How To Implement JWT Authentication In Command-Line Applications
If you've ever built or used a command-line interface (CLI) tool, you know that authentication can be a tricky puzzle to solve. Getting this authentication flow right makes the difference between a tool people love using and one they constantly fight with. In this post, I'll explore what seems to be the most practical approach to CLI authentication: combining initial authentication (either through email/password or OAuth) with a dual-token system. While other methods certainly work for specific use cases, this approach appears to be a sweet spot for many applications.
If you've ever built or used a command-line interface (CLI) tool, you know that authentication can be a tricky puzzle to solve. Getting this authentication flow right makes the difference between a tool people love using and one they constantly fight with.
In this post, I'll explore what seems to be the most practical approach to CLI authentication: combining initial authentication (either through email/password or OAuth) with a dual-token system. While other methods certainly work for specific use cases, this approach appears to be a sweet spot for many applications.











































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)































































































































![[DEALS] Sterling Stock Picker: Lifetime Subscription (85% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)















































































































































_NicoElNino_Alamy.png?width=1280&auto=webp&quality=80&disable=upscale#)
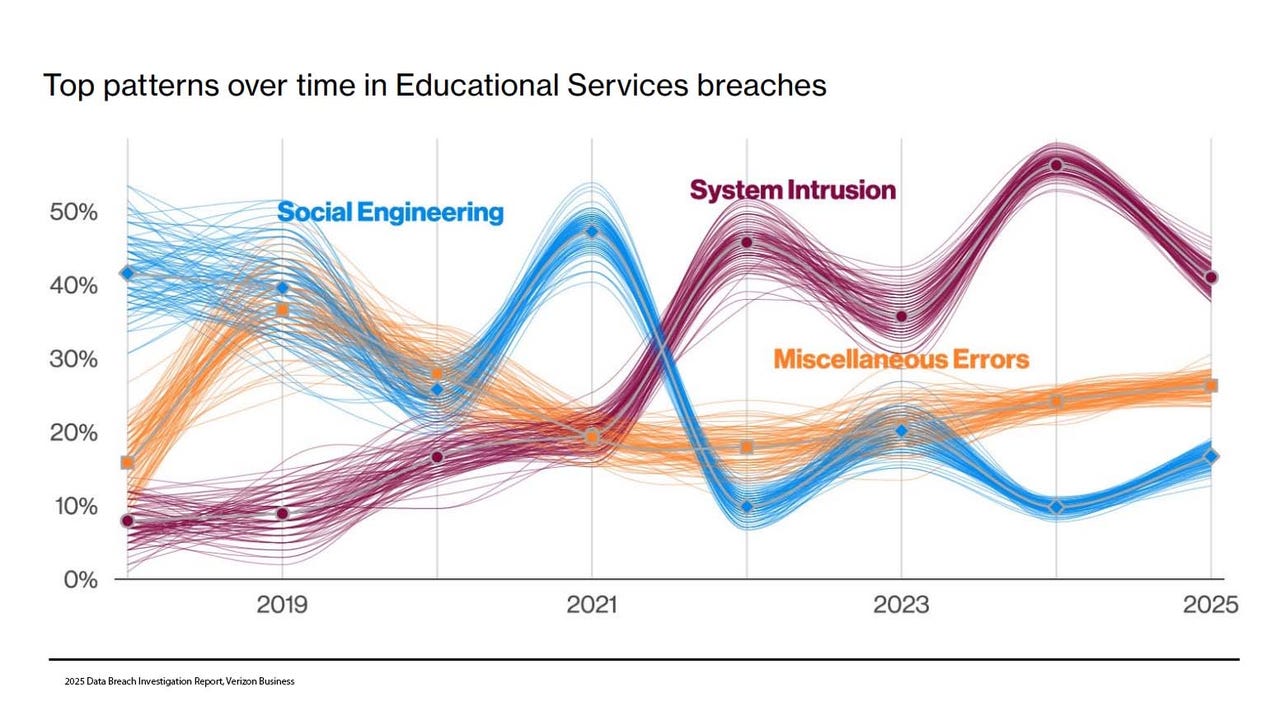
_Olekcii_Mach_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)


























































































![Apple appealing $570M EU fine, White House says it won’t be tolerated [U]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/04/Apple-says-570M-EU-fine-is-unfair-White-House-says-it-wont-be-tolerated.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)
















![At Least Three iPhone 17 Models to Feature 12GB RAM [Kuo]](https://www.iclarified.com/images/news/97122/97122/97122-640.jpg)

![Dummy Models Showcase 'Unbelievably' Thin iPhone 17 Air Design [Images]](https://www.iclarified.com/images/news/97114/97114/97114-640.jpg)