('profile', compact('user'))) ->header('Cache-Control', 'no-store, no-cache, must-revalidate, proxy-revalidate'); } In this example, the Cache-Control header is set to no-store, ensuring that the response is not cached by browsers or proxies. 2. Cache Only Static Content You can cache only static resources such as images, JavaScript, and CSS files to improve your app’s performance. Laravel makes it easy to manage caching with Cache::put() and Cache::get(). Example Code: Cache::put('static_content_key', $content, now()->addMinutes(10)); In this code, we are explicitly caching non-sensitive data and ensuring dynamic content is not cached. Common Misconfigurations to Avoid When using caching mechanisms in Laravel, ensure the following: Use dynamic cache keys: Always include a session ID or user-specific data in the cache key. Example: Cache::put('user_' . auth()->id() . '_profile', $userData); Check cache TTL: Avoid setting too long of a TTL (Time to Live) for user-specific or sensitive data. Properly configure your reverse proxy: Ensure that your reverse proxy (like Nginx or Varnish) is not caching sensitive content. Using the Free Website Security Checker Tool To make sure your Laravel app is secure against Web Cache Deception attacks, you can always check your website’s security status using the Pentest Testing security checker. Here’s an example of a vulnerability assessment report generated by our tool to check Website Vulnerability after scanning a Laravel website: An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities. This report provides a detailed analysis, highlighting any caching issues or other vulnerabilities in your application. Conclusion Web Cache Deception is a serious vulnerability that can expose sensitive user data if left unaddressed. By following the prevention methods outlined in this post, you can safeguard your Laravel application and improve its security. Additionally, use the free Website Security Scanner tool to detect potential security flaws in your application. For more detailed security tips and coding examples, check out our blog at Pentest Testing Blog. By implementing these security measures, you can protect your app and pre

Introduction to Web Cache Deception Attack
Web Cache Deception (WCD) is a vulnerability that occurs when sensitive data is improperly cached by web servers or reverse proxies, which leads to the exposure of private information. This attack typically exploits a misconfigured caching mechanism, causing private user data to be stored in a public cache. Laravel, being a popular PHP framework, is not immune to such attacks.

In this blog post, we will explain how Web Cache Deception works, how to identify vulnerabilities in your Laravel app, and how to mitigate the risk with practical code examples.
How Does Web Cache Deception Work?
Web Cache Deception attacks target caching mechanisms such as Varnish, Nginx, or CDNs that improperly cache private resources. The attacker manipulates URLs or headers to trick the caching mechanism into caching sensitive content like user profiles, account details, or administrative pages.
For instance, when a user visits a URL like:
https://example.com/user/profile?id=123
A vulnerable caching system may cache the private content based on the id parameter. An attacker can access this cached content by visiting a similar URL, like:
https://example.com/user/profile?id=999
If the cache isn’t properly configured, the attacker can view the private user data cached from the earlier request.
Detecting Web Cache Deception in Laravel
You can use the Website Vulnerability Scanner tool to identify web cache misconfigurations in your Laravel app. The tool helps you detect any caching issues that might lead to vulnerabilities like Web Cache Deception.
Here’s how you can use it:
- Go to Pentest Testing Security Checker.
- Enter the URL of your Laravel app.
- Click on "Start Scan" to begin checking for caching vulnerabilities.
 Screenshot of the free tools webpage where you can access security assessment tools.
Screenshot of the free tools webpage where you can access security assessment tools.
This scan will generate a detailed report showing whether your application has any misconfigured caching mechanisms.
Preventing Web Cache Deception in Laravel
Now that we understand how Web Cache Deception works and how to detect it, let’s explore how to mitigate this risk in Laravel.
1. Avoid Caching Dynamic Content
The most effective way to prevent WCD attacks is by avoiding caching sensitive dynamic content. In Laravel, you can prevent caching by modifying the Cache-Control headers in your HTTP response.
Example Code:
use Illuminate\Support\Facades\Response;
public function showProfile($id)
{
$user = User::findOrFail($id);
return Response::make(view('profile', compact('user')))
->header('Cache-Control', 'no-store, no-cache, must-revalidate, proxy-revalidate');
}
In this example, the Cache-Control header is set to no-store, ensuring that the response is not cached by browsers or proxies.
2. Cache Only Static Content
You can cache only static resources such as images, JavaScript, and CSS files to improve your app’s performance. Laravel makes it easy to manage caching with Cache::put() and Cache::get().
Example Code:
Cache::put('static_content_key', $content, now()->addMinutes(10));
In this code, we are explicitly caching non-sensitive data and ensuring dynamic content is not cached.
Common Misconfigurations to Avoid
When using caching mechanisms in Laravel, ensure the following:
- Use dynamic cache keys: Always include a session ID or user-specific data in the cache key.
Example: Cache::put('user_' . auth()->id() . '_profile', $userData);
Check cache TTL: Avoid setting too long of a TTL (Time to Live) for user-specific or sensitive data.
Properly configure your reverse proxy: Ensure that your reverse proxy (like Nginx or Varnish) is not caching sensitive content.
Using the Free Website Security Checker Tool
To make sure your Laravel app is secure against Web Cache Deception attacks, you can always check your website’s security status using the Pentest Testing security checker.
Here’s an example of a vulnerability assessment report generated by our tool to check Website Vulnerability after scanning a Laravel website:
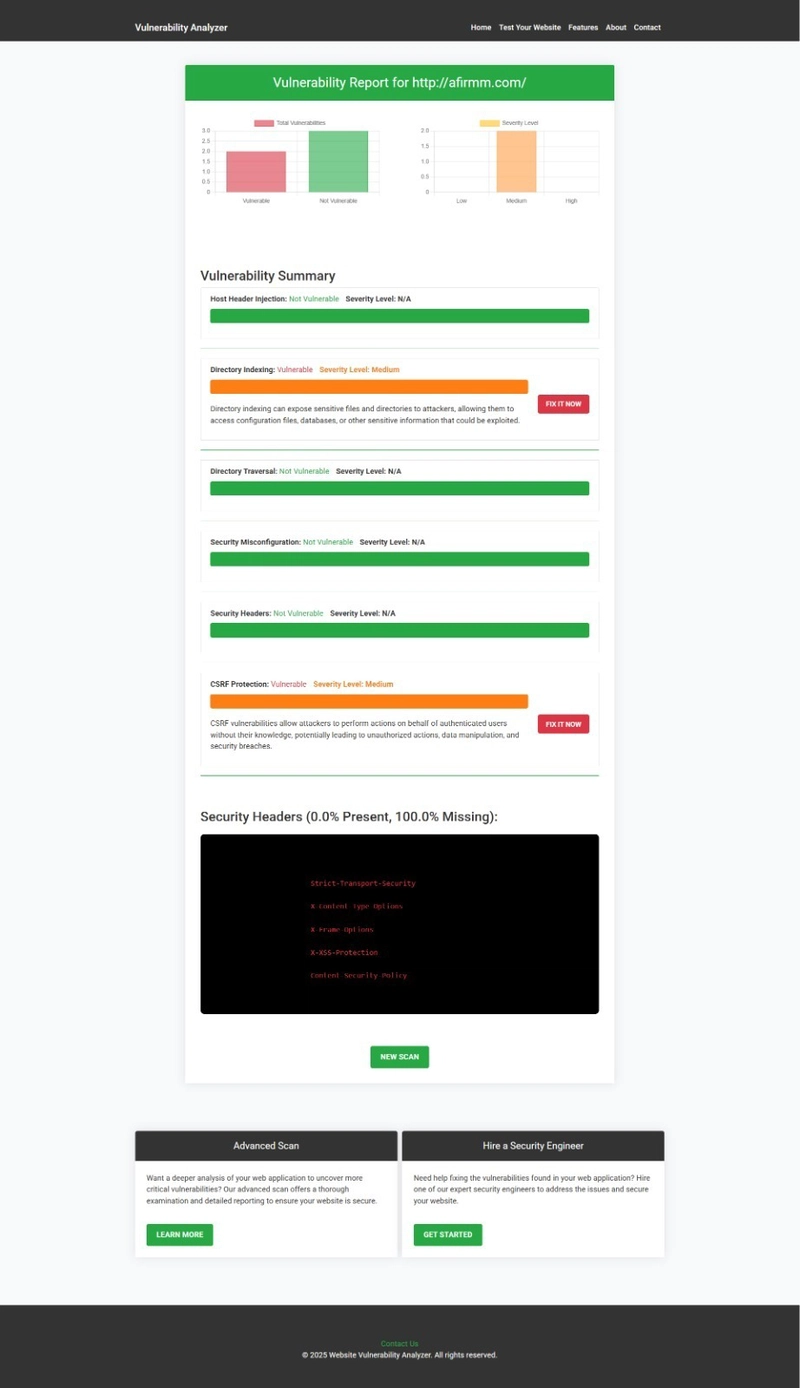 An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
This report provides a detailed analysis, highlighting any caching issues or other vulnerabilities in your application.
Conclusion
Web Cache Deception is a serious vulnerability that can expose sensitive user data if left unaddressed. By following the prevention methods outlined in this post, you can safeguard your Laravel application and improve its security. Additionally, use the free Website Security Scanner tool to detect potential security flaws in your application.
For more detailed security tips and coding examples, check out our blog at Pentest Testing Blog.
By implementing these security measures, you can protect your app and prevent Web Cache Deception attacks from compromising sensitive information.









































































































































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)


























































































































![[FREE EBOOKS] The Kubernetes Bible, The Ultimate Linux Shell Scripting Guide & Four More Best Selling Titles](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)



![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)






































































































.png?#)




.jpg?#)
































_Christophe_Coat_Alamy.jpg?#)







































































































![Rapidus in Talks With Apple as It Accelerates Toward 2nm Chip Production [Report]](https://www.iclarified.com/images/news/96937/96937/96937-640.jpg)