How to Choose Between AWS CodeBuild, Jenkins, and GitHub Actions for Your CI/CD Pipeline
Continuous Integration and Continuous Deployment (CI/CD) pipelines form the backbone of modern software development practices. They automate your testing, building, and deployment processes, significantly reducing manual errors and accelerating your release cycles. With numerous CI/CD tools available in the market, selecting the right one for your project can be challenging. AWS CodeBuild, Jenkins, and GitHub Actions represent three distinct approaches to CI/CD. AWS CodeBuild offers a fully managed service integrated with the AWS ecosystem. Jenkins provides a highly customizable, self-hosted solution with an extensive plugin ecosystem. GitHub Actions delivers a tightly integrated CI/CD experience directly within your GitHub repositories. This article guides you through a detailed comparison of these three popular CI/CD tools, helping you make an informed decision based on your specific requirements, team structure, and technical environment. Prerequisites Before diving into the comparison, ensure you have: Basic understanding of CI/CD concepts and practices Familiarity with software development workflows Knowledge of containerization and infrastructure as code Understanding AWS CodeBuild AWS CodeBuild is a fully managed continuous integration service that compiles source code, runs tests, and produces deployment-ready software packages. Key Features Fully Managed Infrastructure: AWS handles all server provisioning, scaling, and maintenance. Pay-Per-Minute Pricing: Pay only for the compute resources you use during builds. Native AWS Integration: Seamlessly connects with other AWS services like S3, ECR, and Lambda. Custom Build Environments: Configure builds using Docker containers with your specific requirements. Auto-Scaling: Automatically scales to accommodate concurrent builds without configuration. Security Controls: Integrates with IAM for role-based permissions and VPC for network isolation. Configuration Approach AWS CodeBuild uses a buildspec.yml file stored in your repository to define the build process: version: 0.2 phases: install: runtime-versions: nodejs: 16 pre_build: commands: - echo Installing dependencies... - npm install build: commands: - echo Running tests... - npm test - echo Building production asset... - npm run build post_build: commands: - echo Build completed on `date` artifacts: files: - dist/**/* - package.json - appspec.yml base-directory: '.' Understanding Jenkins Jenkins is an open-source automation server that has been a cornerstone of CI/CD processes since 2011. It provides a self-managed environment with extensive customization options. Key Features Self-Hosted Control: Complete ownership of the environment and infrastructure. Plugin Ecosystem: Access to over 1,500 plugins for integrating with virtually any tool. Flexible Deployment: Run on-premises, in the cloud, or in hybrid environments. Distributed Builds: Support for master-agent architecture to distribute workloads. Customizable Workflows: Define complex pipelines with conditional logic and parallel execution. Open-Source Community: Active community support and continuous improvement. Configuration Approach Jenkins typically uses a Jenkinsfile stored in your repository to define the pipeline: pipeline { agent { docker { image 'node:16-alpine' } } stages { stage('Install') { steps { sh 'npm install' } } stage('Test') { steps { sh 'npm test' } } stage('Build') { steps { sh 'npm run build' } } stage('Archive') { steps { archiveArtifacts artifacts: 'dist/**/*', fingerprint: true } } } } Understanding GitHub Actions GitHub Actions is GitHub's integrated CI/CD solution that automates workflows directly from your code repository. Introduced in 2019, it has quickly gained popularity for its simplicity and tight integration with GitHub. Key Features Repository Integration: Built directly into GitHub's ecosystem with no additional accounts. YAML Workflow Definition: Simple configuration using YAML syntax stored in your repository. Actions Marketplace: Extensive library of pre-built actions for common tasks. Matrix Builds: Test across multiple environments and configurations simultaneously. Event-Driven Workflows: Trigger builds based on repository events like push, pull request, or issue creation. Built-in Secret Management: Secure storage and access to sensitive information. Configuration Approach GitHub Actions uses workflow files stored in the .github/workflows directory of your repository: name: Node.js CI o
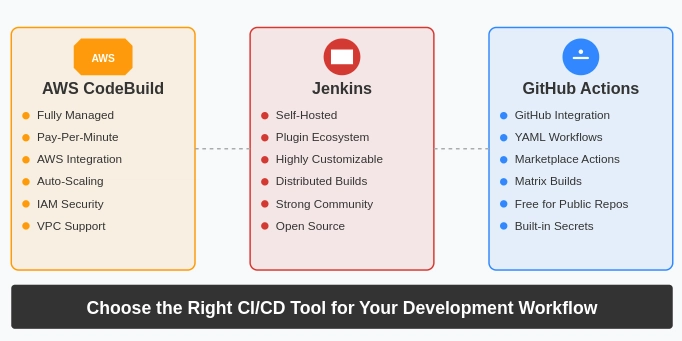
Continuous Integration and Continuous Deployment (CI/CD) pipelines form the backbone of modern software development practices. They automate your testing, building, and deployment processes, significantly reducing manual errors and accelerating your release cycles. With numerous CI/CD tools available in the market, selecting the right one for your project can be challenging.
AWS CodeBuild, Jenkins, and GitHub Actions represent three distinct approaches to CI/CD. AWS CodeBuild offers a fully managed service integrated with the AWS ecosystem. Jenkins provides a highly customizable, self-hosted solution with an extensive plugin ecosystem. GitHub Actions delivers a tightly integrated CI/CD experience directly within your GitHub repositories.
This article guides you through a detailed comparison of these three popular CI/CD tools, helping you make an informed decision based on your specific requirements, team structure, and technical environment.
Prerequisites
Before diving into the comparison, ensure you have:
- Basic understanding of CI/CD concepts and practices
- Familiarity with software development workflows
- Knowledge of containerization and infrastructure as code
Understanding AWS CodeBuild
AWS CodeBuild is a fully managed continuous integration service that compiles source code, runs tests, and produces deployment-ready software packages.
Key Features
- Fully Managed Infrastructure: AWS handles all server provisioning, scaling, and maintenance.
- Pay-Per-Minute Pricing: Pay only for the compute resources you use during builds.
- Native AWS Integration: Seamlessly connects with other AWS services like S3, ECR, and Lambda.
- Custom Build Environments: Configure builds using Docker containers with your specific requirements.
- Auto-Scaling: Automatically scales to accommodate concurrent builds without configuration.
- Security Controls: Integrates with IAM for role-based permissions and VPC for network isolation.
Configuration Approach
AWS CodeBuild uses a buildspec.yml file stored in your repository to define the build process:
version: 0.2
phases:
install:
runtime-versions:
nodejs: 16
pre_build:
commands:
- echo Installing dependencies...
- npm install
build:
commands:
- echo Running tests...
- npm test
- echo Building production asset...
- npm run build
post_build:
commands:
- echo Build completed on `date`
artifacts:
files:
- dist/**/*
- package.json
- appspec.yml
base-directory: '.'
Understanding Jenkins
Jenkins is an open-source automation server that has been a cornerstone of CI/CD processes since 2011. It provides a self-managed environment with extensive customization options.
Key Features
- Self-Hosted Control: Complete ownership of the environment and infrastructure.
- Plugin Ecosystem: Access to over 1,500 plugins for integrating with virtually any tool.
- Flexible Deployment: Run on-premises, in the cloud, or in hybrid environments.
- Distributed Builds: Support for master-agent architecture to distribute workloads.
- Customizable Workflows: Define complex pipelines with conditional logic and parallel execution.
- Open-Source Community: Active community support and continuous improvement.
Configuration Approach
Jenkins typically uses a Jenkinsfile stored in your repository to define the pipeline:
pipeline {
agent {
docker {
image 'node:16-alpine'
}
}
stages {
stage('Install') {
steps {
sh 'npm install'
}
}
stage('Test') {
steps {
sh 'npm test'
}
}
stage('Build') {
steps {
sh 'npm run build'
}
}
stage('Archive') {
steps {
archiveArtifacts artifacts: 'dist/**/*', fingerprint: true
}
}
}
}
Understanding GitHub Actions
GitHub Actions is GitHub's integrated CI/CD solution that automates workflows directly from your code repository. Introduced in 2019, it has quickly gained popularity for its simplicity and tight integration with GitHub.
Key Features
- Repository Integration: Built directly into GitHub's ecosystem with no additional accounts.
- YAML Workflow Definition: Simple configuration using YAML syntax stored in your repository.
- Actions Marketplace: Extensive library of pre-built actions for common tasks.
- Matrix Builds: Test across multiple environments and configurations simultaneously.
- Event-Driven Workflows: Trigger builds based on repository events like push, pull request, or issue creation.
- Built-in Secret Management: Secure storage and access to sensitive information.
Configuration Approach
GitHub Actions uses workflow files stored in the .github/workflows directory of your repository:
name: Node.js CI
on:
push:
branches: [ main ]
pull_request:
branches: [ main ]
jobs:
build:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v2
- name: Use Node.js 16
uses: actions/setup-node@v2
with:
node-version: '16'
cache: 'npm'
- run: npm install
- run: npm test
- run: npm run build
- name: Archive production artifacts
uses: actions/upload-artifact@v2
with:
name: dist
path: dist
Comparing Setup and Configuration
Selecting a CI/CD tool often begins with understanding how much effort is required for initial setup and ongoing configuration.
AWS CodeBuild Setup
- Create a CodeBuild project in the AWS Console or via infrastructure as code.
- Define IAM roles with appropriate permissions for your build process.
- Create a
buildspec.ymlfile in your repository. - Configure build settings including compute type, environment variables, and cache options.
The setup process requires AWS knowledge but leverages existing infrastructure if you already use AWS services.
Jenkins Setup
- Provision a server or container to host Jenkins.
- Install Jenkins and secure the instance.
- Install necessary plugins for your workflow.
- Configure build agents for distributed workloads.
- Create a
Jenkinsfilein your repository.
Jenkins setup involves more operational overhead but provides complete control over your environment.
GitHub Actions Setup
- Create a
.github/workflowsdirectory in your repository. - Add YAML workflow files defining your CI/CD process.
- Configure repository secrets for sensitive information.
GitHub Actions offers the simplest setup process, particularly if your code already resides on GitHub.
Comparing Integration Capabilities
Integration with your existing tools and services significantly impacts the efficiency of your CI/CD pipeline.
AWS CodeBuild Integration
- AWS Services: Native integration with CodePipeline, S3, ECR, Lambda, and other AWS services.
- Source Providers: Supports GitHub, BitBucket, CodeCommit, and S3.
- Notification Services: Integrates with SNS for build notifications.
- Artifact Management: Native support for storing artifacts in S3.
AWS CodeBuild excels when your infrastructure primarily uses AWS services but requires custom scripting for non-AWS integrations.
Jenkins Integration
- Plugin-Based Integration: Extensive plugin ecosystem for nearly any tool or service.
- Source Control: Supports all major source control systems.
- Cloud Providers: Integration with AWS, Azure, GCP, and other cloud services.
- Communication Tools: Connects with Slack, email, and other notification services.
- Container Registries: Supports Docker Hub, ECR, GCR, and other registries.
Jenkins offers the most comprehensive integration options through its plugin architecture.
GitHub Actions Integration
- GitHub Ecosystem: Seamless integration with GitHub repositories, issues, and pull requests.
- Marketplace Actions: Pre-built integrations for common tools and services.
- Cloud Providers: Actions available for all major cloud platforms.
- Container Registries: Native support for GitHub Container Registry and actions for others.
- Third-Party Services: Growing selection of integrations through the Actions Marketplace.
GitHub Actions provides excellent GitHub-centric integrations and a growing ecosystem of third-party integrations.
Comparing Scalability and Performance
As your projects grow, the scalability and performance of your CI/CD solution become increasingly important.
AWS CodeBuild Scalability
- Automatic Scaling: Scales build capacity based on demand without configuration.
- Concurrent Builds: No practical limits on concurrent builds beyond service quotas.
- Build Compute Options: Choose from various compute types to match workload requirements.
- Global Infrastructure: Leverage AWS's global infrastructure for builds close to your deployment targets.
AWS CodeBuild eliminates scaling concerns with its fully managed infrastructure.
Jenkins Scalability
- Manual Scaling: Requires provisioning and configuring additional build agents.
- Resource Constraints: Limited by the hardware resources allocated to the Jenkins server and agents.
- Distributed Architecture: Supports distribution of workloads across multiple agents.
- Configuration Management: Requires careful management of agent configurations as scale increases.
Jenkins scalability depends on your infrastructure investment and operational management.
GitHub Actions Scalability
- Cloud-Based Runners: GitHub-hosted runners scale automatically within usage limits.
- Self-Hosted Runners: Add your own runners for additional capacity and specialized environments.
- Concurrent Jobs: Free tier includes 20 concurrent jobs for public repositories.
- Job Distribution: Automatically distributes jobs to available runners.
GitHub Actions offers good scalability within its usage limits, with options to expand using self-hosted runners.
Comparing Cost Structures
Understanding the cost implications of each CI/CD tool helps ensure your choice aligns with your budget constraints.
AWS CodeBuild Costs
- Pay-Per-Minute: Charges based on build duration and compute type.
- No Idle Costs: Pay only for active build time.
- Tiered Pricing: Costs approximately $0.005 per build minute for medium compute type.
- Free Tier: 100 build minutes per month on smallest compute type.
AWS CodeBuild offers cost-efficient pricing for variable workloads but can become expensive for projects with frequent, long-running builds.
Jenkins Costs
- Infrastructure Costs: Expenses for servers or cloud resources to host Jenkins.
- Operational Overhead: Time and personnel costs for maintenance and management.
- No Per-Build Fees: Fixed infrastructure costs regardless of build frequency.
- Software Costs: No licensing fees for Jenkins itself.
Jenkins involves higher fixed costs but can be more economical for high-volume build environments.
GitHub Actions Costs
- Free Tier: 2,000 minutes per month for private repositories, unlimited for public repositories.
- Paid Tiers: Additional minutes at $0.008 per minute.
- Storage Costs: Artifact and cache storage included with limits based on plan.
- Self-Hosted Runner Costs: Infrastructure expenses if using your own runners.
GitHub Actions provides generous free tier limits with predictable costs for additional usage.
Comparing Security Features
Security is a critical consideration for any CI/CD tool that will access your source code and deployment environments.
AWS CodeBuild Security
- IAM Role-Based Access: Granular permission control through IAM roles and policies.
- VPC Integration: Run builds within a VPC for network isolation.
- Secret Management: Integration with AWS Secrets Manager and Parameter Store.
- Private Registry Access: Secure access to private Docker registries.
- Compliance Certifications: Inherits AWS compliance certifications (SOC, HIPAA, PCI DSS, etc.).
AWS CodeBuild provides enterprise-grade security features, particularly for AWS-centric environments.
Jenkins Security
- Role-Based Access Control: User and role-based permissions system.
- Plugin-Based Security Features: Additional security through plugins like credentials binding.
- Network Isolation: Can be deployed in private networks with controlled access.
- Audit Logging: Tracking of user actions and build history.
- Secret Management: Credentials plugin for managing sensitive information.
Jenkins security depends heavily on proper configuration and regular updates to the core and plugins.
GitHub Actions Security
- Repository Permissions: Inherits GitHub's repository permission model.
- Secret Management: Encrypted environment variables at repository or organization level.
- OIDC Integration: Federated authentication with cloud providers.
- Protected Environments: Approval workflows for sensitive deployment targets.
- Network Isolation: Limited compared to self-hosted solutions.
GitHub Actions offers strong security features for its hosted service, with additional options for self-hosted runners.
Common Implementation Challenges and Troubleshooting
Understanding potential challenges before they arise helps you implement your CI/CD pipeline more smoothly. Each tool presents unique challenges that require specific troubleshooting approaches.
AWS CodeBuild Challenges
-
IAM Permission Issues: Insufficient permissions frequently cause failed builds.
$ aws codebuild start-build --project-name my-project An error occurred (AccessDeniedException) when calling the StartBuild operation: User is not authorized to perform: codebuild:StartBuildSolution: Review and update IAM roles with necessary permissions using the principle of least privilege.
-
Build Container Limitations: Default container sizes may be insufficient for complex builds.
Solution: Adjust compute type in project settings or optimize build processes to reduce resource requirements.
-
VPC Configuration Complexity: Setting up VPC access for builds accessing private resources can be challenging.
Solution: Create a dedicated subnet with appropriate security groups and ensure the VPC has a NAT gateway for internet access.
Jenkins Challenges
-
Plugin Compatibility Issues: Plugin conflicts and version incompatibilities are common.
Solution: Maintain a test instance for verifying plugin updates before applying to production.
-
Resource Exhaustion: Jenkins master can become overwhelmed when handling too many builds.
$ java.lang.OutOfMemoryError: Java heap spaceSolution: Implement distributed builds with agents and adjust JVM memory settings.
-
Credential Management Complexity: Securing and managing credentials across multiple projects requires careful planning.
Solution: Use the Jenkins Credentials Plugin with proper scoping and periodic rotation of secrets.
GitHub Actions Challenges
-
Limited Debugging Capabilities: Troubleshooting failed workflows can be difficult with limited logs.
Solution: Add debugging steps that output environment information and intermediate states.
- name: Debug run: | echo "PWD: $(pwd)" echo "Files: $(ls -la)" env -
Workflow Syntax Errors: Small YAML syntax errors can cause entire workflows to fail.
Solution: Use a YAML validator before committing workflow files and leverage GitHub's workflow visualization tools.
-
Rate Limiting and Queue Times: Free tier users may experience queue times during high-demand periods.
Solution: Implement self-hosted runners for critical workflows and optimize workflow triggers to reduce unnecessary runs.
Community and Support Ecosystem
The strength of the community and available support options significantly impact your long-term success with a CI/CD tool.
AWS CodeBuild Community and Support
- Official Support: Enterprise-grade AWS support plans with response time SLAs.
- Documentation Quality: Comprehensive official documentation with regular updates.
- Community Size: Smaller dedicated community compared to Jenkins or GitHub.
- Learning Resources: AWS workshops, training courses, and certification programs.
- Update Frequency: Regular feature updates and service improvements.
Jenkins Community and Support
- Open Source Community: Large, active community with regular contributions.
- Documentation Quality: Extensive but sometimes fragmented documentation.
- Support Options: Community forums and commercial support from CloudBees.
- User Groups: Local Jenkins user groups in many cities worldwide.
- Release Cycle: Weekly releases for security updates, LTS releases every 12 weeks.
GitHub Actions Community and Support
- GitHub Community: Integrated with GitHub's large developer community.
- Marketplace Growth: Rapidly expanding ecosystem of community-created actions.
- Support Options: GitHub Support and GitHub Premium Support for enterprises.
- Learning Resources: Growing collection of tutorials, blogs, and courses.
- Feature Development: Frequent updates and new features.
DevOps Team Impact and Skill Requirements
Your choice of CI/CD tool affects your team's workflow and requires specific skills for effective implementation and management.
AWS CodeBuild Team Impact
- Required Skills: AWS services knowledge, IAM understanding, YAML configuration.
- Team Workflow: Centralized AWS console management or infrastructure as code approach.
- Hiring Considerations: Requires AWS-certified DevOps engineers or equivalent experience.
- Training Investment: Moderate to high for teams new to AWS services.
Jenkins Team Impact
- Required Skills: Java environment management, plugin ecosystem knowledge, Groovy for pipelines.
- Team Workflow: Dedicated Jenkins administrators often needed for larger installations.
- Hiring Considerations: Widespread Jenkins expertise available in the job market.
- Training Investment: High initial investment but transferable skills across many environments.
GitHub Actions Team Impact
- Required Skills: YAML, GitHub workflow concepts, marketplace action understanding.
- Team Workflow: Developer-centric approach with less DevOps specialist involvement.
- Hiring Considerations: GitHub experience common among developers, reducing specialization needs.
- Training Investment: Low to moderate with gentle learning curve.
Migration Considerations
Whether you're implementing CI/CD for the first time or migrating from an existing solution, understanding the migration path is crucial.
Migrating to AWS CodeBuild
-
From Jenkins:
- Convert Jenkinsfiles to buildspec.yml files
- Replace Jenkins plugins with AWS service integrations
- Migrate credentials to AWS Secrets Manager
- Set up CodePipeline for multi-stage workflows
-
From GitHub Actions:
- Convert workflow YAML to buildspec.yml
- Replace GitHub-specific actions with AWS CLI commands
- Migrate repository secrets to AWS Secrets Manager
- Update deployment targets with appropriate IAM roles
-
Migration Challenges:
- Complex Jenkins pipelines may require significant refactoring
- Custom Jenkins plugins might not have AWS equivalents
- Team retraining on AWS services and IAM policies
Migrating to Jenkins
-
From AWS CodeBuild:
- Set up Jenkins server and required plugins
- Convert buildspec.yml to Jenkinsfile
- Configure Jenkins credentials for AWS access
- Set up agents for distributed builds if needed
-
From GitHub Actions:
- Set up Jenkins server with GitHub integration
- Convert GitHub workflow YAML to Jenkinsfile
- Replace GitHub marketplace actions with Jenkins plugins
- Configure webhook triggers from GitHub
-
Migration Challenges:
- Infrastructure provisioning and maintenance overhead
- Potential performance differences requiring tuning
- Build agent configuration for specific requirements
Migrating to GitHub Actions
-
From AWS CodeBuild:
- Create workflow YAML files in
.github/workflows - Convert buildspec commands to workflow steps
- Set up GitHub secrets for sensitive information
- Configure appropriate triggers and environment variables
- Create workflow YAML files in
-
From Jenkins:
- Convert Jenkinsfile to GitHub workflow syntax
- Replace Jenkins-specific plugins with GitHub marketplace actions
- Set up repository secrets for credentials
- Implement self-hosted runners if needed for special environments
-
Migration Challenges:
- Complex Jenkins pipelines may not have direct equivalents
- Custom build environments may require self-hosted runners
- Usage limits on GitHub-hosted runners for private repositories
Real-world Performance Data
Understanding actual performance metrics helps set realistic expectations for your CI/CD implementation.
Build Time Comparisons
| Scenario | AWS CodeBuild | Jenkins | GitHub Actions |
|---|---|---|---|
| Node.js application build | 45-60 seconds | 60-90 seconds | 50-70 seconds |
| Java application with tests | 3-4 minutes | 4-5 minutes | 3-5 minutes |
| Docker image build and push | 2-3 minutes | 2-4 minutes | 2-3 minutes |
| Full-stack application deployment | 5-8 minutes | 6-10 minutes | 5-9 minutes |
[!NOTE]
These timings represent average scenarios and may vary based on specific configurations, resource allocations, and caching effectiveness.
Scaling Performance
- AWS CodeBuild: Maintains consistent performance with automatic scaling, even during high concurrency (100+ simultaneous builds).
- Jenkins: Performance degradation observed with increasing concurrency unless properly configured with distributed agents.
- GitHub Actions: Maintains good performance for low to medium concurrency, with potential queuing during high demand periods.
Cache Effectiveness
Effective caching significantly improves build performance across all platforms:
- AWS CodeBuild: S3-based caching improves subsequent build times by 40-60%
- Jenkins: Local caching improves subsequent build times by 50-70%
- GitHub Actions: GitHub-managed caching improves subsequent build times by 40-65%
Hybrid Implementation Approaches
Organizations often benefit from combining CI/CD tools to leverage the strengths of each platform for specific scenarios.
Effective Tool Combinations
-
GitHub Actions + AWS CodeBuild:
- Use GitHub Actions for pull request validation and testing
- Use AWS CodeBuild for production builds and deployments to AWS services
- Example workflow:
- Pull request triggers GitHub Actions for fast feedback
- Merge to main triggers AWS CodeBuild for production deployment
-
Jenkins + GitHub Actions:
- Use GitHub Actions for initial testing and validation
- Use Jenkins for complex, resource-intensive builds and specialized deployments
- Example workflow:
- GitHub Actions runs unit tests and code quality checks
- Jenkins handles integration tests and production deployment
-
AWS CodeBuild + Jenkins:
- Use CodeBuild for AWS service deployments
- Use Jenkins for legacy systems and specialized environments
- Example workflow:
- Jenkins orchestrates the overall pipeline
- CodeBuild steps handle AWS-specific deployments
Integration Patterns
- Webhook Chaining: Complete one pipeline triggers another via webhooks
- Artifact Sharing: Output from one tool becomes input for another
- Shared Environment Variables: Pass context between systems using environment variables or parameter stores
# GitHub Actions workflow that triggers AWS CodeBuild
name: Hybrid CI/CD
on:
push:
branches: [ main ]
jobs:
test:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v2
- name: Run tests
run: npm test
- name: Trigger AWS CodeBuild
if: success()
run: |
aws codebuild start-build --project-name production-deploy \
--source-version ${{ github.sha }}
Latest Features and Future Roadmaps
Staying informed about the latest features and development directions helps ensure your CI/CD strategy remains current and effective.
AWS CodeBuild Recent Innovations
- ARM-based build environments for cost-effective builds
- BuildBatch capability for running related builds together
- Report groups for test results analysis
- Enhanced VPC support with simplified configuration
Future Direction: AWS continues to focus on tighter integrations with other AWS services, improved container build experiences, and enhanced security features.
Jenkins Recent Innovations
- Jenkins Pipeline improvements with better visualization
- Configuration as Code (JCasC) for declarative Jenkins configuration
- Jenkins Evergreen for automatic updates and security patches
- Pipeline Authoring UX improvements
Future Direction: The Jenkins project is focusing on stability, security, and modernizing the user experience while maintaining backward compatibility.
GitHub Actions Recent Innovations
- Reusable workflows for sharing common CI/CD patterns
- Composite actions for creating reusable action sequences
- Workflow visualization improvements
- Dependency review and security scanning integrations
Future Direction: GitHub continues to expand the Actions ecosystem, focusing on developer experience, security features, and enterprise capabilities.
Choosing the Right Tool for Your Use Case
Your specific project requirements should guide your CI/CD tool selection. Consider these common scenarios:
When to Choose AWS CodeBuild
AWS CodeBuild works best when:
- Your application primarily uses AWS services
- You prefer managed services with minimal operational overhead
- You need VPC isolation for your builds
- Your builds have variable frequency with periods of inactivity
- You're already using other AWS Developer Tools
Ideal architecture example:
Source Code (CodeCommit/GitHub) → CodeBuild → Artifacts (S3) → CodeDeploy → ECS/EKS
When to Choose Jenkins
Jenkins works best when:
- You need extensive customization for complex build processes
- Your organization has existing Jenkins expertise
- You're working in a hybrid or multi-cloud environment
- You need to support legacy systems with specific requirements
- You have consistent, high-volume builds that make fixed infrastructure cost-effective
Ideal architecture example:
Source Code (Any SCM) → Jenkins Master → Jenkins Agents → Deploy (Any Target)
When to Choose GitHub Actions
GitHub Actions works best when:
- Your code is already hosted on GitHub
- You need simple CI/CD workflows with minimal configuration
- Your team is small and prefers integrated tooling
- Your project is open-source or has public repositories
- You value developer experience and quick setup over advanced customization
Ideal architecture example:
GitHub Repository → GitHub Actions → GitHub Packages/Container Registry → Cloud Provider
Conclusion
Selecting the right CI/CD tool involves balancing several factors including setup complexity, integration capabilities, scalability requirements, cost considerations, and security needs. Each of the three tools examined offers distinct advantages for different scenarios.
AWS CodeBuild excels for AWS-centric architectures, offering a fully managed service with seamless AWS integration. Jenkins provides maximum flexibility and control for organizations with the resources to manage their own infrastructure. GitHub Actions delivers a developer-friendly experience with tight GitHub integration and minimal setup overhead.
Consider these key takeaways when making your decision:
Start with a pilot project: Implement your chosen tool on a smaller, less critical project to evaluate its fit for your environment before full adoption.
Assess team readiness: Consider your team's existing skills and the learning curve associated with each tool.
Plan for growth: Select a solution that can scale with your needs, both in terms of build volume and complexity.
Budget appropriately: Factor in both direct costs (service fees) and indirect costs (maintenance, training, infrastructure).
Consider hybrid approaches: You don't need to choose just one tool—many organizations successfully implement multiple CI/CD solutions for different stages or projects.
Evaluate migration effort: If replacing an existing system, weigh the effort required for migration against the expected benefits.
The most successful CI/CD implementation is one that aligns with your team's workflow, technical requirements, and organizational goals while providing a smooth path to production for your applications. Whichever tool you select, focus on establishing clear processes, promoting automation, and continuously improving your pipeline based on feedback and metrics.











































































































































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)
























































































































![[FREE EBOOKS] The Kubernetes Bible, The Ultimate Linux Shell Scripting Guide & Four More Best Selling Titles](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)



![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)







































































































.png?#)





.jpg?#)






























_Christophe_Coat_Alamy.jpg?#)





































































































![Rapidus in Talks With Apple as It Accelerates Toward 2nm Chip Production [Report]](https://www.iclarified.com/images/news/96937/96937/96937-640.jpg)